This document is applicable for Zimbra Daffodil versions 10.0 and 10.1.0.
License
 Synacor, Inc., 2025-2026
Synacor, Inc., 2025-2026
© 2025-2026 by Synacor, Inc. Zimbra Collaboration Administrator Guide
This work is licensed under the Creative Commons Attribution-ShareAlike 4.0 International License unless another license agreement between you and Synacor, Inc. provides otherwise. To view a copy of this license, visit https://creativecommons.org/licenses/by-sa/4.0 or send a letter to Creative Commons, PO Box 1866, Mountain View, CA 94042, USA.
Synacor, Inc., 2025-2026
505 Ellicott Street, Suite A39
Buffalo, NY 14203
US
Introduction
Zimbra Collaboration is a full-featured messaging and collaboration solution that includes email, address book, calendaring, tasks, and Web document authoring.
|
Zimbra Daffodil (v10.1) introduced a new license service with significant changes in licensing management. Please refer to Licensing section for more details |
Audience
This guide is for system administrators responsible for installing, maintaining, and supporting the server deployment of Zimbra Collaboration.
Readers of this guide should have the following recommended knowledge and skill sets:
-
Familiarity with the associated technologies and standards
-
Linux operating system and open source concepts
-
Industry practices for mail system management
Third-Party Components
Where possible, Zimbra Collaboration adheres to existing industry standards and open source implementations for backup management, user authentication, operating platform, and database management. However, it only supports the specific implementations described in the Zimbra Collaboration architecture overview in the Product Overview chapter as officially tested and certified. This document might occasionally note when other tools are available in the marketplace, but such mention does not constitute an endorsement or certification.
Support and Contact Information
-
Contact Zimbra Sales to purchase Zimbra Daffodil (v10).
-
Zimbra Collaboration customers can contact support at support@zimbra.com.
-
Explore the Zimbra Forums for answers to installation or configuration problems.
-
Join the Zimbra Community Forum, to participate and learn more about Zimbra Collaboration.
-
Send an email to feedback@zimbra.com to let us know what you like about the product and what you would like to see in the product. If you prefer, post your ideas to the Zimbra Forum.
For additional product information, the following resources are available:
Product Life Cycle
This chapter provides information about the Product Life Cycle stages of Zimbra components.
Component Deprecation Statements
| Component | Deprecation Statement |
|---|---|
Zextras/NG modules |
HSM, Backup, Mobile, ABQ, Drive, Docs, Auth, Connect and Admin have been removed. |
IMAPD |
Removed |
Product Overview
This chapter provides a system overview of Zimbra components.
Architectural Overview
The Zimbra Collaboration architecture is built with well-known open source technologies and standards-based protocols. The architecture consists of client interfaces and server components that can run as a single node configuration or be deployed across multiple servers for high availability and increased scalability.
The architecture includes the following core advantages:
| Core Advantage | Components/Description |
|---|---|
Open source integrations |
Linux®, Jetty, Postfix, MariaDB, OpenLDAP® |
Industry-standard open protocols |
SMTP, LMTP, SOAP, XML, IMAP, POP |
Modern technology Design |
HTML5, Javascript, XML, and Java |
Scalability |
Each Zimbra mailbox server includes its own mailbox accounts and associated message store and indexes. The Zimbra platform scales vertically (by adding more system resources) and horizontally (by adding more servers) |
Browser-based client interface |
Easy, intuitive access to Zimbra Collaboration features, using a standard web platform. |
Browser-based Administration Console |
Core Email, Calendar and Collaboration Functionality
Zimbra Collaboration is an innovative messaging and collaboration application that offers the following state-of-the-art solutions that are accessed through the browser based web client.
-
Intuitive message management, search, tagging, and sharing.
-
Personal, external, and shared calendar.
-
Personal and shared Address Books and Distribution Lists.
-
Personal and Shared Task lists.
Zimbra offers an inbuilt feature where a copy of a shared email attachment or mail is stored only once on the filesystem, even if it is sent to multiple users on the same server. This dramatically reduces storage needs because only a single copy is saved, with hard links pointing to the other mailboxes' "blob" stores.
Zimbra Components
Zimbra architecture includes open-source integrations using industry standard protocols. The third-party software listed in Third-Party Software is bundled with Zimbra software and installed as part of the installation process. These components have been tested and configured to work with the software.
| 3rd-Party Component | Description |
|---|---|
Jetty |
Web application server that runs Zimbra software. |
Postfix |
Open source mail transfer agent (MTA) that routes mail messages to the appropriate Zimbra server |
Open LDAP software |
Open source implementation of the Lightweight Directory Access Protocol (LDAP) that stores Zimbra system configuration, the Zimbra Global Address List, and provides user authentication. Zimbra can also work with GAL and authentication services provided by external LDAP directories such as Active Directory |
MariaDB |
Database software |
Lucene |
Open source full-featured text and search engine |
Third-party source that converts certain attachment file types to HTML |
|
Anti-virus/anti-spam |
Open source components that include:
|
Apache JSieve |
Manages filters for email |
LibreOffice |
High fidelity document preview |
OnlyOffice |
Collaborative document editing |
Zimbra Application Packages
Zimbra Collaboration provides the application packages listed in Application Packages.
| Package | Description |
|---|---|
Zimbra Core |
The libraries, utilities, monitoring tools, and basic configuration
files. |
Zimbra Modern Web Client |
The assets required for Zimbra Modern Web App. This package is automatically installed on each server. |
Zimbra Store |
The components for the mailbox server (including Jetty). The Zimbra mailbox server includes the following components:
|
Zimbra LDAP |
Zimbra Collaboration uses the OpenLDAP® software, which is an open source LDAP directory server. User authentication, the Zimbra Global Address List, and configuration attributes are services provided through OpenLDAP. Note that the Zimbra GAL and authentication services can be provided by an external LDAP Directory such as Active Directory. |
Zimbra MTA |
Postfix is the open source mail transfer agent (MTA) that receives email via SMTP and routes each message to the appropriate Zimbra mailbox server using Local Mail Transfer Protocol (LMTP). The Zimbra MTA also includes the anti-virus and anti-spam components. |
Zimbra Proxy |
Zimbra Proxy is a high-performance reverse proxy service for passing IMAP[S]/POP[S]/HTTP[S] client requests to other internal Zimbra services.This package is normally installed on the MTA server(s) or on its own independent server(s). When the zimbra-proxy package is installed, the proxy feature is enabled by default. Installing the Zimbra Proxy is highly recommended, and required if using a separate web application server. |
Zimbra Memcached |
Memcached is automatically selected when the zimbra-proxy is installed. At least one server must run zimbra-memcached when the proxy is in use. You can use a single memcached server with one or more Zimbra proxies. zimbra-memcached is required if using a separate web application server. |
Zimbra SNMP (Optional) |
If you choose to install zimbra-SNMP for monitoring, this package should be installed on every Zimbra server. |
Zimbra Logger (Optional) |
If used, this is installed on one mailbox server, and must be installed at the same time as the mailbox server.The Zimbra Logger installs tools for syslog aggregation and reporting. If you do not install Logger, the server statistics section of the Administration Console will not display. |
Zimbra Spell (Optional) |
Aspell is the open source spell checker used on the Zimbra Classic Web App. When Zimbra-Spell is installed, the Zimbra-Apache package is also installed. |
Zimbra Apache |
This package is installed automatically when Zimbra Spell or Zimbra Convertd is installed. |
Zimbra Convertd |
This package is installed on the zimbra-store server. Only one Zimbra-convertd package needs to be present in the Zimbra Collaboration environment. The default is to install one zimbra-convertd on each zimbra-store server. When Zimbra-Convertd is installed, the Zimbra-Apache package is also installed. |
Zimbra Archiving (Optional) |
Archiving and Discovery offers the ability to store and search all messages delivered to, or sent by the Zimbra Collaboration Server. This package includes the cross mailbox search function which can be used for both live and archive mailbox searches. Note: Using Archiving and Discovery can trigger additional mailbox license usage. To find out more about Zimbra Archiving and Discovery, contact Zimbra sales. |
Zimbra OnlyOffice |
This package installation is required for collaborative document editing of documents which is powered by Onlyoffice and enables collaborative editing of the documents stored in Briefcase. This package can be installed and setup on a Proxy server, Mailbox server or as a separate Document server. |
License Daemon Service (LDS) |
With the introduction of the new license service within Zimbra Daffodil (v10.1) a new license service has been added named License Daemon Service (LDS) to allow enhanced and flexible license management. The LDS is a required service to support the management of the license. |
Mail Flow — Multi-Server Configuration
The configuration for each deployment is dependent on numerous variables such as the number of mailboxes, mailbox quotas, performance requirements, existing network infrastructure, IT policies, security methodologies, spam filtering requirements, and more. In general, deployments share common characteristics for incoming traffic and user connectivity, as depicted in the following diagram. Alternate methods for configuring numerous points within the network are also possible.
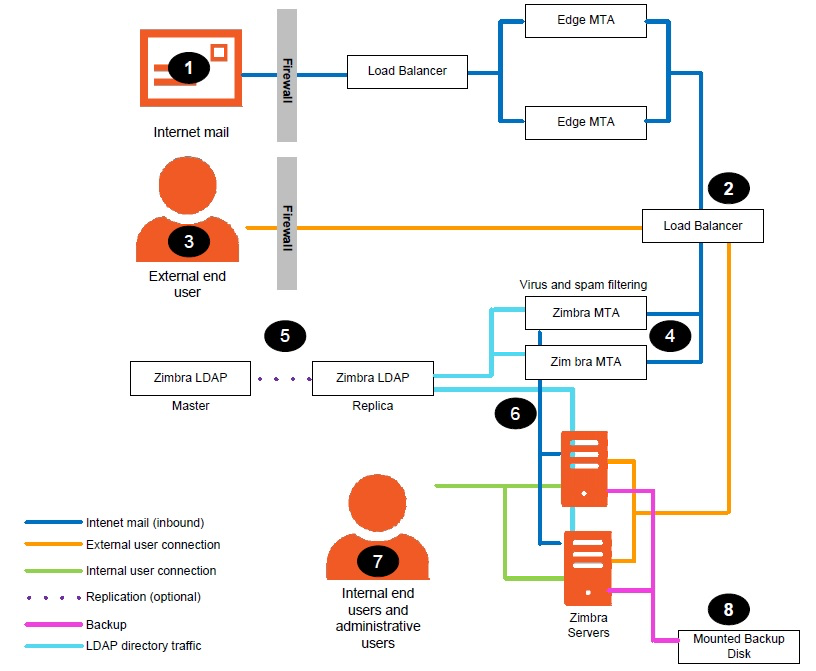
The numbered sequences are described below:
-
Inbound Internet mail goes through a firewall and load balancing to the edge MTA for spam filtering.
-
The filtered mail then goes through a second load balancer.
-
An external user connecting to the messaging server also goes through a firewall to the second load balancer.
-
The inbound Internet mail goes to any of the Zimbra Collaboration MTA servers and goes through spam and virus filtering.
-
The designated Zimbra Collaboration MTA server looks up the addressee’s directory information from the Zimbra Collaboration LDAP replica server.
-
After obtaining the user’s information from the Zimbra Collaboration LDPA server, the MTA server sends the mail to the appropriate Zimbra Collaboration server.
-
Internal end-user connections are made directly to any Zimbra Collaboration server that then obtains the user’s directory information from Zimbra Collaboration LDAP and redirects the user, as needed.
-
The backups from the Zimbra Collaboration servers can be processed to a mounted disk.
Zimbra System Directory Tree
The following table lists the main directories created by the Zimbra
installation packages. The directory organization is identical for any
server in the Zimbra Collaboration, when installing under (parent) /opt/zimbra.
| The directories not listed in the following table are libraries used for building the core Zimbra software or miscellaneous third-party tools. |
| File | Description |
|---|---|
|
Backup target contains full and incremental backup data |
|
Zimbra Collaboration application files, including the utilities described in Command-Line Utilities |
|
Policy functions, throttling |
|
Clam AV application files for virus and spam controls |
|
Configuration information |
|
Third-party scripts for conveyance |
|
Convert service |
|
SASL AUTH daemon |
|
Includes data directories for LDAP, mailboxd, postfix, amavisd, clamav |
|
Data Store |
|
SOAP txt files and technical txt files |
|
Server extensions for different authentication types |
|
Server extensions for different network version authentication types |
|
Contains the Apache Web server. Used for both aspell and convertd as separate processes |
|
Index store |
|
Contains Java application files |
|
mailboxd application server instance. In this directory, the
|
|
Libraries |
|
Internally used executables |
|
Local logs for Zimbra Collaboration server application |
|
RRD and SQLite data files for logger services |
|
MariaDB database files |
|
Used for collecting statistics |
|
OpenLDAP server installation, pre-configured to work |
|
Postfix server installation, pre-configured to work with Zimbra Collaboration |
|
Contains current transaction logs for the Zimbra Collaboration server |
|
SNMP monitoring files |
|
Certificates |
|
Message store |
|
Contains control scripts and Perl modules |
|
Contains Zimlet |
|
Contains Zimlets that are available with the Zimbra Classic Web App |
|
Contains Zimlet |
|
mailboxd statistics, saved as |
Zimbra Web Apps
Zimbra offers multiple Web App types for the use of Zimbra features. The Web Apps provide mail, calendar, address book, and task functions.
| Client Type | Description |
|---|---|
Modern Web App |
Uses modern technologies, UI design, and offers same user experience across devices like Desktop, Mobile and Tablet. |
Classic Web App |
Includes Ajax capability and offers a full set of web collaboration features. Supports desktop web browsers only; does not provide a user experience adapted to smaller screens, touch capabilities, or gestures. |
Users may select the Web App before they sign in, from the 'Version' drop-down on the login page. The admin can set the Default Web App to either Classic Web App or the Modern Web App, for a COS. Users can override this Default:
-
In the Modern Web App, users can go to Settings→General to change the value of default Web App they login to
-
In the Classic Web App, users can go to Preferences→General→Sign in to change the value of default Web App they login to
It is recommended that admins set the Default to the Modern Web App.
Web Services, Desktop Clients and Mobile Apps
In addition to using a web browser or mobile device to connect to Zimbra Collaboration, connection is available using a web service, such as Exchange Web Services (EWS), or a desktop client such as Zimbra Connector to Microsoft Outlook. The following are supported:
-
Exchange Web Services (EWS) provides client access to enable Zimbra Collaboration to communicate with the Exchange Server when using Microsoft Outlook on a Mac device. To enable EWS client access, see the Class of Service section. EWS is a separately licensed add-on feature.
-
Messaging Application Programming Interface (MAPI) synchronizes to supported versions of Microsoft Outlook with full delegate, offline access and support for S/MIME. Use the Zimbra Connector for Outlook to connect to Zimbra Collaboration when using Microsoft Outlook on a Windows device. To enable MAPI (Microsoft Outlook) Connector, see the Class of Service section.
-
Exchange ActiveSync (EAS) enables mobile access to Zimbra Collaboration from supported mail applications on Android and iOS devices. Using EAS, users can sync their email, calendar, and contacts in real time with native apps such as Gmail (Android), Samsung Email, iOS Mail, and Microsoft Outlook Mobile. EAS provides a seamless experience optimized for mobile productivity. To enable EAS access, see the Class of Service section. EAS is a separately licensed add-on feature.
| EAS is not supported on Windows Outlook desktop clients due to Microsoft’s deprecation of EAS on that platform. |
-
Support for all POP3, IMAP4, Calendaring Extensions to Web Distributed Authoring and Versioning (CalDAV), and vCard Extensions to Web Distributed Authoring and Versioning (CardDAV) clients.
Client Compatibility Overview
This table outlines supported apps and operating systems across Zimbra protocols (ZCO, ActiveSync, EWS) for desktop and mobile users.
To setup accounts through the ZCO, EWS, and ActiveSync protocol, please refer to Add account to Outlook and Mobile Apps section.
Recommendation: Zimbra recommends to use ZCO for Outlook on Windows, EWS for Outlook on Mac, and ActiveSync for mobile access on Android and iOS.
| Protocol | Supported Platforms | Supported OS / Versions | Supported Apps | Notes |
|---|---|---|---|---|
ZCO |
Windows Desktop |
Windows OS (versions 10, 11) |
Classic Outlook (Legacy) 2021, 2024, 365 |
Recommended for all Windows desktop users. |
ActiveSync |
Android |
Android OS 15 & 16 |
Gmail, Outlook App, Samsung Email App |
|
iOS |
iOS 18.5 |
iOS Mail App, Outlook App |
||
EWS |
MacOS |
macOS 14 (Sonoma), 15 (Sequoia) |
Classic Outlook (Legacy) 2021, 365 Mail App |
⚠️ Outlook 2019 is deprecated as it reached End of Life in October 2023. |
Offline Mode
| For Classic Web App, Offline mode is no longer supported for Chrome versions 85 and above (affects Kepler9-Patch9 onwards). Users can still continue to use Offline mode in previous browser versions. |
Zimbra Offline Mode allows access to data — without network connectivity — when using the Zimbra Modern Web App.
For example, if there is no server connectivity or if server connectivity is lost, the Web App automatically transitions to “offline mode”. When server connectivity is restored, the Web App automatically reverts to “online mode”.
This offline mode uses the caching capability provided by HTML5 in modern browsers.
Security Measures
The coordinated use of multiple security measures, targeted to increase the security of the whole system, is one of the best approaches to securing your information infrastructure. These measures are implemented in the Zimbra Collaboration platform as a result of defense mechanisms summarized in the following topics:
| To view current and detailed security news and alerts, please refer to Security Center on the Zimbra Wiki. |
Identity and Access Management
Key functions built into the system for user identity management are summarized in the following table:
| Function | Description |
|---|---|
Identity Lifecycle Management |
The leveraging of LDAP directory for all Create, Read, Update, and Delete (CRUD) functions associated to user administration with Zimbra Collaboration. LDAP usage is optional but all attributes specific to Zimbra Collaboration are stored and managed through the native LDAP directory. |
First Factor Authentication |
The combined user name and password primarily employed by authorized users when attempting to access the system. These credentials are retained in the user store: the passwords are stored as salted hash that is compared against that of the entered password, for rejection (no match) or acceptance (matched). If external directory (LDAP or Active Directory) is preferred, the appropriate login credentials can be stored in this external LDAP directory. See also Zimbra LDAP Service for more details. |
Two Factor Authentication |
A second layer of identity security that is configured at the Admin Console to enable or disable passcode generation to mobile devices associated with Zimbra Collaboration. When enabled, user or COS accounts must use the generated passcode to gain access to their client services. See also About 2 Factor Authentication and Two Factor Authentication. |
Authorized Access |
User accounts are defined by various attributes, permission levels, and policies to allow or disallow what data can be viewed and which functions can be performed. Admin Console administrators can create groups and assign access permissions to support targeted business objectives. |
Information Security and Privacy
Functions built into the system to secure data are summarized in the following table:
| Key Concept | Description |
|---|---|
Management of security, integrity, and privacy |
Zimbra Collaboration supports the use of S/MIME certificates (provided by publicly trusted Certification Authority (CA), as well as internal PKI; DomainKeys Identified Mail (DKIM); Domain-based Message Authentication, Reporting and Conformance (DMARC); Amavisd-new, which is housed in the Mail Transfer Agent (MTA) to manage incoming and out going DMARC policies. |
Encryption methods: |
|
In-transit |
Secure connections between endpoints and services use TLS in addition to various other protocols: SMTP, LMTP+STARTTLS, HTTPS, IMAPS/IMAP+STARTTLS, POP3S/POP3+STARTTLS. |
At-rest |
With S/MIME for end-to-end encryption, data stored in a Zimbra Collaboration message store is encrypted until decryption occurs with the appropriate private key. |
Anti-virus and Anti-spam |
Both malware and spam are challenged by the Zimbra Collaboration native functionality and third-party plugins: Amavisd-new, ClamAV, and Spam Assassin. |
| This feature is supported only in the Classic Web App. |
System Logs
The Zimbra Collaboration system logs — generated by SNMP triggers — can be used to record data such as user and administrator activity, login failures, slow queries, mailbox activity, mobile synchronization activity, and data based errors. Events, alerts and traps can be forwarded to log management and event correlation system to create centralized polices and notifications based on your security and compliance requirements.
| Function | Description |
|---|---|
Incident response |
Administrators can use remote device wiping and/or account lockout in the event of a malicious or accidental activities (such as stolen user account credential, or lost smart phone). |
Archiving and discovery |
This optional feature allows administrators to select specific user email messages for archival and application of retention policies, which can be used for both archived and live mailboxes. |
E
Zimbra Daffodil (v10.1) Licensing
Zimbra Daffodil (v10.1) introduced an automated licensing and entitlement system for better flexibility in managing licenses and allows for future growth.
With the introduction of the new license service within Zimbra Daffodil (v10.1) a new license service has been added named License Daemon Service (LDS) to allow enhanced and flexible license management.
| Please see License Daemon Service section for more information on LDS and how to setup. |
A Zimbra Collaboration license is required to enable license features and create accounts.
Following are the Zimbra Daffodil (v10.1) licensing updates:
-
A new license daemon is part of the Zimbra installation. It gets displayed as
zimbra-license-daemonin the modules list and required for the normal functioning of Zimbra. -
An 18-26 alphanumeric character key is required which replaces the older license.xml file.
-
Zimbra Collaboration licenses are restrictive to the entitlement defined within the license and do not support multiple activations.
-
Once the Zimbra Collaboration license is activated no future license management by the user is required. License management is real-time and is managed by Zimbra.
-
An offline license server has been introduced to support environments that don’t have access to the public network.
-
All data gathered is based on license requirements and total usage which meets GDPR and other legal regulations.
The LDAP and LDS hostname are recorded for license registration and activation. -
Independent lab licenses are available. Contact Zimbra Sales or Support team.
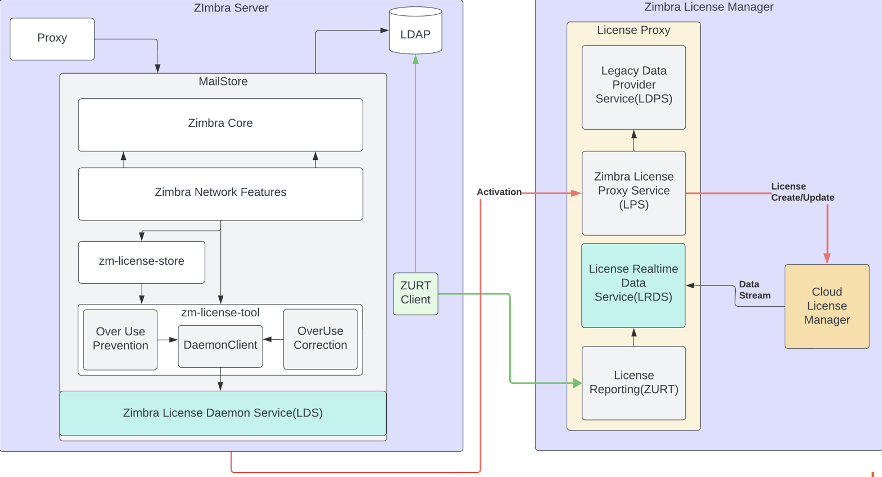
Following is the architecture view:
LDAP Attributes
Following are the new attributes for Zimbra Daffodil (v10.1) licensing:
-
zimbraNetworkRealtimeLicense - Stores the license key required for both online and offline activation.
-
zimbraNetworkRealtimeActivation - Contains activation details, activated product version, features of activated license.
-
zimbraOfflineNetworkRealtimeLicense - Stores the network key required for offline activation.
-
zimbraFeatureActualUsageCount - Storing the Reporting and enforced feature’s over usage count.
License Features
Zimbra Collaboration licensing gives administrators visibility and control of the licensed features they plan to deploy. You can monitor usages and manage the following license features.
Zimbra Daffodil (v10.1) introduced a detailed view of licensed and unlicensed features for better management within the Admin UI or command line. The following are tracked licensed features:
| Feature | Licensed Attributes | Description | Feature Code |
|---|---|---|---|
Accounts |
AccountsLimit |
Accounts you can create. |
AL |
ZCO |
MAPIConnectorAccountsLimit |
Accounts that can use Zimbra Connector for Microsoft Outlook (ZCO). |
MCAL |
EWS |
EwsAccountsLimit |
Accounts that can use EWS for connecting to an Exchange server. EWS is a separately licensed add-on feature. |
EAL |
Zimbra Mobile |
MobileSyncAccountsLimit |
Accounts that can use ActiveSync protocol to access emails on their mobile devices. |
MSAL |
S/MIME |
SMIMEAccountsLimit |
Accounts that can use S/MIME feature. |
SMAL |
Archiving |
ArchivingAccountsLimit |
Allowed archive accounts. The archive feature installation is required. |
AAL |
Zimbra Office |
DocumentEditingAccountsLimit |
Document collaboration feature which enables to create/edit/share the documents within the organization. OnlyOffice installation is required. |
DEAL |
Sharing |
SharingAccountsLimit |
Control the Sharing & Delegation feature for the users. |
SHAL |
Briefcase |
BriefcaseAccountsLimit |
Control the Briefcase feature for the users. |
BAL |
Backup & Restore |
BackupEnabled |
Allows the admin to use Backup & Restore Feature |
BE |
Storage Management (Internal Volumes) |
StorageManagementEnabled |
Allows the admin to use Storage Management feature and create volumes using internal stores. |
SME |
Storage Management (External(S3) Volumes) |
ObjectStoreSupportEnabled |
Allows the admin to use Storage Management feature and create volumes using external S3 providers (e.g. AWS, Ceph). |
OSSE |
Attachment Indexing |
AttachmentIndexingEnabled |
Allows indexing of the attachment contents |
AIE |
Calendar |
CalenderAccountsLimit |
Enabling calendar feature for the users |
CALAL |
Conversation |
ConversationEnabledAccountsLimit |
Enabling conversation feature for the users |
CNEAL |
CrossMailboxSearch |
CrossMailboxSearchEnabled |
Allows doing searches for content across live and archive mailboxes. |
CMBSE |
Delegated Admin |
DelegatedAdminAccountsLimit |
Delegated Admin Accounts you can create |
DAAL |
Group Calendar |
GroupCalenderAccountsLimit |
Enables you to see multiple calendars at the same time |
GCAL |
Tag |
TaggingEnabledAccountsLimit |
Enabling tagging feature for the users |
TEAL |
Task |
TaskEnabledAccountsLimit |
Enabling task feature for the users |
TKEAL |
HTML View of attachements |
ViewInHtmlEnabledAccountsLimit |
View email attachments in HTML format |
VHEAL |
Zimlets |
ManageZimletsEnabledAccountsLimit |
User accounts that can manage Zimlets |
MZEAL |
Multi Factor Auth |
MultiFactorAuthEnabled |
Control the two factor authentication feature for the users. |
MFAE |
The feature codes can be used to check the status of the individual service using the zmlicense command. Please refer to zmlicense section for more details.
|
Zimbra Daffodil (v10.1) License Requirements
| You require a Zimbra’s license to create accounts in Zimbra Collaboration and to use the Modern Web App. |
| Trial License is limited to one email address and an extension can be requested by contacting Zimbra Sales. |
To try out Zimbra Collaboration, you can obtain a trial version free of charge. Once your system is installed in a production environment, you will need to purchase a subscription or a perpetual license.
| License Types | Description |
|---|---|
Trial |
You can obtain a free Trial license from the Zimbra website, at https://www.zimbra.com → Product → Download → Get Trial License. The trial license allows you to create up to 50 users. It expires in 60 days. |
Subscription |
A Zimbra Subscription license can only be obtained through purchase. This license is valid for a specific Zimbra Collaboration system, is encrypted with the number of Zimbra accounts (seats) you have purchased, the effective date, and the expiration date of the subscription license. |
Perpetual |
A Zimbra Perpetual license can only be obtained through purchase. This license is similar to a subscription license. It is valid for a specific Zimbra Collaboration system, is encrypted with the number of Zimbra accounts (seats) you have purchased, the effective date, and an expiration date of 2099-12-31. When you renew your support agreement, you receive no new perpetual license, but your Account record in the system gets updated with your new support end date. |
License Usage by Zimbra Collaboration Account Type
An account assigned to a person, including an account created for archiving, requires a mailbox license. Distribution lists, aliases, locations, and resources do not count against the license.
Below is a description of types of Zimbra Collaboration accounts and if they impact your license limit.
| License Account Type | Description |
|---|---|
System account |
System accounts are specific accounts used by Zimbra Collaboration. They include the spam filter accounts for junk mail (spam and ham), the virus quarantine account for email messages with viruses, and the GALsync account if you configure GAL for your domain. Do not delete these accounts! These accounts do not count against your license. |
Administrator account |
Administrator and delegated administrator accounts count against your license. |
User account |
User accounts count against your license account limit. When you delete an account, the license account limit reflects the change. |
Alias account |
These types do not count against your license. |
Distribution list |
|
Resource account |
License Activation
All Zimbra Daffodil (v10.1) installations require license activation and continues to support the Automatic and Manual license methods. In Daffodil (v10.1), the terms has been changed to Online Activation and Offline Activation.
The Admin Console has been enhanced with a more intuitive and easy-to-follow UI where all the operations related to license deployment are on a single screen.
The activation of the Zimbra Daffodil (v10.1) License can be done during the installation, upgrade, or after the installation. No future license management is required on the server once the license has been activated.
Without activating the license, the Zimbra services will not start.
| A license re-activation is required for any updates to the license (e.g., enable a new feature or updates to the limits). The activation count will not be impacted when re-activating the license on the same server. |
Online License Activation
Licenses are automatically activated if the Zimbra Collaboration server has a connection to the Internet and can communicate with the Zimbra License server.
Following are the applicable activation rules for an online license:
-
Account should have valid support end date.
-
License should be Valid (should not be expired).
-
License can be switched, provided new license limit is greater than or equal to current license usage.
-
Activation of trial license over any existing license (trial, regular, perpetual) is not allowed.
Following are the steps to activate the license:
Admin Console
-
Login to Admin Console and go to Home → Get Started → Install Licenses → Online Activation
-
In the Key text box, specify the 18-26 alphanumeric character license key and click on Activate.
-
After successful activation, you will see a success message - Your license is successfully activated.
Command Line
You can also activate your license from the command line interface.
-
As a
zimbrauser, run the command:
zmlicense -a <license_key>
-
After successful activation, you will see a success message - Your license is successfully activated.
| Upgraded Zimbra Collaboration versions require an immediate activation to maintain network feature functionality. |
If you are unable to activate your license automatically, see the next section on Offline License Activation.
Offline License Activation
The method of generating and activating an Offline License in Zimbra Daffodil (v10.1) has changed. As a pre-requisite, a new package zimbra-nalpeiron-offline-daemon
| The Offline License activation will not work if the package is not installed or the offline daemon service is not running. |
| The Offline Daemon service is a critical and important service for the functioning of a Offline License and its management. You are recommended to have a service monitoring setup to check the state of the service. |
| The offline license may take upto 48 hours to be issued. |
Following is the architectural view of the Offline License process:
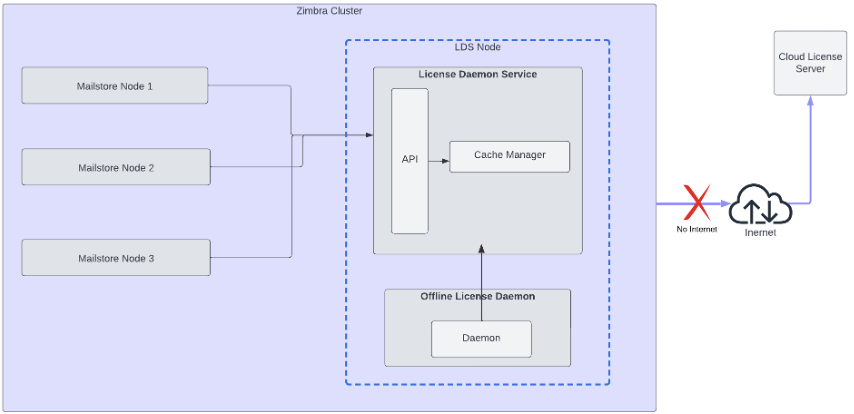
Pre-requisites
Following are the pre-requisites to be completed before installing the offline daemon packages:
Disable FIPS
FIPS should be disabled on the system before installing the offline daemon packages.
Following are the steps to disable FIPS. Execute the commands as root user:
-
For RHEL/CentOS/Rocky Linux systems:
sudo fips-mode-setup --disable sudo reboot
-
Verify FIPS is disabled. Check the /proc/sys/crypto/fips_enabled file. If disabled, following will be the output:
$ cat /proc/sys/crypto/fips_enabled 0
-
-
For Ubuntu systems:
sudo ua disable fips sudo reboot
-
Verify FIPS is disabled. Check the /proc/sys/crypto/fips_enabled file. If disabled, following will be the output:
$ cat /proc/sys/crypto/fips_enabled 0
-
Disable SELinux
SELinux should be disabled on the system before installing the offline daemon packages. You will have to reboot the system to make the changes effective.
Following are the steps to disable SELinux. Execute the commands as root user:
-
For RHEL/CentOS/Rocky Linux systems:
-
Check the SELinux status. If the status appears
enabled, execute the further steps to disable:$ sestatus| grep 'SELinux status\|Current mode' SELinux status: enabled Current mode: enforcing
-
Edit
/etc/sysconfig/selinux:vi /etc/selinux/config
-
Change the SELINUX directive to disabled.
SELINUX=disabled
-
Save and exit the file. Reboot the system:
reboot
-
After the reboot, check the status. SELinux should appear disabled:
$ sestatus| grep 'SELinux status' SELinux status: disabled
-
-
For Ubuntu systems:
-
Check the SELinux status. If the status appears
enabled, execute the further steps to disable:$ sestatus| grep 'SELinux status\|Current mode' SELinux status: enabled Current mode: enforcing
-
Edit
/etc/selinux/config:vi /etc/selinux/config
-
Change the SELINUX directive to disabled.
SELINUX=disabled
-
Save and exit the file. Reboot the system:
reboot
-
After the reboot, check the status. SELinux should appear disabled:
$ sestatus| grep 'SELinux status' SELinux status: disabled
-
Add locale en_US.utf8
Locale en_US.utf-8 is required for the offline daemon packages.
Following are the steps to check and add the locale. Execute the commands as root user:
-
For RHEL/CentOS/Rocky/Ubuntu Linux systems:
-
Check if the required locale
en_US.utf8is available on the system. If available, it will display as following:$ locale -a |grep 'en_US.utf8' en_US.utf8
-
If not available, add the locale:
$ localedef -i en_US -f UTF-8 en_US.UTF-8
-
Install offline daemon packages
Following are the steps to install the offline daemon packages. Execute the commands as a root user:
-
For RHEL/CentOS/Rocky Linux systems:
yum clean metadata yum check-update yum install zimbra-nalpeiron-offline-daemon
-
For Ubuntu systems:
apt-get update apt-get install zimbra-nalpeiron-offline-daemon
-
Verify the nalpdaemon service is active:
$ systemctl status nalpdaemon ● nalpdaemon.service - Nalpeiron Licensing Daemon Loaded: loaded (/usr/lib/systemd/system/nalpdaemon.service; enabled; vendor preset: disabled) Active: active (running) since Sat 2024-06-08 02:03:37 EDT; 1s ago
In case the service is not active, restart the service:
$ systemctl restart nalpdaemon
As a zimbra user, restart the LDS and configdctl service:
$ su - zimbra $ zmlicensectl --service restart $ zmconfigdctl restart
Requesting and Activating Offline license
The method is supported through Admin Console and CLI.
Following are the steps:
Admin Console
-
Contact the Support team to get the Network Key and License Key.
-
Login to Admin Console and go to Home → Get Started → Install Licenses → Offline Activation
-
Under Step 1, specify the Network Key and License Key and click on Generate Activation Request.
-
After the network and product activation files are generated successfully, Download button will appear next to the text box.
-
Click on Download button next to the text box and save the files. The name and filetype will be pre-populated when saving - network_activation_fingerprint, product_activation_fingerprint.
-
Login to Support Portal and select the License tab.
-
Select Generate an Offline License Activation file for versions 10.1 or greater.
-
Specify the Product License Key and Network License Key.
-
Copy the contents of network_activation_fingerprint.txt file and paste in the Network Activation Fingerprint text box.
-
Copy the contents of product_activation_fingerprint.txt file and paste in Product Activation Fingerprint text box.
-
Specify the product version in Product Verstion text box.
-
Click on Generate License Certificate
-
Save the generated License Activation XML file.
-
Go back to the Admin Console License page.
-
Under Offline Activation → Step3, upload the License Activation XML file and click on Activate.
-
After successful activation, you will see a success message - Your license is successfully activated.
Command Line
-
Contact Sales and get the Network Key and License Key.
-
As a
zimbrauser, runzmlicensecommand to generate Network Key and License Keyzmlicense --offlineActivationRequestCert --network <network_key> --product <product_key>
-
Save the certificates printed on the screen as network_activation_fingerprint.txt, and product_activation_fingerprint.txt.
-
Login to Support Portal and select the License tab.
-
Select Generate an Offline License Activation file for versions 10.1 or greater.
-
Specify the Product License Key and Network License Key.
-
Copy the contents of network_activation_fingerprint.txt file and paste in the Network Activation Fingerprint text box.
-
Copy the contents of product_activation_fingerprint.txt file and paste in Product Activation Fingerprint text box.
-
Specify the product version in Product Verstion text box.
-
Click on Generate License Certificate
-
Save the generated License Activation XML file on the server.
-
As a
zimbrauser, runzmlicensecommand to activate the offline licensezmlicense -A /path_to_XML/activation_file.xml
-
After successful activation, you will see a success message - Your license is successfully activated.
If you have problems accessing the Support Portal or facing any issues when activating the Offline License, contact Zimbra Sales or Support.
When Licenses are not Installed or Activated
If you fail to install or activate your Zimbra Collaboration server license, the following scenarios describe how your Zimbra Collaboration server will be impacted.
| License Condition | Description/Impact |
|---|---|
Not installed |
With no installed license, the Zimbra Collaboration server defaults to single user mode where all license-limited features are limited to one user. |
Not valid |
If the license file appears forged or fails validation for other reasons, the Zimbra Collaboration server defaults to single-user mode. |
Not activated |
A license activation grace period is 10 days. If this period passes without activation, the Zimbra Collaboration server defaults to single-user mode. |
For future date |
If the license starting date is in the future, the Zimbra Collaboration server defaults to single-user mode. |
In grace period |
Zimbra Daffodil (v10.1) onwards, the Grace Period functionality has been changed. For more details, please refer to the Grace Period section in the Admin Guide. |
Expired |
Zimbra Daffodil (v10.1.10) onwards, if the license ending date has passed, the server will not enter the grace period. For more details, please refer to the License Expiry and Grace Period section in the Admin Guide. |
Renewal |
Zimbra Daffodil (v10.1.10) onwards, if the license is not renewed before the ending date, the server will not enter the grace period. For more details on how to re-activate the license after renewal, please refer to the License Renewal After Expiry section in the Admin Guide |
Obtaining a License
Go to the Zimbra Website https://www.zimbra.com → Product → Download → Get Trial License to obtain a trial license. Contact Zimbra sales to extend the trial license, or to purchase a subscription license or perpetual license, by emailing sales@zimbra.com or calling 1-972-407-0688.
The subscription and perpetual license can only install on the Zimbra Collaboration system identified during purchase. Only one Zimbra license is required for your Zimbra Collaboration environment. This license sets the maximum number of accounts on the system.
Current license information, including the number of accounts purchased, the number of accounts used, and the expiration date, can be viewed in the Admin Console.
- Admin Console:
-
Home → Get Started → Install Licenses → Current License Information.
License Reconciliation and Data Collection Notice
| By consenting to the End-User License Agreement, you grant Synacor Inc. and its certain licensees, permission to collect licensing and non-personally-identifiable usage data from your Zimbra Collaboration server. |
During installation, upgrades, and periodically while in use, the Zimbra Collaboration server transmits information for reconciliation of billing and license data.
Permission for this data collection is granted under sections 11.4 and 11.6 of the End User License Agreement for Zimbra Collaboration. Copies of the license can be found at https://www.zimbra.com/legal/licensing/.
The data that is being collected consists of elements of the current license information and is governed by Synacor’s Privacy Policy, which can be found at https://www.synacor.com/privacy-policy/.
Admin Console Enhancements
The License Management UI has been enhanced and made it a more intuitive and easy-to-follow UI where all the operations related to license deployment are on a single screen.
The License Management page can be accessed in 2 ways:
-
Login to Admin Console and go to Home → Get Started → Install Licenses
-
Login to Admin Console and go to Home → Configure → Global Settings → License
Overview
All the license operations are now available on a single screen. Following are the details of the section:
Current License Information
Displays the details of the license, status of the features, and usage for each feature.
Online Activation
Prior to Zimbra Daffodil (v10.1), this method was known as Automatic Activation.
If your server has direct connection to internet, you can use the Online method of activating the license.
Specify the 18-26 alphanumeric character license key and click on Activate to activate your license. After successful activation, you will see a success message - Your license is successfully activated
Offline Activation
Prior to Zimbra Daffodil (v10.1), this method was known as Manual Activation.
If your server do not have a direct connect to internet, you can use the Offline method of activating the license.
Please refer to the Offline License Activation section for detailed steps on generating the Offline License.
License check for Storage Management feature
Zimbra Daffodil (v10.1) onwards, the licenses are divided into two parts for the Storage Management feature:
-
StorageManagementEnabled - Attribute to enable/disable the Storage Management feature and to allow/disallow create volumes on internal storage.
-
ObjectStoreSupportEnabled - Attribute to allow/disallow creating volumes on external storage.
| ObjectStoreSupportEnabled attribute is dependent on StorageManagementEnabled attribute. So you cannot enable ObjectStoreSupportEnabled without enabling StorageManagementEnabled for the license. |
Admin Console updates
Depending upon which attributes are enabled in the licenses, following will be the behavior:
StorageManagementEnabled = FALSE or license expired
-
If you try to access the Storage Management tab Home → Configure → <Server> → <Server_Name> → Storage Management, an error dialog gets displayed - Your license for this feature has expired or is not valid. Please see Configure - Global Settings - License for more information.
-
If you try to access the Storage Management tab under Global Settings Home → Configure → Global Settings → Storage Management an error dialog gets displayed - Your license for this feature has expired or is not valid. Please see Configure - Global Settings - License for more information.
StorageManagementEnabled = TRUE and ObjectStoreSupportEnabled = FALSE
If ObjectStoreSupportEnabled is false and StorageManagementEnabled is true:
-
If you try to access the Storage Management tab Home → Configure → <Server> → <Server_Name> → Storage Management, the banner is displayed at the top of the page - You are not currently licensed for external volumes. Please see Configure - Global settings - License for more information.
-
When trying to add a volume, the selection of the external volumes will be disabled.
-
You cannot execute the SM session. The Start button appears disabled. You can execute it through CLI.
-
You cannot schedule an SM session. The scheduling appears disabled.
-
You will be able to create new policies.
-
If you try to access the Storage Management tab under Global Settings Home → Configure → Global Settings → Storage Management, you will not be able to view the bucket information.
-
When setting up volumes, if there were previously created external volumes, they will not appear in the list.
StorageManagementEnabled = TRUE and ObjectStoreSupportEnabled = TRUE
-
All functionality of Storage Management feature is available.
-
You can create internal and external volumes.
Zimbra Daffodil (v10.1.10) - License Expiry and Grace Period Behavior
To ensure stronger compliance with licensing policies, starting with Zimbra Daffodil (v10.1.10), the Grace Period mechanism has been refined to distinguish between license expiry and license server connectivity loss.
License expiry
If your license expires, the system will not enter a Grace Period.
Services will be stopped immediately post expiry.
|
These updates apply to the Regular and Trial license types. |
Pre-Expiry Notifications
To help ensure timely renewals and uninterrupted service, the system notifies the Zimbra administrators through multiple channels ahead of license expiry:
Email Notifications
Email reminders are automatically sent to the administrator email addresses configured in the Zimbra system.
These emails are sent at:
-
90 days
-
60 days
-
45 days
-
30 days
-
15 days
-
1 day before expiry
Emails are sent to addresses configured in the zimbraLicenseNotificationEmail LDAP attribute.
|
Currently, only the internal email address can be updated for notifications. External email address support will be delivered in upcoming releases. If no address is set, the system logs:
Make sure the notification email is set and monitored so that the pre-expiry notifications are not missed. |
Each notification email includes:
-
The license ID.
-
The number of days remaining before the license expiry.
-
The exact expiry date.
Subject: Zimbra License Expiry Notification – X Days Remaining Dear Administrator, Your Zimbra license (ID: <License_KEY>) expires in 90 days on <Expiry_Date>. Please ensure timely renewal to avoid service disruptions. For renewal assistance contact the sales team. Regards, Zimbra Licensing System
|
These notifications are internal to the Zimbra system and do not rely on any external platforms (e.g., Salesforce). Notifications work independently and are sent to the email address defined in the Notifications will be sent only for Regular license type. |
Email Notifications via Salesforce
In addition to internal notifications, Salesforce (SFDC) sends similar pre-expiry notifications to contacts defined in the customer account.
The notifications are sent for the upcoming license expiry or the support contract end date.
It follows the same notification schedule: 90, 60, 45, 30, 15, and 1 day.
Admin Console Alerts
Visual alerts are displayed directly in the Zimbra Admin Console.
-
Alerts appear 30 days before license expiry.
-
Alerts remain visible until the license is renewed.
-
Only visible to users with administrative privileges.
How Pre-Expiry License Notifications Work
Zimbra proactively alerts administrators before a license expires to ensure timely renewal and avoid service disruptions.
Notification Timing
The system starts monitoring for license expiry 90 days before the expiration date.
Alerts are sent at:
-
90 days
-
60 days
-
45 days
-
30 days
-
15 days
-
1 day before expiry
If a notification fails to send (e.g., due to delivery issues), it will be retried the next day.
Daily Check
A background task runs daily at midnight (server local time) to evaluate expiry status and trigger alerts.
Notifications tracking
To prevent duplicate notifications, Zimbra stores alert history in the LDAP attribute:
zimbraLicensePreExpiryReminderSentDetails
{
"category": 90,
"preExpiryMailSentDetails": {
"90": "20250626T032658Z",
"60": "20250619T104011Z"
}
}
What Happens After License Renewal
-
If the new expiry is > 90 days, all alert records are cleared.
-
If new expiry is between 60–89 days, only the 90-day alert record is retained.
This ensures correct future notifications.
Post-License-Expiry System Behavior
When the license expires, the following occurs:
-
Mailstore services are stopped.
-
All Network Edition features are disabled.
-
Admin Console and Modern/Classic Web UI access is blocked.
-
Access via protocols (IMAP, CalDAV, CardDAV, ActiveSync, EWS, ZCO) is disabled.
-
POP access limited to previously downloaded emails.
-
All services (including email delivery, login, backup, restore) stop.
-
Emails are queued. After the "maximal_queue_lifetime" time limit is exhausted, the queued messages are bounced.
|
No past data is lost — services are simply restricted until a valid license is applied. However, continued halting of services could lead to data loss due to overflow of mail queues. |
The LDS service remains active. Admins must ensure it is running to apply license updates post-expiry.
License Renewal After Expiry
For Online Licenses
-
Ensure LDS service is running.
-
As
zimbrauser, run:zmlicense -l -a <license_key>
-
Restart mailbox services:
zmcontrol restart
For Offline Licenses
-
As root, verify offline daemon:
systemctl status nalpdaemon
-
If needed, restart it:
systemctl restart nalpdaemon
-
As
zimbrauser, generate activation certs:zmlicense -l --offlineActivationRequestCert --network <network_key> --product <product_key>
-
Copy the Network Activation Certificate and Product Activation Certificate.
-
Log into Support Portal > License tab. Paste the copied certificates into the respective fields.
-
Provide product version and click Generate License Certificate.
-
Save the generated License Activation XML file and copy it to the mailbox node.
-
Apply the license using:
zmlicense -l -A <Offline_Lic.XML>
-
Restart mailbox services:
zmcontrol restart
Grace Period
Zimbra Daffodil (v10.1.10) onwards, the mailbox server will enter into the Grace Period only in the following scenario:
-
Unavailability of LDS / third-party license server.
-
If the mailbox server loses connection to the License Server for approximately 12 hours, the server will enter a Grace Period.
-
If the LDS node is set up on a dedicated server, and the mailbox node loses connection to it.
-
The server/s will continue to run in the grace period until the connection is established to the LDS / third-party license server or till the expiry date of the license.
Once connectivity is restored, normal license validation resumes.
If the license expires during the Grace Period, services will be disabled as per the license expiry rules.
Functionality in Grace Period
Following functionality is available when the system is in Grace Period:
-
Email Operations - All the email operations will continue to function and there will be no impact or interruption for the end users.
-
Account modification - Users can modify any of the settings for their account. E.g. creating signatures or filters, changing password, etc.
-
Network features - All the network features will continue to function except restoring of an account.
Following functionality is not available when the system is in Grace Period:
-
Account operations:
-
You cannot create a new user or delete an existing user.
-
You cannot modify/update the following features for the existing users - EWS, SMIME, ActiveSync & ZCO
-
You cannot restore the account from a backup.
-
Feature in Grace Period
Zimbra Daffodil (v10.1.1) onwards, if the feature usage exceeds the allowed licensed limit, the feature enters the Grace Period for 10 days. During this time, periodic notifications are sent to the admin for 10 days to notify them of the feature/s in the grace period.
When the feature is in grace period, it cannot be enabled for the new/existing accounts.
If the feature remains in the grace period, then after 10 days, the correction process is triggered, and the overused feature/s are disabled at the account level. The notification emails contain information about the accounts where the feature is disabled.
The following features will go in the grace period after the limit is exceeded:
-
SMIME - Licensed Attribute SMIMEAccountsLimit
-
EWS - Licensed Attribute EwsAccountsLimit
-
MAPI (ZCO) - Licensed Attribute MAPIConnectorAccountsLimit
-
Zimbra Mobile - Licensed Attribute MobileSyncAccountsLimit
Following are the corrective actions to be taken when the feature goes in a grace period:
-
Disable the feature at the account or COS level: For example, the S/MIME feature limit is 10 and the used count is 21. The admin should disable the feature for 11 or more users to get the feature out of the grace period and within licensed limit. Once the feature is within the licensed limit, it will return to a normal state within 24 hours.
-
Increase the license limit: For example, if MAPI’s limit is 10 and the used count is 25, you can contact our sales team and request to increase the licensed limit by 15. Once the limit is updated, the feature will be back to a normal state within 24 hours.
Following are the scenarios where the feature/s can go in grace period:
-
Upgrade to Zimbra Daffodil (v10.1.1) or later:
-
After upgrading to Zimbra Daffodil (v10.1.1) or later, if the feature/s limit exceeds the licensed accounts, the feature will go in grace period.
-
-
Downgrading the licensed limit:
-
If the licensed limit is lowered which causes the feature to exceed the limit, the feature will go in grace period. E.g. The license had a SMIME limit of 100 accounts and you enabled it for 100 accounts. If this limit is lowered to 50 accounts, then the feature will go in grace period.
-
-
Restoring account/s:
-
If you restore the account/s which had feature/s enabled, it may cause to exceed the licensed limit.
-
Notifications
By default, the admin account provided during the installation of the server is set as the notification email. The notification email address is stored in the LDAP attribute zimbraLicenseNotificationEmail and can be changed.
-
As a zimbra user, execute the following:
zmprov mcf zimbraLicenseNotificationEmail newemail@domain.com
The notifications are sent in following scenarios:
-
When the feature limit is exceeded and enters in a grace period.
-
When there is no action taken on the grace period feature and it is disabled for accounts.
-
If the feature is disabled for more than 100 accounts, then the account list is attached in the notification email.
Following is the sample notification email when the feature limit exceeds and it goes in a grace period:
Subject: Zimbra System Alert: Feature(s) usage limit exceeded The licensed number of accounts has been reached or exceeded for the following features: MobileSyncAccountsLimit: - Licensed users:10 - Current users:20 - Usage Exceeded on: 29-August 2024 MAPIConnectorAccountsLimit: - Licensed users:10 - Current users:21 - Usage Exceeded on: 29-August 2024 SMIMEAccountsLimit: - Licensed users:10 - Current users:20 - Usage Exceeded on: 29-August 2024 EwsAccountsLimit: - Licensed users:10 - Current users:20 - Usage Exceeded on: 29-August 2024 You can either reduce the usage of the existing users or increase the feature license limit. To increase the feature license limit, please contact Zimbra Sales at sales@zimbra.com To manage account feature allocation, please sign in to the Admin Portal. Please note the following: 1. You will continue to receive the notification for 10 days from the usage exceeded date. 2. You will not be able to enable the overused feature for any accounts. 3. If you do not take any action on the overused feature, the feature would be disabled for the users to get it under the licensed limit. Regards, Zimbra Support
Following is the sample notification email when no action is taken for a feature/s during grace period and it is disabled for less than 100 accounts:
Subject: Zimbra System Alert: Feature(s) disabled due to exceeded usage The licensed number of accounts has been exceeded and automatically adjusted at the account level for the following features: MobileSyncAccountsLimit - Licensed Users : 10 - Current Users : 14 - Users reduced by : 4 Feature disabled for the following accounts: test10@domain.com test11@domain.com test13@domain.com test14@domain.com EwsAccountsLimit - Licensed Users : 10 - Current Users : 15 - Users reduced by : 5 Feature disabled for the following accounts: test10@domain.com test11@domain.com test12@domain.com test13@domain.com test14@domain.com MAPIConnectorAccountsLimit - Licensed Users : 10 - Current Users : 15 - Users reduced by : 5 Feature disabled for the following accounts: admin@domain.com test10@domain.com test11@domain.com test12@domain.com test13@domain.com To increase the number of licenses, please visit the Zimbra Support Portal. To manage allocation of licenses to accounts, please sign in to the Admin Portal. Regards, Zimbra Support
Following is the sample notification email no action is taken for a feature/s during grace period and it is disabled for more than 100 accounts. The account list is attached in the notification email:
Subject: Zimbra System Alert: Feature(s) disabled due to exceeded usage The licensed number of accounts has been exceeded and automatically adjusted at the account level for the following features: SMIMEAccountsLimit - Licensed Users : 10 - Current Users : 211 - Users reduced by : 201 MAPIConnectorAccountsLimit - Licensed Users : 10 - Current Users : 211 - Users reduced by : 201 To increase the number of licenses, please visit the Zimbra Support Portal. To manage allocation of licenses to accounts, please sign in to the Admin Portal. Regards, Zimbra Support
Usage Prevention
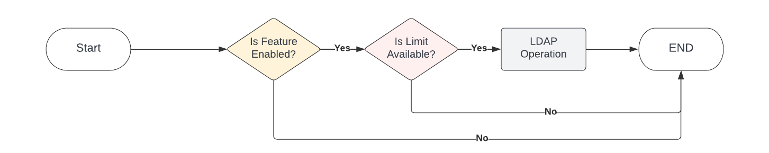
When enabling a feature for an account or a cos, the Usage Prevention module prevents administrators from over provisioning of the features.
The Usage Prevention will be executed for the following features:
-
SMIME - Licensed Attribute SMIMEAccountsLimit
-
EWS - Licensed Attribute EwsAccountsLimit
-
MAPI (ZCO) - Licensed Attribute MAPIConnectorAccountsLimit
-
Zimbra Mobile - MobileSyncAccountsLimit
The Usage Prevention will be executed when doing following actions:
-
Create Account.
-
Modify Account.
-
Modify COS.
Following diagram explains the flow:
Following are the scenarios and their outcome which will be encountered when enabling the feature for an account or a COS:
-
Enabling overused feature - If you want to enable the SMIME feature on a cos that has 120 accounts and the licensed limit for the SMIME feature is 100. The operation will not be allowed as the license limit is exceeded. You will see the following error:
-
COS:
-
Cos Modification Failed : Please disable over used features to proceed, features list : zimbraFeatureSMIMEEnabled
-
Account:
Account Modification Failed : Exceeded limit for following feature(s): zimbraFeatureSMIMEEnabled
-
Enabling non-licensed feature - If you try to enable a feature for a COS/Account which is not licensed, you will see the following error:
-
COS:
-
Cos Modification Failed : Please disable features which are not licensed to use : zimbraFeatureMobileSyncEnabled
-
For Account:
Account Modification Failed : Features are not licensed to use, following feature(s) : zimbraFeatureMobileSyncEnabled
-
Enabling overused and non-licensed feature - When trying to enable a overused feature along with the non-licensed feature for a COS/Account, you will see the following error:
-
COS:
-
Cos Modification Failed : Please disable over used features to proceed, features list : zimbraFeatureSMIMEEnabled Please disable features which are not licensed to use : zimbraFeatureMobileSyncEnabled
-
Account:
Account Modification Failed : Exceeded limit for following feature(s): SMIME Features are not licensed to use, following feature(s) : zimbraFeatureMobileSyncEnabled
Enhanced zmlicense command
Zimbra Daffodil (v10.1) onwards, the License management is real-time and provides the administrator with the overall usage view of the features.
Following are some enhancements along with the existing features of the command
Activate Online License key - zmlicense -a
-
As a zimbra user, execute
zmlicense -a:
$ zmlicense -a <activation-key>
If the activation key is valid, a success message will be displayed else error is displayed.
Activate Offline License XML File - zmlicense -A
-
As a zimbra user, execute
zmlicense -A:
$ zmlicense -A <license-activation-XML>
If the activation key is valid, a success message will be displayed else error is displayed.
Print License Details - zmlicense -p
-
As a zimbra user, execute
zmlicense -p:
$ zmlicense -p Current activated license : 512345113142067890 Activated Product Version : 10.1.0_GA_4629 LDS Device Id : KgQIAuHG5gjU2kKo3VBk Feature : AccountsLimit Status: Authorized for use Max Limit: 10 Used Limit: 1 Feature : ArchivingAccountsLimit Status: Authorized for use Max Limit: 10 Used Limit: 0 Feature : AttachmentIndexingEnabled Status: Authorized for use . . .
Following are the details of the output:
-
Feature : Name of the licensed feature.
-
Status : Whether the licensed feature is entitled for the use or not:
-
Authorized for use - The feature is licensed for use.
-
Not authorized for use - The feature is not licensed for use.
-
-
Max Limit - Maximum number of accounts the feature can be enabled for.
-
Used Limit - The utilized limit of the feature.
Check License status - zmlicense -c
-
As a zimbra user, execute
zmlicense -c:
$ zmlicense -c checking license status. . . Current license code : 53944123451399294, Activation status: License is OK
If the license is valid, a success message will be displayed else error is displayed.
Check individual feature status - zmlicense -fc <feature-code>
Please see the table in License Feature section for feature codes.
-
As a zimbra user, execute
zmlicense -fc:
$ zmlicense -fc AL Feature AccountsLimit[AL] Status: Feature authorized for use
$ zmlicense -fc SHAL Feature SharingAccountsLimit[SHAL] Status: Feature not authorized, contact zimbra support for help.
Refresh license cache - zmlicense -rc
To refresh the license cache on the mailbox (reloading data from the license daemon service), you can use rc option:
-
As a zimbra user, execute
zmlicense -rc:
$ zmlicense -rc refreshing the license cache.. Cache refreshed status : true
License Daemon Service [LDS]
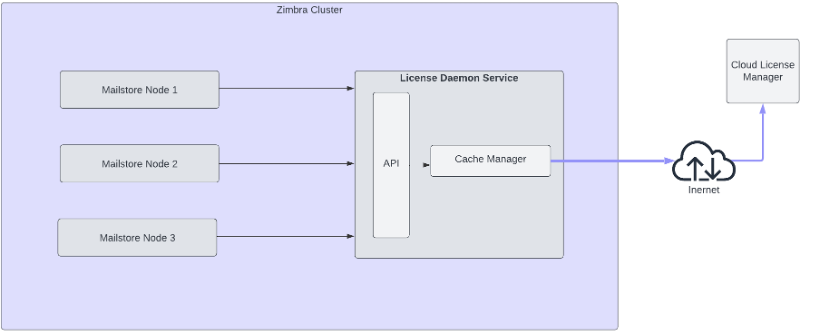
The License Daemon Service (LDS) is a new service that communicates with the Zimbra License Server in online mode and the LAN daemon (local installation) in offline mode.
LDS is responsible for managing license information with Zimbra License Server. During Install/Upgrade, it gets displayed as zimbra-license-daemon in the modules list and is a required service. All real-time licensing operations are carried out through the LDS.
| The license daemon service is a critical and important service for normal functioning of Zimbra and license management. You are recommended to have a service monitoring setup to check the state of the service. |
Overview
-
LDS is a simple Java service that is included when you install Zimbra.
-
It offers an API for managing licenses, like activating them, allocating features for accounts, or releasing them.
-
It is secure because it uses TLS Authentication, and only mailstores can access it.
-
It keeps a local cache of licenses.
-
The LDS is a required service to support the management of the license.
-
If the license daemon service is not installed or not running, Zimbra’s network features will not be able to validate and will be disabled which will affect license functionality and account management.
-
You can use the
zmlicensectlcommand to manage the service.
Following is the architecture view:
System Requirements
LDS is not a resource intensive (CPU / Memory) service.
If it is deployed on a dedicated node, below minimum configurations are required: If deploying on a dedicated node, following are the minimum system requirements:
-
Processor Family: Intel/AMD w/ PassMark CPU Mark > 7,000
-
vCPU count: 2
-
RAM (GB): 8
Ports
Following ports on LDS node should be internally accessible from Mailbox:
| Process | Port |
|---|---|
LDS |
8081 |
Offline LAN daemon |
80 |
Offline pg daemon |
16700 |
Following ports should be externally accessible from LDS to my.nalpeiron.com and license.zimbra.com host:
| Process | Port |
|---|---|
Http |
80 |
Https |
443 |
Installing a separate License Daemon Service node
To separate the license daemon service from rest of the Zimbra services, you can setup a dedicated LDS node. You need to setup this node after upgrading the LDAP server and before you begin to upgrade the Mailbox servers.
The package zimbra-license-daemon gets installed by default during Zimbra installation unless the administrator marks N for the package during Zimbra installation.
Type y and press Enter to install the zimbra-license-daemon package.
Install zimbra-license-daemon [Y]Installing the zimbra-license-daemon package on a separate server
Unpack the Zimbra Daffodil (v10.1) and execute the installer script ./install.sh.
Type y and press Enter to install the zimbra-license-daemon package.
Select the packages to install Install zimbra-ldap [Y] N Install zimbra-logger [Y] N Install zimbra-mta [Y] N Install zimbra-dnscache [Y] N Install zimbra-snmp [Y] N Install zimbra-license-daemon [Y] Y Install zimbra-store [Y] N Install zimbra-apache [Y] N Install zimbra-spell [Y] N Install zimbra-convertd [Y] N Install zimbra-memcached [Y] N Install zimbra-proxy [Y] N Install zimbra-archiving [N] N Install zimbra-onlyoffice [Y] N Install zimbra-patch [Y] N Install zimbra-mta-patch [Y] N Install zimbra-proxy-patch [Y] N
Complete the rest of the installation.
Setting up Mailbox Server
After the installation of the LDS Node is successfully completed, you can now install/upgrade the Mailbox servers.
Unpack the Zimbra Daffodil (v10.1) and execute the installer script ./install.sh.
If upgrading an existing mailbox server, provide a valid license key when prompted and continue till the package selection step.
ZCS upgrade from 8.8.15 to 10.1.0 will be performed. Validating whether an existing license is expired or not and checking if it qualifies for an upgrade Please enter the license key (an alphanumeric string of 18-24 characters without any special characters):5332567329720607741 SUCCESS: License valid License is valid and supports this upgrade. Continuing. Validating ldap configuration
You can also specify the license key with the ./install.sh command. If the validation is successful, the installer will continue:
./install.sh --licensekey 5332567329720607741
If installing a new mailbox server, continue till the package selection step.
-
Following are the steps to setup mailbox server to use the dedicated LDS node:
-
Select
NInstall zimbra-license-daemonInstall zimbra-license-daemon [Y] N
-
Installer will show the following prompt. Enter Y
Have you installed zimbra-license-daemon package on different node [N] Y
-
Installer will prompt to enter the host where the LDS is installed. Specify the LDS hostname:
Please enter the zimbra-license-daemon host [] <LDS_Hostname>
-
If LDS is running on server, the installation will continue.
-
In case the server failed to connect the LDS, the installer will display the
license-daemon should be running and healthyand abort the installation. Please review the connection to the server and restart the installation. Refer to Troubleshooting section for common errors and its solution.
-
LDS Management command zmlicensectl
A new command zmlicensectl has been introduced to manage the various operations for LDS.
Since the license daemon service is a critical and important service, this is not managed through the zmcontrol command. The zmcontrol command will show the status but you cannot start/stop/restart the LDS.
|
Following are the details on the options:
| Operations | Parameter | Description |
|---|---|---|
Display Help |
--help |
Display Help |
Service Management |
--service <arg> |
Manage various operations |
--service start, restart, stop, status |
Start, Restart, Stop or Check the service status |
|
--service setLogLevel=INFO,DEBUG,ERROR,WARN |
Set the various log levels. Helpful for debugging. |
|
--service setOfflineMode=true,false |
Enable/disable the offline mode |
|
Offline Service Management |
--nalpeiron <arg> |
When Offline License mode is enabled, this parameters is used to manage the offline service |
--nalpeiron start, restart, stop, status |
Start, Restart, Stop or Check the offline service status |
|
Export offline Data |
--exportOfflineLicenseData |
Extracts offline license usage data for analysis and billing |
Clear license directory |
--clearLicenseWorkDir |
A troubleshooting option for resolving potential license caching issues on LDS |
Example:
-
To restart the LDS, execute the command as
zimbrauser:
zmlicensectl --service restart
-
To set the log level in debug mode, execute the command as
zimbrauser:
zmlicensectl --service setLogLevel=DEBUG
-
To change the license mode from Online to Offline, execute the command as
zimbrauser:
zmlicensectl --service setOfflineMode=true
-
To restart the LAN daemon required for offline mode, execute the command as
zimbrauser:
zmlicensectl --nalpeiron restart
-
To export the Offline Usage data (required only for BSP’s), execute the command as
zimbrauser:
zmlicensectl --exportOfflineLicenseData
Troubleshooting
Logging
Following are the logs where all the licensing operations are logged:
-
Mailstore Logs:
-
Contains logs for the mailstore operations
-
Location: /opt/zimbra/log/mailbox.log
-
-
License Daemon Service logs
-
Contains logs relate to API communication between mailstore and LDS
-
Location: /opt/zimbra/log/license-daemon-service.log
-
-
Native Library Logs
-
Contains library errors occurred while communicating to nalpeiron server.
-
Location: /opt/zimbra/license/work/15xx.log
-
License Daemon Service logs
The file logging mechanism for LDS has been enhanced with a rolling policy that manages log files based on size and time. This ensures that logs are stored efficiently and that older logs are archived or deleted based on defined criteria.
Following are the details:
-
File Location: /opt/zimbra/log/license-daemon-service.log
-
Log Format: Logs include timestamp, thread name, log level, and message. e.g.
2024-08-01 10:11:03 [main] INFO c.zimbra.license.service.Application - The following 1 profile is active: "dev"
-
History Management: Maintains a history of log files for a specified number of days. Log files are retained for up to 15 days. Files older than 15 days are automatically deleted to adhere to the retention policy.
-
Size Cap: The total size of all log files combined will not exceed 5 gigabytes (GB). Once this limit is reached, older log files will be deleted to make room for new ones.
-
Size-Based Rolling: Log files are rotated when they reach a specified maximum size(max limit: 500 MB).This means each log file will be limited to 500 MB before a new file is created.
-
Time-Based Rolling: The time-based rolling configuration ensures that log files are organized by date and that a new log file is created for each day.
-
Time-Size Based Rolling
-
Daily Files:
-
Daily Creation: Each day, a new log file is created with the base name license-daemon-service.log. For example, logs for September 1, 2024, will be saved in a file named license-daemon-service.log.
-
End of Day Rolling: At the end of the day, the log file is rolled over and renamed with a date stamp in the format YYYY-MM-DD. For instance, the logs for September 1, 2024, will be saved as license-daemon-service-2024-09-01.0.log. If the file is rolled over multiple times within the day, subsequent files will be numbered sequentially, e.g., license-daemon-service-2024-09-01.1.log, license-daemon-service-2024-09-01.2.log, etc.
Accessing Logs:
-
Current Day Logs: To access the log file for the current day, you can use the command tail -f /opt/zimbra/log/license-daemon-service.log.
-
Previous Day Logs: To access logs from the previous day, you should use the date-stamped log file. For instance, logs from September 1, 2024, would be accessed with cat /opt/zimbra/log/license-daemon-service-2024-09-01.0.log.
File Indexing:
-
Sequential Numbering: If multiple log files are generated within the same day due to exceeding the maximum file size (maxFileSize), the files are sequentially numbered. For example,
license-daemon-service-2024-09-01.0.log license-daemon-service-2024-09-01.1.log license-daemon-service-2024-09-01.2.log
Error conditions/codes
There might be scenarios where you encounter various license errors/code or specific errors.
Following are some of the common scenarios and their resolution:
License Activation Failed:
-
license-daemon should be running and healthyerror when mailstore trying to connect to LDS:-
Make sure LDS is up and running.
-
Check status -
zmlicensectl --service status -
If not running, Restart the service -
zmlicensectl --service restart
-
-
Failed to activate License:
-
Make sure LDS node have internet access.
-
-
Invalid License error with code “4001”:
-
Verify license is not expired.
-
-
Invalid license error with code “-10116”:
-
Check Account has valid support end date.
-
-
Invalid license error with code “-5000”:
-
Support end date might be empty.
-
-
Invalid license error with code “-401”:
-
License activation restricted or license inactive.
-
-
Invalid license error with error code “4000”:
-
License usage are not valid. May happen if you are trying to change the license.
-
-
Invalid license error with code “4002”:
-
Trial cannot be activated on regular license setup.
-
Feature Check Failed:
-
Make sure LDS is up and running -
zmlicensectl --service status-
If not running, restart the LDS service -
zmlicensectl --service restart
-
-
Failed to use server level features such as Backup Restore, Storage Management, etc.
-
Make sure feature is authorized to use -
zmlicense -fc <feature_code>** If it is enabled, then restart the mailbox -zmmailboxdctl restart
-
-
Failed to enabled feature on account/cos:
-
Make sure feature is authorized to use -
zmlicense -fc <feature_code> -
If feature is of type limit, then make sure you have sufficient limit available -
zmlicense -p | grep -E '(EwsAccountsLimit)' -A3 -
If feature is of type limit, then make sure you have sufficient limit available -
zmlicense -p | grep -E '(EwsAccountsLimit)' -A3
-
Zimbra Mailbox Server
The Zimbra mailbox server is a dedicated server that manages all the mailbox content, including messages, contacts, calendar, and attachments.
The Zimbra mailbox server has dedicated volumes for backup and log files. Each Zimbra mailbox server can see only its own storage volumes. Zimbra mailbox servers cannot see, read, or write to another server.
Mailbox Server
Each account is configured on one mailbox server, and this account is associated with a mailbox that contains email messages, attachments, calendar, contacts and collaboration files for that account.
Each mailbox server has its own standalone message store, data store, and index store for the mailboxes on that server. The following is an overview of each store and their directory location.
Message Store
All email messages are stored in MIME format in the Message Store, including the message body and file attachments.
By default, the message store is located on each mailbox server under
/opt/zimbra/store. Each mailbox has its own directory named after its
internal mailbox ID. Mailbox IDs are unique per server, not system-wide.
Messages with multiple recipients are stored as a single -copy on the message store. On UNIX systems, the mailbox directory for each user contains a hard link to the actual file.
When Zimbra Collaboration is installed, one index volume and one message volume are configured on each mailbox server. Each mailbox is assigned to a permanent directory on the current index volume. When a new message is delivered or created, the message is saved in the current message volume.
To manage your email storage resources, you can configure storage volumes for older messages by implementing a Storage Management (SM) policy. See Managing Configuration.
Data Store
The Data Store is a SQL database where internal mailbox IDs are
linked with user accounts. All the message metadata including tags,
conversations, and pointers indicate where the messages are stored in
the file system. The SQL database files are located in
/opt/zimbra/db.
Each account (mailbox) resides only on one server. Each server has its own standalone data store containing data for the mailboxes on that server.
-
The data store maps the mailbox IDs to the users' LDAP accounts. The primary identifier within the Zimbra Collaboration database is the mailbox ID, rather than a user name or account name. The mailbox ID is only unique within a single mailbox server.
-
Metadata including user’s set of tag definitions, folders, contacts, calendar appointments, tasks, Briefcase folders, and filter rules are in the data store database.
-
Information about each mail message, including whether it is read or unread, and which tags are associated is stored in the data store database.
Index Store
The index and search technology is provided through Apache Lucene. Each
email message and attachment is automatically indexed when the message
arrives. An index file is associated with each account. Index files are
located in /opt/zimbra/index.
The tokenizing and indexing process is not configurable by administrators or users.
The process is as follows:
-
The Zimbra MTA routes the incoming email to the mailbox server that contains the account’s mailbox.
-
The mailbox server parses the message, including the header, the body, and all readable file attachments such as PDF files or Microsoft Word documents, in order to tokenize the words.
-
The mailbox server passes the tokenized information to Lucene to create the index files.
| Tokenization is the method for indexing by each word. Certain common patterns, such as phone numbers, email addresses, and domain names are tokenized as shown in the Message Tokenization illustration. |
Web Application Server
The Jetty web application server runs web applications (webapps) on any store server. It provides one or more web application services.
Mailstore Services
Mailstore services provides the back-end access to mailbox/account data. Webapps for the mailstore include:
-
Mailstore (mail server) =
/opt/zimbra/jetty/webapps/service -
Zimlets =
/opt/zimbra/jetty/webapps/zimlet
User Interface Services
User Interface services provide front-end user interface access to the mailbox account data and Administration Console, including:
-
Web Apps =
/opt/zimbra/jetty/webapps/zimbra -
Zimbra administrator console =
/opt/zimbra/jetty/webapps/zimbraAdmin -
Zimlets =
/opt/zimbra/jetty/webapps/zimlet
Backing Up the Mailbox Server
Zimbra Collaboration includes a configurable backup manager that resides on
every Zimbra Collaboration server and performs both backup and restore
functions. You do not have to stop the Zimbra Collaboration server in order
to run the backup process. The backup manager can be used to restore a
single user, rather than having to restore the entire system in the event
that one user’s mailbox becomes corrupted. Full and incremental backups are
in /opt/zimbra/backup.
See Backup and Restore.
Each Zimbra mailbox server generates redo logs that contain current and archived transactions processed by the message store server since the last incremental backup. When the server is restored, after the backed up files are fully restored, any redo logs in the archive and the current redo log in use are replayed to bring the system to the point before the failure.
Mailbox Server Logs
A Zimbra Collaboration deployment consists of various third-party
components with one or more mailbox servers. Each of the components may
generate its own logging output. Local logs are in /opt/zimbra/log.
Selected Zimbra Collaboration log messages generate SNMP traps, which you can capture using any SNMP monitoring software. See Monitoring Zimbra Servers.
| System logs, redo logs, and backup sessions should be on separate disks to minimize the possibility of unrecoverable data loss in the event that one of those disks fails. |
IMAP
Zimbra Collaboration has a built-in IMAP server which is installed by default and is part of zimbra-mailboxd process (Zimbra Mailbox Server).
Common IMAP Configuration settings
The following global and server level configuration attributes are available to control and tune the IMAP service.
-
zimbraImapServerEnabled. When set to TRUE, in-process IMAP server is enabled. When set to FALSE, in-process IMAP server is disabled. Default value is TRUE.
-
zimbraImapSSLServerEnabled. When set to TRUE, in-process IMAP SSL server is enabled. When set to FALSE, in-process IMAP SSL server is disabled. Default value is TRUE
-
zimbraImapBindAddress (can be set only on server level). Specifies interface address on which in-process IMAP server should listen; if empty, binds to all interfaces.
-
zimbraImapBindPort. Specifies port number on which in-process IMAP server should listen. Default value is 7143.
-
zimbraImapSSLBindAddress (can be set only on server level). Specifies interface address on which in-process IMAP SSL server should listen; if empty, binds to all interfaces.
-
zimbraImapSSLBindPort. Specifies port number on which in-process IMAP SSL server should listen on. Default value is 7993.
-
zimbraImapNumThreads. Specifies number of threads in IMAP handler’s thread pool. Zimbra Collaboration uses IMAP NIO by default, which allows each IMAP handler thread to handle multiple connections. The default value of 200 is sufficient to handle up to 10,000 active IMAP clients.
-
zimbraImapCleartextLoginEnabled. Specifies whether or not to allow cleartext logins over a non SSL/TLS connection. Default value is FALSE.
-
zimbraImapProxyBindPort. Specifies port number on which IMAP proxy server should listen. Default value is 143. See Zimbra Proxy Components for more information.
-
zimbraImapSSLProxyBindPort. Specifies port number on which IMAP SSL proxy server should listen. Default value is 993. See Zimbra Proxy Components for more information.
-
zimbraImapMaxRequestSize. Specifies maximum size of IMAP request in bytes excluding literal data. Note: this setting does not apply to IMAP LOGIN requests. IMAP LOGIN requests are handled by IMAP Proxy (Zimbra Proxy Components) and are limited to 256 characters.
-
zimbraImapInactiveSessionCacheMaxDiskSize. Specifies the maximum disk size of inactive IMAP cache in Bytes before eviction. By default this value is 10GB. This is a rough limit, because due to internals of Ehcache actual size on disk will often exceed this limit by a modest margin.
-
zimbraImapInactiveSessionEhcacheSize. Specifies the maximum heap size of the inactive session cache in Bytes before eviction. By default this value is 1 megabyte. This is a rough limit, because due to internals of Ehcache actual size in memory will often exceed this limit by a modest margin.
-
zimbraImapActiveSessionEhcacheMaxDiskSize. Specifies the maximum amount of disk space the imap active session cache will consume in Bytes before eviction. By default this value is 100 gigabytes. This is a rough limit, because due to internals of ehcache actual size in memory will often exceed this limit by a modest margin.
Zimbra LDAP Service
LDAP directory services provide a centralized repository for information about users and devices that are authorized to use your Zimbra service. The central repository used for Zimbra’s LDAP data is the OpenLDAP directory server.
| Zimbra Collaboration supports integration with Microsoft’s Active Directory Server. Contact support for information on specific directory implementation scenarios. |
The LDAP server is installed when Zimbra is installed. Each server has its own LDAP entry that includes attributes specifying operating parameters. In addition, a global configuration object sets defaults for any server whose entry does not specify every attribute.
A subset of these attributes can be modified through the Zimbra administration console and others through the zmprov commands.
LDAP Traffic Flow
The LDAP Directory Traffic figure shows traffic between the Zimbra-LDAP directory server and the other servers in the Zimbra Collaboration system. The Zimbra MTA and the Zimbra Collaboration mailbox server read from, or write to, the LDAP database on the directory server.
The Zimbra clients connect through the Zimbra server, which connects to LDAP.
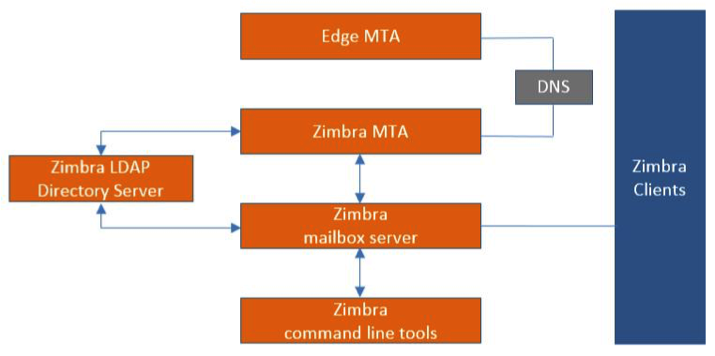
LDAP Directory Hierarchy
LDAP directories are arranged in an hierarchal tree-like structure with two types of branches, the mail branches and the config branch. Mail branches are organized by domain. Entries belong to a domain, such as accounts, groups, aliases, are provisioned under the domain DN in the directory. The config branch contains admin system entries that are not part of a domain. Config branch entries include system admin accounts, global config, global grants, COS, servers, mime types, and Zimlets.
The Zimbra LDAP Hierarchy figure shows the Zimbra LDAP hierarchy. Each type of entry (object) has certain associated object classes.
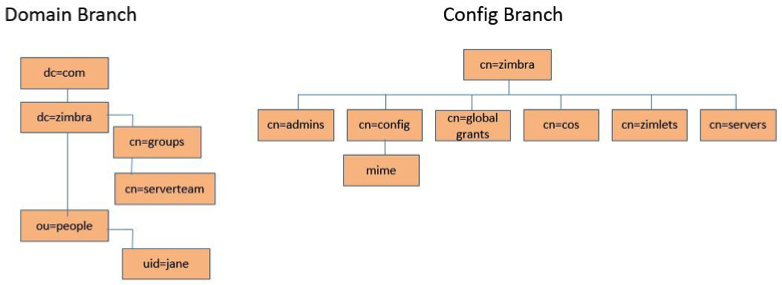
An LDAP directory entry consists of a collection of attributes and has a
globally unique distinguished name (dn). The attributes allowed for an
entry are determined by the object classes associated with that entry.
The values of the object class attributes determine the schema rules the
entry must follow.
An entry’s object class that determines what kind of entry it is, is called a structural object class and cannot be changed. Other object classes are called auxiliary and may be added to or deleted from the entry.
Use of auxiliary object classes in LDAP allows for an object class to be combined with an existing object class. For example, an entry with structural object class inetOrgPerson, and auxiliary object class zimbraAccount, would be an account. An entry with the structural object class zimbraServer would be a server in the Zimbra system that has one or more Zimbra packages installed.
Zimbra Collaboration LDAP Schema
At the core of every LDAP implementation is a database organized using a schema.
The Zimbra LDAP schema extends the generic schema included with OpenLDAP software. It is designed to coexist with existing directory installations.
All attributes and object classes specifically created for Zimbra Collaboration
are prefaced by “zimbra”, such as zimbraAccount object class or
zimbraAttachmentsBlocked attribute.
The following schema files are included in the OpenLDAP implementation:
-
core.schema
-
cosine.schema
-
inetorgperson.schema
-
zimbra.schema
-
amavisd.schema
-
dyngroup.schema
-
nis.schema
| You cannot modify the Zimbra schema. |
Zimbra Collaboration Objects
| Object | Description | Object class | ||
|---|---|---|---|---|
Accounts |
Represents an account on the Zimbra mailbox server that can be logged into.
Account entries are either administrators or user accounts.
The object class name is zimbraAccount.
This object class extends the zimbraMailRecipient object class.
|
zimbraAccount |
||
Class of Service (COS) |
Defines the default attributes an account has and what features are allowed or denied. The COS controls features, default preference settings, mailbox quotas, message lifetime, password restrictions, attachment blocking, and server pools for creation of new accounts. |
zimbraCOS |
||
Domains |
Represents an email domain such as example.com or example.org. A domain must exist before email addressed to users in that domain can be delivered. |
zimbraDomain |
||
Distribution Lists |
Also known as mailing lists, are used to send mail to all members of a list by sending a single email to the list address. |
zimbraDistributionList |
||
Dynamic Groups |
Are like distribution lists. The difference is members of a dynamic group are dynamically computed by a LDAP search. The LDAP search filter is defined in an attribute on the dynamic group entry.
|
zimbraGroup |
||
Servers |
Represents a particular server in the Zimbra system that has one or more of the Zimbra software packages installed. Attributes describe server configuration information, such as which services are running on the server. |
zimbraServer |
||
Global Configuration |
Specifies default values for the following objects: server and domain. If the attributes are not set for other objects, the values are inherited from the global settings. Global configuration values are required and are set during installation as part of the Zimbra core package. These become the default values for the system. |
zimbraGlobalConfig |
||
Alias |
Represents an alias of an account, distribution list or a dynamic group. The zimbraAliasTarget attribute points to target entry of this alias entry. |
zimbraAlias |
||
Zimlet |
Defines Zimlets that are installed and configured in Zimbra. |
zimbraZimletEntry |
||
Calendar Resource |
Defines a calendar resource such as conference rooms or equipment that can be selected for a meeting. A calendar resource is an account with additional attributes on the zimbraCalendarResource object class. |
zimbraCalendarResource |
||
Identity |
Represents a persona of a user. A persona contains the user’s identity such as display name and a link to the signature entry used for outgoing emails. A user can create multiple personas. Identity entries are created under the user’s LDAP entry in the DIT. |
zimbraIdentity |
||
Data Source |
Represents an external mail source of a user. Two examples of data source are POP3 and IMAP. A data source contains the POP3/IMAP server name, port, and password for the user’s external email account. The data source also contains persona information, including the display name and a link to the signature entry for outgoing email messages sent on behalf of the external account. Data Source entries are created under the user’s LDAP entry in the DIT. |
zimbraDataSource |
||
Signature |
Represents a user’s signature. A user can create multiple signatures. Signature entries are created under the user’s LDAP entry in the DIT. |
zimbraSignature |
Account Authentication
Supported authentication mechanisms are Internal, External LDAP, and
External Active Directory. The authentication method type is set on a
per-domain basis. If zimbraAuthMech attribute is not set, the default is
to use internal authentication.
The internal authentication method uses the Zimbra schema running on the OpenLDAP server.
The zimbraAuthFallbackToLocal attribute can be enabled so that the system
falls back to the local authentication if external authentication fails.
The default is FALSE.
Internal Authentication Mechanism
The internal authentication method uses the Zimbra schema running on the
OpenLDAP directory server. For accounts stored in the OpenLDAP server, the
userPassword attribute stores a salted-SHA512 (SSHA512) digest of the user’s
password. The user’s provided password is computed into the SSHA digest
and then compared to the stored value.
External LDAP and External AD Authentication Mechanism
External LDAP and external Active Directory authentication can be used if the email environment uses another LDAP server or Microsoft Active Directory for authentication and Zimbra LDAP for all other Zimbra Collaboration related transactions. This requires that users exist in both OpenLDAP and in the external LDAP server.
The external authentication methods attempt to bind to the specified LDAP server using the supplied user name and password. If this bind succeeds, the connection is closed and the password is considered valid.
The zimbraAuthLdapURL and zimbraAuthLdapBindDn attributes are required
for external authentication.
-
zimbraAuthLdapURLattributeldap://ldapserver:port/identifies the IP address or host name of the external directory server, and port is the port number. You can also use the fully qualified host name instead of the port number.For example:
ldap://server1:3268 ldap://exch1.acme.com
If it is an SSL connection, use
ldaps:instead ofldap:. The SSL certificate used by the server must be configured as a trusted certificate. -
zimbraAuthLdapBindDnattribute is a format string used to determine which DN to use when binding to the external directory server.During the authentication process, the user name starts out in the format: user@example.com
The user name might need to be transformed into a valid LDAP bind
DN(distinguished name) in the external directory. In the case of Active Directory, that binddnmight be in a different domain.
Custom Authentication
You can implement a custom authentication to integrate external authentication to your proprietary identity database. When an authentication request comes in, Zimbra checks the designated auth mechanism for the domain. If the auth mechanism is set to custom authentication, Zimbra invokes the registered custom auth handler to authenticate the user.
To set up custom authentication, prepare the domain for the custom auth and register the custom authentication handler.
Preparing a domain for custom auth
To enable a domain for custom auth, set the domain attribute, zimbraAuthMech to custom:{registered-custom-auth-handler-name}.
In the following example, "sample" is the name under which custom authentication is registered.
zmprov modifydomain {domain|id} zimbraAuthMech custom:sampleRegister a custom authentication handler
To register a custom authentication handler, invoke:
ZimbraCustomAuth.register( handlerName, handler )in the init method of the extension.
-
Class: com.zimbra.cs.account.ldap.ZimbraCustomAuth
-
Method:
public synchronized static void register (String handlerName, ZimbraCustomAuth handler)Definitions:
-
handlerName is the name under which this custom auth handler isregistered to Zimbra’s authentication infrastructure. This name is set in the domain’s zimbraAuthMech attribute of the domain.
-
handler is the object on which the authenticate method is invoked forthis custom auth handler. The object has to be an instance of
ZimbraCustomAuth(or subclasses of it).
-
public class SampleExtensionCustomAuth implements ZimbraExtension {
public void init() throws ServiceException {
/*
* Register to Zimbra's authentication infrastructure
* custom:sample should be set for domain attribute zimbraAuthMech
*/
ZimbraCustomAuth.register("sample", new SampleCustomAuth());
}
...
}How Custom Authentication Works
When an authentication request comes in and the domain is specified to use custom authentication, the authenticating framework invokes the authenticate method on the ZimbraCustomAuth instance passed as the handler parameter to ZimbraCustomAuth.register().
The account object for the principal to be authenticated and the clear-text password entered by the user are passed to ZimbraCustomAuth.authenticate().
All attributes of the account can be retrieved from the account object.
Kerberos5 Authentication Mechanism
Kerberos5 Authentication Mechanism authenticates users against an external Kerberos server.
-
Set the domain attribute
zimbraAuthMechtokerberos5. -
Set the domain attribute
zimbraAuthKerberos5Realmto the Kerberos5 realm in which users in this domain are created in the Kerberos database. When users log in with an email password and the domain,zimbraAuthMechis set tokerberos5, the server constructs the Kerberos5 principal by{localpart-of-the-email}@{value-of-zimbraAuthKerberos5Realm}and uses that to authenticate to the kerberos5 server.
To specify Kerberos5 for an individual account set the account’s
zimbraForeignPrincipal as kerberos5:{kerberos5-principal}. For
example: kerberos5:user1@MYREALM.COM.
Global Address List
The Global Address List (GAL) is a company directory of users, usually within the organization itself, that is available to all users of the email system. Zimbra Collaboration uses the company directory to look up user addresses from within the company.
For each Zimbra Collaboration domain you can configure GAL to use:
-
External LDAP server
-
Zimbra Collaboration internal LDAP server
-
Both external LDAP server and Zimbra Collaboration LDAP in GAL searches
The Zimbra Collaboration Web Client can search the GAL. When the user searches
for a name, that name is turned into an LDAP search filter similar to the
following example, where the string %s is the name the user is searching
for.
(|(cn = %s*)(sn=%s*)(gn=%s*)(mail=%s*))
(zimbraMailDeliveryAddress = %s*)
(zimbraMailAlias=%s*)
(zimbraMailAddress = %s*)GAL Attributes in Zimbra Collaboration
The Attributes Mapped to Zimbra Collaboration Contact table maps generic GAL search attributes to their Zimbra Collaboration contact fields.
LDAP attributes are mapped to GAL entry fields. For example, the LDAP
attribute displayName and cn can be mapped to GAL entry field fullName.
The mapping is configured in the zimbraGalLdapAttrMap attribute.
| Standard LDAP Attribute | Zimbra Collaboration Contact Field |
|---|---|
|
workCountry |
|
Company |
|
firstName |
|
lastName |
|
fullName |
|
initials |
|
workCity |
|
workStreet |
|
workPostalCode |
|
workPhone |
|
mobile |
|
pager |
|
faxNumber |
|
workState |
|
jobTitle |
|
|
|
thumbnailPhoto |
|
Not currently mapped |
Zimbra Collaboration GAL Search Parameters
GAL is configured on a per-domain basis. To configure the attributes, you can run the GAL Configuration Wizard from the Administration Console.
Modifying Attributes
Additions, changes and deletions to the GAL attributes are made through the
Zimbra Administration Console or from the zmprov commands.
Users can modify attributes for their account in the directory. When users change their options from the Zimbra Classic Web App, they also modify the attributes when they change their preferences.
Flushing LDAP Cache
When you modify the following type of entries in the Zimbra LDAP server, you might need to flush the LDAP cache to make the change available on the server.
-
Themes
-
Locales
-
Account
-
Groups
-
COS
-
Domains
-
Global configuration
-
Server
-
Zimlet configuration
Flush the Cache for Themes and Locales
When you add or change theme (skin) property files and locale resource files for Zimbra on a server, you must flush the cache to make the new content available.
zmprov flushCache skinzmprov flushCache localeFlush Accounts, Groups, COS, Domains, and Servers
When you modify the account, COS, groups, domain, and server attributes, the change is effective immediately on the server to which the modification is done. On the other servers, the LDAP entries are automatically updated after a period of time if the attributes are cached.
The default Zimbra setting to update the server is 15 minutes. The caching period is configured on local config key.
zmlocalconfig ldap_cache_<object>_maxagezmprov flushCache {account|cos|domain|group|server|...} [name|id]...If you do not specify a name or ID along with the type, all entries in cache for that type are flushed and the cache is reloaded.
| Some server attributes require a server restart even after the cache is flushed. For example, settings like bind port or number of processing threads. |
Flush Global Attributes
When you modify global config attributes, the changes are effective immediately on the server to which the modification is done. On other mailbox servers, you must flush the cache to make the changes available or restart the server. LDAP entries for global config attributes do not expire.
Some global config attributes are computed into internal representations only once per server restart. For efficiency reasons, changes to those attributes are not effective until after a server restart, even after the cache is flushed. Also, some global configuration settings and server settings that are inherited from global config are only read once at server startup, for example port or number of processing threads. Modifying these types of attributes requires a server restart.
To flush the cache for global config changes on all servers:
-
Modify the setting on the local server
zmprov mcf zimbraImapClearTextLoginEnabled TRUEThe change is performed via the server identified by the localconfig keys
zimbra_zmprov_default_soap_serverandzimbra_admin_service_port. -
To flush the global config cache on all other servers,
zmprov flushCachemust be issued on all servers, one at a time (or usezmprov flushCache -a).For example:
zmprov –s server2 flushCache config zmprov –s server3 flushCache config -
To determine if the action requires a restart
zmprov desc -a <attributename>The
requiresRestartvalue is added to the output if a restart is required.
Zimbra Mail Transfer Agent
The Zimbra MTA (Mail Transfer Agent) receives mail via SMTP and routes each message using Local Mail Transfer Protocol (LMTP) to the appropriate Zimbra mailbox server.
| You can set MTA parameters with the Admin Console and the CLI. However, it is highly recommended that you use the CLI for MTA configuration to ensure the best results. |
The Zimbra MTA server includes the following programs:
| MTA Server Programs | Purpose/Description |
|---|---|
Postfix MTA |
Mail routing, mail relay, and attachment blocking |
Clam Anti-Virus |
Scanning email messages and attachments in email messages for viruses |
Spam Assassin |
Identify unsolicited commercial email (spam) |
Amavisd-New |
Interface between Postfix and ClamAV / SpamAssassin |
Zimbra Milter Server |
Enforce restrictions on which addresses can send to distribution lists and adds Reply-To and X-Zimbra-DL headers to messages sent from distribution lists |
Zimbra policy server |
Aid in protecting Alias Domains from Backscatter Spam |
Cluebringer |
Policy daemon/cbpolicyd used to enforce actions, such as rate limiting. For more information, see https://wiki.zimbra.com/wiki/Postfix_Policyd |
Opendkim |
Sign outgoing email if it has been configured to do so. For more information, see https://wiki.zimbra.com/wiki/Configuring_for_DKIM_Signing |
In the Zimbra Collaboration configuration, mail transfer and delivery are distinct functions: Postfix acts as a MTA, and the Zimbra mail server acts as a Mail Delivery Agent (MDA).
The MTA configuration is stored in LDAP. The zmconfigd process polls the
LDAP directory every two minutes for modifications and updates the
Postfix configuration files with the changes.
Incoming Mail Routing Overview
The Zimbra mailbox server receives the messages from the Zimbra MTA server and passes them through any filters that have been created.
The MTA server receives mail via SMTP and routes each mail message to the appropriate mailbox server using LMTP. As each mail message arrives, its contents are indexed so that all elements can be searched.
Zimbra MTA Deployment
Zimbra includes a precompiled version of Postfix to route and relay mail and manage attachments. Postfix receives inbound messages via SMTP, performs anti-virus and anti-spam filtering and hands off the mail messages to the Zimbra Collaboration server via LMTP.
Postfix also plays a role in transferring outbound messages. Messages composed from the Zimbra Classic Web App are sent by the Zimbra server through Postfix, including messages sent to other users on the same server.
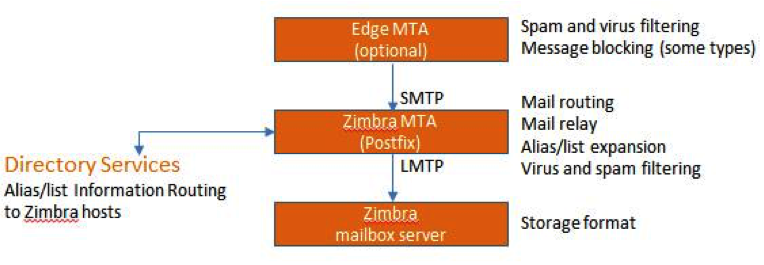
| The Edge MTA can be any edge security solution for mail. You might already deploy such solutions for functions such as filtering. Some filtering might be duplicated between an edge MTA and the Zimbra MTA. |
Postfix Configuration Files
Zimbra modified Postfix files — main.cf and master.cf — specifically to work with Zimbra:
-
main.cf — Modified to include the LDAP tables. The
zmconfigdin the Zimbra MTA pulls data from the Zimbra LDAP and modifies the Postfix configuration files. -
master.cf — Modified to use Amavisd-New.
| Changes made to postfix configuration files will be overwritten with every upgrade and should be well documented. If possible, try to implement any necessary configuration changes using Zimbra defined parameters. |
SMTP Authentication
SMTP authentication allows authorized mail clients from external networks to relay messages through the Zimbra MTA. The user ID and password is sent to the MTA when the SMTP client sends mail so that the MTA can verify if the user is allowed to relay mail.
The user ID and password is sent to the MTA when the SMTP client sends mail. This ensures that the MTA can verify if the user is allowed to relay mail, by checking the associated credentials with the LDAP account.
| User authentication is provided through the Zimbra LDAP directory server, or if implemented, through the Microsoft Active Directory Sever. |
SMTP Restrictions
You can enable restrictions so that messages are not accepted by Postfix when non-standard or other disapproved behavior is exhibited by an incoming SMTP client. These restrictions provide some protection against spam senders. By default, clients that do not greet with a fully qualified domain name are restricted. DNS based restrictions are also available.
| Understand the implications of these restrictions before you implement them. You might have to compromise on these checks to accommodate people outside of your system who have poorly implemented mail systems. |
Sending Non Local Mail to a Different Server
You can configure Postfix to send nonlocal mail to a different SMTP server, commonly referred to as a relay or smart host.
A common use case for a relay host is when an ISP requires that all your email be relayed through a designated host, or if you have filtering SMTP proxy servers.
The relay host setting must not be confused with Web mail MTA setting. Relay host is the MTA to which Postfix relays non-local email. Webmail MTA is used by the Zimbra server for composed messages and must be the location of the Postfix server in the Zimbra MTA package.
To use the Administration Console to configure Relay MTA for external delivery:
- Admin Console:
-
Home → Configure → Global Settings → MTA → Network
| To prevent mail loops, use caution when setting the relay host. |
Anti-Virus and Anti-Spam Protection
The Amavisd-New utility is the interface between the Zimbra MTA and Clam Anti-Virus (ClamAV) and SpamAssassin scanners.
Anti-Virus Protection
ClamAV software is the virus protection engine enabled for each Zimbra server.
The anti-virus software is configured to put messages that have been identified as having a virus to the virus quarantine mailbox. By default, the Zimbra MTA checks every two hours for any new anti-virus updates from ClamAV.
You can change anti-virus settings at the Administration Console.
- Admin Console:
-
Home → Configure → Global Settings → AS/AV → Anti-virus Settings
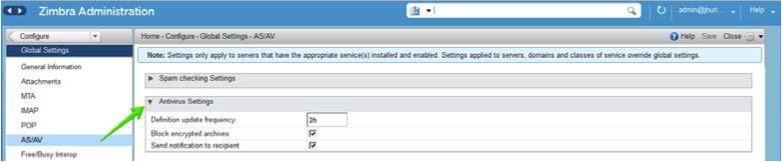
| Updates are obtained via HTTP from the ClamAV website. |
Scanning Attachments in Outgoing Mail
You can enable real-time scanning of attachments in outgoing emails sent using the Zimbra Classic Web App. If enabled, when an attachment is added to an email, it is scanned using ClamAV prior to sending the message. If ClamAV detects a virus, it will block attaching the file to the message. By default, scanning is configured for a single node installation.
To enable scanning, using a single node:
zmprov mcf zimbraAttachmentsScanURL clam://localhost:3310/
zmprov mcf zimbraAttachmentsScanEnabled TRUETo enable scanning in a multi-node environment:
-
Designate the MTA nodes to handle ClamAV scanning.
-
Enable, as follows:
zmprov ms <mta_server> zimbraClamAVBindAddress <mta_server> zmprov mcf zimbraAttachmentsScanURL clam://<mta_server>:3310/ zmprov mcf zimbraAttachmentsScanEnabled TRUE
Anti-Spam Protection
Zimbra uses SpamAssassin to identify unsolicited commercial email (spam) with learned data stored in either the Berkeley DB database or a MariaDB database. You can also use the Postscreen function to provide additional protection against mail server overload. Both strategies are described in the following topics:
Spam Assassin Methods for Avoiding Spam
Usage guidelines are provided in the following topics:
| For information about how to customize SpamAssassin, see https:// wiki.zimbra.com/wiki/Anti-spam_strategies. |
Managing the Spam Assassin Score: SpamAssassin uses predefined rules as well as a Bayes database to score messages with a numerical range. Zimbra uses a percentage value to determine “spaminess” based on a SpamAssassin score of 20 as 100%. Any message tagged between 33%-75% is considered spam and delivered to the user’s junk folder. Messages tagged above 75% are always considered spam and discarded.
You can change the spam percentage settings, and the subject prefix at the Administration Console.
- Admin Console:
-
Home → Configure → Global Settings → AS/AV → Spam checking Settings
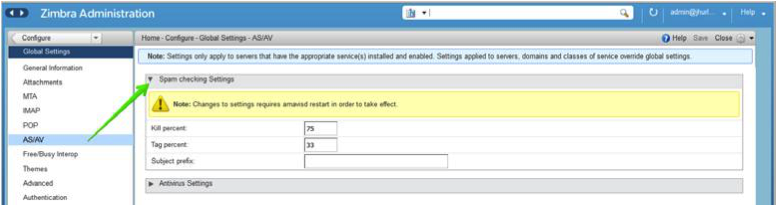
By default, Zimbra uses the Berkeley DB database for spam training. You can also use a MariaDB database.
To use the MariaDB method on the MTA servers:
zmlocalconfig -e antispam_mysql_enabled=TRUEWhen this is enabled, Berkeley DB database is not enabled.
Training the Spam Filter — The effectiveness of the anti-spam filter is dependent on user input to differentiate spam or ham. The SpamAssassin filter learns from messages that users specifically mark as spam by sending them to their junk folder or not spam by removing them from their junk folder. A copy of these marked messages is sent to the appropriate spam training mailbox.
At installation, a spam/ham cleanup filter is configured on only the
first MTA. The Zimbra spam training tool, zmtrainsa, is configured to
automatically retrieve these messages and train the spam filter. The
zmtrainsa script empties these mailboxes each day.
|
New installations of Zimbra limit spam/ham training to the first
MTA installed. If you uninstall or move this MTA, you will need to
enable spam/ham training on another MTA, as one host should have this
enabled to run To set this on a new MTA server: |
Initially, you might want to train the spam filter manually to quickly
build a database of spam and non-spam tokens, words, or short character
sequences that are commonly found in spam or ham. To do this, you can
manually forward messages as message/rfc822 attachments to the spam and
non-spam mailboxes. When zmtrainsa runs, these messages are used to teach
the spam filter. Make sure you add a large enough sampling of messages to
get accurate scores. To determine whether to mark messages as spam at least
200 known spams and 200 known hams must be identified.
SpamAssassin’s sa-update tool is included with SpamAssassin. This tool
updates SpamAssassin rules from the SA organization. The tool is
installed into /opt/zimbra/common/bin.
Configuring Final Destination for Spam — You can configure Amavis behavior to handle a spam item’s final destination by using the following attribute:
zimbraAmavisFinalSpamDestiny
The default is D_DISCARD (which will not deliver the email to the
addressee).
Setting final spam destiny attributes:
zmprov mcf "zimbraAmavisFinalSpamDestiny" D_PASS
zmprov ms serverhostname.com D_PASS| Value | Description |
|---|---|
|
Deliver the email to the recipient. The email is likely to be placed in the recipient’s junk folder (although some sites disable junk). |
|
The email is bounced back to the sender. Because this setting can create backscatter — as the "sender" is not the person who actually sent the email — it is not advised. |
|
Reject the email. This setting reduces the chance of backscatter:
|
|
The email is silently discarded (not delivered). |
Setting Up Trusted Networks: The Zimbra configuration allows relaying only for the local network, but you can configure trusted networks that are allowed to relay mail. You set the MTA trusted networks as a global setting, but you can configure trusted networks as a server setting. The server setting overrides the global setting.
To use the Administration Console to set up MTA trusted networks as a global setting:
- Admin Console:
-
Home → Configure → Global Settings → MTA → Network
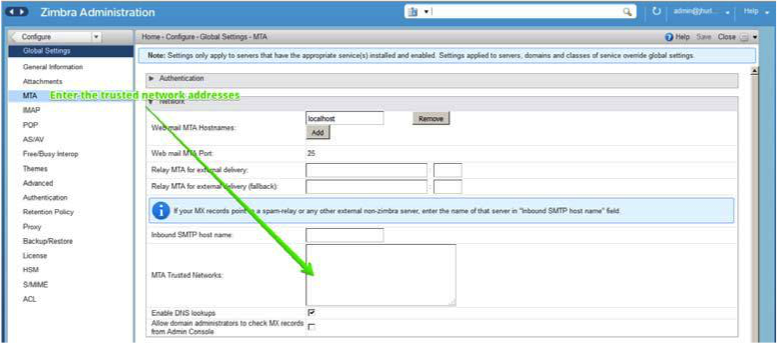
When using the Administration Console to set up MTA trusted networks on a per server basis, first ensure that MTA trusted networks have been set up as global settings.
- Admin Console:
-
Home → Configure → Servers → server → MTA → Network
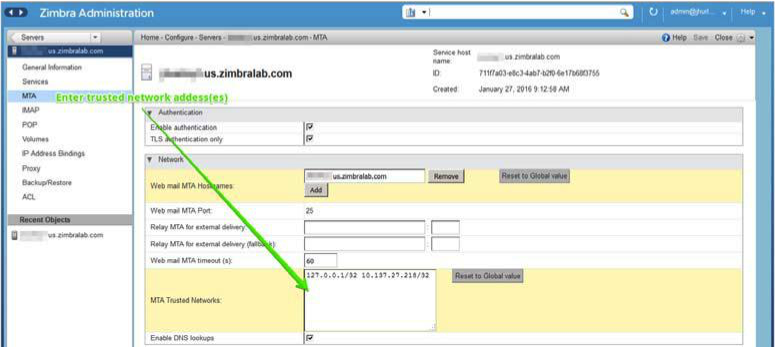
Enter the network addresses separated by commas and/or a space. Continue long lines by starting the next line with space, similar to the following examples:
127.0.0.0/8, 168.100.189.0/24 127.0.0.0/8 168.100.189.0/24 10.0.0.0/8 [::1]/128 [fe80::%eth0]/64
Enabling a Milter Server: Milter server can be enabled to enforce restrictions on which addresses can send to distribution lists and add Reply-To and X-Zimbra-DL headers to messages sent from distribution lists. This can be enabled globally or for specific servers from the Administration Console.
| Only enable a Milter Server on a server where an MTA is running. |
For global configuration, enable the milter server from the Administration Console:
- Admin Console:
-
Home → Configure → Global Settings → MTA → Milter Server
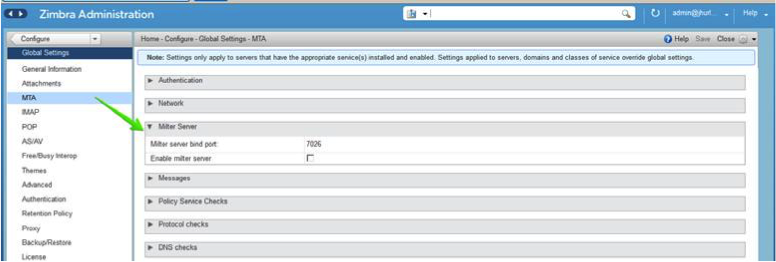
Use the Administration Console to enable a specific milter server, and to set bind addressing for individual servers.
- Admin Console:
-
Home → Configure → Servers → server → MTA → Milter Server
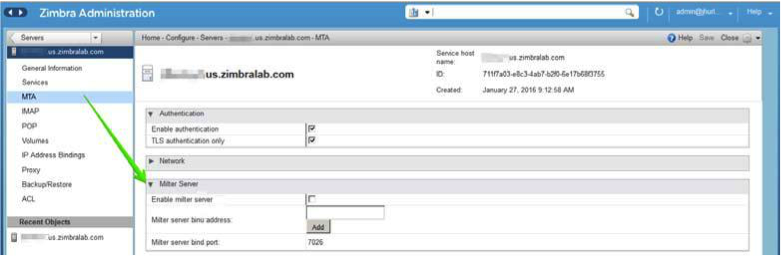
Postscreen Methods for Avoiding Spam
Zimbra Postscreen is the 8.7 enhancement to the Zimbra Collaboration anti-spam strategy, to provide additional protection against mail server overload. By design, Postscreen is not an SMTP proxy. Its purpose is to keep spambots away from Postfix SMTP server processes, while minimizing overhead for legitimate traffic. A single Postscreen process handles multiple inbound SMTP connections and decides which clients may communicate to a Post-fix SMTP server process. By keeping spambots away, Postscreen frees up SMTP server processes for legitimate clients, and delays the onset of server overload conditions.
In a typical deployment, Postscreen handles the MX service on TCP port 25, while MUA clients submit mail via the submission service on TCP port 587, which requires client authentication. Alternatively, a site could set up a dedicated, non-Postscreen, “port 25” server that provides submission service and client authentication without MX service.
| Postscreen should not be used on SMTP ports that receive mail from end-user clients (MUAs). |
Zimbra Collaboration Postscreen maintains a temporary white-list for clients that have passed a number of tests. When an SMTP client IP address is whitelisted, Postscreen immediately passes the connection to a Postfix SMTP server process. This minimizes the overhead for legitimate mail.
In a typical scenario that uses Postscreen service, it is reasonable to expect potentially malicious email entities — such as bots and zombies — to be mixed in with friendly candidates in email loads. This concept is illustrated in the following diagram, in which undesirable entities are depicted in red; good email candidates are green.
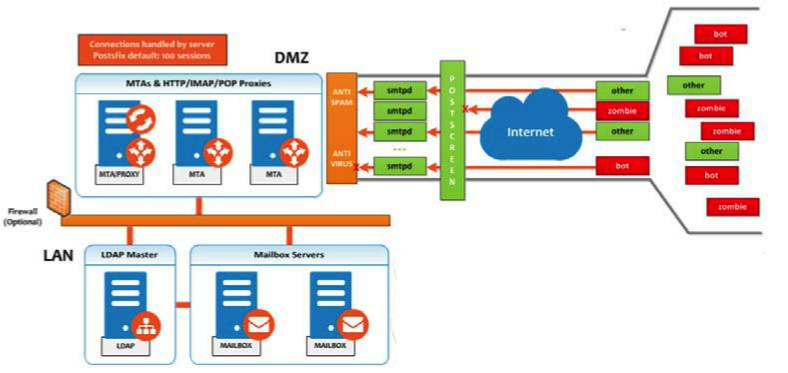
Postscreen performs basic checks and denies connection(s) that are clearly from a bot or zombie. If the connection is not in the temporary whitelist, Postscreen passes the email to the local Anti-SPAM and Anti-Virus engines, which can either accept it or deny it. Good connections are accepted via Postscreen security, then allowed to talk directly with the SMTP daemon, which scans the Email (as usual) with the AS/AV. By default, all bots or zombies are rejected.
Use Zimbra CLI attributes to set parameters for Postscreen operations. For any Postscreen Attributes that provide the ignore, enforce, or drop instruction, use guidelines as follows:
-
ignore — Ignore this result. Allow other tests to complete. Repeat this test with subsequent client connections. This is the default setting, which is useful for testing and collecting statistics without blocking mail.
-
enforce — Allow other tests to complete. Reject attempts to deliver mail with a 550 SMTP reply, and log the hello/sender/recipient information. Repeat this test with subsequent client connections.
-
drop — Drop the connection immediately with a 521 SMTP reply. Repeat this test with subsequent client connections.
Postscreen Attributes:
Go to the zmprov mcf prompt (release 8.7+) to use Postscreen commands.
You can see example usages of these attributes in
Enabling Postscreen.
-
zimbraMtaPostscreenAccessList— Default = permit_mynetworksPostconf
postscreen_access_listsetting, which is the permanent white/ blacklist for remote SMTP client IP addresses. Postscreen(8) searches this list immediately after a remote SMTP client connects. Specify a comma- or whitespace -separated list of commands (in upper or lower case) or lookup tables. The search stops upon the first command that fires for the client IP address. -
zimbraMtaPostscreenBareNewlineAction— Default = ignoreThe action that postscreen(8) is to take when a remote SMTP client sends a bare newline character, that is, a newline not preceded by carriage return — as either ignore, enforce, or drop.
-
zimbraMtaPostscreenBareNewlineEnable— Default = noEnable (yes) or disable (no) “bare newline” SMTP protocol tests in the postscreen(8) server. These tests are expensive: a remote SMTP client must disconnect after it passes the test, before it can talk to a real Postfix SMTP server.
-
zimbraMtaPostscreenBareNewlineTTL— Default = 30dThe amount of time allowable for postscreen(8) to use the result of a successful “bare newline” SMTP protocol test. During this time, the client IP address is excluded from this test. The default setting is lengthy because a remote SMTP client must disconnect after it passes the test, before it can talk to a real Postfix SMTP server.
Specify a non-zero time value (an integral value plus an optional one-letter suffix that specifies the time unit). Time units: s (seconds), m (minutes), h (hours), d (days), w (weeks).
-
zimbraMtaPostscreenBlacklistAction— Default = ignoreThe action that postscreen(8) is to take when a remote SMTP client is permanently blacklisted with the
postscreen_access_listparameter, as either ignore, enforce, or drop. -
zimbraMtaPostscreenCacheCleanupInterval— Default = 12hThe amount of time allowable between postscreen(8) cache cleanup runs. Cache cleanup increases the load on the cache database and should therefore not be run frequently. This feature requires that the cache database supports the “delete” and “sequence” operators. Specify a zero interval to disable cache cleanup.
After each cache cleanup run, the postscreen(8) daemon logs the number of entries that were retained and dropped. A cleanup run is logged as “partial” when the daemon terminates early after
postfix reload,postfix stop, or no requests for$max_idleseconds.Time units: s (seconds), m (minutes), h (hours), d (days), w (weeks).
-
zimbraMtaPostscreenCacheRetentionTime— Default = 7dThe amount of time that postscreen(8) is allowed to cache an expired temporary whitelist entry before it is removed. This prevents clients from being logged as “NEW” just because their cache entry expired an hour ago. It also prevents the cache from filling up with clients that passed some deep protocol test once and never came back.
Time units: s (seconds), m (minutes), h (hours), d (days), w (weeks).
-
zimbraMtaPostscreenCommandCountLimit— Default = 20Value to set the limit on the total number of commands per SMTP session for postscreen(8)'s built-in SMTP protocol engine. This SMTP engine defers or rejects all attempts to deliver mail, therefore there is no need to enforce separate limits on the number of junk commands and error commands.
-
zimbraMtaPostscreenDnsblAction— Default = ignoreThe action that postscreen(8) is to take when a remote SMTP client’s combined DNSBL score is equal to or greater than a threshold (as defined with the
postscreen_dnsbl_sitesandpostscreen_dnsbl_thresholdparameters), as either ignore, enforce, or drop. -
zimbraMtaPostscreenDnsblSitesOptional list of DNS white/blacklist domains, filters and weight factors. When the list is non-empty, the dnsblog(8) daemon will query these domains with the IP addresses of remote SMTP clients, and postscreen(8) will update an SMTP client’s DNSBL score with each non-error reply.
When postscreen rejects mail, it replies with the DNSBL domain name. Use the postscreen_dnsbl_reply_mapfeature to hide “password” information in DNSBL domain names.When a client’s score is equal to or greater than the threshold specified with
postscreen_dnsbl_threshold, postscreen(8) can drop the connection with the remote SMTP client.Specify a list of
domain=filter*weightentries, separated by comma or whitespace.-
When no
=filteris specified, postscreen(8) will use any non-error DNSBL reply. Otherwise, postscreen(8) uses only DNSBL replies that match the filter. The filter has the formd.d.d.d, where each d is a number, or a pattern inside[]that contains one or more “;”-separated numbers or number..number ranges. -
When no
*weightis specified, postscreen(8) increments the remote SMTP client’s DNSBL score by 1. Otherwise, the weight must be an integral number, and postscreen(8) adds the specified weight to the remote SMTP client’s DNSBL score. Specify a negative number for whitelisting. -
When one
postscreen_dnsbl_sitesentry produces multiple DNSBL responses, postscreen(8) applies the weight at most once.
Examples:
To use example.com as a high-confidence blocklist, and to block mail with example.net and example.org only when both agree:
postscreen_dnsbl_threshold = 2 postscreen_dnsbl_sites = example.com*2, example.net, example.org
To filter only DNSBL replies containing 127.0.0.4:
postscreen_dnsbl_sites = example.com=127.0.0.4
-
-
zimbraMtaPostscreenDnsblThreshold— Default = 1Value to define the inclusive lower bound for blocking a remote SMTP client, based on its combined DNSBL score as defined with the
postscreen_dnsbl_sitesparameter. -
zimbraMtaPostscreenDnsblTTL— Default = 1hThe amount of time allowable for postscreen(8) to use the result from a successful DNS-based reputation test before a client IP address is required to pass that test again.
Specify a non-zero time value (an integral value plus an optional one-letter suffix that specifies the time unit). Time units: s (seconds), m (minutes), h (hours), d (days), w (weeks).
-
zimbraMtaPostscreenDnsblWhitelistThreshold— Default = 0Allow a remote SMTP client to skip “before” and “after 220 greeting” protocol tests, based on its combined DNSBL score as defined with the
postscreen_dnsbl_sitesparameter.Specify a negative value to enable this feature. When a client passes the
postscreen_dnsbl_whitelist_thresholdwithout having failed other tests, all pending or disabled tests are flagged as completed with a time-to-live value equal topostscreen_dnsbl_ttl. When a test was already completed, its time-to-live value is updated if it was less thanpostscreen_dnsbl_ttl. -
zimbraMtaPostscreenGreetAction— Default = ignoreThe action that postscreen(8) is to take when a remote SMTP client speaks before its turn within the time specified with the
postscreen_greet_waitparameter, as either ignore, enforce, or drop. -
zimbraMtaPostscreenGreetTTL— Default = 1dThe amount of time allowed for postscreen(8) to use the result from a successful PREGREET test. During this time, the client IP address is excluded from this test. The default is relatively short, because a good client can immediately talk to a real Postfix SMTP server.
Specify a non-zero time value (an integral value plus an optional one-letter suffix that specifies the time unit). Time units: s (seconds), m (minutes), h (hours), d (days), w (weeks).
-
zimbraMtaPostscreenNonSmtpCommandAction— Default = dropThe action that postscreen(8) takes when a remote SMTP client sends non-SMTP commands as specified with the
postscreen_forbidden_commands parameter, as either ignore, enforce, or drop. -
zimbraMtaPostscreenNonSmtpCommandEnable— Default = noEnable (yes) or disable (no) "non- SMTP command" tests in the postscreen(8) server. These tests are expensive: a client must disconnect after it passes the test, before it can talk to a real Postfix SMTP server.
-
zimbraMtaPostscreenNonSmtpCommandTTL— Default = 30dThe amount of time allowable for postscreen(8) to use the result from a successful “non_smtp_command” SMTP protocol test. During this time, the client IP address is excluded from this test. The default is long because a client must disconnect after it passes the test, before it can talk to a real Postfix SMTP server.
Specify a non-zero time value (an integral value plus an optional one-letter suffix that specifies the time unit). Time units: s (seconds), m (minutes), h (hours), d (days), w (weeks).
-
zimbraMtaPostscreenPipeliningAction— Default = enforceThe action that postscreen(8) is to take when a remote SMTP client sends multiple commands instead of sending one command and waiting for the server to respond, as either ignore, enforce, or drop.
-
zimbraMtaPostscreenPipeliningEnable— Default = noEnable (yes) or disable (no) “pipelining” SMTP protocol tests in the postscreen(8) server. These tests are expensive: a good client must disconnect after it passes the test, before it can talk to a real Postfix SMTP server.
-
zimbraMtaPostscreenPipeliningTTL— Default = 30dTime allowable for postscreen(8) to use the result from a successful “pipelining” SMTP protocol test. During this time, the client IP address is excluded from this test. The default is lengthy because a good client must disconnect after it passes the test, before it can talk to a real Postfix SMTP server.
Specify a non-zero time value (an integral value plus an optional one-letter suffix that specifies the time unit). Time units: s (seconds), m (minutes), h (hours), d (days), w (weeks).
-
zimbraMtaPostscreenWatchdogTimeout— Default = 10sTime allowable for a postscreen(8) process to respond to a remote SMTP client command, or to perform a cache operation, before it is terminated by a built-in watchdog timer. This is a safety mechanism that prevents postscreen(8) from becoming non-responsive due to a bug in Postfix itself or in system software. To avoid false alarms and unnecessary cache corruption this limit cannot be set under 10s.
Specify a non-zero time value (an integral value plus an optional one-letter suffix that specifies the time unit). Time units: s (seconds), m (minutes), h (hours), d (days), w (weeks).
-
zimbraMtaPostscreenWhitelistInterfacesA list of local postscreen(8) server IP addresses where a non-whitelisted remote SMTP client can obtain postscreen(8)'s temporary whitelist status. This status is required before the client can talk to a Postfix SMTP server process. By default, a client can obtain postscreen(8)'s whitelist status on any local postscreen(8) server IP address.
When postscreen(8) listens on both primary and backup MX addresses, the
postscreen_whitelist_interfacesparameter can be configured to give the temporary whitelist status only when a client connects to a primary MX address. Once a client is whitelisted it can talk to a Postfix SMTP server on any address. Thus, clients that connect only to backup MX addresses will never become whitelisted, and will never be allowed to talk to a Postfix SMTP server process.Specify a list of network addresses or network/netmask patterns, separated by commas and/or whitespace. The netmask specifies the number of bits in the network part of a host address. Continue long lines by starting the next line with whitespace.
You can also specify
/file/nameortype:tablepatterns. A/file/namepattern is replaced by its contents; atype:tablelookup table is matched when a table entry matches a lookup string (the lookup result is ignored).The list is matched left to right, and the search stops on the first match. Specify
!patternto exclude an address or network block from the list.IPv6 address information must be specified inside []in thepostscreen_whitelist_interfacesvalue, and in files specified with/file/name. IP version 6 addresses contain the “:” character, and would otherwise be confused with atype:tablepattern.Example:
/etc/postfix/main.cf: # Don't whitelist connections to the backup IP address. postscreen_whitelist_interfaces = !168.100.189.8, static:all
-
zimbraMtaPostscreenDnsblMinTTL— Default = 60sThe minimum amount of time that postscreen(8) is allowed — resulting from a successful DNS -based reputation test — before a client IP address is required to pass that test again. If the DNS reply specifies a larger TTL value, that value will be used unless it would be larger than
postscreen_dnsbl_max_ttl.Specify a non-zero time value (an integral value plus an optional one-letter suffix that specifies the time unit). Time units: s (seconds), m (minutes), h (hours), d (days), w (weeks).
-
zimbraMtaPostscreenDnsblMaxTTL— Default = postscreen dnsbl ttlThe maximum amount of time allowable for postscreen(8) to use the result from a successful DNS-based reputation test before a client IP address is required to pass that test again. If the DNS reply specifies a shorter TTL value, that value will be used unless it would be smaller than
postscreen_dnsbl_min_ttl.Specify a non-zero time value (an integral value plus an optional one-letter suffix that specifies the time unit). Time units: s (seconds), m (minutes), h (hours), d (days), w (weeks).
Note that the default setting is backwards-compatible with Postscreen versions earlier than 3.1.
Enabling Postscreen:
The example in this section demonstrates settings appropriate for a global configuration with medium-to-high level Postscreen protection.
zmprov mcf zimbraMtaPostscreenAccessList permit_mynetworks zmprov mcf zimbraMtaPostscreenBareNewlineAction ignore zmprov mcf zimbraMtaPostscreenBareNewlineEnable no zmprov mcf zimbraMtaPostscreenBareNewlineTTL 30d zmprov mcf zimbraMtaPostscreenBlacklistAction ignore zmprov mcf zimbraMtaPostscreenCacheCleanupInterval 12h zmprov mcf zimbraMtaPostscreenCacheRetentionTime 7d zmprov mcf zimbraMtaPostscreenCommandCountLimit 20 zmprov mcf zimbraMtaPostscreenDnsblAction enforce zmprov mcf \ zimbraMtaPostscreenDnsblSites 'b.barracudacentral.org=127.0.0.2_7' \ zimbraMtaPostscreenDnsblSites 'dnsbl.inps.de=127.0.0.2*7' \ zimbraMtaPostscreenDnsblSites 'zen.spamhaus.org=127.0.0.[10;11]*8' \ zimbraMtaPostscreenDnsblSites 'zen.spamhaus.org=127.0.0.[4..7]*6' \ zimbraMtaPostscreenDnsblSites 'zen.spamhaus.org=127.0.0.3*4' \ zimbraMtaPostscreenDnsblSites 'zen.spamhaus.org=127.0.0.2*3' \ zimbraMtaPostscreenDnsblSites 'list.dnswl.org=127.0.[0..255].0*-2' \ zimbraMtaPostscreenDnsblSites 'list.dnswl.org=127.0.[0..255].1*-3' \ zimbraMtaPostscreenDnsblSites 'list.dnswl.org=127.0.[0..255].2*-4' \ zimbraMtaPostscreenDnsblSites 'list.dnswl.org=127.0.[0..255].3*-5' \ zimbraMtaPostscreenDnsblSites 'bl.mailspike.net=127.0.0.2*5' \ zimbraMtaPostscreenDnsblSites 'bl.mailspike.net=127.0.0.[10;11;12]*4' \ zimbraMtaPostscreenDnsblSites 'wl.mailspike.net=127.0.0.[18;19;20]*-2' \ zimbraMtaPostscreenDnsblSites 'dnsbl.sorbs.net=127.0.0.10*8' \ zimbraMtaPostscreenDnsblSites 'dnsbl.sorbs.net=127.0.0.5*6' \ zimbraMtaPostscreenDnsblSites 'dnsbl.sorbs.net=127.0.0.7*3' \ zimbraMtaPostscreenDnsblSites 'dnsbl.sorbs.net=127.0.0.8*2' \ zimbraMtaPostscreenDnsblSites 'dnsbl.sorbs.net=127.0.0.6*2' \ zimbraMtaPostscreenDnsblSites 'dnsbl.sorbs.net=127.0.0.9*2' zmprov mcf zimbraMtaPostscreenDnsblTTL 5m zmprov mcf zimbraMtaPostscreenDnsblThreshold 8 zmprov mcf zimbraMtaPostscreenDnsblTimeout 10s zmprov mcf zimbraMtaPostscreenDnsblWhitelistThreshold 0 zmprov mcf zimbraMtaPostscreenGreetAction enforce zmprov mcf zimbraMtaPostscreenGreetTTL 1d zmprov mcf zimbraMtaPostscreenNonSmtpCommandAction drop zmprov mcf zimbraMtaPostscreenNonSmtpCommandEnable no zmprov mcf zimbraMtaPostscreenNonSmtpCommandTTL 30d zmprov mcf zimbraMtaPostscreenPipeliningAction enforce zmprov mcf zimbraMtaPostscreenPipeliningEnable no zmprov mcf zimbraMtaPostscreenPipeliningTTL 30d zmprov mcf zimbraMtaPostscreenWatchdogTimeout 10s zmprov mcf zimbraMtaPostscreenWhitelistInterfaces static:all
Testing Postscreen:
Testing uses Postscreen to view results without taking any action. In a testing scenario, you instruct Postscreen to log email connections without taking action on them. Once you are satisfied with the results, you can set Postscreen values to enforce or drop emails, as required.
-
Set up the DNS-based Blackhole List (DNSBL).
-
Set Postscreen to ignore.
The following real-world example demonstrates return of a 550 error from Postscreen during a test session:
Mar 1 02:03:26 edge01 postfix/postscreen[23154]: DNSBL rank 28 for [112.90.37.251]:20438 Mar 1 02:03:26 edge01 postfix/postscreen[23154]: CONNECT from [10.210.0.161]:58010 to [10.210.0.174]:25 Mar 1 02:03:26 edge01 postfix/postscreen[23154]: WHITELISTED [10.210.0.161]:58010 Mar 1 02:03:27 edge01 postfix/postscreen[23154]: NOQUEUE: reject: RCPT from [112.90.37.251]:20438: 550 5.7.1 Service unavailable; client [112.90.37.251] blocked using zen.spamhaus.org; from=<hfxdgdsggfvfg@gmail.com>, to=<support@zimbra.com>, proto=ESMTP, helo=<gmail.com> Mar 1 02:03:27 edge01 postfix/postscreen[23154]: DISCONNECT [112.90.37.251]:20438
Receiving and Sending Mail
The Zimbra MTA delivers the incoming and the outgoing mail messages. For outgoing mail, the Zimbra MTA determines the destination of the recipient address. If the destination host is local, the message is passed to the Zimbra server for delivery. If the destination host is a remote mail server, the Zimbra MTA must establish a communication method to transfer the message to the remote host. For incoming messages, the MTA must be able to accept connection requests from remote mail servers and receive messages for the local users.
To send and receive email, the MTA must be configured in DNS with both an A record and an MX Record. For sending mail, the MTA uses DNS to resolve hostnames and email-routing information. To receive mail, the MX record must be configured correctly to route messages to the mail server.
You must configure a relay host if you do not enable DNS.
Message Queues
When the Zimbra MTA receives mail, it routes the mail through a series of queues to manage delivery; incoming, active, deferred, hold, and corrupt.
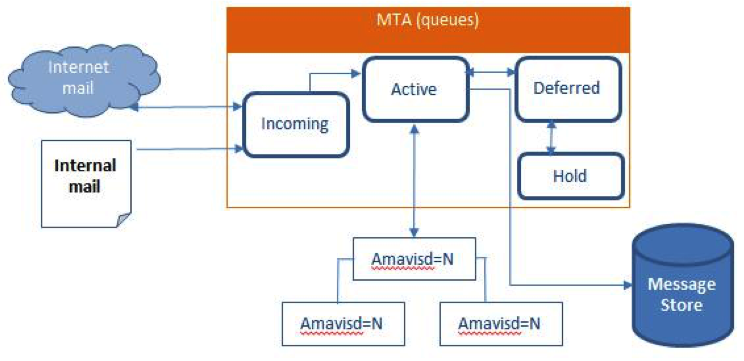
The incoming message queue holds the new mail that has been received. Each message is identified with a unique file name. Messages are moved to the active queue when there is room. If there are no problems, message move through this queue very quickly.
The active message queue holds messages that are ready to be sent. The MTA sets a limit to the number of messages that can be in the active queue at any one time. From here, messages are moved to and from the anti-virus and anti-spam filters before being delivered to another queue.
Messages that cannot be delivered are placed in the deferred queue. The reasons for the delivery failures are documented in a file in the deferred queue. This queue is scanned frequently to resend the message. If the message cannot be sent after the set number of delivery attempts, the message fails and is bounced back to the original sender. You can choose to send a notification to the sender that the message has been deferred.
The hold message queue keeps mail that could not be processed. Messages stay in this queue until the administrator moves them. No periodic delivery attempts are made for messages in the hold queue.
The corrupt queue stores damaged unreadable messages.
You can monitor the mail queues for delivery problems from the Administration Console. See Monitoring Zimbra Servers.
Message banner for mails from external domains
A message banner in the mails can be added for the mails coming from external domains. This will help users to identify the mails originating outside their organization. The feature is controlled by a localconfig attribute and by default it is disabled.
Following are the details of the attributes:
-
zimbra_external_email_warning_enabled- Attribute to enable/disable the feature. -
zimbra_external_email_warning_message- Attribute to customize the message to be displayed in the mails.
Following are the instructions to be executed as zimbra user:
-
Enabling the feature:
su - zimbra zmlocalconfig -e zimbra_external_email_warning_enabled=true
-
Restart mailbox service:
zmmailboxdctl restart
When a user receives mail from an external domain, the message banner will get displayed at the top of the message body.
Modifying the message
The message for external domains can also be modified.
Following are the instructions:
-
Edit the localconfig attribute
zimbra_external_email_warning_messagewith the new message:zmlocalconfig -e zimbra_external_email_warning_message="The external domain warning has been edited"
-
Restart mailbox service:
zmmailboxdctl restart
When a user receives mail from an external domain, the edited message banner will get displayed at the top of the message body.
Zimbra Proxy Server
Zimbra Proxy is a high-performance proxy server that can be configured as a POP3/IMAP/HTTP proxy used to reverse proxy IMAP/POP3 and HTTP client requests to a set of backend servers.
The Zimbra Proxy package is installed and configured during the Zimbra Collaboration installation. You can install this package on a mailbox server, MTA server, or on its own independent server. When the Zimbra Proxy package is installed, the proxy feature is enabled. In most cases, no modification is necessary.
Benefits of Using Zimbra Proxy
Benefits for using Zimbra Proxy include:
-
Zimbra proxy centralizes access to Mailbox servers
-
Load Balancing
-
Security
-
Authentication
-
SSL Termination
-
Caching
-
Centralized Logging and Auditing
-
URL Rewriting
-
Strict Server Name Enforcement (optional)
For more information, see the wiki page Zimbra_Proxy_Guide.
Zimbra Proxy Components
Zimbra Proxy is designed to provide a HTTP/POP/IMAP proxy that is quick, reliable, and scalable. Zimbra Proxy includes the following:
| Component | Description |
|---|---|
Nginx |
High performance HTTP/IMAP/POP3 proxy server that handles all incoming HTTP/POP/IMAP requests. |
Memcached |
High performance distributed memory object caching system in which routing information is cached to enable increased performance. |
Zimbra Proxy Route Lookup Handler |
Servelet—located on the Zimbra mailbox server—that handles queries for the user account route information. This routing information consists of the server and port number where the user account resides. |
Proxy Architecture and Flow
This section describes the architecture and flow sequence of Zimbra proxy.
-
End clients connect to Zimbra Proxy using HTTP/HTTPS/POP/IMAP ports.
-
When Zimbra Collaboration Proxy receives an incoming connection, the Nginx component sends an HTTP request to Zimbra Collaboration Proxy Route Lookup Handler component.
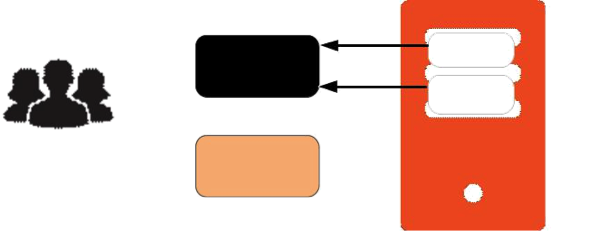
-
Zimbra Collaboration Proxy Route Lookup Handler locates the route information for the account being accessed and returns this to Nginx.
-
The Memcached component stores the route information for the configured period of time (the default is one hour). Nginx uses this route information instead of querying the Zimbra Collaboration Proxy Route Lookup Handler until the default period of time has expired.
-
Nginx uses the route information to connect to Zimbra Collaboration Mailbox.
-
Zimbra Collaboration Proxy connects to Zimbra Collaboration Mailbox and initiates the web/mail proxy session. The end client behaves as if it is connecting directly to Zimbra Collaboration Mailbox.
Changing the Zimbra Proxy Configuration
When Zimbra proxy is configured, the Zimbra proxy config performs keyword substitution as necessary with values from the LDAP configuration and localconfig.
If changes are required after the Zimbra Proxy is set up, modify the Zimbra
LDAP attributes or localconfig values and run zmconfigd to generate the
updated Zimbra Proxy configuration. The Zimbra proxy configuration file is
in /opt/zimbra/conf/nginx.conf. The nginx.conf includes the main config,
memcache config, mail config, and web config files.
Common changes to Zimbra Proxy configuration are IMAP/POP configuration changes from the original default setup
-
HTTP reverse proxy configuration changes from the original default setup
-
GSSAPI authentication for Kerberos. In this case you manually identify the location of the Kerberos Keytab file, including Zimbra Proxy password
Zimbra Proxy
Zimbra Proxy allows end users to access their Zimbra Collaboration account using clients such as Microsoft Outlook, Mozilla Thunderbird, or other POP/IMAP end-client software. End users can connect using POP3, IMAP, POP3S (Secure POP3), or IMAPS (Secure IMAP).
For example, proxying allows users to enter imap.example.com as their IMAP server. The proxy running on imap.example.com inspects their IMAP traffic, does a lookup to determine which backend mailbox server a user’s mailbox lives on and transparently proxies the connection from user’s IMAP client to the correct mailbox server.
Zimbra Proxy Ports
The following ports are used either by Zimbra Proxy or by Zimbra Mailbox (if Proxy is not configured). If you have any other services running on these ports, turn them off.
End clients connect directly to Zimbra Proxy, using the Zimbra Proxy Ports. Zimbra Proxy connects to the Route Lookup Handler or Zimbra Mailbox using the Zimbra Mailbox Ports.
| Zimbra Proxy Ports (External to Zimbra) | Port |
|---|---|
HTTP |
80 |
HTTPS |
443 |
POP3 |
110 |
POP3S (Secure POP3) |
995 |
IMAP |
143 |
IMAPS (Secure IMAP) |
993 |
Zimbra Mailbox Ports (Internal to Zimbra) |
Port |
Route Lookup Handler |
7072 |
HTTP Backend (if Proxy configured) |
8080 |
HTTPS Backend (if Proxy configured) |
8443 |
POP3 Backend (if Proxy configured) |
7110 |
POP3S Backend (if Proxy configured) |
7995 |
IMAP Backend (if Proxy configured) |
7143 |
IMAPS Backend (if Proxy configured) |
7993 |
Strict Server Name Enforcement
Zimbra Proxy has the ability to strictly enforce which values are allowed in the Host header
passed in by the client.
This is enabled by default on new installations but left disabled for upgrades from previous versions unless toggled during the installation.
The functionality may be altered by setting the zimbraReverseProxyStrictServerNameEnabled boolean configuration
option followed by restarting the proxy server.
-
TRUE - strict server name enforcement enabled
-
FALSE - strict server name enforcement disabled
zmprov mcf zimbraReverseProxyStrictServerNameEnabled TRUEWhen the strict server name functionality is enabled, additional valid server names may be specified
using the zimbraVirtualHostName and zimbraVirtualIPAddress configuration items at the domain level.
zmprov md example.com zimbraVirtualHostName mail.example.com zimbraVirtualIPAddress 1.2.3.4| Only one virtual ip address is needed per domain although more than one is acceptable. |
Setting Up IMAP and POP Proxy After HTTP Proxy Installation
IMAP proxy is installed with Zimbra Collaboration and set up during installation from the configuration menus. To set up the HTTP proxy, the proxy must be installed on the identified proxy nodes in order to set up HTTP proxy. No other configuration is usually required.
If you need to, set up IMAP/POP proxy after you have already installed HTTP proxy, and set up the mailbox server and the proxy node.
You can run the command as zmproxyconfig -r, to run against a remote
host. This requires the server to be properly configured in the LDAP
master.
|
Set Up IMAP/POP Proxy with Separate Proxy Node
Use steps in this section if your configuration includes a separate proxy server.
-
On each Zimbra mailbox server that you want to proxy with, enable the proxy for IMAP/POP proxy.
/opt/zimbra/libexec/zmproxyconfig -e -m -H mailbox.node.service.hostnameThis configures the following:
Port Attributes Setting zimbraImapBindPort7143
zimbraImapProxyBindPort143
zimbraImapSSLBindPort7993
zimbraImapSSLProxyBindPort993
zimbraPop3BindPort7110
zimbraPop3ProxyBindPort110
zimbraPop3SSLBindPort7995
zimbraPop3SSLProxyBindPort995
zimbralmapCleartextLoginEnabledTRUE
zimbraReverseProxyLookupTargetTRUE
zimbraPop3CleartextLoginEnabledTRUE
-
Restart services on the proxy and mailbox servers.
zmcontrol restart
Set Up the Proxy Node
On each proxy node that has the proxy service installed, enable the proxy for the web.
/opt/zimbra/libexec/zmproxyconfig -e -m -H proxy.node.service.hostnameThis configures the following:
| Port Attribute | Setting |
|---|---|
|
7143 |
|
143 |
|
7993 |
|
993 |
|
7110 |
|
110 |
|
7995 |
|
995 |
|
TRUE |
Set Up a Single Node
Use steps in this section if Zimbra proxy is installed with Zimbra Collaboration on the same server.
-
Enable the proxy for the web.
/opt/zimbra/libexec/zmproxyconfig -e -m -H mailbox.node.service.hostnameThis configures the following:
Port Attribute Setting zimbraImapBindPort7143
zimbraImapProxyBindPort143
zimbraImapSSLBindPort7993
zimbraImapSSLProxyBindPort993
zimbraPop3BindPort7110
zimbraPop3ProxyBindPort110
zimbraPop3SSLBindPort7995
zimbraPop3SSLProxyBindPort995
zimbraImapCleartextLoginEnabledTRUE
zimbraReverseProxyLookupTargetTRUE
zimbraPop3CleartextLoginEnabledTRUE
zimbraReverseProxyMailEnabledTRUE
-
Restart services on the proxy and mailbox servers.
zmcontrol restart
Configuring Zimbra HTTP Proxy
Zimbra Proxy can also reverse proxy HTTP requests to the right back-end server.
For example, users can use a web browser to connect to the proxy server at https://mail.example.com. The connection from users whose mailboxes live on mbs1.example.com is proxied to mbs1.example.com by the proxy running on the mail.example.com server. The proxy also supports REST and CalDAV clients, Zimbra Connector for Outlook, and Zimbra Mobile Sync devices.
HTTP reverse proxy routes requests as follows:
-
If the requesting URL can be examined to determine the user name, then the request is routed to the backend mailbox server of the user in the URL. REST, CalDAV, and Zimbra Mobile Sync are supported through this mechanism.
-
If the request has an auth token cookie (ZM_AUTH_TOKEN), the request is routed to the backend mailbox server of the authenticated user.
-
If the above methods do not work, the IP hash method is used to load balance the requests across the backend mailbox servers which are able to handle the request or do any necessary internal proxying.
Setting Up HTTP Proxy
To set up HTTP proxy, Zimbra Proxy must be installed on the identified nodes.
You can run the command as /opt/zimbra/libexec/zmproxyconfig -r, to run
against a remote host. Note that this requires the server to be properly
configured in the LDAP master.
|
Setting Up HTTP Proxy as a Separate Proxy Node
Use steps in this section if your configuration includes a separate proxy server.
-
On each Zimbra mailbox server that you want to proxy with, enable the proxy for the web.
/opt/zimbra/libexec/zmproxyconfig -e -w -H mailbox.node.service.hostnameThis configures the following:
Attribute Setting zimbraMailReferModereverse-proxied.
zimbraMailPort8080 (to avoid port conflicts)
zimbraMailSSLPort8443 (to avoid port conflicts)
zimbraReverseProxyLookupTargetTRUE
zimbraMailModeHTTP
-
Restart services on the proxy and mailbox servers.
zmcontrol restart -
Configure each domain with the public service host name to be used for REST URLs, email, and Briefcase folders.
zmprov modifyDomain <domain.com> zimbraPublicServiceHostname <hostname.domain.com>
Setting Up Proxy Node
On each proxy node that has the proxy service installed, enable the proxy for the web.
/opt/zimbra/libexec/zmproxyconfig -e -w -H proxy.node.service.hostnameThis configures the following:
| Attribute | Setting |
|---|---|
|
reverse-proxied. To set the proxy server mail mode, add the -x option to the command, with the specific mode as either http, https, both, redirect, or mixed. |
|
80 (to avoid port conflicts). |
|
443 (to avoid port conflicts). |
|
TRUE (to indicate that Web proxy is enabled). |
|
HTTP (default) |
To set the proxy server mail mode, add the -x option to the command
with the specific mode: http, https, both, redirect, mixed.
Setting Up a Single Node for HTTP Proxy
Use steps in this section if Zimbra proxy is installed along with Zimbra on the same server.
-
On each zimbra mailbox server that you want to proxy with, enable the proxy for the web.
/opt/zimbra/libexec/zmproxyconfig -e -w -H mailbox.node.service.hostnameThis configures the following:
Attribute Setting zimbraMailReferModereverse-proxied.
zimbraMailPort8080 (to avoid port conflicts)
zimbraMailSSLPort8443 (to avoid port conflicts)
zimbraReverseProxyLookupTargetTRUE
zimbraMailModeHTTP (the only supported mode)
zimbraMailProxyPort80 (to avoid port conflicts)
zimbraMailSSLProxyPort443 (to avoid port conflicts)
zimbraReverseProxyHttpEnabledTRUE (to indicate that Web proxy is enabled)
zimbraReverseProxyMailModeHTTP (default)
To set the proxy server mail mode, add the
-xoption to the command with the specific mode: http, https, both, redirect, mixed. -
Restart services on the proxy and mailbox servers.
zmcontrol restartConfigure each domain with the public service host name to be used for REST URLs, email and Briefcase folders.
zmprov modifyDomain <domain.com> zimbraPublicServiceHostname <hostname.domain.com>
Set Up Proxy to use Clear Text for Upstream Connections
When setting up the proxy to use clear text for upstream connections, set
zimbraReverseProxySSLToUpstreamEnabled to FALSE.
This attribute defaults to TRUE. In an "out of the box" proxy set up, the upstream communication defaults to SSL.
REST URL Generation
For REST URL, you set the host name, service protocol, and services port globally or for a specific domain from the following attributes.
-
zimbraPublicServiceHostname -
zimbraPublicServiceProtocol -
zimbraPublicServicePort
When generating REST URL’s:
-
If
domain.zimbraPublicServiceHostnameis set, usezimbraPublicServiceProtocol+zimbraPublicServiceHostname+zimbraPublicServicePort -
Otherwise it falls back to the server (account’s home server) attributes:
-
protocol is computed from
server.zimbraMailMode -
hostname is
server.zimbraServiceHostname
-
-
port is computed from the protocol.
About using zimbraMailReferMode - In earlier versions, a local config
variable — zimbra_auth_always_send_refer — determined which action the
back-end server took when a user’s mailbox did not reside on the server
that the user logged in to. The default value of FALSE redirected the user
if the user was logging in on the incorrect backend host.
|
On a multiserver Zimbra, if a load balanced name was needed to create a
friendly landing page, a user would always have to be redirected. In that
case, zimbra_auth_always_send_refer was set to TRUE.
Now with a full-fledged reverse proxy, users do not need to be
redirected. The localconfig variable zimbraMailReferMode is used with
nginx reverse proxy.
Setting Proxy Trusted IP Addresses
When a proxy is configured with Zimbra, each proxy server’s IP
address must be configured in LDAP attribute zimbraMailTrustedIP to
identify the proxy addresses as trusted when users log in through the
proxy. The proxy IP address is added to the X-Forwarded-For header
information. The X-Forwarded-For header is automatically added to the
localconfig zimbra_http_originating_ip header attribute. When a user logs
in, this IP address and the user’s address are verified in the Zimbra
mailbox log.
Set each proxy IP address in the attribute. For example, if you have two proxy servers:
zmprov mcf +zimbraMailTrustedIP {IP of nginx-1} +zimbraMailTrustedIP {IP of nginx-2}|
To verify that X-Forwarded-For was correctly added to the localconfig, type You should see |
Configuring Zimbra Proxy for Kerberos Authentication
Use steps in this section if you use the Kerberos5 authenticating mechanism, and want to configure it for the IMAP and POP proxy.
| Make sure that your Kerberos5 authentication mechanism is correctly configured. See Zimbra LDAP Service |
-
On each proxy node, set the zimbraReverseProxyDefaultRealm server attribute to the realm name corresponding to the proxy server. For example:
zmprov ms [DNS name.isp.net] zimbraReverseProxyDefaultRealm [ISP.NET] -
Each proxy IP address where email clients connect must be configured for GSSAPI authentication by the mail server. On each proxy node for each of the proxy IP addresses:
zmprov mcf +zimbraReverseProxyAdminIPAddress [IP address] -
On each proxy server:
zmprov ms [proxyexample.net] zimbraReverseProxyImapSaslGssapiEnabled TRUE zmprov ms proxyl.isp.net zimbraReverseProxyPop3SaslGssapiEnabled TRUE -
Restart the proxy server
zmproxyctl restart
Zimbra Administration Console
The Zimbra Administration Console is a browser-based user interface for the central management of Zimbra servers and user accounts.
Administrator Accounts
When you log in to the Administration Console, the tasks you are authorized to perform show up on the Navigation pane. These tasks depend on the rights assigned to your administrator role.
You can create two types of administrator accounts to manage Zimbra Collaboration:
-
Global Administrators have full privileges to manage servers, global settings, domains, and accounts as well as create other administrators. One global administrator account gets created automatically during software installation. Create additional global administrator accounts anytime later. You can perform administration tasks from the Administration Console or the command line.
-
Delegated Administrators are granted customized administrator roles by the global administrator to manage different tasks from the Administration Console. See Delegated Administration for more details.
Logging into the Administration Console
-
To launch the Administration Console in a typical installation, use the following URL pattern.
https://server.domain.com:7071/Parameter Description server.domain.com
The Zimbra server name or IP address.
7071
The default HTTP listen port.
-
At the login screen, enter the complete administrator address - e.g., admin@domain.com - and the password configured for it during server installation of Zimbra Collaboration.
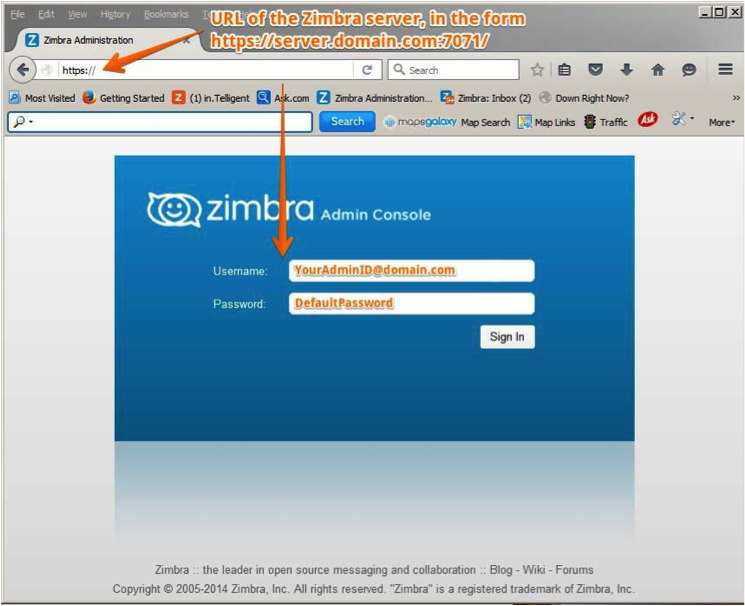
Two-Factor Authentication for Admin Console Login
Two-Factor Authentication (2FA) login mechanism is available when logging into the Admin Console. It can be enabled for Administrators and Delegated Administrators. Once enabled, the admins must complete an additional verification step when logging into the Admin Console.
For details on the feature and how to enable the 2FA feature, refer to: Two-Factor Authentication
Setting Up 2FA for an Administrator Account (via Webmail)
Administrator accounts must configure their own 2FA from the Web Client interface.
-
Log in to the Web Client using the administrator account
-
Go to Preferences
-
Select Accounts or Security (based on UI version)
-
Open Two-Factor Authentication
-
Click Set up Two-Factor Authentication
-
Choose the preferred verification method:
-
Authenticator app (TOTP)
-
Email-based verification
-
-
Follow the on-screen steps to complete setup
-
Confirm setup using the verification code
Once enabled, the administrator will be required to enter a 2FA code when logging into both: - Web Client - Administration Console
Notes
-
2FA is enforced for Admin Console login once enabled for the administrator account
-
Supported verification methods include authenticator apps and email (if enabled)
-
2FA configuration must be managed through the Web Client
Modifying Administrator Passwords
You can change the password - from either the Administration Console or the CLI - at any time.
From the Administration Console, use the Change Password screen to set the new password string, and to define the policy for user password modifications.
- Admin Console:
-
Home → Manage → Accounts
Double click select user account or from the Gear icon, select Change Password from the popup menu.
zmprov sp adminname@domain.com passwordCustomizing the Login and Logout Pages
A different login and logout page can be configured either as a global setting or as a domain setting.
To specify a URL to redirect administrators to if their login fails authentication, or if their authentication has expired:
Global:
zmprov mcf zimbraAdminConsoleLoginURL <https://example.com>Domain:
zmprov md <domain> zimbraAdminConsoleLoginURL <https://example.com>To specify a URL to redirect administrators to, for logging out:
Global:
zmprov mcf zimbraAdminConsoleLogoutURL <https://example.com>Domain:
zmprov md <domain> zimbraAdminConsoleLogoutURL <https://example.com>Managing Tasks
Most Zimbra tasks - such as creating accounts and Classes of Service, Server Status Monitoring, Domain management, Backup Scheduling, and Session management - can be managed from the Administration Console.
Other configuration and maintenance tasks require the use of the Zimbra CLI because you cannot perform them in the Administration Console. For example: starting and stopping services and managing the local server configuration.
At the Administration Console, if you need to view the attribute associated with a particular function, you can click on the text labels of the currently visible configuration page to open the information in a popup. Guide text is also provided from these popups, as demonstrated in the following illustration.
Click the field label to view the Attribute popup. |
|
With the attribute popup in view, click More to view guidetext about the field. |
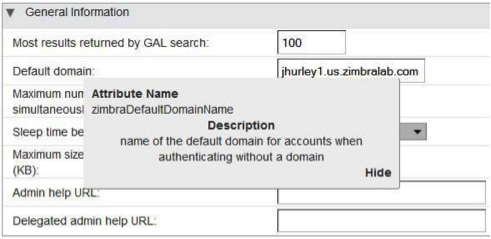
|
Navigating the User Interface
The organization of the Zimbra Collaboration Administration Console provides quick navigation to the configuration and monitoring tools and views associated with your login privileges. It also provides easy access to various types of Help and the on-screen guide text.
After logging in to the Administration Console, the Home page provides status information and options you can select to navigate to the configuration and viewing options described in this user guide.
<1> Go to Previous or Next page <2> Current Location/Path <3> Search <4> Screen Refresh <5> Current User and Logout Option <6> Help <7> Gear Icon <8> Status Pane <9> Viewing Pane <10> Navigation Pane
The displays and options in the navigation pane and viewing pane change according to your selections. Other portions of the UI — arrow buttons, search field, screen refresh, current location/path, current login, and Help — always remain in view.
The Gear Icon ![]() is displayed with some screens, to enable quick access to functions associated with the functions provided in the screens.
For more information about the Gear icon, see Using the Gear icon
is displayed with some screens, to enable quick access to functions associated with the functions provided in the screens.
For more information about the Gear icon, see Using the Gear icon
Home Navigation Pane
The options provided in the Home navigation pane get categorized under the Home directory. Some of the options lead to configuration pages; others lead to pages containing reports, as associated with your selections.
The illustration at right is an expanded view of the options currently supported in the Navigation Pane.
The upper bar of the in-view page always displays your current position in the hierarchy, and you can use multiple options for dismissing the current view:
-
To return to a previous page or go to the next page, click the left or right arrows.
-
To return to a specific portion of the UI, select an option from the Home dropdown.
-
To go directly to a specific option, click through the hierarchy in the Navigation Pane.
The Navigation pane options are described in the following topics:
Home UI
The Home screen is the default, login view, which provides the Home navigation pane and the Home page. This page provides a snapshot view of system status and a series of quick-access links for essential tasks.
<1> Go to Previous or Next page <2> Search <3> Screen Refresh <4> Current User and Logout Option <5> Help <6> System Status <7> Status Pane <8> Quick Start <9> Navigation Pane
| Topic | Description |
|---|---|
Summary |
Displays the version of Zimbra Collaboration currently running and in view, and the detected number of servers, account, domains, and classes of service associated with this session. |
Maintenance |
Displays the most recent software backup performed. |
Runtime |
Displays the runtime statistics for Service, Active Session, and Queue Length. |
1 Get Started |
Displays the steps essential to getting started with your Zimbra Collaboration operations, and provides quick links to the functions in this UI:
|
2 Set up Domain |
Displays the steps you use to establish the domain(s) to be managed by the Collaborator. Each step is a link to the function in this UI:
|
3 Add Accounts |
Displays the steps for adding accounts for management by the Collaborator. Each step is a link to the function in this UI:
|
Monitor UI
The Monitor screen provides the Monitor navigation pane and the Monitor pages, which display various itemizations about servers monitored by the Collaborator.
<1> Go to Previous or Next page <2> Search <3> Screen Refresh <4> Current User and Logout Option <5> Help <6> Status Pane <7> Navigation Pane
Monitor Navigation Pane and Pages
The options provided in the Monitor pages provide various methods- dynamic charts, or tables-for viewing the individual or system-wide monitored servers and services listed in the following table.
| Adobe Flash Player must be activated to enable views of the dynamic charts. |
| Option | Description |
|---|---|
Server Status |
Server, Service, and Time details for each server monitored by the Collaborator. |
Advanced Statistics |
System-wide Information page for Advanced Statistics, which allows you to set up a new monitoring chart using parameters from the selection fields available from this page: Server, Group, Start, end, and Counters. From this Advanced Statistics page, you can also elect to perform the following operations:
|
Message Count |
System-wide Information page, for Message Counts, to examine charts depicting counts over the last 48, 30, 60, and 365 days. The information summarizes the number of recipients of messages using either SMTP or LMTP. The polling intervals for the counts are posted directly beneath each chart. |
Message Volume |
System-wide Information page, for Message Volume, to view charts depicting the number of recipients of messages using either SMTP or LMTP, and associated message sizes. These counts get summarized in periods over the last 48, 30, 60, and 365 days. The polling intervals for the counts are posted directly beneath each chart. |
Anti-Spam/Anti-Virus |
System-wide Information page, for Anti-Spam/Anti-Virus |
Activity |
Activity, depicting the number of unique messages processed by the AS/AC system over the last 48, 30, 60, and 365 days. The polling intervals for the counts are posted directly beneath each chart. |
Server Statistics |
Access to statistics for a selected Service Host. You can view information for a selected host, as follows:
For the selected Server, the Server Statistics navigation pane provides options to view Disk, Session, Mailbox Quota, Message Count, Message Volume, and Anti- Spam/Anti-Virus Activity. |
Mail Queues |
Tab pages from which to view counts of Deferred, Incoming, Active, Held, and Corrupt statistics for detected mail queues. Each tab page provides summary filtering information and Message details. |
Manage UI
The Manage screen provides the Manage navigation pane, and the Manage pages, which display the tables categorically provided as Accounts, Aliases, Distribution Lists, and Resources that are currently managed by Collaborator.
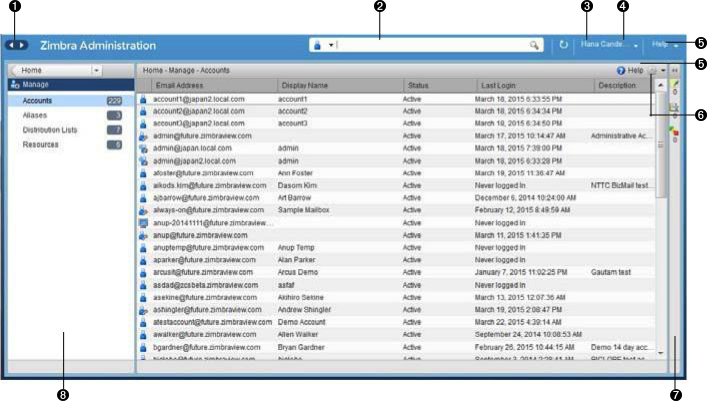
<1> Go to Previous or Next page <2> Search <3> Screen Refresh <4> Current User and Logout Option <5> Help <6> Gear Icon <7> Status Pane <8> Navigation Pane
| Option | Description |
|---|---|
Accounts (count) |
Table of accounts managed by the Collaborator. Actions you can perform:
|
Aliases (count) |
Table of Aliases managed by the Collaborator. Each alias is an email address that forwards all email to a specified account. Actions you can perform:
|
Distribution Lists (count) |
Table of Distribution Lists managed by the Collaborator. A Distribution List is a group of mail addresses contained in a list, with a mail address for the list. When you send a message to a distribution list, you are sending it implicitly to everyone whose address appears in the list. The To: address line displays the distribution list address. Actions you can perform:
|
Resources (count) |
Table of Resources managed by the Collaborator. A Resource is a location or a piece of equipment that supports scheduling for meetings. Actions you can perform:
|
Configure UI
The Configure screen provides the Configure navigation pane, and the Configure pages, which enable configurations for individual or global components.
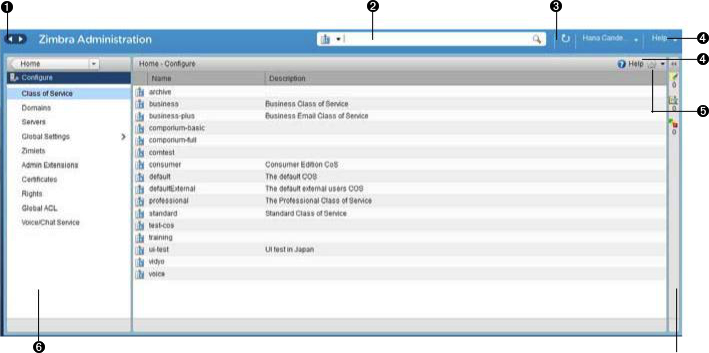
<1> Go to Previous or Next page <2> Search <3> Screen Refresh <4> Help <5> Gear Icon <6> Status Pane <7> Configure Navigation Pane
| Option | Description |
|---|---|
Class of Service |
Displays the COSs managed from this AdministrationConsole.
|
Domains |
Displays the domains managed from this Administration Console.
|
Servers |
Displays the servers managed from this Administration Console.
|
Global Settings |
Provides access to tools you use to set various global parameters for your Zimbra Collaboration. Gear Icon: Save, Download, Update License, Activate License, Manually Activate License |
Zimlets |
Displays the Zimlets managed from this Administration Console.
|
Admin Extensions |
Displays the Admin Extensions managed from this Administration Console.
|
Certificates |
Displays the Certificates managed from this Administration Console.
|
Rights |
Displays the various Rights applicable to this Administration Console.
|
Global ACL |
Displays the Global Access Control Lists managed from this Administration Console.
|
Global Settings UI
Global Settings define the default global values for servers, accounts, COS, and domains. These default values and parameters apply when no specific values and parameters for particular items are in their settings.
You configure the defaults for Global Settings during installation. You can change the settings at any time from Global Settings at the Administration Console.
| Option | Description |
|---|---|
General Information |
For more information, see General Information Configuration |
Attachments |
For more information, see Attachments Configuration. |
MTA |
For more information, see MTA Configuration. |
IMAP |
Enable IMAP service. Changes to these settings do not take effect until the server restarts. |
POP |
Enable POPS3 Service. Changes to these settings do not take effect until the server restarts. |
AS/AV |
Set anti-spam and anti-virus rules. Changes to the Spam-check settings do not take effect until the server restarts. |
Themes |
Changes to the theme settings require flushing of the server theme cache by using Flush Cache on the toolbar in Server settings. For more information, see Color and Logo Management. |
Advanced |
|
Retention Policy |
Set up a retention and deletion time threshold for items in user folders. You can configure retention and deletion policies as a global setting, or configure COS-level policies instead of inheriting from the global settings. |
Proxy |
Set parameters for Web Proxy and Mail Proxy. There are also tools provided for setting Advanced Proxy parameters. |
S/MIME |
(Secure Multipurpose Internet Mail Extensions): Configure the LDAP settings on the S/MIME tab (if S/MIME feature is enabled). Users retrieve private keys from LDAP servers. |
ACL |
(Access Control List): Go to ACE (Access Control Entry) configuration for delegated administration rights granted on selected target(s), to add, edit, or delete an ACE. |
Backup/Restore |
Set parameters for backup-for standard or auto- grouped mode. For more information see Backup and Restore. |
SM |
(storage management): Configure the aging of messages before they move to the secondary volume. |
License |
|
Tools and Migration UI
The Tools and Migration screen provides the Tools and Migration navigation pane, for access to system software management and system backup/restore. Administrators can access and download specific wizards and tools from this page.
<1> Go to Previous or Next page <2> Search <3> Screen Refresh <4> Current User and Logout Option <5> Help <6> Status Pane <7> _Tools and Migration_ Navigation Pane
| Option | Description |
|---|---|
Downloads |
Access Zimbra utilities, which provides downloadable |
Software Updates |
Find out if your system needs a Zimbra Server update or not, and use this page to view polling and email contact information pertinent to software updates for your system. See also Checking for Zimbra Collaboration Software Updates. |
Account Migration |
View tabular details about account migrations, as detected by your system. This page lists total imports and the status of each. This page also provides the name(s) of the owners for each account migration listed. See also Migrating Accounts from a Zimbra Server. |
Client Upload |
Use this page to browse for the latest version of software to be uploaded to your system. After selecting the image, you can use Upload on this page to complete the software upload. |
Backups |
Access a summary view of current free and total space (MB) based on the most recent system backup. You can also choose an administrator from this navigation pane to view their backup history. The history lists labels, start and end times, and success or failure for each backup occurrence. Each of these listings is associated with an identical displayed directory path to the backup target. The section Backup and Restore provides additional information. |
Downloadable Wizards and Connectors
Use the Tools and Migration screen Downloads option to get the tools described in this section.
Zimbra Collaboration Migration Wizard for Exchange/PST (32 bit) |
Get
|
||
Zimbra Collaboration Migration Wizard for Domino |
|
||
Legacy Zimbra Collaboration Migration Wizard for Exchange |
|
||
Zimbra Connector for Outlook MSI Customizer |
Present text file containing functions you can use to customize the standard ZCO MSI. The server name, port, and other variables particular to an organization can be customized. |
||
Zimbra Connector for Outlook Branding MSI |
Get the Windows Visual Basic Script Edition (VBScript Script File) to customize the standard ZCO MSI. Customization replaces all instances of the Zimbra product name and logo. |
Zimbra Connector for Outlook (32 bits) |
This application enables Outlook to synchronize calendar, contacts, and mail with the Zimbra server and access Zimbra Collaboration’s business features. Address books, Contacts, Calendars, Tasks, and mail are synced directly with the Zimbra Collaboration server. |
||
(Legacy) Microsoft Outlook PST Import Tool |
|
||
(Legacy) Migration Wizard for Microsoft Exchange |
|
||
General Migration Wizard |
This tool imports data within Microsoft Exchange servers and Outlook PST files to the Zimbra Server.
|
Search UI
The Search screen displays the Search results from queries made in the Search field in the Administration Console header.
-
When you open this page without entering a search query, All Results is the default search, which displays accounts, domains, and distribution lists in the Content pane.
-
The auto-completion function allows you to enter a partial name, then select a searchable name from the displayed list of matched strings.
-
You can also use the Zimbra mailbox ID number to search for an account. However, to return a search from a mailbox ID, the complete ID string must be entered in the search.
<1> Go to Previous or Next page <2> Search Options <3> Search <4> Screen Refresh <5> Current User and Logout Option <6> Help <7> Gear Icon <8> Status Pane <9> Search Navigation Pane
| Option | Description |
|---|---|
All Result |
View the count and table of all search results. |
Accounts |
View the count and table resulting from a query for Accounts. |
Domains |
View the count and table resulting from a query for Domains. |
Distribution Lists |
View the count and table resulting from a query for Distribution Lists. |
Basic Attributes |
Search for a user by first name, last name, display name, or account ID number. You can search for administrators or delegated administrators only. |
Status |
Search for an account by status: Active, Closed, Locked, Logout, Pending, or Maintenance. |
Last Login Time |
Search for accounts by the last login time. You can specify a date range to search. |
External Email Address |
Search for an account with an external email address. |
COS |
Search for objects by COS or for objects that are not assigned a COS. |
Server |
Search for accounts on selected servers. |
Domains |
Search for accounts on selected domains. |
Saved Searches |
By default, this section includes predefined common search queries. You can also create and save your queries. After you enter the query syntax, click Save Search and provide a name for the search. The search is then added to this Saved Searches section. |
Setting Up a Simple Search
-
At the Search field, use search options from the drop-down selector to define the type of search, as either accounts, distribution lists, aliases, resources, domains, class of service, or all objects.
For accounts, you can search by display name, first/last name, the first part of an email address, alias, delivery address, or mailbox ID.
-
Type the search string into the Search field.
Partial entries are allowed as search criteria, but a search based on mailbox ID must include the complete ID string.
-
Click Search.
The Search page appears, containing results of the search based on your criteria.
-
View the total number of results at the Navigation pane, in Search> All Results.
Help Center UI
The Help Center is a reference of resources available from the online help and documentation, which you can access with the links provided in the Help Center screen. Use this page, also, to access community forums and to view expert responses to the top migration questions.
<1> Go to Previous or Next page <2> Search <3> Screen Refresh <4> Current User and Logout Option <5> Help <6> Status Pane <7> Help Center Navigation Pane
Tools in Collaborator Tables
The selection of a category from the Navigation pane typically results in a tabular display of all managed objects for the selected category. All tables display labeled columns in which to view information such as email addresses, display names, status, last logins, and descriptions (if configured).
Each row in a table enables actions you can perform if you require additional information or access to the configuration for the selected table entry.
| Action at Table Row | Result | |
|---|---|---|
Hold cursor |
Display ID details for the selection, similar to the example at right (invoked from an Accounts row). |
|
Right-click |
Access the popup menu for a selected table row. The popup menus from a typical table may differ from row to row, as demonstrated in the following examples. |
Accounts and Aliases: Dist Lists and Resources: 
|
Double-click |
Leave the current page, and go to the configuration tools you can use for the selection. |
Message of the Day
Global administrators can create the message- or messages-of-the-day (MOTD) that administrators view when logging into the Administration Console.
The MOTD displays during administrative login at the top-left of the Administration Console, similar to the example below.
The message can be closed, replaced, or removed.
Closing a Message of the Day
To remove a message from view, click Close located alongside the message content.
Creating Message(s) of the Day
Use the zimbraAdminConsoleLoginMessage attribute, with guidelines in this section, to create a single message of the day, or to create multiple messages to be displayed.
| When creating a message with your command entry, always place double-quote marks at the beginning and end of the message to be displayed. |
Creating a global message or domain-specific message.
zmprov md <domain> zimbraAdminConsoleLoginMessage "message to display"Creating a multiple-message display:
zmprov md <domain> +zimbraAdminConsoleLoginMessage "second message to display"Removing Message(s) of the Day
Use the zimbraAdminConsoleLoginMessage attribute, with guidelines in this section, to delete a single message of the day, or to delete multiple messages.
| When removing a message with your command entry, use the following guidelines for individual and multiple deletions: |
-
Place a minus sign (-) before the attribute, and double quote marks at the beginning and end of an individual message-id for deletion.
-
Use single quote marks with the attribute to remove all messages.
Removing a specific message:
zmprov md <domain> -zimbraAdminConsoleLoginMessage "message to display"Removing all messages:
zmprov md <domain> zimbraAdminConsoleLoginMessage ''Functional Reference
This section provides birds-eye views of the functions you can use when navigating the Administration Console, in the following topics:
GUI Roadmap
The following illustration provides a high-level view of the Administration Console UI.

Popup Menu Options
You can select options to perform on a selected entity from the navigation pane from the Gear icon or a topical popup menu.
Using the Gear icon
The Gear icon is always located at the upper-right edge of the page view if pertinent to selectable items in the displayed page.
To view the available options, highlight a topic at the navigation pane or in the page view: In the popup, the options that do not apply to your selection are disabled — the remaining enabled options are valid with your selection. The following example demonstrates Gear options based on the selection of a navigation bar topic, versus a table row entry from within the same page view.
The following table provides a high-level view of the operations derived from the Gear icon, which varies for particular functions.
| Navigation Pane Topic | Selections | Options |
|---|---|---|
Home Monitor |
Server Statistics |
View |
Mail Queues |
Flush |
|
Manage |
Accounts |
New, New Administrator, Edit, Delete, Change Password, Invalidate Sessions, View Mail, Move Mailbox, View Rights, Configure Grants |
Aliases |
New, New Administrator, Edit, Delete, Move Alias, Invalidate Sessions, View Mail, Move Mailbox, View Rights, Configure Grants |
|
Distribution Lists |
New, New Administrator, Edit, Delete, View Mail, View Rights, Configure Grants |
|
Resources |
New, New Administrator, Edit, Delete, View Mail, View Rights, Configure Rights |
|
Configure |
Class of Service |
New, Delete, Edit, Duplicate |
Domains |
New, Delete, Edit, Configure GAL, Configure Authentication, View Accounts, Add a Domain Alias, Configure Grants |
|
Servers |
Edit, Flush Cache, Enable Proxy, Disable Proxy |
|
Global Settings |
Save, Download, Update License, Activate License, Manually Activate License |
|
Zimlets |
Deploy, Undeploy, Toggle Status |
|
Admin Extensions |
Deploy, Undeploy |
|
Certificates |
Install Certificate, View Certificate |
|
Voice/Chat Service |
New, Delete, Edit, Generate Session ID |
|
Rights |
View |
|
Global ACL |
Add, Delete, Edit |
|
Tools and Migration |
Account Migration |
Delete Task, Refresh, Migration Wizard |
Software Updates |
Save, Check Now |
|
Backups |
View, Backup, Restore, Configure, Refresh |
|
Search |
All Result |
Delete, Edit, Change Password, View Mail, Move Alias, Invalidate Sessions, Move Mailbox, Download |
Accounts |
||
Aliases |
||
Domains |
||
Distribution Lists |
Using the Topical Popup Menus
You can elect to access options to perform on a selection by using popup menus:
| There are no popup menus in the Navigation Pane. |
The following example demonstrates the popup options provided by a specific selection in the page view.
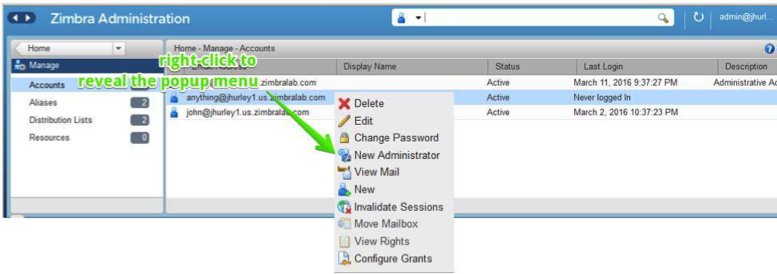
Containers
The Administration Console logically groups a wide range of Configuration options into containers. Applicable configuration options inside these containers are listed in the High-level View of Administration Console UI
By default, all containers on a page are opened (expanded). You can opt to close (collapse) containers - which can free up additional space in a page view - by clicking on collapse/expand located at the upper-left edge of the container.
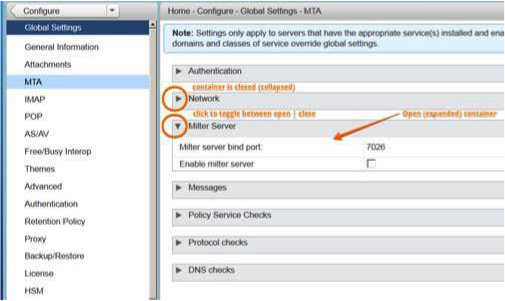
Managing Configuration
The Zimbra components are configured during the initial installation of the software. After the installation, you can manage the following components from either the Administration Console or using the CLI utility.
Help is available from the Administration Console about how to perform tasks from the Administration Console. If the task is only available from the CLI, see Zimbra CLI Commands for a description of how to use the CLI utility.
Global Configuration
Global Settings apply to all accounts in the Zimbra servers. They are initially set during installation. You can modify the settings from the Administration Console.
Configurations set in Global Settings define inherited default values for the following objects: server, account, COS, and domain. If these attributes are set in the server, the server settings override the global settings.
- Admin Console:
-
To configure global settings, navigate to:
Home → Configure → Global Settings
Configured global settings are:
-
Default domain
-
Maximum number of results returned for GAL searches. Default = 100.
-
User views of email attachments and attachment types not permitted.
-
Configuration for authentication process, Relay MTA for external delivery, DNS lookup, and protocol checks.
-
Spam check controls and anti-virus options to check messages received.
-
Free/busy scheduling across a mix of Zimbra Collaboration servers and third party email servers.
-
Customization of themes: modify colors and add your logo.
-
Configuration of company name display for external guest log on, when viewing a shared Briefcase folder.
-
Backup default directory and backup notification information.
-
Global SM schedule that defines when messages should be moved to a secondary storage space.
-
View of current Zimbra license information, license updating, and view the number of accounts created.
General Information Configuration
- Admin Console:
-
Home → Configure → Global Settings
Use the General Information screen to view and set global parameters for servers that have been installed and enabled.
| Settings defined at the server(s) override those configured in the General Information screen. |
-
Modify parameters, as appropriate for your requirements.
-
From the Gear icon, select Save to use your settings.
| Option | Description | ||
|---|---|---|---|
Most results returned by GAL search |
The maximum number of GAL results returned from a user search. This value
can be set by domain: the domain setting overrides the global setting. |
||
Default domain |
Domain that users' logins are authenticated against. |
||
Number of scheduled tasks that can run simultaneously |
Number of threads used to fetch content from remote data
sources.
* If set too low, users do not get their mail from external sources pulled down often enough.
* If set too high, the server may be consumed with downloading this mail and not servicing "main" user requests. |
||
Sleep time between subsequent mailbox purges |
The duration of time that the server should "rest" between purging
mailboxes. If the message purge schedule is set to 0, messages are not
purged, even if the mail, trash and spam message life time is set. |
||
Maximum size of an uploaded file for Briefcase files (KB) |
The maximum size of a file that can be uploaded into Briefcase.
|
||
Admin Help URL |
To use the Zimbra Collaboration Help, you can designate the URL that is linked from the Administration Console Help |
Attachments Configuration
Setting Up Email Attachment Rules
Global email attachment settings allow you to specify global rules for handling attachments to an email message. You can also set rules by COS and for individual accounts. When attachment settings are configured in Global Settings, the global rule takes precedence over COS and Account settings.
- Admin Console:
-
Home → Configure → Global Settings → Attachments
See
Blocking Email Attachments by File type
for information about this section of the screen.
| Option | Description |
|---|---|
Attachments cannot be viewed regardless of COS |
Users cannot view any attachments. This global setting can be set to prevent a virus outbreak from attachments, as no mail attachments can be opened. |
Attachments are viewed in HTML regardless of COS |
Email attachments can only be viewed in HTML. The COS may have another setting but this global setting overrides the COS setting. |
Attachments are viewed according to COS |
This global setting states the COS sets the rules for how email attachments are viewed |
Send blocked extension notification to recipient |
Blocking Email Attachments by File Type
You can also reject messages with certain types of files attached. You select which file types are unauthorized from the Common extensions list. You can also add other extension types to the list. Messages with those type of files attached are rejected. By default the recipient and the sender are notified that the message was blocked.
If you do not want to send a notification to the recipient when messages are blocked, you can disable this option.
- Admin Console:
-
Home → Configure → Global Settings → Attachments
Email Message Size Restriction
As an admin, you can configure a per-user message size limit using the LDAP attribute zimbraMailAttachmentMaxSize.
This allows decoupling the global max message size (zimbraMtaMaxMessageSize) from user-specific settings.
Feature Summary
-
zimbraMtaMaxMessageSizedefines the global maximum message size allowed across the system (default: 10MB). This is a hard limit and cannot be exceeded by any user or COS-level setting. -
zimbraMailAttachmentMaxSizecan be set at the Class of Service (COS) or User level. -
Inheritance applies: COS → User. User-level value overrides COS-level value.
-
The per-user or COS-level limit must not exceed
zimbraMtaMaxMessageSize.
|
Hard Limit: |
Supported Clients
This setting applies across:
-
Web Client
-
Desktop
-
ZCO (Zimbra Connector for Outlook)
Admin Console Configuration
For COS
- Admin Console:
-
Home → Configure → COS → [COS Name] → Preferences → Composing Email
-
Field: Maximum Message Size (MB)
-
Applies to all users under the COS unless overridden at the user level.
-
For User
- Admin Console:
-
Home → Manage → Accounts → [User Name] → Preferences → Composing Email
-
Field: Maximum Message Size (MB)
-
Overrides COS-level setting.
-
MTA Configuration
Use options from the MTA page to enable or disable authentication and configure a relay hostname, the maximum message size, enable DNS lookup, protocol checks, and DNS checks.
- Admin Console:
-
Home → Configure → Global Settings → MTA
| Option | Description | ||
|---|---|---|---|
Authentication |
|
||
Network |
|
||
Milter Server |
|
||
Archiving |
|
||
Messages |
|
||
Policy Service |
|
||
Protocol checks |
|
||
DNS checks |
|
Global IMAP and POP Configuration
Use the IMAP and POP pages to enable global access.
- Admin Console:
-
Home → Configure → Global Settings → IMAP
Home → Configure → Global Settings → POP
| When you make changes to the IMAP or POP settings, you must restart Zimbra Collaboration before the changes take effect. |
IMAP and POP3 polling intervals can be set from the Administration Console
COS Advanced page.
Default = No polling interval.
| If IMAP/POP proxy is set up, ensure that the port numbers are configured correctly. |
With POP3, users can retrieve their mail stored on the Zimbra server and download new mail to their computer. The user’s POP configuration in their Preference → Mail page determines how their messages are downloaded and saved.
Working With Domains
One domain is identified during the installation process. You can add domains after installation. From the Administration Console you can manage the following domain features.
-
Global Address List
-
Authentication
-
Virtual hosts for the domain to establish a default domain for a user login
-
Public service host name that is used for REST URLs, commonly used in sharing.
-
Maximum number of accounts that can be created on the domain
-
Free/Busy Interop settings for use with Microsoft Exchange.
-
Domain SSL certificates
A domain can be renamed and all account, distribution list, alias and resource addresses are changed to the new domain name. The CLI utility is used to changing the domain name. See Renaming a Domain.
| Domain settings override global settings. |
Domain General Information Configuration
Use the New Domain Wizard to set options described in this section.
- Admin Console:
-
Home → 2 Set up Domain → 1. Create Domain…
| Option | Description | ||
|---|---|---|---|
Domain name * |
Enter the host name of the REST URL. This is commonly used for sharing. See Setting up a Public Service Host |
||
Public service protocol |
Select HTTP or HTTPS from the drop-down field. |
||
Public service port |
|||
Inbound SMTP host name |
If your MX records point to a spam-relay or any other external non-Zimbra server, enter the name of the server here. |
||
Description |
|||
Default Class of Service |
This COS (for the domain) is automatically assigned to accounts created on the domain if another COS is not set. |
||
Status |
The domain status is active in the normal state. Users can log in and mail is delivered. Changing the status can affect the status for accounts on the domain also. The domain status is displayed on the Domain → General page. Domain status can be set as follows:
|
Setting up a Public Service Host Name
You can configure each domain with the public service host name to be used for REST URLs. This is the URL that is used when sharing email folders and Briefcase folders, as well as sharing task lists, address books, and calendars.
When users share a Zimbra Collaboration folder, the default is to create
the URL with the Zimbra server hostname and the Zimbra service host
name. This is displayed as https://server.domain.com/service/home/username/sharedfolder. The
attributes are generated as follows:
-
Hostname is server.zimbraServiceHostname
-
Protocol is determined from server.zimbraMailMode
-
Port is computed from the protocol
When you configure a public service host name, this name is used instead of
the server/service name, as https://publicservicename.domain.com/home/username/sharedfolder. The
attributes to be used are:
-
zimbraPublicServiceHostname -
zimbraPublicServiceProtocol -
zimbraPublicServicePort
You can use another FQDN as long as the name has a proper DNS entry to point at 'server' both internally and externally.
Global Address List (GAL) Mode Configuration
The Global Address List (GAL) is your company-wide listing of users that is available to all users of the email system. GAL is a commonly used feature in mail systems that enables users to look up another user’s information by first or last name, without having to know the complete email address.
GAL is configured on a per-domain basis. The GAL mode setting for each domain determines where the GAL lookup is performed.
Use the GAL Mode Settings tool with your domain configuration to define the Global Address List.
- Admin Console:
-
Home → 2 Set up Domain → 1 Create Domain… → GAL Mode Settings
| Option | Description |
|---|---|
GAL Mode |
|
Most results returned by GAL search |
Maximum number of search results that can be returned in one GAL search.
If this value is undefined here, the system will use the value defined in
Global Settings. |
GAL sync account name* |
Read-only field that displays the galsync name and associated domain. |
Datasource name for internal GAL |
Read-only field that displays the name of the internal GAL. |
Internal GAL polling interval |
Define how often — as days, hours, minutes, or seconds — the GAL sync account is to sync with the LDAP server. With the first sync to the LDAP server, all GAL contacts from the LDAP are added to the galsync account’s address book. On subsequent syncs, the account is updated with information about new contacts, modified contacts, and deleted contacts. |
Using GAL sync accounts for faster access to GAL
A GAL sync account is created for the domain when an internal or external GAL is created, and if you have more than one mailbox server, you can create a GAL sync account for each mailbox server in the domain. Using the GAL sync account gives users faster access to auto complete names from the GAL.
When a GAL sync account is created on a server, GAL requests are directed to the server’s GAL sync account instead of the domain’s GAL sync account. The GalSyncResponse includes a token which encodes the GAL sync account ID and current change number. The client stores this and then uses it in the next GalSyncRequest. Users perform GAL sync with the GAL sync account they initially sync with. If a GALsync account is not available for some reason, the traditional LDAP-based search is run.
| The GAL sync accounts are system accounts and do not use a Zimbra license. |
When you configure the GAL sync account, you define the GAL datasource and the contact data is synced from the datasource to the GAL sync accounts' address books. If the mode Both is selected, an address book is created in the account for each LDAP data source.
The GAL polling interval for the GAL sync determines how often the GALsync account syncs with the LDAP server. The sync intervals can be in x days, hours, minutes, or seconds. The polling interval is set for each data source.
When the GAL sync account syncs to the LDAP directory, all GAL contacts from the LDAP are added to the address book for that GAL. During the sync, the address book is updated with new contact, modified contact and deleted contact information. You should not modify the address book directly. When the LDAP syncs the GAL to the address book, changes you made directly to the address book are deleted.
You create GALsync accounts from the Administration Console. The CLI associated with this feature is zmgsautil.
Creating Additional GALsync Accounts
When Zimbra is configured with more than one server, you can add an additional GAL sync account for each server.
- Admin Console:
-
Home → Configure → Domains
-
Select the domain to add another GAL sync account.
-
In the Gear icon, select Configure GAL.
-
Click Add a GAL account.
-
In the GAL sync account name field, enter the name for this account. Do not use the default name.
-
Select the mailbox server that this account will apply to.
-
Enter the GAL datasource name. If the GAL mode is BOTH, enter the data source name for both the internal GAL and the external GAL.
-
Set the GAL polling interval to how often the GAL sync account should sync with the LDAP server to update.
-
Click Finish.
-
Changing GAL sync account name
The default name for the GAL sync account is galsync. When you configure the GAL mode, you can specify another name. After the GAL sync account is created, you cannot rename the account because syncing the data fails.
To change the account name, delete the existing GAL sync account and configure a new GAL for the domain.
- Admin Console:
-
Home → Configure → Domains
-
Select the domain where you want to change the GAL sync account name.
-
In the Gear icon, select Configure GAL to open the configuration wizard and change the GAL mode to internal. Do not configure any other fields. Click Finish.
-
In the domain’s account Content pane, delete the domain’s galsync account.
-
Select the domain again and select Configure GAL to reconfigure the GAL. In the GAL sync account name field, enter the name for the account. Complete the GAL configuration and click Finish. The new account is displayed in the Accounts Content pane.
-
Authentication Modes
Authentication is the process of identifying a user or a server to the directory server and granting access to legitimate users based on user name and password information provided when users log in.
Set the authentication method on a per-domain basis.
- Admin Console:
-
Home → 2 Set up Domain → 1 Create Domain… → Authentication Mode
| Option | Description |
|---|---|
Authentication mechanism |
|
Virtual Hosts
Virtual hosting allows you to host more than one domain name on a server. The general domain configuration does not change.
When you create a virtual host, this becomes the default domain for user login; users can log in without having to specify the domain name as part of their user name.
- Admin Console:
-
Home → 2 Set up Domain → 1 Create Domain… → Virtual Hosts
| Option | Description |
|---|---|
Add virtual host |
Alphanumeric string to identify the virtual host(s) for this domain. The virtual host requires a valid DNS configuration with an A record. To delete a virtual host from the domain, click Remove alongside the host name displayed in this wizard screen. |
To open the Zimbra Classic Web App log in page, users enter the virtual host
name as the URL address. For example, https://mail.company.com.
When the Zimbra login screen displays, users enter only their user name and password. The authentication request searches for a domain with that virtual host name. When the virtual host is found, the authentication is completed against that domain.
Setting Account Limits
You can limit the number of accounts that can be provisioned on a domain. The maximum number of accounts that can be provisioned for the domain can be set when the domain is created. You can also edit the domain configuration to add or change the number.
In the Administration Console this is set for a domain in the Account Limits page. If this page is not configured, no limits on the domain are set.
Resources, spam, and ham accounts are not counted against this limit.
| You cannot exceed the account limit set by the Zimbra Collaboration license. |
When multiple Classes of Service (COS) are available, you can select which classes of service can be configured and how many accounts on the domain can be assigned to the COS. This is configured in the domain’s Account Limits page. The number of COS account types used is tracked. The limits for all COSs cannot exceed the number set for the maximum accounts for the domain.
The number of COS assigned to accounts is tracked. You can see the number assigned/number remaining from any account’s General Information page.
Renaming a Domain
When you rename a domain you are actually creating a new domain, moving all accounts to the new domain and deleting the old domain. All account, alias, distribution list, and resource addresses are changed to the new domain name. The LDAP is updated to reflect the changes.
Before you rename a domain
-
Make sure MX records in DNS are created for the new domain name
-
Make sure you have a functioning and current full backup of the domain
After the domain has been renamed
-
Update external references that you have set up for the old domain name to the new domain name. This may include automatically generated emails that were sent to the administrator’s mailbox such as backup session notifications. Immediately run a full backup of the new domain:
zmprov -l rd [olddomain.com] [newdomain.com]Domain Rename Process
When you run this zmprov command, the domain renaming process goes
through the following steps:
-
The status of the old domain is changed to an internal status of shutdown, and mail status of the domain is changed to suspended. Users cannot login, their email is bounced by the MTA, and accounts, calendar resources and distribution lists cannot be created, deleted or modified.
-
The new domain is created with the status of shutdown and the mail status suspended.
-
Accounts, calendar resources, distribution lists, aliases, and resources are all copied to the new domain.
-
The LDAP is updated to reflect the new domain address.
-
The old domain is deleted.
-
The status for the new domain is changed to active. The new domain can start accepting email messages.
Adding a Domain Alias
A domain alias allows different domain names to direct to a single domain
address. For example, your domain is domain.com, but you want users to have
an address of example.com, you can create example.com as the alias for the
domain.com address. Sending mail to user@example.com is the same as sending
mail to user@domain.com.
| A domain alias is a domain name just like your primary domain name. You must own the domain name and verify your ownership before you can add it as an alias. |
- Admin Console:
-
Home → Configure → Domains, from the Gear icon select, Add a Domain Alias.
Enabling Support for Domain Disclaimers
Disclaimers are set per-domain. When upgrading, an existing global disclaimer is converted to domain specific disclaimers on every domain to preserve behavior with previous releases.
Per domain disclaimer support can be enabled using the following steps:
-
Create a new domain (e.g.
example.com) and account (e.g.user2@example.com).$ zmprov cd example.com cb9a4846-6df1-4c18-8044-4c1d4c21ccc5 $ zmprov ca user2@example.com test123 95d4caf4-c474-4397-83da-aa21de792b6a $ zmprov -l gaa user1@example.com user2@example.com -
Enable the use of disclaimers
$ zmprov mcf zimbraDomainMandatoryMailSignatureEnabled TRUE $ zmprov gcf zimbraDomainMandatoryMailSignatureEnabled zimbraDomainMandatoryMailSignatureEnabled: TRUE -
Add disclaimers to the new domain
$ zmprov md example.com zimbraAmavisDomainDisclaimerText "text disclamer" zimbraAmavisDomainDisclaimerHTML "HTML disclaimer" $ zmprov gd example.com zimbraAmavisDomainDisclaimerText zimbraAmavisDomainDisclaimerHTML # name example.com zimbraAmavisDomainDisclaimerHTML: HTML disclaimer zimbraAmavisDomainDisclaimerText: text disclamer $ zmprov gd eng.example.com # name eng.example.com zimbraAmavisDomainDisclaimerText zimbraAmavisDomainDisclaimerHTML-
On the first MTA:
/opt/zimbra/libexec/zmaltermimeconfig -e example.com Enabled disclaimers for domain: example.comm Generating disclaimers for domain example.com. -
On all additional MTAs:
/opt/zimbra/libexec/zmaltermimeconfig-
To test, send an email from the account (e.g.
user2@example.com) in html and plain text format -
To verify, check emails received with correct HTML disclaimer and plain text disclaimer.
-
To disable for the domain example.com
-
On the first MTA, as the Zimbra user:
/opt/zimbra/libexec/zmaltermimeconfig -d example.com -
On all additional MTAs:
/opt/zimbra/libexec/zmaltermimeconfig
-
-
-
Disabling Disclaimers for Intra-domain Emails
You can enable the option for emails between individuals in the same domain to not have a disclaimer attached.
Set the attribute attachedzimbraAmavisOutboundDisclaimersOnly to TRUE.
To preserve backward-compatibility, this attribute defaults to FALSE.
Disabling the Disclaimer Feature
It is possible to completely remove support for disclaimers by setting the
related attribute to FALSE.
zmprov mcf zimbraDomainMandatoryMailSignatureEnabled FALSEZimlets on the Domain
All Zimlets that are deployed are displayed in the domain’s Zimlets page. If you do not want all the deployed Zimlets made available for users on the domain, select from the list the Zimlets that are available for the domain. This overrides the Zimlet settings in the COS or for an account.
Managing Server Settings
A server is a machine that has one or more of the Zimbra service packages installed. During the installation, the Zimbra server is automatically registered on the LDAP server.
In the Administration Console, you can view the current status of all the servers that are configured with Zimbra software, and you can edit or delete existing server records. You cannot add servers directly to LDAP. The Zimbra Collaboration installation program must be used to add new servers because the installer packages are designed to register the new host at the time of installation.
The server settings that can be viewed from the Administration Console, Configure Servers link for a specific server include:
-
General information about the service host name, and LMTP advertised name and bind address, and the number of threads that can simultaneously process data source imports.
-
A list of enabled services. You can disable and enable the services.
-
Authentication types enabled for the server, setting a Web mail MTA host-name different from global. Setting relay MTA for external delivery, and enabling DNS lookup if required. Enable the Milter Server and set the bind address.
-
Enabling POP and IMAP and setting the port numbers for a server. If IMAP/POP proxy is set up, making sure that the port numbers are configured correctly.
-
Index and message volumes configuration. Setting SM policies.
-
IP Address Bindings. If the server has multiple IP addresses, IP Address binding allows you to specify which interface to bind to.
-
Proxy settings if proxy is configured.
-
Backup and Restore configuration for the server. When backup and restore is configured for the server, this overrides the global backup and restore setting.
Servers inherit global settings if those values are not set in the server configuration. Settings that can be inherited from the Global configuration include MTA, SMTP, IMAP, POP, anti-virus, and anti-spam configurations.
General Server Settings
The General Information page includes the following configuration information:
-
Server display name and a description field
-
Server hostname
-
LMTP information including advertised name, bind address, and number of threads that can simultaneously process data source imports.
Default = 20 threads. -
Purge setting: The server manages the message purge schedule. You configure the duration of time that the server should "rest" between purg-ing mailboxes from the Administration Console, Global settings or Server settings, or General Information page.
Default = message purge is scheduled to run each minute.
When installing a reverse proxy the communication between the proxy server and the backend mailbox server must be in plain text. Checking This server is a reverse proxy lookup target automatically sets the following parameters:
zimbraImapCleartextLoginEnabled TRUE zimbraReverseProxyLookupTarget TRUE zimbraPop3CleartextLoginEnabled TRUE
The Notes text box can be used to record details you want to save.
Change MTA Server Settings
- Admin Console:
-
Home → Configure → Servers → server → MTA
The MTA page show the following settings:
-
Authentication enabled.
Enables SMTP client authentication, so users can authenticate. Only authenticated users or users from trusted networks are allowed to relay mail. TLS authentication when enabled, forces all SMTP auth to use Transport Layer Security (successor to SSL) to avoid passing passwords in the clear.
-
Network settings, including Web mail MTA hostname, Web mail MTA time-out, the relay MTA for external delivery, MTA trusted networks ID, and the ability to enable DNS lookup for the server.
-
Milter Server.
If Enable Milter Server is checked, the milter enforces the rules that are set up for who can send email to a distribution list on the server.
Setting Up IP Address Binding
If the server has multiple IP addresses, you can use IP address binding to specify which specific IP addresses you want a particular server to bind to.
- Admin Console:
-
Home → Configure → Servers → server → IP Address Bindings
| Option | Description |
|---|---|
Web Client Server IP Address |
Interface address on which the HTTP server listens |
Web Client Server SSL IP Address |
Interface address on which the HTTPS server listens |
Web Client Server SSL Client Cert IP Address |
Interface address on which HTTPS server accepting the client certificates listen |
Administration Console Server IP Address |
Administrator console Interface address on which HTTPS server listens |
Managing SSL Certificates for Zimbra
A certificate is the digital identity used for secure communication between different hosts or clients and servers. Certificates are used to certify that a site is owned by you.
Two types of certificates can be used - self-signed and commercial certificates.
-
A self-signed certificate is an identity certificate that is signed by its own creator.
You can use the Certificate Installation Wizard to generate a new self-signed certificate. This is useful when you use a self-signed certificate and want to change the expiration date. Self-signed certificates are normally used for testing.
Default = 1825 days (5 years) -
A commercial certificate is issued by a certificate authority (CA) that attests that the public key contained in the certificate belongs to the organization (servers) noted in the certificate.
When Zimbra Collaboration is installed, the self-signed certificate is automatically installed and can be used for testing Zimbra Collaboration. You should install the commercial certificate when Zimbra Collaboration is used in your production environment.
| ZCO users in a self-signed environment will encounter warnings about connection security unless the root CA certificate is added to the client’s Window Certificate Store. See the Zimbra Wiki article ZCO Connection Security for more information. |
Installing Certificates
To generate the Certificate Signing Request (CSR) you complete a form with details about the domain, company, and country, and then generate a CSR with the RSA private key. You save this file to your computer and submit it to your commercial certificate authorizer.
To obtain a commercially signed certificate, use the Zimbra Certificates Wizard in the Administration Console to generate the RSA Private Key and CSR.
- Admin Console:
-
Home → 1 Get Started → 2. Install Certificates
Use guidelines from the Install Certificates table to set parameters for your certificates.
| Option | Description |
|---|---|
Common Name (CN) |
Exact domain name that should be used to access your Web site securely. Are you going to use a wildcard common name? If you want to manage multiple sub domains on a single domain on the server with a single certificate, check this box. An asterisk (*) is added to the Common Name field. |
Country Name (C) |
Country name you want the certificate to display as our company location |
State/Province (ST) |
State/province you want the certificate to display as your company location. |
City (L) |
City you want the certificate to display as your company location. |
Organization Name (O) |
Your company name |
Organization Unit (OU) |
Unit name (if applicable) |
Subject Alternative Name (SAN) |
If you are going to use a SAN, the input must be a valid domain name. When SAN is used, the domain name is compared with the common name and then to the SAN to find a match. You can create multiple SANs. When the alternate name is entered here, the client ignores the common name and tries to match the server name to one of the SAN names. |
Download the CSR from the Zimbra server and submit it to a Certificate Authority, such as VeriSign or GoDaddy. They issue a digitally signed certificate.
When you receive the certificate, use the Certificates Wizard a second time to install the certificate on Zimbra Collaboration. When the certificate is installed, you must restart the server to apply the certificate.
Viewing Installed Certificates
You can view the details of certificates currently deployed. Details include the certificate subject, issuer, validation days and subject alternative name.
- Admin Console:
-
Home → Configure → Certificates → zmhostname
Certificates display for different Zimbra services such as LDAP, mailboxd, MTA and proxy.
Maintaining Valid Certificates
It is important to keep your SSL certificates valid to ensure clients and environments work properly, as the Zimbra system can become non-functional if certificates are allowed to expire. You can view deployed SSL certificates from the Zimbra administrator console, including their validation days. It is suggested that certificates are checked periodically, so you know when they expire and to maintain their validity.
Install a SSL Certificate for a Domain
You can install an SSL certificate for each domain on a Zimbra Collaboration server. Zimbra Proxy must be installed on Zimbra Collaboration and correctly configured to support multiple domains. For each domain, a virtual host name and Virtual IP address are configured with the virtual domain name and IP address.
Each domain must be issued a signed commercial certificate that attests that the public key contained in the certificate belongs to that domain.
Configure the Zimbra Proxy Virtual Host Name and IP Address.
zmprov md <domain> +zimbraVirtualHostName {domain.example.com} +zimbraVirtualIPAddress {1.2.3.4}| The virtual domain name requires a valid DNS configuration with an A record. |
Edit the certificate for the domain:
- Admin Console:
-
Home → 1 Get Started → 2. Install Certificates
Copy the domain’s issued signed commercial certificates and private key files to the Domain Certificate section for the selected domain.
-
Copy the root certificate and the intermediate certificates in descending order, starting with your domain certificate. This allows the full certificate chain to be validated.
-
Remove any password (passphrase) from the private key before the certificate is saved.
See your commercial certificate provider for details about how to remove the password.
-
Click Upload.
The domain certificate is deployed to
/opt/zimbra/conf/domaincerts
Using DKIM to Authenticate Email Message
Domain Keys Identified Mail (DKIM) defines a domain-level authentication mechanism that lets your organization take responsibility for transmitting an email message in a way that can be verified by a recipient. Your organization can be the originating sending site or an intermediary. Your organization’s reputation is the basis for evaluating whether to trust the message delivery.
You can add a DKIM digital signature to outgoing email messages, associating the message with a domain name of your organization. You can enable DKIM signing for any number of domains that are being hosted by Zimbra. It is not required for all domains to have DKIM signing enabled for the feature to work.
DKIM defines an authentication mechanism for email using
-
A domain name identifier
-
Public-key cryptography
-
DNS-based public key publishing service.
The DKIM signature is added to the email message header field. The header information is similar to the following example.
DKIM-Signature a=rsa-sha1; q=dns;
d=example.com;
i=user@eng.example.com;
s=jun2021.eng; c=relaxed/simple;
t=1117574938; x=1118006938;
h=from:to:subject:date;
b=dzdVyOfAKCdLXdJOc9G2q8LoXSlEniSbav+yuU4zGeeruD00lszZVoG4ZHRNiYzR
Receivers who successfully validate a DKIM signature can use information about the signer as part of a program to limit spam, spoofing, phishing, or other undesirable behavior.
Configure Zimbra Collaboration for DKIM Signing
DKIM signing to outgoing mail is done at the domain level.
To set up DKIM you must run the CLI zmdkimkeyutil to generate the DKIM keys and selector. You then update the DNS server with the selector which is the public key.
-
Log in to the Zimbra server and as zimbra:
/opt/zimbra/libexec/zmdkimkeyutil -a -d <example.com>The public DNS record data that must be added for the domain to your DNS server is displayed. The public key DNS record appears as a DNS TXT-record that must be added for the domain to your DNS server.
Optional. To specify the number of bits for the new key, include
-bin the command line,-b <####>. If you do not add the-b, the default setting is 2048 bits.DKIM Data added to LDAP for domain example.com with selector B534F5FC-EAF5-11E1-A25D-54A9B1B23156 Public signature to enter into DNS: B534F5FC-EAF5-11E1-A25D-54A9B1B23156._domainkey IN TXT "v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC+ycHjGL/mJXEVlRZnxZL/VqaN/Jk9VllvIOTkKgwLSFtVsKC69kVaUDDjb3zkpJ6qpswjjOCO+0eGJZFA4aB4BQjFBHbl97vgNnpJq1sV3QzRfHrN8X/gdhvfKSIwSDFFl3DHewKDWNcCzBkNf5wHt5ujeavz2XogL8HfeL0bTwIDAQA B" ; ----- DKIM B534F5FC-EAF5-11E1-A25D-54A9B1B23156 for example.com
The generated DKIM data is stored in the LDAP server as part of the domain LDAP entry.
-
Work with your service provider to update your DNS for the domain with the DKIM DNS text record.
-
Reload the DNS and verify that the DNS server is returning the DNS record.
-
Verify that the public key matches the private key. See the Identifiers table for
-d,-s, and-xdescriptions./opt/zimbra/common/sbin/opendkim-testkey -d <example.com> -s <0E9F184A-9577-11E1-AD0E-2A2FBBAC6BCB> -x /opt/zimbra/conf/opendkim.confTable 30. Identifiers Parameter Description -dDomain name
-sSelector name
-xConfiguration file name.
Update DKIM Data for a Domain
When the DKIM keys are updated, the DNS server must be reloaded with the new TXT record.
Good practice is to leave the previous TXT record in DNS for a period of time so that email messages that were signed with the previous key can still be verified.
Log in to the Zimbra server and as zimbra:
/opt/zimbra/libexec/zmdkimkeyutil -u -d <example.com>Optional. To specify the number of bits for the new key, include -b in
the command line, -b <####>. If you do not add the -b, the default
setting is 2048 bits.
-
Work with your service provider to update your DNS for the domain with the DKIM DNS text record.
-
Reload the DNS and verify that the DNS server is returning the DNS record.
-
Verify that the public key matches the private key: See the Identifiers table for
-d,-s, and-xdescriptions./opt/zimbra/common/sbin/opendkim-testkey -d <example.com> -s <0E9F184A-9577-11E1-AD0E-2A2FBBAC6BCB> -x /opt/zimbra/conf/opendkim.conf
Remove DKIM Signing from Zimbra
Removing DKIM signing deletes the DKIM data from LDAP, and new email messages are no longer signed for the domain. When you remove DKIM from the domain, it is a good practice to leave the previous TXT record in DNS for some time so that email messages that were signed with the previous key can still be verified.
Use the following command syntax to remove the file:
/opt/zimbra/libexec/zmdkimkeyutil -r -d example.comRetrieve DKIM Data for a Domain
Use the following command syntax to view the stored DKIM information for the domain, selector, private key, public signature and identity:
/opt/zimbra/libexec/zmdkimkeyutil -q -d example.comAnti-spam Settings
Zimbra uses SpamAssassin to control spam. SpamAssassin uses predefined rules as well as a Bayes database to score messages. Zimbra evaluates spam as a percentage value. Messages tagged between 33%-75% spam are delivered to the user’s junk folder. Messages tagged above 75% are not sent to the user and are discarded.
You can change the anti-spam settings.
- Admin Console
-
Home → Configure → Global Settings → AS/AV
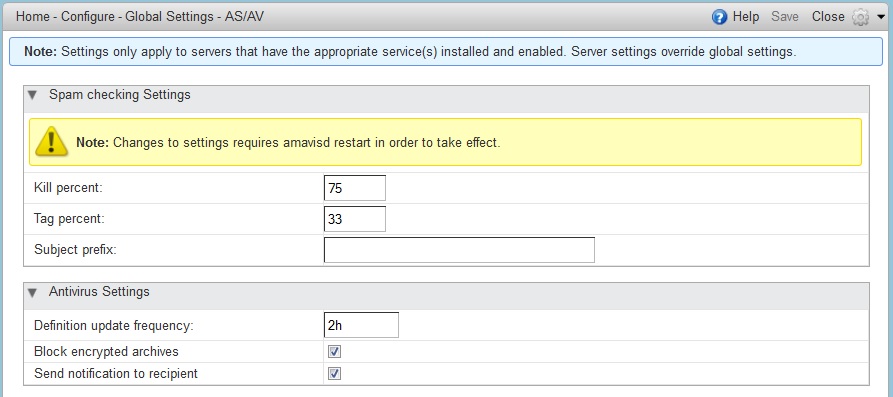
-
At the Anti-Spam fields, enter parameters, as appropriate for your requirements.
-
From the Gear icon, select Save to use your settings.
Table 31. Anti-Spam Option Description Kill percent
Percent that scored mail to be considered as spam, and therefore not to be delivered.
Default = 75%Tag percent
Percent that scores mail to be considered as spam, which should be delivered to the Junk folder.
Default = 33%Subject prefix
Text string to be added to the subject line for messages tagged as spam.
When a message is tagged as spam, the message is delivered to the recipient’s junk folder. Users can view the number of unread messages that are in their junk folder and can open the junk folder to review the messages marked as spam. If you have the anti-spam training filters enabled, when users add or remove messages in the junk folder, their action helps train the spam filter.
RBL (Real time black-hole lists) can be turned on or off in SpamAssassin from the Zimbra CLI.
Anti-Spam Training Filters
The automated spam training filter is enabled by default and two feedback system mailboxes are created to receive mail notification.
-
Spam Training User for mail that was not marked as spam but should be.
-
Non-spam (referred to as ham) training user for mail that was marked as spam but should not have been.
The mailbox quota and attachment indexing is disabled for these training accounts. Disabling quotas prevents bouncing messages when the mailbox is full.
How well the anti-spam filter works depends on recognizing what is considered spam. The SpamAssassin filter learns from messages that users specifically mark as spam by sending them to their junk folder or not spam by removing them from their junk folder. A copy of these marked messages is sent to the appropriate spam training mailbox.
When Zimbra is installed, the spam/ham cleanup filter is configured on only the first MTA. The Zimbra spam training tool, zmtrainsa, is configured to automatically retrieve these messages and train the spam filter. The zmtrainsa script is enabled through a crontab job to feed mail to the SpamAssassin application, allowing SpamAssassin to 'learn' what signs are likely to mean spam or ham. The zmtrainsa script empties these mailboxes each day.
|
New installs of Zimbra limit spam/ham training to the first MTA installed. If
you uninstall or move this MTA, you will need to enable spam/ham training
on another MTA, as one host should have this enabled to run To set this on a new MTA server |
Disabling the Spam Training Mailboxes
The Zimbra default is that all users can give feedback when they add or remove items from their junk folder.
If you do not want users to train the spam filter you can disable this function.
-
Modify the global configuration attributes,
ZimbraSpamIsSpamAccountandZimbraSpamIsNotSpamAccount -
Remove the account addresses from the attributes.
zmprov mcf ZimbraSpamIsSpamAccount '' zmprov mcf ZimbraSpamIsNotSpamAccount ''
When these attributes are modified, messages marked as spam or not spam are not copied to the spam training mailboxes.
Manually Training Spam Filters
Initially, you might want to train the spam filter manually to quickly build a database of spam and non-spam tokens, words, or short character sequences that are commonly found in spam or ham. To do this, you can manually forward messages as message/rfc822 attachments to the spam and non-spam mailboxes.
When zmtrainsa runs, these messages are used to teach the spam filter.
Make sure you add a large enough sampling of messages to get accurate
scores. To determine whether to mark messages as spam at least 200 known
spams and 200 known hams must be identified.
Protect Alias Domains from Backscatter Spam
To reduce the risk of backscatter spam, you can run a service that runs a Zimbra Access Policy Daemon that validates RCPT To: content specifically for alias domains.
| For information about creating domain aliases, see the Zimbra wiki article Managing Domains. |
-
Set the Postfix LC key.
zmlocalconfig -e postfix_enable_smtpd_policyd=yes -
Define the MTA restriction.
zmprov mcf +zimbraMtaRestriction "check_policy_service unix:private/policy"
The postfix_policy_time_limit key is set because by default the Postfix
spawn(8) daemon kills its child process after 1000 seconds. This is too
short for a policy daemon that might run as long as an SMTP client is
connected to an SMTP process.
Disabling Postfix Policy Daemon
Disable the SMTPD policy.
zmlocalconfig -e postfix_enable_smtpd_policyd=no- Admin Console:
-
Home → Configure → Global Settings → MTA
Define the policy restriction.Setting Email Recipient RestrictionsRealtimeBlackhole Lists and Realtime Right-Hand Side Blocking/Black Lists can be turned on or off in the MTA.
For protocol checks, the following three RBLs can be enabled:
-
tname
-
Client must greet with a fully qualified hostname -
reject_non_fqdn_hostname -
Sender address must be fully qualified - reject_non_fqdn_sender
Hostname in greeting violates RFC - reject_invalid_host
zmprov mcf -zimbraMtaRestriction "check_policy_service unix:private/policy"The following RBLs can also be set.
-
reject_rbl_client cbl.abuseat.org -
reject_rbl_client bl.spamcop.net -
reject_rbl_client dnsbl.sorbs.net -
reject_rbl_client sbl.spamhaus.org
As part of recipient restrictions, you can also use the
reject_rbl_client <rbl hostname> option.
- Admin Console:
-
Home → Configure → Global Settings → MTA → DNS Checks
Use the DNS tools in MTA configuration to define the restriction lists.
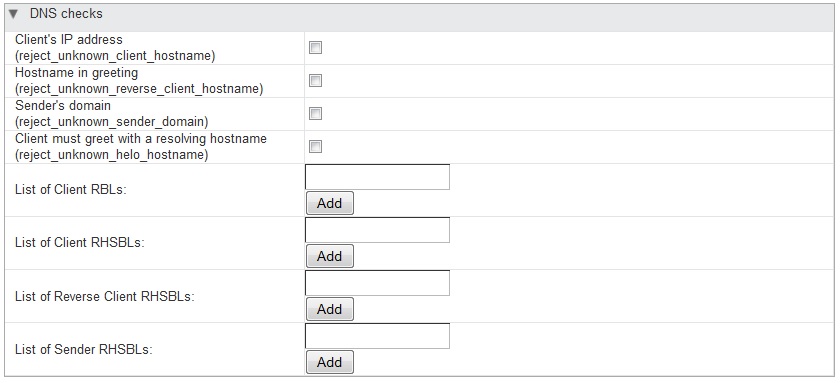
For a list of current RBL’s, see the Comparison of DNS blacklists article.
Adding RBLs with the CLI
-
View the current RBLs.
zmprov gacf zimbraMtaRestriction -
Add new RBLs: list the existing RBLs and the new Add, in the same command entry. For 2-word RBL names, surround the name with quotes in your entry.
zmprov mcf zimbraMtaRestriction [RBL type]
zmprov mcf \
zimbraMtaRestriction reject_invalid_hostname \
zimbraMtaRestriction reject_non-fqdn_hostname \
zimbraMtaRestriction reject_non_fqdn_sender \
zimbraMtaRestriction "reject_rbl_client cbl.abuseat.org" \
zimbraMtaRestriction "reject_rbl_client bl.spamcop.net" \
zimbraMtaRestriction "reject_rbl_client dnsbl.sorbs.net" \
zimbraMtaRestriction "reject_rbl_client sbl.spamhaus.org"Setting Global Rule for Messages Marked as Both Spam and Whitelist
When you use a third-party application to filter messages for spam before messages are received by Zimbra, the Zimbra global rule is to send all messages that are marked by the third-party as spam to the junk folder. This includes messages that are identified as spam and also identified as whitelisted.
If you do not want messages that are identified as whitelisted to be sent
to the junk folder, you can configure zimbraSpamWhitelistHeader and
zimbraSpamWhitelistHeaderValue to pass these messages to the user’s
mailbox. This global rule is not related to the Zimbra MTA spam filtering
rules. Messages are still passed through a user’s filter rules.
To search the message for a whitelist header:
zmprov mcf zimbraSpamWhitelistHeader <X-Whitelist-Flag>To set the value:
zmprov mcf zimbraSpamWhitelistHeaderValue <value_of_third-party_white-lists_messages>Anti-virus Settings
Anti-virus protection is enabled for each server when the Zimbra software is installed. The anti-virus software is configured to send messages that have been identified as having a virus to the virus quarantine mailbox. An email notification is sent to recipients letting them know that a message has been quarantined. The quarantine mailbox message lifetime is set to 7 days.
From the Admin Console, you can specify ho aggressively spam is to be filtered in your Zimbra Collaboration.
- Admin Console:
-
Home → Configure → Global Settings → AS/AV

-
At the Anti-Virus fields, enter parameters, as appropriate for your requirements.
-
From the Gear icon, select Save to use your settings.
| Option | Description |
|---|---|
Definition update frequency |
By default, the Zimbra MTA checks every two hours for any new anti-virus updates from ClamAV. The frequency can be set between 1 and 24 hours. |
Block encrypted archives |
Restrict encrypted files, such as password protected zipped files. |
Send notification to recipient |
To alert that a mail message had a virus and was not delivered. |
During Zimbra Collaboration installation, the administrator notification address for anti- virus alerts is configured. The default is to set up the admin account to receive the notification. When a virus has been found, a notification is automatically sent to that address.
| Updates are obtained via HTTP from the ClamAV website. |
Zimbra Free/Busy Calendar Scheduling
The Free/Busy feature allows users to view each other’s calendars for efficiently scheduling meetings. You can set up free/busy scheduling across Zimbra and Microsoft Exchange servers.
Zimbra can query the free/busy schedules of users on supported Microsoft Exchange servers and also can propagate the free/busy schedules of Zimbra users to the Exchange servers.
To set free/busy interoperability, the Exchange systems must be set up as described in the Exchange Setup Requirements section, and the Zimbra Collaboration Global Config, Domain, COS and Account settings must be configured. The easiest way to configure Zimbra Collaboration is from the Administration Console.
Exchange Setup Requirements
The following is required to set up the free/busy feature:
-
Either a single Active Directory (AD) must be in the system or the global catalog must be available.
-
The Zimbra Collaboration server must be able to access the HTTP(S) port of IIS on at least one of the Exchange servers.
-
Web interface to Exchange public folders needs to be available via IIS. (
http://server/public/) -
Zimbra Collaboration users must be provisioned as a contact on the AD using the same administrative group for each mail domain. This is required only for Zimbra to Exchange free/busy replication.
-
For Zimbra Collaboration to Exchange free/busy replication, the Exchange user email address must be provisioned in the account attribute zimbra-ForeignPrincipal for all Zimbra Collaboration users.
Configuring Free/Busy on Zimbra Collaboration
To set Free/Busy Interoperability up from the Administration Console, the global config, Domain, COS and Account settings must be configured as described here.
-
Configure the Exchange server settings, either globally or per-domain.
-
Microsoft Exchange Server URL. This is the Web interface to the Exchange.
-
Microsoft Exchange Authentication Scheme, either Basic or Form.
-
Basic is authentication to Exchange via HTTP basic authentication.
-
Form is authentication to Exchange as HTML form based authentication.
-
-
Microsoft Exchange Server Type, either WebDav or ews
-
Select WebDAV to support free/busy with Exchange 2003 or Exchange 2007.
This is for information only, as these versions of Exchange are no longer supported. -
Select ews (Exchange Web Service) to support free/busy with Exchange 2010 SP1 and newer.
-
-
-
Include the Microsoft Exchange user name and password. This is the name of the account in Active Directory and password that has access to the public folders. These are used to authenticate against the Exchange server on REST and WebDAV interfaces.
-
Add the o and ou values that are configured in the legacyExchangeDN attribute for Exchange on the Global Config Free/Busy Interop page, the Domain Free/Busy Interop page or on the Class of Service (COS) Advanced page. Set at the global level this applies to all accounts talking to Exchange.
-
In the Account’s Free/Busy Interop page, configure the foreign principal email address for the account. This sets up a mapping from the Zimbra Collaboration account to the corresponding object in the AD.
To find these settings on the Exchange server, you can run the Exchange
ADSI Edit tool and search the legacyExchangeDN attribute for the o= ,
ou= , and cn= settings.
|
Zimbra Collaboration to Zimbra Collaboration Free/Busy Interoperability
You can set up free/busy interoperability between Zimbra servers. Free/Busy interoperability is configured on each server.
| Each server must be running Zimbra Collaboration 8.0.x or later. |
-
Enter the server host names and ports.
zmprov mcf zimbraFreebusyExternalZimbraURL http[s]://[user:pass@]host:portIf the user:pass is not included, the server runs an anonymous free/busy lookup.
-
Restart the server.
zmcontrol restart -
Repeat these steps at all other servers.
Setting Up S/MIME
S/MIME is a standard to send secure email messages. S/MIME messages use digital signature to authenticate and encrypt messages.
Currently, there are two different methods for providing the S/MIME feature
-
The old client based solution which requires Java 1.6 SE deployed on the client machine
-
The new server based solution which does not require Java on the client machine. The server performs all the cryptographic operations. (Recommended)
| This feature is supported only in the Classic Web App. |
Setting up for using the S/MIME feature using the client based solution
Prerequisites
-
To use S/MIME, users must have a PKI certificate and a private key. The private key must be installed in the user’s local certificate store on Windows and Apple Mac and in the browser certificate store if they use the Firefox browser. See the appropriate computer or browser documentation for how to install certificates.
-
Users can use any of the following browsers:
-
Mozilla Firefox 4 or later
-
Internet Explorer 8, 9
-
Chrome 12 or later
-
-
Users computers must have Java 1.6 SE deployed to use S/MIME. If they do not, they see an error asking them to install it.
S/MIME License
You must have a Zimbra license that is enabled for S/MIME.
Enable S/MIME Feature
- Admin Console:
-
Home → Configure → Class of Service → COS → Features
Home → Manage → Accounts → account → Features
The S/MIME feature can be enabled from either the COS or Account FeaturesTab.
-
Select the COS or account to edit.
-
In the Features tab S/MIME features section, check Enable S/MIME.
-
Click Save.
Importing S/MIME Certificates
Users can send encrypted messages to recipients if they have the recipients' public-key certificate stored in one of the following:
-
Recipient’s contact page in their Address Book.
-
Local OS or browser keystore.
-
External LDAP directory.
The certificates should be published into the LDAP directory so that they can be retrieved from the GAL. The format of the S/MIME certificates must be X.509 Base64 encoded DER.
Configure External LDAP Lookup for Certificates
If you use an external LDAP to store certificates, you can configure the Zimbra server to lookup and retrieve certificates from the external LDAP, on behalf of the client.
- Admin Console:
-
Home → Configure → Global Settings → S/MIME
Home → Configure → Domains → domain → S/MIME
You can configure the external LDAP server settings from either the Global Settings → S/MIME tab or the Domains → S/MIME tab.
| Global Settings override Domain settings |
-
Edit the global settings page or select a domain to edit. Open the S/MIME tab.
-
In the Configuration Name field, enter a name to identify the external LDAP server. Example,
companyLDAP_1 -
In the LDAP URL field, enter the LDAP server’s URL. Example,
ldap://host.domain:3268 -
To use DN to bind to the external server, in the S/MIME LDAP Bind DN field, enter the bind DN. Example,
administrator@domainIf you want to use anonymous bind, leave the Bind ND and Bind password fields empty.
-
In the S/MIME Ldap Search Base field, enter the specific branch of the LDAP server that should be searched to find the certificates.
Example,
ou=Common Users, DC=host, DC=domainOr, check Automatically discover search base to automatically discover the search base DNs. For this to work, the S/MIME Search Base field must be empty.
-
In the S/MIME Ldap filter field, enter the filter template for the search. The filter template can contain the following conversion variables for expansion:
-
%n- search key with@(or without, if no@was specified) -
%u- with@removed (For example,mail=%n)
-
-
In the S/MIME Ldap Attribute field, enter attributes in the external LDAP server that contain users' S/MIME certificates. Multiple attributes can be separated by a comma (
,).Example, "userSMIMECertificate, UserCertificate"
-
Click Save.
To set up another external LDAP server, click Add Configuration.
Setting up for using the S/MIME feature using the server based solution
Prerequisites
Same as for the client based S/MIME solution except that Java is not required on the client machine. The private key is also not required to be on the client machine’s local/browser certificate store.
S/MIME License
Same as for the client based S/MIME solution
Enable S/MIME Feature
Same as for the client based S/MIME solution
Importing S/MIME Certificates
Same as for the client based S/MIME solution except that the recipients' public-key certificate no longer needs to be stored in the Local OS or browser keystore. The certificate can be published to all other places mentioned in previous S/MIME version.
List of LDAP attributes introduced to support the server based S/MIME solution
-
zimbraSmimeOCSPEnabled-
Used by server at the time of validating the user as well as public certificates
-
If
TRUE, the revocation check will be performed during certificate validation -
If
FALSE, the revocation check will not be performed during certificate validation
-
-
zimbraSmimePublicCertificateExtensions-
The supported public certificate file extensions separated by commas
-
Contains the list of supported formats for the
userCertificateLDAP attribute -
Default values:
cer,crt,der,spc,p7b,p7r,sst,sto,pem -
Zimbra Classic Web App retrieves the supported file formats or extensions for uploading public certificate from the server
-
-
zimbraSmimeUserCertificateExtensions-
The supported public certificate file extensions separated by commas
-
Contains the list of supported formats for the userSmimeCertificate LDAP attribute
-
Default values:
p12,pfx -
Zimbra Classic Web App retrieves the supported file formats or extensions for uploading public certificate from the server
-
Process for Adding the CA certificate to the mailbox truststore for S/MIME
S/MIME uses the mailbox trust store path and its password which are defined in localconfig.xml
The key names are:
-
mailboxd_truststore
-
mailboxd_truststore_password
If the mailboxd_truststore key is not defined in localconfig.xml, by default the value of mailboxd_truststore is:
-
<zimbra_java_home>/jre/lib/security/cacerts
A CA certificate can be imported to the mailbox trust store by executing the following command:
keytool -import -alias -keystore <mailboxd_truststore path> -trustcacerts -file <CA_Cert>Email Retention Management
You can configure retention policies for user account’s email, trash, and junk folders. The basic email retention policy is to set the email, trash and spam message lifetime in the COS or for individual accounts.
You can set up specific retention policies that users can enable for the Inbox and other email folders in their account. Users can also create their own retention policies.
You can enable the dumpster feature to save messages that are deleted from Trash. When a message reaches the end of its retention lifetime, based on email lifetime rules or deletion policies, the message is moved to the dumpster if enabled. Users can recover deleted items from the dumpster until the threshold set in the Visibility lifetime in dumpster for end user setting.
If dumpster is not enabled, messages are purged from the server when the email retention lifetime is reached.
You can also set up a legal hold on an account to prevent messages from being deleted.
Configuring Email Lifetime Rules
You can configure when email messages should be deleted from an accounts folders, and the trash and junk folders by COS or for individual accounts.
| Email Lifetime Option | Description |
|---|---|
Email message lifetime |
Number of days a message can remain in a folder before it is purged. This
includes data in RSS folders. |
Trashed message lifetime |
Number of days a message remains in the Trash folder before it is purged. |
Spam message lifetime |
Number of days a message can remain in the Junk folder before it is purged. |
Purging Email Messages
By default, the server purges email messages that have exceeded their lifetime every minute. You can change the duration of time that the server should "rest" between purging mailboxes.
Use the global Sleep Time setting to define duration, in minutes, between mailbox purges.
- Admin Console:
-
Home → Configure → Global Settings → General Information
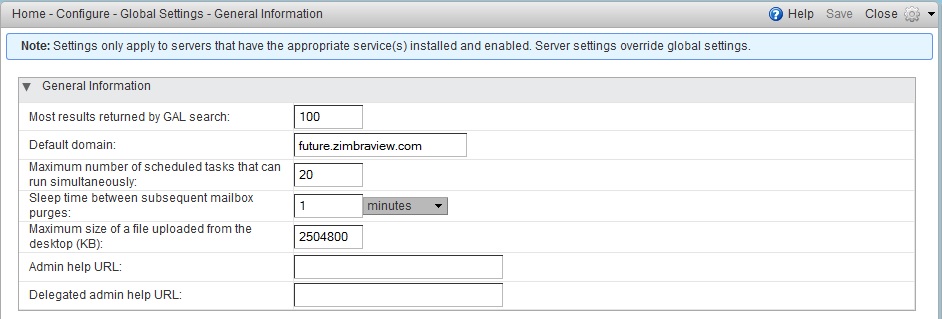
For example, if the purge interval is set to 1 minute, the server purges mailbox1, waits for 1 minute, and then begins to purge mailbox2.
If the message purge schedule is set to 0, messages are not purged even if the mail, trash and spam message lifetime is set.
| Because users cannot view message lifetime settings, you will need to apprise them of your purge policies. |
Configuring Message Retention and Deletion Policies
Retention and deletion policies can be configured as a global setting or as a COS setting. Users can select these policies to apply to their message folders in their account. They can also set up their own retention and deletion policies. Users enable a policy you set up or create their own policies from their folders' Edit Properties dialog box.
Global Retention Policy
System wide retention and deletion policies can be managed from the Administration Console.
Use the global Retention Policy page to set global retention or deletion policies.
- Admin Console:
-
Home → Configure → Global Settings → Retention Policy
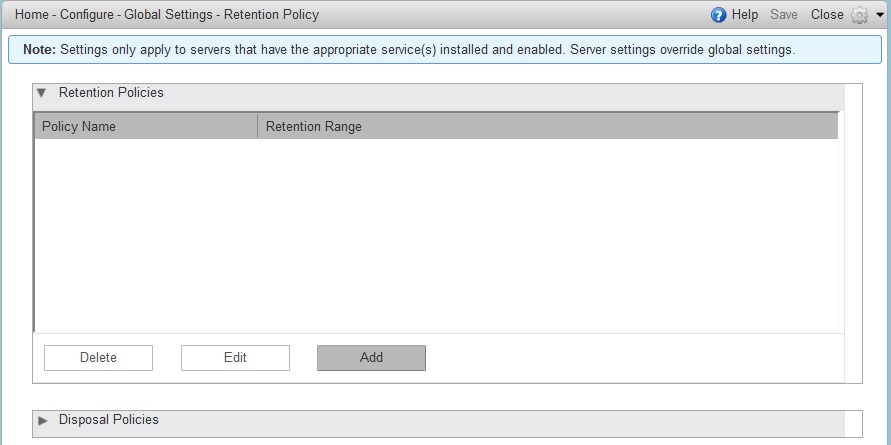
COS Retention Policy
Use the COS Retention Policy page to set retention or deletion for the selected COS.
- Admin Console:
-
Home → Configure → Class of Service → COS → Retention Policy
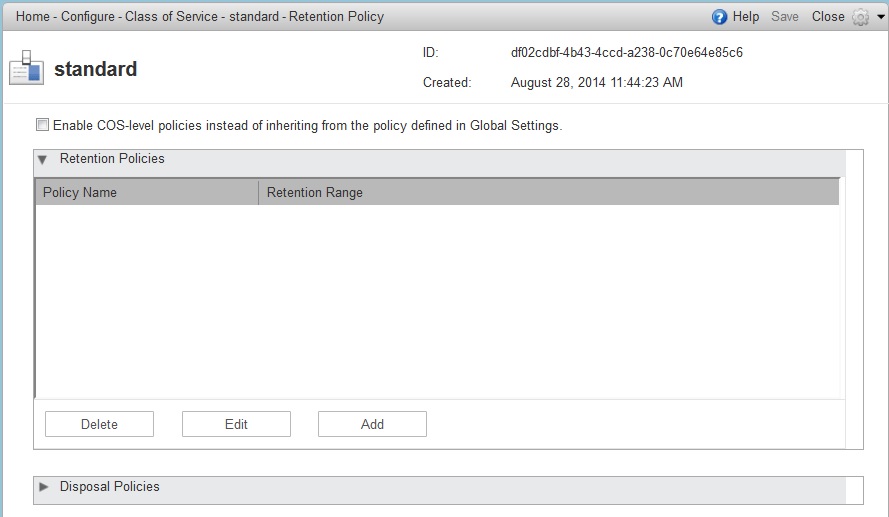
Ensure that the Enable COS-level policies instead of inheriting from the policy defined in Global Settings is enabled.
The retention policy is not automatically enforced on a folder. If users option an item in a folder that has not met the threshold of the retention policy, the following message is displayed, You are deleting a message that is within its folder’s retention period. Do you wish to delete the message?
When the threshold for the deletion policy is reached, items are deleted from the account. They are not sent to the Trash folder. If the dumpster feature is enabled, they are sent to the dumpster, if it is not enabled, they are purged from the server.
How Lifetime and Retention/Deletion Policies Work Together
If the Email Message Lifetime is set to a value other than zero (0), this setting applies in addition to the disposal or retention policy values applied to a folder. For example:
Email Message Lifetime is set to 120 days
-
Folder A has a policy with a disposal threshold of 360 days. Messages in Folder a are disposed of in 120 days.
-
Folder B has a policy with disposal threshold of 90 days. Messages in Folder B are disposed of in 90 days.
-
Folder C has a policy with retention range of 150 days. Messages in Folder C are disposed of in 120 days.
Managing the Dumpster
When a message, trash or spam lifetime has been reached, the message is moved to the dumpster if the feature is enabled. When users right-click on Trash, they can click Recover deleted items to retrieve items from their trash that have been deleted in the last x days. This threshold is based on the Visibility lifetime in dumpster for end user setting.
The Retention lifetime in dumpster before purging setting sets retention lifetime for items in dumpster. Items in dumpster older than the threshold are purged and cannot be retrieved.
Administrators can access the individual dumpster’s content, including spam, and they can delete data at any time before the message lifetime is reached.
Searching for an item in the dumpster folder
zmmailbox -z -m <user@example.com> search --dumpster -l <#> --types <message,contact,document> <search-field>The search field can be a date range: 'before:mm/dd/yyyy and after:mm/dd/yyyy' or emails from or to a particular person: 'from:Joe', etc.
Deleting items in the dumpster folder
Items in the dumpster folder can be deleted with the CLI or from the Administration Console:
zmmailbox -z -m <user@example.com> -A dumpsterDeleteItem <item-ids>- Admin Console:
-
Home → Configure → Class of Service → COS → Features → General Features
-
Enable (check) the Dumpster folder checkbox.
-
To set Visibility lifetime in dumpster for end user, go to the Timeout Policy section on COS' Advanced page
-
To set Retention lifetime in dumpster before purging, go to the COS’s Advanced page, Email Retention Policy section.
-
Configure Legal Hold on an Account
If the dumpster folder feature is enabled, you can set up a legal hold to preserve all items in user accounts.
When dumpster is enabled, Can purge dumpster folder is also enabled. Disabling this feature turns off purging of items in the user’s dumpster. This can be set on a COS or for individual accounts. When Can purge dumpster folder is enabled, any deletion policies set up on the accounts' folders are ignored.
Configure legal hold:
- Admin Console:
-
Home → Configure → Class of Service → COS → Features
Home → Manage → Accounts → account → Features
Deselect Can purge dumpster folder on the Features page.
Customized Admin Extensions
Developers can create and add custom modules to the Zimbra Administration Console user interface, to provide new views, manage new data objects, extend existing objects with new properties, and customize existing views.
For the most up-to-date and comprehensive information about how to create an extended Administration Console UI module, go to the Zimbra wiki Extending Admin UI article located at Extending_Admin_UI.
All Zimbra extensions currently incorporated at the Administration Console UI are listed in the content pane as view only.
Only those created by you can be removed (see also Removing Admin Extension Modules).
Deploying New Administration Console UI Modules
- Admin Console:
-
Home → Configure → Admin Extensions
Save the module zip file to the computer you use to access the
Administration Console.
-
From the Gear icon, select Deploy to present the Deploying a Zimlet or an extension dialog.
-
Browse to the custom module
zipfile you need to upload. -
Click Deploy.
The file is uploaded and the extension is immediately deployed on the server.
Removing An Admin Extension Module
Deleting an Admin Extension results in removal of the selected extension
and all associated files. This action does not delete the originating zip
file.
- Admin Console:
-
Home → Configure → Admin Extensions
Use steps in this section to remove custom Admin Extensions.
-
Select the module to remove, and select Undeploy from the Gear icon. A confirmation query is presented.
-
At the confirmation query, click Yes to proceed.
Ephemeral Data
There are 3 main types of ephemeral data stored in LDAP during normal operation of Zimbra Collaboration.
-
Last Logon Time Stamps (
zimbraLastLogonTimestamp) -
Auth Tokens (
zimbraAuthTokens) -
CSRF Tokens (
zimbraCsrfTokenData)
On small systems, storage of these types of ephemeral data may be done in the LDAP Server. However, mail systems with large numbers of active users have been found to overload LDAP for short-lived data storage. Therefore, the preferred option is to store this ephemeral data using an external server.
| This document does not cover how to install and maintain the ephemeral storage server. |
Configuring the storage location of ephemeral data is done through the following LDAP attribute:
Attribute |
Format |
Description |
zimbraEphemeralBackendURL |
[backend name]:[params] |
Ephemeral Backend URL Configuration |
The two currently supported Ephemeral Data backends are:
Backend |
Format |
Description |
LDAP |
ldap://default |
Default configuration |
SSDB |
ssdb:127.0.0.1:8888 |
SSDB server and port |
Frequent authentication requests place a high load on Ephemeral Data storage backend. See the following Zimbra wiki pages for results of authentication-based load tests:
Configuring a Running Zimbra Collaboration to Use SSDB
Configuring an already running Zimbra Collaboration installation
to utilize SSDB instead of LDAP for short-lived data storage is done through the following process:
-
Install
SSDBand note the IP address and port configured since you will need this data for the next steps. Refer to Overview of Configuration Options for more information. -
Migrate any existing short-lived data to
SSDBusing the/opt/zimbra/bin/zmmigrateattrscommand. -
Configure Zimbra Collaboration to utilize
SSDB.
Migration Procedure
-
Access the command prompt on one of the machines in the installation.
-
Migrate existing ephemeral data to the
SSDBbackend using thezmmigrateattrsutility
sudo su - zimbra /opt/zimbra/bin/zmmigrateattrs ssdb:<ip address|hostname>:port # substituting your server values
You may use either an IP address or a hostname for the host portion of the destination URL. Either way, you will need to ensure it resolves to the proper IP address on all machines in the cluster. If the provided SSDB address does not resolve to a functioning backend, the migration process will terminate.
-
Configure Zimbra Collaboration to use
SSDB:
sudo su - zimbra zmprov mcf zimbraEphemeralBackendURL ssdb:<ip address|hostname>:port # substituting your server values
As with migration, the host and port must resolve to a functioning SSDB backend. Otherwise,
the value of zimbraEphemeralBackendURL will not be changed.
Migration Details
Migration Info
Information about the latest migration process can be viewed by running the command zmmigrateattrs --status.
If the migration is currently in progress, this command may have to be run from a new terminal window.
This command will output three pieces of information:
-
The status of the migration: one of IN_PROGRESS, COMPLETED or FAILED
-
The URL of the SSDB backend acting as the destination
-
A timestamp of when the migration process was initiated
The migration info can be reset with the command zmmigrateattrs --clear. This should only be done if
the status does not reflect the true state of the system.
Changing the Ephemeral Backend URL
When the value of zimbraEphemeralBackendURL is modified, Zimbra Collaboration checks the status of the last known migration.
This can result in one of several scenarios:
-
If the migration is completed and the URL of this migration matches the newly provided value,
zimbraEphemeralBackendURLis changed to the new value and the migration info is reset. This is the expected use case. -
If a migration is currently in progress,
zimbraEphemeralBackendURLwill not be changed. -
If no migration info is available, the migration has failed, or the new URL does not match the migration URL,
zimbraEphemeralBackendURLwill be changed; however, a warning will be logged stating that data is not guaranteed to have been migrated.
Forwarding Ephemeral Data
During the migration process, and until the backend URL is changed, Zimbra Collaboration will store new ephemeral data
both in LDAP and SSDB; this keeps the two backends from getting out of sync. If the new value of zimbraEphemeralBackendURL
is changed to match the migration URL, migration info is reset and the forwarding mechanism is turned off.
If the values do not match, migration info is not reset, and forwarding remains in place.
Note that this means that migration only needs to be run once, even if there is a gap between the initial migration
and URL change. As long as the target backend is never taken offline, it will stay up-to-date. However, if SSDB is
taken offline between the end of the migration and the backend URL change, migration will need to be re-run.
These scenarios are demonstrated below:
Advanced Migration Options
The zmmigrateattrs tool provides several migration options, to be used with careful consideration:
-
The
-ror--dry-runoption outputs the changes to be made for each account to the console, without actually performing the migration. -
The
-nor--num-threadsoption specifies how many threads will be used for migration. Omitting this will result in migration happening synchronously. -
The
-aor--accountoption allows for migration of a comma-separated list of specific accounts. This should be used only for testing or debugging. -
The
-dor--debugoption enables debug logging.
If no attribute names are explicitly passed in as arguments, migration will occur for all known ephemeral attributes, as in the example above.
Migration Limitations
Ephemeral data migration is a one-way process. The zmmigrateattrs script does not support migrating data from SSDB
back into LDAP, nor does it support migrating data between different instances of SSDB. This means that if the value of
zimbraEphemeralBackendURL is reverted back to LDAP after migration, prior authentication data will become inaccessible,
and all user sessions will be invalidated. If migration to a new SSDB backend becomes necessary, the data should be
replicated to the new location prior to changing the value of zimbraEphemeralBackendURL.
There is one exception to this is: the backend can be safely reverted back to LDAP immediately after the switch to
SSDB with minimal loss of data. This is because the original values are retained in LDAP during migration; switching
the backend to SSDB leaves a "snapshot" of ephemeral data in LDAP at the time of the switch. The migration utility
does not currently provide a way to delete this data to free up space; however, it allows for the backend to be reverted.
The more time passes between the initial change and the reversion, the less the LDAP snapshot will reflect the true state
of ephemeral data.
Changes to zmprov
Due to changes in the way multi-valued ephemeral data is stored, the attributes zimbraAuthTokens and zimbraCsrfTokenData
are no longer returned as part of the zmprov ga <account> response. The value of zimbraLastLogonTimestamp is returned
as before, although only if the -l flag is not used, as adding the -l flag will restrict the server to accessing attributes
in LDAP only. It is still possible to modify these attributes using the zmprov ma <account> command, regardless of the
ephemeral backend. In order to do this, the provided attribute value must match its LDAP format: tokenId|expiration|serverVersion
for auth tokens; data:crumb:expiration for CSRF tokens.
Migration CSV Output
Each run of zmmigrateattrs generates a CSV file in the /opt/zimbra/data/tmp/ folder. The file contains migration info
for every migrated account, such as the number of attributes migrated. Note that it is possible for this to be zero,
which can happen if all ephemeral data for an account is already present in the destination store.
If any migrations fail, a cutdown CSV file report detailing only the errors is also created in the same directory. The name(s) of the file(s) are logged at the end of the run.
Account Deletion Behavior
Ephemeral data deletion behavior differs slightly between SSDB and LDAP backends. With SSDB as the backend, account deletion
results in the zimbraLastLogonTimestamp attribute being explicitly deleted from SSDB. zimbraAuthTokens and zimbraCsrfTokenData,
however, are left to be expired by SSDB when the token lifetimes are reached (default of 2 days). Conversely, ephemeral data
in LDAP is wiped immediately as part of the account deletion process.
SSDB Installation and Configuration
Installation
Zimbra Collaboration packages do not include SSDB server and Zimbra Collaboration installation and configuration utilities do not alter SSDB configuration. To install the latest version of SSDB, follow instructions provided by SSDB developer community in SSDB Installation Documentation. Please note, that Zimbra Collaboration has been tested with SSDB version 1.9.5. In order to install SSDB 1.9.5, download stable-1.9.5.zip instead of master.zip when following SSDB installation instructions.
| SSDB does not have encryption or authentication support, this means you have to protect access to it at the network level. |
Overview of Configuration Options
The purpose of this guide is to discuss some of the options available
with SSDB, specifically with regards to:
-
High-availability via master-slave replication
-
High-availability via master-master replication
-
Horizontal scaling, with high-availability, via multi-master configuration.
This guide is not meant to be an exhaustive treatment of the subject.
Also, as of the time of this writing, SSDB and any related packages
must be installed and configured by the system administrator prior to
updating zimbraEphemeralBackendURL and migrating attributes.
SSDB is compatible with Redis clients and
Zimbra Collaboration currently uses a Redis-compatible client for
communication with SSDB, so many of the concepts described herein
are applicable with a Redis backend.
High-availability with Master-Slave replication
Normal Operation
The method described in this document to implement master-slave
replication makes use of Keepalived to
maintain a configured virtual IP address that is bound to the master
SSDB instance under normal conditions.
Fail-over
If Keepalived detects a failure of the master instance, then the
backup instance is promoted to master by re-binding the virtual IP
address to the backup.
High-availability with Master-Master replication
This differs from master-slave replication in that both SSDB
instances are online and accessible. Each replicates changes from the
other. In the example set-up described later, we use
HAProxy as a front-end. Keep in mind that,
for production, you must use a proxy service that is, itself, highly-available.
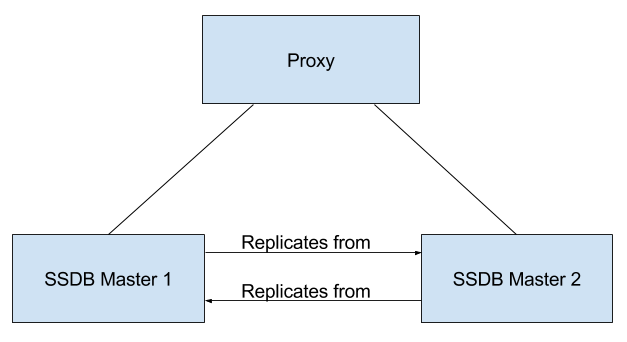
Horizontal Scaling via Multi-Master Configuration
Normally, both SSDB and Redis contain the entire key-space in a
single instance. It is possible to front-end multiple instances using
a service such as twemproxy. It
supports various hashing modes such that the data associated with a
particular key is always stored on the same server. This allows for
horizontal scaling with very large installations.
By configuring each SSDB instance in master-slave configuration, you
get both horizontal scaling and high-availability.
Master-Slave Replication
One way to ensure that SSDB remains highly-available is to set-up
master-slave replication and configure a system that will allow the
backup SSDB instance to automatically take-over in the event that
the primary instance goes down. This document will describe one
technique for accomplishing that goal.
Overview
SSDB will be installed on two servers. It will be configured such
that one server is the designated master and the other server is the
designated slave, or backup, that will constantly replicate changes
from the master server.
Keepalived will also be installed on these two servers. Each
Keepalived instance will monitor the other. In the event that the
master server goes down, Keepalived will detect that failure and
promote the slave, or backup, server to master. Keepalived will
maintain a Virtual
IP address bound to whichever server is the current master.
Zimbra Collaboration will be configured such that the
zimbraEphemeralBackendURL will bind to the Virtual IP address that is
being maintained by Keepalived.
Once the installation and configuration of both the SSDB
master-slave setup and Zimbra Collaboration have been completed, follow the
instructions in Ephemeral Data to update the
zimbraEphemeralBackendURL accordingly.
The example documented here was done on servers running Ubuntu 16.04.
Required Packages
Prerequisites
Install SSDB and Keepalived on two servers in accordance with the
procedure that is applicable to the Linux distribution that you are
using.
Configuration
The following configuration steps assume that you have installed
SSDB to /var/lib/ssdb and that all SSDB configuration files are
located in that same directory. It further assumes that the internal
host addresses are on the 192.168.56/24 network.
-
192.168.56.111- This is IP address of the initial masterSSDBserver -
192.168.56.112- This is the IP address of the initial slaveSSDBserver -
192.168.56.120- This is the virtual IP address that will be maintained byKeepalived.
SSDB Configuration, Designated (Initial) Master
The IP address of this machine is 192.168.56.111.
/var/lib/ssdb/ssdb_master.conf
The key configuration items in the following block are:
-
server/ip- Binding to all available IP addresses -
server/port- Binding to standardSSDBport -
server/deny,server/allow- RestrictSSDBaccess tolocalhostand the internal (host) addresses.`
Only the configuration items related to master-slave replication are shown here.
# ssdb-server config
# MUST indent by TAB!
# relative to path of this file, directory must exists
work_dir = ./var
pidfile = ./var/ssdb.pid
server:
ip: 0.0.0.0
port: 8888
deny: all
allow: 127.0.0.1
allow: 192.168.56
replication:
binlog: yes
# Limit sync speed to *MB/s, -1: no limit
sync_speed: -1
slaveof:
# sync|mirror, default is sync
#type: sync
/var/lib/ssdb/ssdb_slave.conf
The key configuration items in the following block are:
-
server/ip- Binding tolocalhost -
server/port- Binding to standardSSDBport -
slaveof/type-sync -
slaveof/host-192.168.56.112is the otherSSDBserver -
slaveof/port-8888- The standardSSDBport
Again, only the configuration items related to master-slave replication are show.
# ssdb-server config
# relative to path of this file, must exist
work_dir = ./var_slave
pidfile = ./var_slave/ssdb.pid
server:
ip: 127.0.0.1
port: 8888
replication:
binlog: yes
# Limit sync speed to *MB/s, -1: no limit
sync_speed: -1
slaveof:
# sync|mirror, default is sync
type: sync
# Can use host: <hostname> with SSDB 1.9.2 or newer
ip: 192.168.56.112
port: 8888
SSDB Configuration, Designated (Initial) Slave
The IP address of this machine is 192.168.56.112.
The ssdb_master.conf file is identical to that of the designated
master server.
The ssdb_slave.conf file is almost identical to that of the
designated master server. Only the following items differ;
-
slaveof/ip (or host)-192.168.56.111is the otherSSDBserver
Keepalived configuration, Designated (Initial) Master
/etc/keepalived/keepalived.conf
The key configuration items to note are:
-
state- State is set toBACKUPfor both the designated (initial) master and backup servers. In this scenario, thepriorityis used to negotiate which server will assumeMASTERstatus initially. -
nopreempt- In the event that the master server fails and the backup server is promoted to master, this configuration directive will keep the original master from reclaiming that role should it come back online automatically. This is required because it will likely be stale. In this case, when it comes back up, it will remain in backup mode and will begin replicating information from the new master. Note: Human intervention may be required to bring a failed master back into service. -
interface- In this example,enp0s8is the interface identifier for which thevirtual_ipaddresswill be defined. You will choose a value that is appropriate to your installation. -
priority- The designated initial master must have a higher priority than the designated initial backup. -
advert_int- For the purposes of this documentation, the default value of 1 second was use. If you installKeepalived1.2.21or newer, you can specify a floating-point value here; e.g.,0.1(seconds). This will allowKeepalivedto detect a master failure more rapidly. -
notify- This is the path to a script that will be called for state transitions. The full contents of the script is shown below -
virtual_ipaddress- This is the virtual IP address that is maintained byKeepalived.
vrrp_instance VRRP1 {
state BACKUP
nopreempt
interface enp0s8
virtual_router_id 41
priority 200
advert_int 1
notify /var/lib/ssdb/notify.sh
authentication {
auth_type PASS
auth_pass 1234
}
virtual_ipaddress {
192.168.56.120 dev enp0s8 label enp0s8:vip
}
}
/var/lib/ssdb/notify.sh
This is the script that is called by Keepalived during state
transitions. Note that the value assigned to USER should be the
username that owns the SSDB process.
#!/bin/bash
# This must be run as root.
ENDSTATE=$3
NAME=$2
TYPE=$1
LOG=/var/log/keepalived-state-transition.log
LOG_ERROR=0
LOG_WARNING=1
LOG_INFO=2
LOG_DEBUG=3
LOG_LEVEL=$LOG_INFO
KPCFG=/etc/keepalived/keepalived.conf
USER=<SSDB-user-name>
PREFIX=/var/lib/ssdb
function log {
lvl=$1
msg="$2"
if [ $lvl -le $LOG_LEVEL ]
then
now=$(date)
echo "$now [$lvl] $msg" >> $LOG
fi
}
function log_error {
log $LOG_ERROR "$1"
}
function log_warning {
log $LOG_WARNING "$1"
}
function log_info {
log $LOG_INFO "$1"
}
function log_debug {
log $LOG_DEBUG "$1"
}
function backup {
log_info "Transitioning to BACKUP state"
runuser -l $USER -c "${PREFIX}/ssdb-server ${PREFIX}/ssdb.conf -s stop"
runuser -l $USER -c "cp ${PREFIX}/ssdb_slave.conf ${PREFIX}/ssdb.conf"
runuser -l $USER -c "${PREFIX}/ssdb-server -d ${PREFIX}/ssdb.conf"
}
function fault {
log_error "keepalived is in FAULT state"
}
function master {
log_info "Transitioning to MASTER state"
runuser -l $USER -c "${PREFIX}/ssdb-server ${PREFIX}/ssdb.conf -s stop"
runuser -l $USER -c "cp ${PREFIX}/ssdb_master.conf ${PREFIX}/ssdb.conf"
runuser -l $USER -c "${PREFIX}/ssdb-server -d ${PREFIX}/ssdb.conf"
}
case $ENDSTATE in
"BACKUP") # Perform action for transition to BACKUP state
backup
exit 0
;;
"FAULT") # Perform action for transition to FAULT state
fault
exit 0
;;
"MASTER") # Perform action for transition to MASTER state
master
exit 0
;;
*) echo "Unknown state ${ENDSTATE} for VRRP ${TYPE} ${NAME}"
exit 1
;;
esacKeepalived configuration, Designated (Initial) Backup
/etc/keepalived/keepalived.conf
This file is almost identical to the same file on the master node. Exceptions:
-
priority- It is given a lower initial priority. -
It does not contain the
nopreemptoption. Once the backup server has become master due to a failure of the original master, the system should allow for some human intervention before restoring the original server to master status.
vrrp_instance VRRP1 {
state BACKUP
interface enp0s8
virtual_router_id 41
priority 100
advert_int 1
notify /var/lib/ssdb/notify.sh
authentication {
auth_type PASS
auth_pass 1234
}
virtual_ipaddress {
192.168.56.120 dev enp0s8 label enp0s8:vip
}
}
The /var/lib/ssdb/notify.sh for the backup server is identical to
the master.
Master-Master Replication
Overview
Another way to ensure that SSDB remains highly-available is to set-up
master-master replication and configure a proxy that understands
Redis protocol in front of the two SSDB servers. The proxy is
responsible for monitoring the health of the two servers and removing
a failed server from the poop.
The following simplified example uses a single HAProxy instance in
front of two SSDB servers.
Required Packages
Prerequisites
Install SSDB on two servers in accordance with the
procedure that is applicable to the Linux distribution that you are
using. Install HAProxy on an additional server. Note that
Keepalived can be used to configure a
highly-available pool of HAProxy servers.
Configuration
SSDB Configuration, First Master
Notes:
-
Only the configuration related to master-master replication is shown.
# ssdb-server config
## ssdb-server config MUST indent by TAB!
# relative to path of this file, directory must exists
work_dir = ./var
pidfile = ./var/ssdb.pid
server:
ip: 0.0.0.0
port: 8888
deny: all
allow: 127.0.0.1
# e.g., 192.168.56
allow: <ip-address-prefix>
replication:
binlog: yes
# Limit sync speed to *MB/s, -1: no limit
sync_speed: -1
slaveof:
id: svc_2
type: mirror
host: <hostname-of-other-master>
port: 8888
SSDB Configuration, Second Master
Notes:
-
Only the configuration related to master-master replication is shown.
# ssdb-server config
# MUST indent by TAB!
# relative to path of this file, directory must exists
work_dir = ./var
pidfile = ./var/ssdb.pid
server:
ip: 0.0.0.0
port: 8888
deny: all
allow: 127.0.0.1
# e.g., 192.168.56
allow: <ip-address-prefix>
replication:
binlog: yes
# Limit sync speed to *MB/s, -1: no limit
sync_speed: -1
slaveof:
id: svc_1
type: mirror
host: <hostname-of-other-master>
port: 8888
HAProxy Configuration
Notes:
-
Only the configuration related to
SSDBis shown. -
SSDBsupportsRedisnetwork protocol. You can useRedisclients to connect to anSSDBserver and operate on it. This is what Zimbra Collaboration does.
defaults REDIS
mode tcp
timeout connect 4s
timeout server 30s
timeout client 30s
frontend ft_redis
bind <published-ip-address>:8888 name redis
default_backend bk_redis
backend bk_redis
option tcp-check
server R1 <first-master-ip-address>:8888 check inter 1s
server R2 <second-master-ip-address>:8888 check inter 1s
Multi-Master Scaling / Replication
Overview
The details of multi-master configuration will not be covered in this
document. In essence, you will install and configure multiple
independent SSDB master-slave pairs using the instructions included
above. Each pair will be responsible for storing a subset of the total
key-space.
As in the master-master configuration, all of the pairs in the pool of SSDB
servers will be front-ended by a proxy service that understands
Redis protocol. It must also be capable of consistently hashing the
data keys that are presented such that all requests relating to a
particular key always get routed to the same master-slave pair.
LDAP Attributes
The the SSDB backend makes use of a resource pool to manage access to the
SSDB server; threads attempting ephemeral data operations must first
acquire a resource from this pool. To that end, two LDAP attributes have
been introduced to control the pool configuration.
zimbraSSDBResourcePoolSize controls the size of the pool. This determines
how many client threads can simultaneously perform ephemeral API operations.
By default this is set to 0, which results an unlimited pool size.
zimbraSSDBResourcePoolTimeout controls the amount of time a thread will
wait for a resource before throwing an exception. The default is 0,
which results in no timeout. This attribute has no effect when the pool size
is 0, as threads will never have to wait for resources to be freed in order
to perform ephemeral data operations.
A non-zero timeout value is recommended when the pool size is finite.
Otherwise, a lost SSDB connection may cause mailboxd threads to remain
blocked indefinitely, even after the connection is re-established.
In general, the resource pool should be sized such that the mailbox server
is not starved for resources.
Invalidate all user sessions
Depending on your environment, running this command will take some time, there will not be a progress indication. Use the cd command to change into the SSDB installation directory:
./ssdb-cli -h 127.0.0.1 -p 8888 flushdb
SSDB replication may be affected, so it is best to first break replication and run this command on a single master of SSDB and then resume SSDB replication.
Scaling SSDB for Production Load with Zimbra Collaboration
The main characteristics of Zimbra Collaboration production load that affects load on SSDB server are the frequency of authentication requests and frequency of SOAP requests sent by Zimbra Collaboration Web Client and 3rd party SOAP clients. Each authentication request results in a 2 or 3 write operations for SSDB. The write operations update zimbraLastLogonTimestamp, zimbraAuthTokens and zimbraCsrfTokenData values. Note, that zimbraCsrfTokenData is updated only when using a CSRF-enabled SOAP client such as Zimbra Collaboration Web Client. Each authenticated SOAP request results in 2 read operations for SSDB.
Minimum Recommended SSDB Configuration
We recommend that your SSDB server has at least 2GB RAM and 1 CPU. If you plan on running additional tools, such as monitoring and configuration management on your SSDB server, consider increasing memory and adding one more CPU core to accommodate additional software. Check out Zimbra and SSDB Authentication Load Tests for more information.
Conclusion
For installations whose ephemeral data storage requirements will fit
in a single instance, simple master-slave replication is the easiest
to implement and requires the fewest resources. Master-master
replication does allow requests to be load-balanced across both
masters; however, each master is also constantly replicating from the
other, so SSDB must do additional work to maintain
consistency.
Class of Service and Accounts
The Class of Service (COS) assigned to an account determines the default attributes for user accounts, and the features to be enabled or denied. Each account is assigned a COS. The COS controls mailbox quotas, message lifetime, password restrictions, attachment blocking, and server pool usage.
A COS is a global object and is not restricted to a particular domain or set of domains.
You can create and edit the classes of services from the Administration Console:
- Admin Console:
-
Home → Configure → Class of Service → COS
Managing Features and Settings with a COS
A default COS is created when Zimbra Collaboration is installed. You can modify the default COS and create new ones.
From a COS, you can manage the following functions:
-
Features and preferences that users can access.
-
Themes and Zimlets that users can access.
-
Advanced settings including attachment settings, quotas, and password login policies.
-
Web App Versions (Modern Web App and Classic Web App).
-
Web Services and Desktop Clients (EWS, MAPI and more).
-
Offline Mode.
-
Retention policies.
As an example, you could create an Executive COS that is configured to enable all features, provide unlimited mailbox quotas, and never purges messages. Another General-Employee COS may also be created, which enables only the mail feature, sets the mailbox quota, and purges messages every 60 days. Grouping accounts to a specific COS allows you update or change account features in bulk. As such, when the COS is changed, all accounts assigned to the COS are changed.
If a COS is not explicitly set for a new account, or if the COS assigned to a user no longer exists, the default COS is automatically assigned.
You can create a COS and assign that as a default COS for all accounts that are created on that domain. You can create different COSs and specify which ones are available for the domain. If a domain does not have a COS defined, and you do not specify a COS, the original default COS is automatically assigned when an account is created.
Some COS settings can be overridden either by global settings or by user settings. For example:
-
Whether outgoing messages are saved to Sent can be changed from the Zimbra Classic Web App in the user’s preferences.
-
Attachment blocking set as a global setting can override the COS setting.
| Some COS settings assigned to an account are not enforced for IMAP clients. |
Selecting Features and Preferences
All the features available for a COS are displayed in its Features page. From there, you can select or deselect the features you do not want included in the COS.
| Changes made at the account level override the rules in the COS assigned to the account. |
You can define the initial preferences for saving and viewing messages, in the Preferences page. You can also select a specific locale for the Classic Web App and Modern Web App. If a locale is not specified, the browser locale is the default.
For a description of the features and preferences, see Customizing Accounts.
Disabling Preferences
By default, Preferences are enabled, and your users can modify the default preferences that are configured for their accounts.
As the Administrator, you can disable Preferences. As a result, the Preferences page will not display in users mailboxes: they therefore cannot modify the default configuration for features that are set up for their accounts.
| A user can change their Preferences in the Modern Web App under Settings. Disabling Preferences does not have any impact on the Modern Web App. |
Setting Default Time Zone
When using the Classic Web App or the Modern Web App, the time zone setting on the computer is used as the time stamp for displaying received messages and for calendar activities.
The Time Zone value in Calendar settings is used only to identify where the Working Hours start and end times are anchored, and how they appear in Free / Busy information.
Using Server Pools
In an environment with multiple mailbox servers, the COS is used to assign a new account to a mailbox server. When you configure the COS, you select which servers to add to the server pool. Within each pool of servers, a random algorithm assigns new mailboxes to any available server.
You can assign an account to a particular mailbox server when you create an account in the New Account Wizard, Server field. Uncheck auto and enter the mailbox server in the Server field.
Setting Account Quota
An account quota is the storage limit allowed for an account. Email messages, address books, calendars, tasks, and Briefcase files contribute to the volume of the quota. Account quotas can be set for a COS or for individual accounts from the Administration Console.
If you set the quota to 0, accounts do not have a quota.
Viewing Account Quotas
To view account quotas for all accounts on a domain:
- Admin Console:
-
Home → Configure → Domains → domain → Mailbox Quota
Notifying Users When Maximum Quota is Near
Users can be notified that their mailboxes are nearing their quota. The quota percentage can be set and the warning message text can be modified: Go to the Quotas container for a specified Class of Service:
- Admin Console:
-
Home → Configure → Class of Service → COS → Advanced → Quotas
When the displayed/configured threshold is reached, a quota warning message is sent to the user.
Setting Quotas in Domains
You can set a maximum mailbox quota for a domain. The default for the domain mailbox quota is unlimited. The domain quota is the maximum amount of storage that can be used by all mailboxes within the domain.
You can set an aggregate quota as well. The sum of the quotas for all accounts in the domain can exceed the size of the aggregate.
An aggregate quota policy for how to handle messages that are sent or received once the aggregate quota has been reached can be set up. The policy options include:
-
Continue to allow messages to be sent and received as usual.
-
Do not allow messages to be sent.
-
Do not allow messages to be sent or received.
Notifications can be automatically sent when the quota is within a configured percentage of the aggregate quota. A cron tab job runs daily to check the aggregate quota percentage and if the percentage has been reached, the quota warning email is sent.
| When a domain quota is set, the effective quota for an account is the minimum quota setting of either the domain or account. |
To configure domain quotas, go to the Domain Quota Setting container for a specified domain:
- Admin Console:
-
Home → Configure → Domains → domain → Advanced → Domain Quota Setting
Managing Excess Quota
You can set how message delivery is handled when a user’s mailbox exceeds the configured quota. The default behavior is for the MTA to temporarily send the message to the deferred queue. When the mailbox has sufficient space, the message is delivered. You can change this behavior to either have messages bounce back to the sender instead of being sent to the deferred queue first or you can configure to send the message to the mailbox even if the quota has been exceeded.
To bounce messages instead of sending them to the deferred queue:
zmprov mcf zimbraLmtpPermanentFailureWhenOverQuota TRUETo send the message to the mailbox even if the quota has been exceeded:
zmprov mc {cos-name} zimbraMailAllowReceiveButNotSendWhenOverQuota TRUEWhen this attribute is set to TRUE, a mailbox that exceeds its quota is still allowed to receive new mail and calendar invites. This quote bypass is only implemented for messages. All other mail items are still affected by the quota.
Managing Passwords
If you use internal authentication, you can quickly change an account’s password from the Account’s toolbar. The user must be told the new password to log on.
| If Microsoft Active Directory (AD) is used for user authentication, you must disable the Change Password feature in the COS. The AD password policy is not managed by Zimbra. |
If you want to make sure users change a password that you create, you can enable Must Change Password for the account. The user must change the password the next time he logs on.
Password restrictions can be set either at the COS level or at the account level. You can configure settings to require users to create strong passwords and change their passwords regularly, and you can set the parameters to lock out accounts when incorrect passwords are entered.
Directing Users to Your Change Password Page
If authentication is configured as external auth, you can configure Zimbra Collaboration to direct users to your password change page when users change their passwords. You can either set this URL as a global setting or a per domain setting.
Set the zimbraChangePasswordURL attribute to the URL of your password change page.
Change Password in the Classic Web App under Preferences → General links to this URL, and when passwords expire, users are sent to this page. In the Modern Web App, Change Password appears under the account avatar menu, and it will also link to the provided URL.
Modifying the password for the domain:
zmprov md example.com zimbraChangePasswordURL https://auth.example.comConfiguring a Password Policy
If internal authentication is configured for the domain, you can require users to create strong passwords to guard against simple password harvest attacks. Users can be locked out of their accounts if they fail to sign in after the maximum number of attempts configured.
To set password policy, use the Password container for a specified Class of Service:
- Admin Console:
-
Home → Configure → Class of Service → COS → Advanced → Password
The password settings that can be configured are listed below.
| Password Options | Description |
|---|---|
Minimum/Maximum password length |
Specifies the required length of a password. The default minimum and maximum are 6 and 64 characters, respectively. |
Minimum/Maximum password age |
Configures the password expiration date. Users can change their passwords at any time between the minimum and maximum. They must change it when the maximum password age is reached. |
The following settings require users to add complexity to their passwords. |
|
Minimum upper case characters |
Uppercase A - Z |
Minimum lower case characters |
Lowercase a - z |
Minimum punctuation symbols |
Non-alphanumeric, for example !, $, #, &, % |
Minimum numeric characters |
Base 10 digits 0 - 9 |
Minimum numeric characters or punctuation |
Combined Non-alphanumeric and digits |
Minimum number of unique passwords history |
Number of unique new passwords that a user must create before an old password can be reused. |
Minimum password age (Days) |
Minimum days between password changes |
Maximum password age (Days) |
Maximum days between password changes |
Password locked |
Users cannot change their passwords. This should be set if authentication is external. |
Must change password |
User is required to change password at first sign in. |
Change password |
When enabled, users can change their password at any time within the password age settings from their account Preferences tab. |
Password Expiry Reminder
Zimbra Daffodil (v10.1.10) now supports password expiry reminders, the admin users will be able to notify users in advance about their upcoming password expiry. This helps prevent unexpected account lockouts and ensures users update their passwords on time.
Overview
When this feature is enabled, users will receive automated reminder emails starting 10 days before their password expires. These reminders will continue daily until the password is either updated or expires.
LDAP Attributes
The password expiry reminder functionality works based on the following LDAP attributes:
-
zimbraFeaturePasswordExpiryReminderEnabled::
Type: Boolean
Default:FALSE
Description: Enables or disables password expiry reminders. -
zimbraPasswordModifiedTime::
Type: DateTime
Description: Indicates the last time the password was changed. -
zimbraPasswordMaxAge::
Type: Integer (in days)
Default:0(no expiry limit)
Description: Specifies the maximum number of days a password remains valid before requiring a change.
Reminder Eligibility Criteria
A user will receive password expiry reminders only if all the following conditions are met:
-
zimbraFeaturePasswordExpiryReminderEnabledis set toTRUE -
zimbraPasswordMaxAgeis set to a value greater than0 -
The number of days remaining until the password expires is 10 or fewer
Execution and Scheduling
Password expiry reminders are triggered by a daily cron job that runs at 00:00 UTC. The job executes the zmpasswordexpiryreminder script, which performs the following tasks:
-
Identifies all eligible users on the mailbox server
-
Sends reminder emails to each eligible user
This ensures that users receive timely notifications and can take appropriate action before their password expires.
Sample Password Expiry Reminder Email
Subject: Your password expires in {days_remaining} Days
From: Password Expiration Notification <no-reply@{mail_domain}>
To: {username}
Email Body:
"Dear {username},
Your account password expires in {days_remaining} Days, on {expiry_date}.
To maintain access to your account, please reset your password before the expiration date.
You will continue to receive notifications daily until the password is changed or expires.
This is an automated email notification."
Block Common Passwords
Block Common Passwords feature enables an organization to restrict the use of the commonly used passwords when creating users. The list of the common passwords is maintained on the server which is referred to when an administrator tries to create a user with a commonly used password.
The feature is controlled by a local config attribute zimbra_block_common_passwords_enabled and the default value is set to FALSE.
When this feature is enabled, it will also prevent end users from setting their password to a commonly used password via these options:
-
Profile → Change Password in Modern Web App at the top right corner.
-
Forgot Password option on the Login page. (If the Forgot Password feature is enabled for the user).
Enabling Block Common Passwords feature
-
Login as
zimbrauser:
su - zimbra
-
Set the localconfig
zimbra_block_common_passwords_enabledvalue toTRUE:
zmlocalconfig -e zimbra_block_common_passwords_enabled=TRUE
-
Restart mailbox service:
zmmailboxdctl restart
After enabling this feature, if you try to create a user, Password is invalid error is displayed and the user is not created.
Managing Login Policies
You can set the maximum number of failed login attempts before the account is locked out for the specified lockout time. This type of policy is used to prevent password attacks.
To set user login policy, use the Filed Login Policy container for a specified Class of Service:
- Admin Console:
-
Home → Configure → Class of Service → COS → Advanced → Failed Login Policy
| Login Policy Options | Description |
|---|---|
Enable failed login lockout |
This enables "failed login lockout" feature. You can configure the following settings. |
Number of consecutive failed logins allowed |
Number of failed login attempts before the account is locked out. The default is 10. If set to 0, the account is never locked out. |
Time to lockout the account |
Amount of time the account is locked out. If this is set to 0, the account is locked out until the correct password is entered, or the administrator manually changes the account status and creates a new password. The default is 1 hour. |
Time window in which the failed logins must occur to lock the account |
Duration of time after which the number of consecutive failed login attempts is cleared from the log. If this is set to 0, the user can continue attempts to authenticate, no matter how many consecutive failed login attempts have occurred. The default is 1 hour. |
About 2 Factor Authentication
With the 2 Factor Authentication (FA) feature you can apply additional security policies to COS and/or user accounts to provide another layer of authentication during attempts to access the system. This feature must be enabled or disabled in the Admin Console, to manage 2FA functions applicable to user mailboxes.
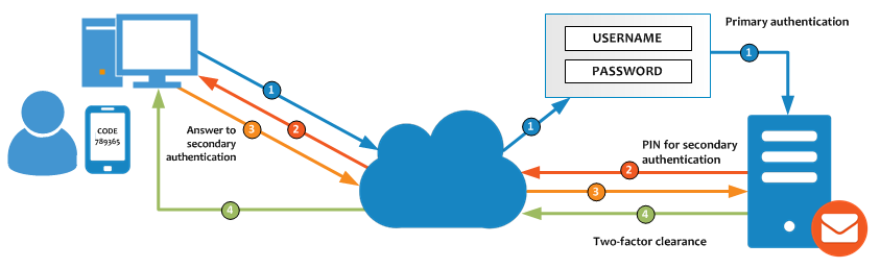
For more information, see 2 Factor Authentication.
Managing Session Timeout Policies
You can set the period of time to allot for user sessions based on various conditions.
To set the session timeout policy use the Timeout Policy container for a specified Class of Service:
- Admin Console:
-
Home → Configure → Class of Service → COS → Advanced → Timeout Policy
| Session Timeout Policy Options | Description |
|---|---|
Admin console auth token lifetime |
Sets a browser cookie that contains the admin auth token. Administrators can open the Administration Console without having to log on again until the auth token expires. The default is 12 hours. |
Auth token lifetime |
Sets a browser cookie that contains the Web App auth token. User can open the Classic Web App or Modern Web App without having to log on again until the auth token expires. The default is 2 days. When it expires, the login page is displayed and the user must log on to continue. |
Session idle lifetime |
How long a user session remains active, if no activity occurs. Activity includes any clickable mouse action, such as viewing folder contents or clicking a button. The default is unlimited. |
You can manually expire a user’s web client session from the Administration Console Expire Sessions link. This forces the current session of the account to expire immediately.
Managing Default External COS
The defaultExternal COS is assigned to external virtual accounts that are created when external users accepts a Zimbra provisioned users'
invitation to share their calendar or briefcase items.
This account is not provisioned on the server, but the external user can sign in to the Classic Web App, create a display name and set a password to view the shared items. The only folders available are for the content they have access to.
The defaultExternal COS is configured with the following general features:
Change password, Change UI themes, HTML compose, Export and Search.
None of the major features are configured.
| The Modern Web App does not currently support login by external users. |
Customizing Accounts
This chapter describes the features and user preferences that can be configured for an account, either from the assigned COS or in an individual account.
| Mailbox features are enabled for Zimbra Classic Web App users. When IMAP or POP clients are used, users might not have these features available. |
| Some features mentioned in the following sections may not be currently available for the Modern Web App. |
| For Classic Web App, Offline mode is no longer supported for Chrome versions 85 and above. Users can still continue to use Offline mode in previous browser versions. |
Messaging and Collaboration Applications
Your COS configuration and assignment of a COS to accounts determines the default settings for account features and the restrictions to be applied to groups of accounts. Individual accounts can be configured differently, and any changes you make override the COS setting. When you update the COS, the changes are not reflected in accounts that have COS overrides.
Email Messaging Features
You configure which email messaging features are enabled. Users can then manage many of the enabled features as preferences.
By default, users manage their own preferences, but you can administratively elect not to allow user modifications to their account preferences. Currently supported Web App Email Messaging Features are listed and described in Email Features.
| Email Messaging Feature | Description | ||
|---|---|---|---|
Enables the email application. Enabled by default. See COS → Features → Major Features container in the Admin Console. |
|||
Conversations |
Messages can be grouped into conversations by a common thread. The default is to thread messages in a conversation by the References header. If there is no References header, the Subject is used to determine the conversation thread. To change the default, update attribute If this feature is enabled, conversation view is the default. You can change the default on the COS Preferences page. Users can also change the default. See COS → Features → Mail Features container in the Admin Console. |
||
HTML compose |
Users can compose email messages with an HTML editor. They can specify default font settings as a preference. See COS → Preferences → Composing Mail container in the Admin Console. |
||
Draft auto save interval |
Frequency of saving draft messages. The default is every 30 seconds. Users cannot change the frequency, but they can turn off the save draft feature. See COS → Preferences → Composing Mail container in the Admin Console. |
||
Mail send later |
When enabled, users can choose Send Later to send a message at a later time. The user configures the data and time for sending. Messages are saved in the Draft folder. See COS → Features → Mail Features container in the Admin Console. |
||
Message priority |
When enabled, users can set the priority of the message. The recipient viewing from the Web App sees the priority flag if it is high or low. See COS → Features → Mail Features container in the Admin Console. |
||
Enable Attachment indexing |
Attachments are indexed. Indexed attachments can be searched. See COS → Advanced → Attachment Settings container in the Admin Console. |
||
Allow the user to specify a forwarding address |
You can specify a default forwarding address that the user can use. Users can change the forwarding address from their account Preferences tab. You can also specify forwarding addresses that are hidden from the user. A copy of a message sent to the account is immediately forwarded to the designated forwarding address. See COS → Features → Mail Features container in the Admin Console. |
||
Out of office reply |
Users can create an email message that automatically replies to incoming messages. By default a message is sent to each recipient only once every seven days, regardless of how many messages that person sends to the address. This setting can be changed in the COS Preferences page, Out of office cache lifetime field. See COS → Features → Mail Features container in the Admin Console. |
||
New mail notification |
Allows users the option to specify an address to be notified of new mail. They can turn this feature on or off and designate an address from their account Preferences tab.
See COS → Features → Mail Features container in the Admin Console. |
||
Persona |
When enabled, users can create additional account names to manage different roles.
Account aliases can be selected for the From name of messages sent from that persona account and a specific signature can be set for the persona account.
The number of personas that can be created is configurable depending on your requirements.
The minimum is 0, and the default is 20 (
See COS → Features → Mail Features container in the Admin Console. |
||
Maximum length of mail signature |
The maximum number of characters that can be in a signature. The default is 1024 characters. The number of signatures users can create is configured in See COS → Preferences → Composing Mail container in the Admin Console. |
||
Advanced search |
Allows users to build a complex search by date, domain, status, tags, size, attachment, Zimlets, and folders. See COS → Features → Search Features container in the Admin Console. |
||
Saved searches |
Users can save a search that they have previously executed or built. See COS → Features → Search Features container in the Admin Console. |
||
Initial search preference |
When enabled, the default search mailbox can be changed. See COS → Features → General Options container in the Admin Console. |
||
External POP access |
When enabled, users can retrieve their POP accounts' email messages directly from their Zimbra account. They add the external account address to their account settings. See COS → Features → Mail Features container in the Admin Console. |
||
External IMAP Access |
When enabled, users can retrieve their IMAP accounts' email messages directly from their Zimbra account. They can add the external account address to their account settings. See COS → Features → Mail Features container in the Admin Console. |
||
Aliases for this account |
You can create aliases for the account. Users cannot change this. |
||
Mail filters |
Users can define a set of rules and corresponding actions to apply to incoming and outgoing mail and calendar appointments. When an incoming email message matches the conditions of a filter rule, the corresponding actions associated with that rule are applied.
See COS → Features → Mail Features container in the Admin Console. |
||
Flagging |
Users can create flags and assign them to messages, contacts, and files in Briefcase folders. (This feature is supported only in the Classic Web App.) See COS → Features → Mail Features container in the Admin Console. |
||
Enable keyboard shortcuts |
Users can use keyboard shortcuts within their mailbox. The shortcut list can be viewed in the Classic Web App from the Username drop-down menu. Keyboard shortcuts are always available in the Modern Web App. The shortcut list can be viewed by typing Ctrl-Q. See COS → Preferences → General Options container in the Admin Console. |
||
Global Address List (GAL) access |
Users can access the company directory to find names for their email messages. See COS → Features → General Features container in the Admin Console. |
||
Autocomplete from GAL |
When enabled, users enter a few letters in their compose header and names listed in the GAL are displayed ranked by usage. See also Autocomplete Ranks Names. See COS → Features → General Features container in the Admin Console. |
||
Offline support for Web App |
When enabled, users can use the offline mode to access their data without network connectivity when using the Zimbra Modern Web App. See also Offline Mode. See COS → Features → General Features container in the Admin Console. |
||
IMAP access |
Users can use third party mail applications to access their mailbox using the IMAP protocol. You can set the polling interval from the COS or Account Advanced page, Data Source → IMAP polling interval section. The polling interval is not set by default. See COS → Features → Mail Features container in the Admin Console. |
||
POP3 access |
Users can use third party mail applications to access their mailbox using the POP protocol. When they retrieve their POP email messages, the messages and attachments are saved on the Zimbra server. Users can configure from their Preferences → Mail page
You can set the polling interval from the COS or Account Advanced page, Data Source → POP3 polling interval section. The polling interval is not set by default. See COS → Features → Mail Features container in the Admin Console. |
Autocomplete Ranks Names
The autocomplete feature displays names ranked with the most frequently recalled contact listed at the top. If the contact name that appears first should not be listed at the top, the user can click Forget and the contact names are re-ranked. (Classic Web App only.)
Email Preferences that Users Manage
The default behavior for many of the preferences listed in this section can be set from either the COS or the Accounts Preferences page. Users can modify the following mail preferences from their account Preferences or Settings in the Classic Web App or Modern Web App.
-
How often, in minutes, that the Web Client checks for new messages:
Check for new mail every…
-
Set or change email message alerts. Alerts can be set up to play a sound, highlight the Mail tab when a message arrives, and flash the browser, depending on which Web App they use.
-
Set the display language for the Classic Web App and Modern Web App. If more than one language locale is installed on Zimbra Collaboration, users can select a locale that is different from the browser language settings.
| The Modern Web App currently supports a subset of the languages available in the Classic Web App, and will fallback to US English if the user’s language locale is not yet supported. |
-
Whether to save copies of outbound messages to the Sent folder.
-
Whether to save a local copy of a message that is forwarded or to have it deleted from their mailbox. (Only the Classic Web App can manage this setting currently.)
-
Whether to compose messages in a separate window. (This feature is supported only in the Classic Web App.)
-
Whether to view mail as HTML for messages that include HTML or to view messages as plain text. (This feature is supported only in the Classic Web App.)
-
Whether to send a read receipt when it is requested.
-
Adjust the default font size for printed messages. The default is 12 points. (This feature is supported only in the Classic Web App.)
-
Users can set up their own Spam mail options of whitelist and blacklist email addresses that are used to filter incoming message from their Preferences Mail folder. The default maximum number of whitelist and blacklist addresses is 100 on each list. This value can be changed using CLI
zmprovfor accounts and COS. The attributes arezimbraMailWhitelistMaxNumEntriesandzimbraMailBlacklistMaxNumEntries. -
Users can modify the following mail preferences under Signatures:
-
Whether to automatically append a signature to outgoing messages.
-
Preferences for how signatures are applied to messages that are replied to or forwarded.
-
Using Import and Export to Save User’s Data
From the Preferences Import/Export page in the Classic Web App or under Accounts → Primary account in the Modern Web App users may export all of their account data, including mail, contacts, calendar, and tasks. By selecting export options, they can export specific items in their account and save the data to their computer.
The account data is saved as a tar-gzipped (.tgz) archive file so that it can be imported to restore their account.
Individual contacts are saved as .csv files, and individual calendar files are saved as .ics files.
The data are copied, not removed from the user’s account.
The exported account data file can be viewed with an archive program such as WinZip. Any of these files can be imported into their account from the same page.
You can turn the Import/Export feature off from the COS or Account Features page, General Features section.
Setting Up RSS Polling Intervals
Users can subscribe to Websites that provide RSS and podcast feeds and receive updated information directly to their mailboxes. The maximum number of feeds that can be returned is 50. RSS feeds count against users' account quota.
The default is to update the RSS data every 12 hours. Users can right-click on an RSS feed folder to manually load new feed.
You can change the polling interval from the Administration Console the COS or Account Advanced page, Data Source → RSS polling interval section.
Contacts Features
Zimbra Contacts allows users to create multiple contact lists and add contact names automatically when mail is received or sent. Users can import contacts into their Address Book.
|
To allow users to share their mail folders, address books, and calendars, enable Sharing on the General Features container: Home → Configure → Class of Service → COS → Features → General Features |
| Feature | Description | COS/Account Tabs |
|---|---|---|
Address Book |
Users can create personal contacts lists. By default, a "Contacts" list and "Emailed Contacts" list are created. |
Features |
Address book size limit |
Maximum number of contacts a user can have in all address books.
|
Advanced |
Users can modify the following Address Book preferences from their account Preferences Address Book page.
To set default behavior:
- Admin Console:
-
Home → Configure → Class of Service → COS → Preferences
Home → Manage → Accounts → account → Preferences-
Enable auto adding of contacts to automatically add contacts to their Emailed Contact list when they send an email to a new address.
-
Enable the ability to use the Global Access List when using the contact picker to look up names.
-
Enable the options to include the GAL addresses and names in shared address books when using autocomplete to address a message.
-
Calendar Features
Zimbra Calendar lets users schedule appointments and meetings, establish recurring activities, create multiple calendars, share calendars with others, and delegate manager access to their calendars. They can subscribe to external calendars and view their calendar information from the Zimbra Classic Web App or Modern Web App. They can also use search for appointments in their calendars.
|
To allow users to share their calendars, address books, and Briefcase files, enable Sharing in the General Features container. |
- Admin Console:
-
Home → Configure → Class of Service → COS → Features → General Features
| Calendar Feature | Description | COS/Account Tabs | ||
|---|---|---|---|---|
Calendar |
Lets users maintain their calendar, schedule meetings, delegate access to their calendar, create multiple personal calendars, and more. |
Features |
||
Group Calendar |
When Group Calendar is not checked, users can create personal appointments and accept invitations to meetings only. The Find Attendees, Schedule and Find Resources tabs are not displayed.
|
Features |
||
Nested Calendars |
Calendars can be nested within Zimbra folders like Mail, Contact, and Calendar folders. The administrator creates a nested list of calendars using CLI. A nested calendar grouping can be imported through migration as well. See example below.
|
|||
Time zone |
Sets the time zone to use for Calendar scheduling. Domain admins set this in the Accounts, General Information page. |
Preferences |
||
Forward calendar invitation to specific addresses |
You can specify email addresses to forward a user’s calendar invitations. Users can also specify forwarding address from the Preferences Calendar folder.
The account the invitation is forwarded to must have admin privileges on the shared calendar to reply to the invitation. |
Accounts Forwarding |
Create a calendar nested under the "Calendar Name" folder:
zmmailbox -z -m user1 cf -V appointment "/Calendar Name/Sub Calendar"Troubleshooting Calendar Appointment Problems
Use the zmcalchk command to check for discrepancy between different users' calendars for the same meeting, and send an email notification regarding the discrepancies.
You can also use this command to notify the organizer and/or all attendees when an appointment is out of sync.
Changing Remote Calendar Update Interval
Remote calendars are updated every 12 hours, by default. The frequency can be modified at the Admin Console.
To modify the frequency of calendar updates in the Admin Console go to the desired COS or Account Advanced page, Data Source → Calendar polling interval field.
Disabling Attendee Edits to Appointments
Attendees can edit appointments in their calendars, but their changes do not affect anyone else.
If the appointment organizer makes changes, these changes overwrite the attendees edits.
You can modify the COS attribute zimbraPrefCalendarApptAllowAtendeeEdit to prevent attendees from editing appointments in their calendar.
zmprov mc <cosname> zimbraPrefCalendarApptAllowAtendeeEdit FALSE| This feature is supported only in the Classic Web App. |
Setting Other User Calendar Preferences
Users can modify the Calendar preferences listed in the Calendar Preference table. You can set the default behavior in the COS or Accounts Preferences page.
| Calendar Preference | Description | ||
|---|---|---|---|
Time zone |
Time zone displayed in the user’s Preferences. See Setting Default Time Zone. If the time zone is configured in the COS, the time zone configured in the domain is ignored. |
||
Number of minutes before an appointment to show reminder |
Sets the minutes before the meeting to send a reminder notice. |
||
Initial calendar view |
Sets the default view. Options are Day, Work Week, 7-Day Week, Month, List, or Schedule. |
||
First day of the week |
Sets the default first day of a user’s work week. |
||
Default appointment visibility |
Options are Public or Private. Sets the default visibility options on the new appointment page. The default is Public, appointments details can be viewed by others. When the default is Private, all incoming calendar invites are marked as private on the user’s calendar and details are hidden when the calendar is shared. |
||
Use iCal delegation model for shared calendars for CalDAV |
Apple iCal can be configured to access users' calendars using the CalDAV protocol. When enabled, shared calendars are displayed in users' iCal account’s Delegation tab and they can delegate access to their calendars. For automatic polling, the polling interval can be set up in the COS or Account Advanced page, Data Source → CalDAV polling interval field. |
||
Enable past due reminders |
Users log into the Classic Web App or Modern Web App, the reminder notifications for the last two weeks pop up for meeting reminders that were not dismissed. When this is disabled, Zimbra Collaboration silently dismisses the old reminders. |
||
Enable toaster notification for new calendar events |
A popup displays in the Classic Web App when new calendar events are received.
|
||
Allow sending cancellation email to organizer |
When users receive an invitation they cannot attend at the scheduled time, they have the option to click Propose New Time and select another time. The meeting organizer receives an email with the proposed time.
|
||
Automatically add invites with PUBLISH method |
A calendar invitation email should have |
||
Automatically add forwarded invites to calendar |
Invites that have been forwarded to users are automatically added to the forwarded recipient’s calendar. |
||
Flash browser title on appointment reminder |
When appointment reminders pop up, the browser flashes until the user closes the pop-up.
|
||
Enable audible appointment notification |
When an appointment reminder pops up, users can be notified by a beep on their computer. Users must have either QuickTime or Windows Media installed.
|
||
Auto-decline invites from users who are denied from inviting this user |
Users can configure who can send them calendar invites. When enabled, an auto-reply message is sent to those users to let them know they do not have permission to invite the user.
|
||
Automatically add appointments when invited |
When enabled, appointments are automatically added to user’s Primary calendar.
|
||
Show declined meetings |
When enabled, declined appointments display on the Classic Web App calendar in a faded view.
|
||
Notify of changes made via delegated access |
Users that delegated their calendar are notified of changes made to an appointment by a delegated access grantee.
|
||
Always show the mini-calendar |
The mini-calendar automatically displays in the Calendar view.
|
||
Use the QuickAdd dialog when creating new appointments |
When is enabled, the QuickAdd dialog displays when users double-click or drag on the calendar in the Zimbra Classic Web App. QuickAdd is always available in the Modern Web App. |
||
Show time zone list in appointment view |
When enabled, a time zones list displays in the event editor along with event time, giving them the opportunity to change time zones while making appointments. |
Setting Up Zimbra Tasks
Zimbra Tasks lets users create to-do lists and manage tasks through to completion.
| To allow users to share their Task lists, enable Sharing in the Features page. Task lists can be shared with individuals, groups, and the public. |
| This feature is supported only in the Classic Web App. |
To enable or disable the Tasks feature:
- Admin Console:
-
Home → Configure → Class of Service → COS → Features
Home → Manage → Accounts → account → Features
Zimbra Classic Web App User Interface Themes
The appearance of the Zimbra Classic Web App user interface can be changed. A number of Zimbra themes are included with Zimbra, and you can create others. You can select a theme to be the default and the themes that users can select to customize their user experience. To develop themes, see Color and Logo Management.
| This feature is supported only in the Classic Web App. |
The following theme usage options can be configured either from COS or by individual accounts.
-
Limit users to one theme
On the Features page, remove the check mark from Change UI Themes. The Classic Web App theme is the theme listed in Current UI theme field on the Themes page.
-
Let users access any of the installed Zimbra themes
If the Change UI Themes is checked, users can access any of the themes that are listed in the Available UI themes list.
Two Factor Authentication
The Two Factor Authentication (2FA) function allows you to configure a secondary set of security requirements that may be applicable to any or all critical mailboxes or users in the environment. You can set 2FA for user accounts and/or class of service.
2FA for New User Account
In the Wizard setup for a new user account, you will find settings for 2FA with other Advanced options.
- Admin Console:
-
Home → 3 Add Accounts → 1. Add Account
— Next until Advanced, scroll down to Two Factor Authentication
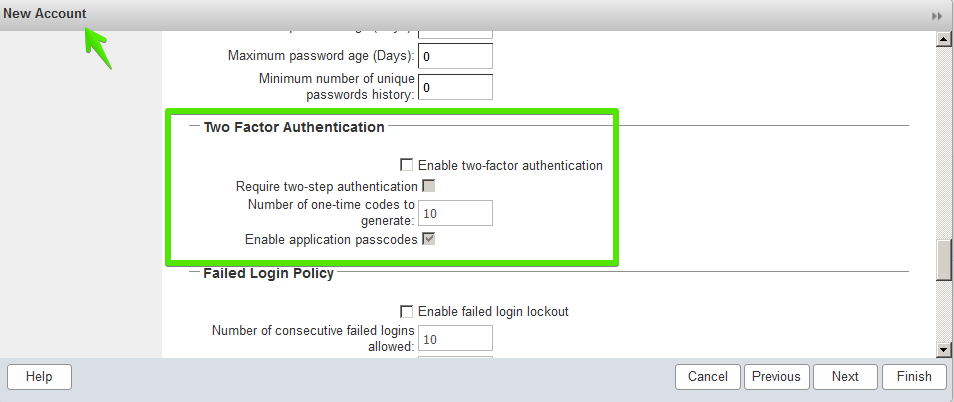
See Two Factor Authentication Parameters for parameter descriptions.
2FA for Existing User Account
For an existing user account, you can apply 2FA settings from the Advanced options.
- Admin Console:
-
Home → Manage → Accounts
Locate the Two Factor Authentication container within the editable configurations for an account:
-
Select an account from the list of accounts.
-
Select Edit from the Gear icon.
— The General Information for the account is now displayed.
-
Select Advanced from the left panel.
-
Scroll down to the Two Factor Authentication container in the main panel.
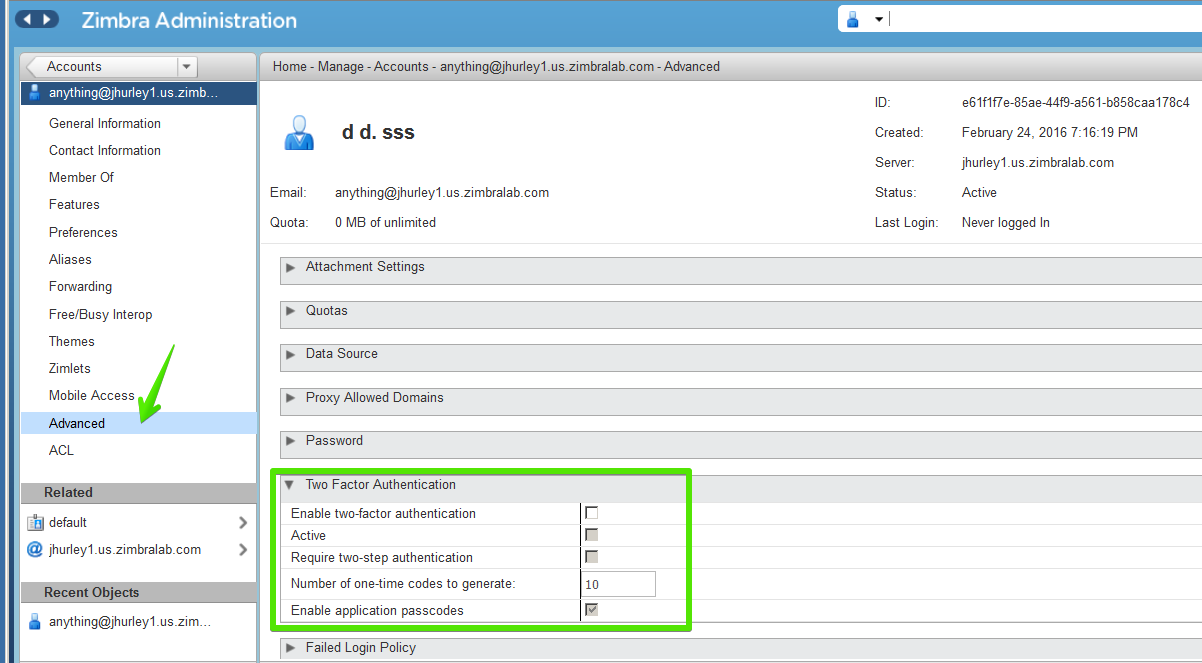
See Two Factor Authentication Parameters for parameter descriptions.
2FA for Class of Service
Parameters you can use to set up 2FA for a Class of Service are included with other Advanced features.
To apply 2FA to a class of service, use the Two Factor Authentication container to set parameters.
- Admin Console:
-
Home → Configure → Class of Service → COS → Advanced → Two Factor Authentication
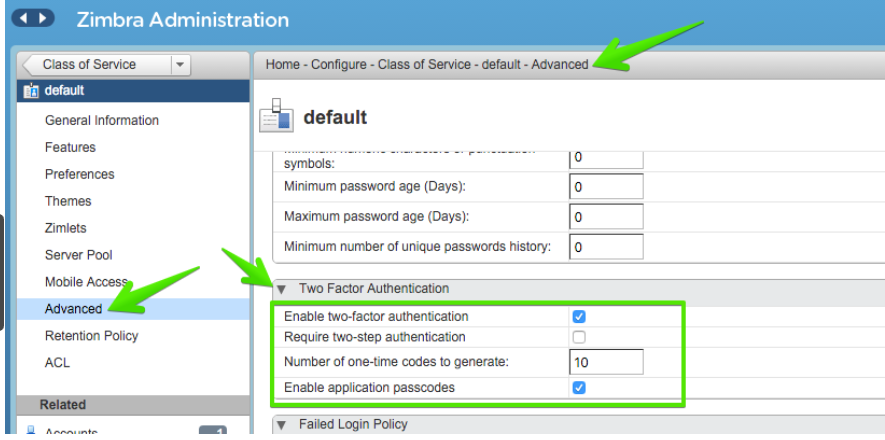
See Two Factor Authentication Parameters for parameter descriptions.
| Parameters | Description |
|---|---|
Enable two factor authentication |
Enable (check) or disable (un-check) this function for the selected COS account. |
Require two-step authentication |
Enable (check) or disable (un-check) mandatory use of this function for the selected COS account. |
Number of one-time codes to generate |
Value to assign maximum number of 6-digit passcodes that may be viewed/used by the account when attempting to access the system. The passcode is presented to the account once the initial login credentials are accepted. Each passcode has a 15-second life cycle. |
Enable application passcodes |
Users can generate exception codes for legacy applications that do not support two-factor authentication. |
Email as an Additional Factor in Two-Factor Authentication
The Email as an Additional Factor in Two-Factor Authentication feature allows users to use their recovery email as an additional authentication factor. This feature enhances account security by adding an extra layer of verification.
Features
-
Email as 2FA Setup: Users can configure their recovery email to be used as an additional factor for authentication.
-
Verification Process: The system prompts users to verify their recovery email even if it is already verified.
-
Fallback Options: Users can use alternative 2FA methods if they are unable to access their recovery email.
-
Preference Selection: Users can select their preferred 2FA method between email and an authenticator app.
-
Administrative Control: Admins can view and manage 2FA preferences for users and reset 2FA settings if needed.
Configuring Email as 2FA
To configure email as a 2FA method:
-
Navigate to Security Settings:
-
Go to the Zimbra Admin Console.
-
Access the security settings for the user or Class of Service (COS).
-
-
Enable Email as 2FA:
-
Ensure that the recovery email field is set up and verified. If not, prompt the user to configure and verify their recovery email.
-
Enable the email option as a valid 2FA method.
-
When the "Status of password reset feature" (zimbraFeatureResetPasswordStatus) is not enabled, a user can directly configure "Email as 2FA". The user is asked to enter an email address (recovery address) during the setup.
|
Admins can access this feature at: Account or COS setting > Features > "Status of password reset feature" in the admin console.
Verification Process
The system sends a verification code to the user’s recovery email. Upon verification, the email becomes an active 2FA method. Users need to verify a recovery address every time "Email as 2FA" is configured.
Fallback Options
Users can use other configured 2FA methods like an authenticator app if they cannot access their recovery email.
Managing User Preferences
-
View User 2FA Preferences:
-
In the Admin Console, navigate to the user’s account settings.
-
View the active 2FA methods and the user’s preferred method.
-
-
Override User 2FA Preferences:
-
Admins can reset or override 2FA settings for users. This is useful in cases of security breaches or for administrative purposes.
-
Use Command-Line Options
-
Enable Email as 2FA for Users:
'zmprov ma user@example.com zimbraTwoFactorAuthEnabled TRUE zimbraTwoFactorAuthMethodAllowed email' 'zmprov ma user@example.com zimbraTwoFactorAuthEnabled TRUE zimbraTwoFactorAuthMethodAllowed app'
If no 2FA method is configured yet and internal secrets data for the user has not been generated, the command `zmprov ma zimbraTwoFactorAuthEnabled TRUE` does not work.
-
Related attributes:
-
zimbraFeatureTwoFactorAuthAvailable– controls whether a user can configure and use 2FA. -
zimbraTwoFactorAuthEnabled– controls whether a user has enabled 2FA (app and/or email method). -
zimbraTwoFactorAuthMethodAllowed– controls which methods are available as 2FA methods for a user. -
zimbraTwoFactorAuthMethodEnabled– controls what method has been enabled (configured) by a user (app and/or email).
-
Mandate Specific 2FA Methods
Admins can mandate specific 2FA methods for groups of users using Class of Service (COS) settings:
-
Navigate to COS settings in the Admin Console.
-
Update the 2FA Settings:
-
Enable specific 2FA methods (Email or Authenticator App).
-
Save the changes.
-
When Upgrading
-
If 2FA using an authenticator app was used before the upgrade,
zimbraTwoFactorAuthMethodAllowedmust have "app" after the upgrade. An empty value is regarded as "app". -
If 2FA using an authenticator app was used before the upgrade and the administrator wants to allow users to use both app and email methods,
zimbraTwoFactorAuthMethodAllowedmust have both "app" and "email". -
If 2FA using an authenticator app was used before the upgrade and the administrator wants to allow users to use the email method only:
-
2FA needs to be disabled on all accounts.
-
Then
zimbraTwoFactorAuthMethodAllowedmust be set to "email".
-
2FA for Delegated Administrator
Delegated Administrators can control the 2FA feature for the users. Bydefault the option is not enabled for them and needs to be setup. You can setup View and Edit permissions for DA.
Edit Permissions
-
Provide edit rights to the DA. As a
zimbrauser, execute the following commands:zmprov grr global usr <da@example.com> domainAdminZimletRights zmprov grr domain <domain_name> usr <da@example.com> set.account.zimbraTwoFactorAuthEnabled zmprov grr domain <domain_name> usr <da@example.com> set.account.zimbraFeatureTwoFactorAuthRequired zmprov grr domain <domain_name> usr <da@example.com> set.account.zimbraFeatureTwoFactorAuthAvailable -
As a DA, login to the Admin Console.
-
Go to Manage → Accounts → <account_name> → Advanced.
-
Two Factor Authentication option should be available and the DA can edit the settings.
View Permissions
-
Provide view rights to the DA. As a
zimbrauser, execute the following command:zmprov grr global usr <da@example.com> domainAdminZimletRights -
As a DA, login to the Admin Console.
-
Go to Manage → Accounts → <account_name> → Advanced.
-
Two Factor Authentication option should be available in View mode.
-
DA will not be able to edit any 2FA settings.
Other Configuration Settings for Accounts
Enable Sharing
When the Sharing feature is enabled, users can share any of their folders, including their mail folders, calendars, address books, task lists, and Briefcase folders.
A users specifies the type of access permissions to give the grantee. They can share with internal users who can be given complete manager access, external guests who must use a password to view the folder content, as well as public access so that anyone who has the URL can view the folder’s content.
When internal users share a mail folder, a copy of the shared folder is put in the grantee’s folder list on the Overview pane. Users can manage their shared folders from their Classic Web App Preferences Sharing page.
At this time, the Modern Web App supports share management from folder and calendar context menus only.
Configure SMS Notification
The Classic Web App Preferences → Notification page lets users configure an email address or SMS alert to their mobile device to receive a reminder message for a task or a meeting on their calendar. Notification by SMS is disabled by default.
SMS notification can be configured by domain, COS or for individual accounts. SMS notification set in a COS overrides SMS notifications set on a domain. In the Administration Console, this is set on the domain, COS or account’s Feature page.
Users select a region and a carrier when setting up their SMS alert. The list of SMS/email gateways is in ZmSMS.properties. You can customize this list to add SMS/email gateways that are not listed.
| This feature is supported only in the Classic Web App. |
Configure Attachment Viewing
You can set attachment viewing rules as a global setting, by COS, or for a specific account. The global setting takes precedence over COS and account Settings. You can select from four options.
| The Modern Web App always provides Hi-Def Attachment Previews, with no user settings required. |
| Feature Name | Description | COS/Account Tabs | ||
|---|---|---|---|---|
Disable attachment viewing from web mail UI |
Attachments cannot be viewed. This can also be set as a global setting. |
Advanced |
||
Attachments can be viewed in HTML only |
Attachments received in another format are opened in HTML view. |
Advanced |
||
Attachments can be viewed in their original format only |
|
Advanced |
||
Attachments can be viewed in HTML and their original format |
Users can select to open either in the original format or as HTML. |
Advanced |
Display a Warning When Users Try to Navigate Away
Users can click the Back and Forward arrows in the browser, or close their browser without logging out of their account.
-
If this preference is checked, users are asked to confirm that they want to navigate away from their account.
-
If this preference is not checked, the question is not asked.
| This setting is not provided in the Modern Web App. |
Enabling the Check Box for the Web Client
If Show selection checkbox for selecting email, contact, voicemail items in a list view for batch operations is enabled, when users view email messages,contacts, and tasks lists in the Content pane, a check box displays for each item. Users can select items and then perform an action such as mark as read/unread, move to a specific folder, drag and drop to a folder, delete, and tag for all those selected items.
| Checkboxes are enabled by default on the Modern Web App. |
Preferences Import/Export
From the Preferences Import/Export page in the Classic Web App or under Accounts → Primary account in the Modern Web App users may export all of their account data, including mail, contacts, calendar, and tasks. By selecting export options, they can export specific items in their account and save the data to their computer.
The account data is saved as a tar-gzipped (.tgz) archive file so that it can be imported to restore their account.
Individual contacts are saved as .csv files, and individual calendar files are saved as .ics files.
The data are copied, not removed from the user’s account.
The exported account data file can be viewed with an archive program such as WinZip. Any of these files can be imported into their account from the same page.
You can turn the Import/Export feature off from the COS or Account Features page, General Features section.
Adding Words to Spell Dictionary
If Classic Web App users frequently use words, abbreviations or acronyms that are marked as spelling errors during a Classic Web App spell check, you can update the COS or domain attribute zimbraPrefSpellIgnoreWord with the words that should be ignored when spell check is run.
To configure words to ignore for a domain:
zmprov md example.com +zimbraPrefSpellIgnoreWord <word> +zimbraPrefSpellIgnoreWord <word2>| This feature is supported only in the Classic Web App. |
Hierarchical Address Book (HAB) in Zimbra
What is a HAB?
The hierarchical address book (HAB) allows users to look for recipients in their address book using organizational hierarchy. Typically, users only see the default global address list (GAL) whose structure doesn’t help understand who reports to whom or to identify one John Doe from another. Being able to customize a HAB, which maps to your organization’s unique business structure, provides your users with an efficient method for locating internal recipients.
Using Hierarchical Address Book
In a Hierarchical Address Book (HAB), your root organization (e.g., Zimbra) is the top-level tier. Under this top-level tier, you can add several child tiers to create a customized HAB that is segmented by division, department, or any other organizational level you want to specify. The following figure illustrates a HAB for Zimbra with the following structure:
-
The top-level tier represents the root organization — Zimbra.
-
The second-level child tiers represent the business divisions within Zimbra — Corporate Office, Engineering, Product Support, and Sales & Marketing.
-
The third-level child tiers represent departments within the Corporate Office division — Human Resources, Accounts, and Administration.
Seniority Index
Seniority Index provides an additional level in the hierarchy. When creating a HAB, use this parameter to rank individuals or organizational groups by seniority within these organizational tiers. This ranking specifies the order in which HAB displays recipients or groups. A higher seniority index ensures that a user or group appears above another with a lower seniority index.
-
100for Vice President -
50for Administration Operations Manager -
25for Business Administrator
| If the Seniority Index parameter isn’t set or is equal for two or more users, the HAB sorting order lists the users and groups in ascending alphabetical order. |
Configuring hierarchical address books
Create an organizational unit (OU)
Format
zmprov createHABOrgUnit <domain name of OU> <OU Name>
Example
zmprov createHABOrgUnit example.com ZimbraOU
Explanation
ZimbraOU as an organizational unit created.
Create groups within this OU
You have to create a group and assign an email address for each department.
Format
zmprov createHABGroup <name of the group> <name of OU> <group email address>
Example
In this series of commands, we create 8 HAB groups — as per the Example Hierarchy.
zmprov createHABGroup Zimbra ZimbraOU zimbra@example.com
zmprov createHABGroup CorporateOffice ZimbraOU CorpOffice@example.com
zmprov createHABGroup Engineering ZimbraOU eng@example.com
zmprov createHABGroup ProdSupport ZimbraOU prodsupport@example.com
zmprov createHABGroup SalesAndMarketing ZimbraOU sales-mark@example.com
zmprov createHABGroup HumanResources ZimbraOU hr@example.com
zmprov createHABGroup Accounts ZimbraOU accounts@example.com
zmprov createHABGroup Administration ZimbraOU administration@example.com
Create Hierarchy
Each of these groups (except Zimbra) needs to be assigned a parent group to create a hierarchy.
Format
zmprov addHABGroupMember ParentGroupEmailAddress ChildGroupEmailAddress
In this series of commands, we designate 7 HAB groups — except Zimbra because it is root — as per the hierarchy in the figure Example Hierarchy.
For this, we add Human Resources, Accounts, and Administration to Corporate Office; and add Corporate Office, Engineering, Product Support, and Sales & Marketing to Zimbra.
zmprov addHABGroupMember CorpOffice@example.com hr@example.com
zmprov addHABGroupMember CorpOffice@example.com accounts@example.com
zmprov addHABGroupMember CorpOffice@example.com administration@example.com
zmprov addHABGroupMember zimbra@example.com CorpOffice@example.com
zmprov addHABGroupMember zimbra@example.com eng@example.com
zmprov addHABGroupMember zimbra@example.com prodsupport@example.com
zmprov addHABGroupMember zimbra@example.com sales-mark@example.com
Get Zimbra ID
zimbraId is a unique identifier associated with an email address. It is used to assign users to groups and to specify a group as root.
For this example, and everywhere else we have used a placeholder (xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx) for zimbraId.
|
Format
zmprov gdl <group email address> zimbraId
Example
zmprov gdl zimbra@example.com zimbraId
Example Output
# distributionList zimbra@example.com memberCount=4 zimbraId: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
Explanation
zimbra@example.com is the email address of the group which is to become root.
Add users to Groups
This example adds the users Jane Doe and John Smith to the group named CorporateOffice without affecting other existing members.
Format
zmprov addHABGroupMember <group email address> <user's email address>
Example
zmprov addHABGroupMember hr@example.com jane.doe@example.com
zmprov addHABGroupMember accounts@example.com john.smith@example.com
Set Sort Order
Configure the sort order for groups in the HAB. Groups with higher seniority index appear above groups with lower seniority index.
Format
zmprov modifyHABGroupSeniority <zimbra ID> <seniority index>
Example
To have Engineering appear above CorporateOffice — irrespective of their names and alphabetical order, get Zimbra ID, decide on a number in place of SeniorityIndexNumber, and run the below command.
Assign CorporateOffice a seniority index of 90
zmprov modifyHABGroupSeniority xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx 90
Assign Engineering a seniority index of 100
zmprov modifyHABGroupSeniority xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx 100
| Commands used to set seniority index for groups also set Seniority Index for users. |
Specify the root organization for the HAB
A group needs to be specified as root so that other groups can be added as child groups to comply with the organizational hierarchy. Run below command to make zimbra@example.com as root.
Format
zmprov md <domain name> zimbraHierarchicalAddressBookRoot <ZimbraID of the group to be made root>
Example
zmprov md 'example.com' zimbraHierarchicalAddressBookRoot xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
Example Output
# distributionList zimbra@example.com memberCount=4 zimbraId: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
Did it work?
-
Log in to Zimbra client.
-
Click New Message.
-
In the Compose window, click the To field.
-
On Select Addresses window, locate the Show Names from: drop-down on the top right corner.
-
Choose Organizational Address Book.
-
The address book in a hierarchical format appears in the left pane.
-
Click any group to view and select users of that group.
Manage Organisational Units (OUs)
List Organisational Units (OUs)
There can be multiple organizational units in a domain. This command lists all the OUs in a specified domain.
Format
zmprov listHABOrgUnit <domain name of OU>
Example
zmprov listHABOrgUnit example.com ZimbraOU
Explanation
All OUs in example.com listed.
Rename Organisational Units (OUs)
This command renames the specified OU in a domain.
Format
zmprov renameHABOrgUnit <domain name of OU> <OU Name> <New name for OU>
Example
zmprov renameHABOrgUnit example.com ZimbraOU ZMXOU
Explanation
ZimbraOU renamed to ZMXOU.
Rename Organisational Units (OUs)
This command deletes the specified OU in a domain.
Format
zmprov renameHABOrgUnit <domain name of OU> <OU Name>
Example
zmprov renameHABOrgUnit example.com ZimbraOU
Explanation
ZimbraOU deleted.
Provisioning User Accounts
When an account is provisioned, you create the mailbox, assign the primary account email address, and assign a class of service (COS) to enable Zimbra Collaboration applications and features.
You can configure one account at a time or migrate multiple existing accounts from a server.
Creating a Single User Accounts
Before adding a user account, determine which features and access privileges should be assigned. You can either assign a class of service (COS) with the features enabled when you create the account or you can configure the features for the individual accounts. For a description of the features, see Class of Service and Accounts.
If the COS you assign has the correct functionality for the account, you do not need to perform any additional configuration.
Creating an account sets up the appropriate entries on the Zimbra LDAP directory server. When the user logs in for the first time or when an email is delivered to the user’s account, the mailbox is created on the mailbox server.
Basic user account setup:
- Admin Console:
-
Home → 3 Add Accounts → 1. Add Account
-
In the Account Name section, enter the account name and the last name as a minimum to configure the account.
The default COS is assigned to the account.
-
Click Finish to create the account.
-
You can continue to configure features and functionality for the individual account. Changes you make to the account override the COS that is assigned to the account.
Migrating Accounts and Importing Account Email
| Zimbra Collaboration Account Migration within the Zimbra Admin UI is no longer supported, with End of Technical Guidance set for 17 December 2019. We recommend Audriga’s self-service migration solution as a preferred alternative for all account migrations. |
You can provision multiple accounts at one time using the Account Migration Wizard from the Administration Console. You can import accounts from either a generic IMAP server or from another Zimbra server.
| Only accounts on Zimbra Collaboration 7.2 or later can be migrated to Zimbra Collaboration 8. |
You can also import account names to provision from an XML file that you create.
You can run the migration wizard one time to provision accounts and import data or you can run the migration wizard the first time to provision the accounts and then run the wizard again to import the provisioned accounts' data.
Whether you get the account records from an LDAP directory or use an XML file, you need to set the password requirements for the newly provisioned accounts. The options are to have Zimbra randomly create passwords for each account or to set the same password on each account. You have the option to force users to change the password when they sign in the first time.
When the provisioning is complete, the wizard generates a .csv file with a
list of new accounts. This includes the passwords that are generated. You
should download this file for future reference. Choose a secure location
to store the file as it can contain password information for the user
accounts you provisioned.
If you’re running a split-domain configuration, you can set the SMTP host and port in the wizard. For more information about split domains, see the wiki article about split domains at https://wiki.zimbra.com/wiki/Split_Domain.
Migrating Accounts from a Zimbra Server
To migrate accounts from a server running Zimbra Collaboration 7.2 or later to Zimbra Collaboration 8.
- Admin Console:
-
Home → 3 Add Accounts → 3. Migration and Co-existence
-
In the Type of mail server field, select Zimbra Collaboration.
-
If you are provisioning accounts, select Yes to import the account’s records. If you are not going to import the data at this time, in the Would you like to import mail, select No.
-
Click Next.
-
On the Overview dialog, Import from another Zimbra LDAP directory is selected. Click Next.
-
On the Bulk provisioning options page, select whether to generate random passwords or to assign the same password for each account.
Table 42. Bulk Provisioning Features Bulk Provisioning Feature Description Generate random password
If you select Generate a random password for each account, set the length for the password. The password can be from 6 to 64 characters.
Default = 8 characters
If you select to generate a random password, you must download the
.csvfile that is created so that you can give the password information to each user.Use same password
If you select Use same password for all new accounts, enter the password to use.
Require users to change password after first login
It is recommended that this is checked to force users to change their passwords when they log on the first time.
SMTP Host / SMTP Port
For split domain configurations, set the SMTP Host name and port.
-
Click Next.
-
On the Directory connection dialog enter the information to connect to the server.
Table 43. Directory Connection Options Directory Connection Options Description Automatically create missing domains
Enable this option to create a domain when an account is imported and the domain they were on is not created.
If you do not enable this, accounts from domains that do not exist on the server are not created. Disabling this option makes it easy to import accounts from specific domains that have been pre-created.
Maximum records to fetch
Enter the maximum number of accounts to import at one time. The default is 0, which means that no limits are set.
Server name, LDAP URL, Port, and Use of SSL
-
The LDAP URL is entered as:
ldap://<ldapdirectory.example.com> -
The default port is 389, but you can change this.
-
Check SSL if this is used.
Bind DN
The Zimbra setting is in the field by default as
uid=zimbra,cn=admins,cn=zimbraBind password
Enter the password for the server.
LDAP filter
In this field enter the LDAP search filter to run. Here you can define search criteria to collect the type of account information you want to import. The default filter in the field is (objectclass=zimbraAccount). This filter includes the email address, the account ID, and attributes for the account.
LDAP search base
Configure the subsections of the LDAP forest to search.
-
-
Click Next.
The Account Migration Wizard connects to the directory server and generates a report showing the number of domains found; number of accounts found on the server and how many of those accounts are already created on Zimbra. This dialog also shows the password options you configured.
-
Review the report generated and then click Next. The accounts are provisioned on the Zimbra Collaboration server.
-
Download the
.csvfile that lists the provisioned accounts and their passwords. The.csvfile is deleted when you close the wizard. If you do not download the file, you cannot access the report later.
Migrating Accounts from Generic IMAP Servers
Use steps in this section to provision accounts on the Zimbra server.
- Admin Console:
-
Home → 3 Add Accounts → 3. Migration and Co-existence
-
In the Type of mail server field, select Generic IMAP Server.
-
If you are provisioning accounts, select Yes to import the account’s records. If you are not going to import the data at this time, in the Would you like to import mail, select No.
-
Click Next.
-
On the Overview dialog, Import from another LDAP directory is selected. Click Next.
-
On the Bulk provisioning options page, select whether to generate random passwords or to assign the same password for each account.
Table 44. Bulk Provisioning Features Bulk Provisioning Feature Description Generate random password
If you select Generate a random password for each account, set the length for the password. The password can be from 6 to 64 characters.
Default = 8 characters
If you select to generate a random password, you must download the
.csvfile that is created so that you can give the password information to each user.Use same password
If you select Use same password for all new accounts, enter the password to use.
Require users to change password after first login
It is recommended that this is checked to force users to change their passwords when they log on the first time.
SMTP Host / SMTP Port
For split domain configurations, set the SMTPHost name and port.
-
Click Next.
-
On the Directory connection dialog enter the information to connect to the server.
Table 45. Directory Connection Options Directory Connection Options Description Automatically create missing domains
Enable this option to create a domain when an account is imported and the domain they were on is not created.
If you do not enable this, accounts from domains that do not exist on the server are not created. Disabling this option makes it easy to import accounts from specific domains that have been pre-created.
Maximum records to fetch
Enter the maximum number of accounts to import at one time. The default is 0, which means that no limits are set.
Server name, LDAP URL, Port, and Use of SSL
-
The LDAP URL is entered as:
ldap://<ldapdirectory.example.com> -
The default port is 389, but you can change this.
-
Check SSL if this is used.
Bind DN
The Zimbra setting is in the field by default as
uid=zimbra,cn=admins,cn=zimbraBind password
Enter the password for the server.
LDAP filter
In this field enter the LDAP search filter to run. Here you can define search criteria to collect the type of account information you want to import. The default filter in the field is (objectclass=zimbraAccount). This filter includes the email address, the account ID, and attributes for the account.
LDAP search base
Configure the subsections of the LDAP forest to search.
-
-
Click Next.
The Migration Wizard connects to the directory server and generates a report showing the number of domains found; number of accounts found on the server and how many of those accounts are already created on Zimbra. This dialog also shows the password options you configured.
-
Review the report generated and then click Next. The accounts are provisioned on the Zimbra Collaboration server.
-
Download the
.csvfile that lists the provisioned accounts and their passwords. The.csvfile is deleted when you close the wizard. If you do not download the file, you cannot access the report later.
Migrating Accounts using an XML File
Use steps in this section to create an XML file with the account information and save it to a computer you can access.
- Admin Console:
-
Home → 3 Add Accounts → 3. Migration and Co-existence
-
In the Type of mail server field, select the type of server your are migrating from.
-
If you are provisioning accounts, select Yes to import the account’s records. If you are not going to import the data at this time, in the Would you like to import mail, select No.
-
Click Next.
-
On the Overview dialog, select Import from an XML file.
-
Click Next.
-
The Review options dialog displays the number of domains; number of accounts and the password options configured in the XML file.
-
If this information is correct, click Next. If this information is not correct, fix your XML file before proceeding.
If you clicked Next, the accounts are provisioned on the Zimbra Collaboration server.
-
Download the
.csvfile that lists the provisioned accounts and their passwords. The.csvfile is deleted when you close the wizard. If you do not download the file, you cannot access the report later.
Importing Email for Selected Accounts
Use steps in this section to specify the list of accounts whose mail you want to import by either selecting the accounts to import data or by using an XML file to select the accounts.
| Ensure that accounts are provisioned on the Zimbra server before attempting this procedure. |
- Admin Console:
-
Home → 3 Add Accounts → 3. Migration and Co-existence
-
In the Type of mail server field, select the type of server your are importing the data from.
-
In the Would you like to import account records menu, select No.
-
In the Would you like to import mail menu, select Yes.
-
Click Next.
-
On the Import options dialog box, select which way you are going to specify the accounts whose mail is being imported.
-
Click Next.
If you are selecting accounts, go to step 7. If you are using an XML file go to step 9.
-
If you are selecting the accounts to import, on the Selected Accounts dialog box, search for the accounts to add. You can search by domain or user name. If you click Search without entering text, all accounts are returned.
Add the accounts to the Accounts for data import column.
-
Click Next.
-
If you are using an XML file with the accounts listed, browse to the XML file to use.
-
Click Next.
-
In the IMAP Connection details dialog box, enter the information necessary to connect to the exporting server’s IMAP, this includes the IMAP host name, port and administrator login information.
-
Click Next.
-
Review the data import options. If the information is correct, click Next.
XML File Examples
This section contains three examples of the XML file structure to provision accounts and import data.
The following example shows an XML file that is used to provision multiple email accounts without importing mail:
<?xml version="1.0" encoding="UTF-8"?>
<ZCSImport>
<ImportUsers>
<User>
<sn>Sample</sn>
<givenName>Sam</givenName>
<displayName>Sam Sample</displayName>
<RemoteEmailAddress>ssample@example.com</RemoteEmailAddress>
<password>test123</password>
<zimbraPasswordMustChange>TRUE</zimbraPasswordMustChange>
</User>
<User>
<sn>Zackry</sn>
<givenName>Zak</givenName>
<displayName>Zak Zackry</displayName>
<RemoteEmailAddress>zzackry@example.com</RemoteEmailAddress>
<password>test123</password>
<zimbraPasswordMustChange>TRUE</zimbraPasswordMustChange>
</User>
</ImportUsers>
</ZCSImport>The following example shows an XML file that is used to provision multiple email accounts for externally hosted domain without importing mail.
In this example, the zimbraMailTransport attribute of newly provisioned
accounts will be set to point to external SMTP server instead of the Zimbra
server.
<?xml version="1.0" encoding="UTF-8"?>
<ZCSImport>
<SMTPHost>smtp.example.com</SMTPHost>
<SMTPPort>25</SMTPPort>
<ImportUsers>
<User>
<sn>Sample</sn>
<givenName>Sam</givenName>
<displayName>Sam Sample</displayName>
<RemoteEmailAddress>sam@example.com</RemoteEmailAddress>
</User>
<User>
<sn>Zackry</sn>
<givenName>Zak</givenName>
<displayName>Zak Zackry</displayName>
<RemoteEmailAddress>zzackry@example.com</RemoteEmailAddress>
</User>
</ImportUsers>
</ZCSImport>The following example shows an XML file that is used to import email for one account via IMAP from a gmail account without provisioning the email account in Zimbra. The account must be provisioned on Zimbra before running this type of XML file.
<?xml version="1.0" encoding="UTF-8"?>
<ZCSImport>
<IMAPHost>imap.gmail.com</IMAPHost>
<IMAPPort>993</IMAPPort>
<ConnectionType>ssl</ConnectionType>
<UseAdminLogin>0</UseAdminLogin>
<ImportUsers>
<User>
<sn>Sample</sn>
<givenName>Sam</givenName>
<displayName>Sam Sample</displayName>
<RemoteEmailAddress>sam@example.com</RemoteEmailAddress>
<RemoteIMAPLogin>sam@example.com</RemoteIMAPLogin>
<remoteIMAPPassword>test123</remoteIMAPPassword>
</User>
</ImportUsers>
</ZCSImport>Auto Provisioning New Accounts from External LDAP
Auto provisioning of new accounts from external LDAP is supported via the CLI. This section describes the supported CLI attributes and auto provisioning methods.
Overview
When an external LDAP authentication mechanism - such as external LDAP authentication, preauth, or SPNEGO - is configured for a Zimbra domain, you can set up Zimbra to automatically create user accounts on Zimbra. Primary email address and account attributes are mapped from an external directory. You can configure how and when new accounts should be created from the external directory data.
Three modes are supported for auto-provisioning configuration.
| Mode | Description |
|---|---|
Eager |
Zimbra polls the external directory for accounts to auto provision. For this mode, you configure how often the external directory is polled for new users, the maximum number of users to process at each interval, and which domains are scheduled for account auto provision on specified servers. Guidelines are provided in Eager Mode Configuration. |
Lazy |
If a user logs into the Classic Web App the first time through one of the authentication mechanisms supported for auto provisioning, and if the user does not exist in the Zimbra directory, a new account is automatically created in Zimbra for this user. Guidelines are provided in Lazy Mode Configuration. |
Manual |
Auto provisioning does not occurs: instead, the administrator manually searches from the configured external auto-provisioning LDAP source and selects an entry from the search result to create the corresponding Zimbra account for the external entry. Guidelines are provided in Manual Mode Configuration. |
When an account is created, the account name (consisting of the characters
alongside the @ symbol) is mapped from a user attribute on the external
directory that you define in zimbraAutoProvAccountNameMap. Other account
information, such as first and last name, phone numbers, and address, is
populated from the attributes mapped from the external directory based on
zimbraAutoProvAttrMap. You can review the external directory’s
attributes to determine those that should be mapped to a Zimbra attribute.
The COS assignment for auto-provisioned accounts is identical to the way that COS is determined for manually provisioned accounts:
-
If a COS is defined for the domain, this COS is assigned to the accounts that are created.
-
If a domain COS is not defined, the Zimbra default COS is assigned.
You can configure a Welcome email message to be sent to newly created
accounts. The subject and body of this email can be configured with
AutoProvNotification attributes on the domain.
Auto-Provisioning Attributes
The attributes listed in this section can be used with the zmprov command
to configure auto provisioning of new accounts with an external LDAP
directory.
zimbraAutoProvMode-
Set auto provision mode as either EAGER, LAZY, and/or MANUAL. Multiple auto-provisioning modes can be enabled on a domain.
zimbraAutoProvAuthMech-
Set type of authentication mechanism - as either LDAP, PREAUTH, KRB5, or SPNEGO - to enable for LAZY mode. Once a user authenticates via the specified authentication mechanism, and if the user account does not yet exist in the Zimbra directory, an account will be automatically created in the Zimbra directory.
zimbraAutoProvLdapURL-
Set the LDAP URL of the external LDAP source for auto provisioning
zimbraAutoProvLdapStartTlsEnabled-
Enable (TRUE) or disable (FALSE) the StartTLS protocol when accessing the external LDAP server for auto provisioning.
Default = FALSE. zimbraAutoProvLdapAdminBindDn-
Defines the LDAP search bind DN for auto provisioning.
zimbraAutoProvLdapAdminBindPassword-
Set the LDAP search admin bind password for auto provisioning.
zimbraAutoProvLdapSearchBase-
Set the LDAP search base for auto provisioning, used in conjunction with zimbra
zimbraAutoProvLdapSearchFilter.
If not set, LDAP root DSE will be used. zimbraAutoProvLdapSearchFilter-
Defines the LDAP search filter template for account auto provisioning. For LAZY mode, either
zimbraAutoProvLdapSearchFilterorzimbraAutoProvLdapBindDnmust be set.If both are set,
zimbraAutoProvLdapSearchFilterwill take precedence. See Placeholders for supported placeholders. zimbraAutoProvLdapBindDn-
Defines the LDAP external DN template for account auto provisioning. For LAZY mode, either
zimbraAutoProvLdapSearchFilterorzimbraAutoProvLdapBindDnmust be set.If both are set,
zimbraAutoProvLdapSearchFilterwill take precedence. See Placeholders for supported placeholders. zimbraAutoProvAccountNameMap-
Defines the attribute name in the external directory that contains local part of the account name. This is the name used to create the Zimbra account. If this is not specified, the local part of the account name is the principal user used to authenticated to Zimbra.
zimbraAutoProvAttrMap-
Defines the attribute map for mapping attribute values from the external entry to Zimbra account attributes. Values are in the format of
{external attribute}={zimbra attribute}. If this is not set, no attributes from the external directory are populated in Zimbra account.Invalid mapping configuration will cause the account creation to fail. Bad mapping may be due to conditions such as:
-
Invalid external attribute name.
-
Invalid Zimbra attribute name.
-
External attribute contains multiple values; the Zimbra attribute contains only a single value.
-
Syntax violation (such as external attribute=string, but Zimbra attribute=integer).
-
zimbraAutoProvNotificationFromAddress-
Defines the email address to put in the From header for the Welcome email sent to the newly created account. If not set, no notification email is sent to the newly created account.
zimbraAutoProvNotificationSubject-
Template used to construct the subject of the notification message sent to the user when the user’s account is auto provisioned.
Supported variables:
${ACCOUNT_ADDRESS},${ACCOUNT_DISPLAY_NAME} zimbraAutoProvNotificationBody-
Template used to construct the body of the notification message sent to the user when the user’s account is auto provisioned.
Supported variables:
${ACCOUNT_ADDRESS},${ACCOUNT_DISPLAY_NAME} zimbraAutoProvListenerClass-
Domain setting to define the class name of auto provision listener. The class must implement the
com.zimbra.cs.account.Account.AutoProvisionListenerinterface. The singleton listener instance is invoked after each account is auto created in Zimbra. Listener can be plugged in as a server extension to handle tasks like updating the account auto provision status in the external LDAP directory.At each eager provision interval, Zimbra does an LDAP search based on the value configured in
zimbraAutoProvLdapSearchFilter. Returned entries from this search are candidates to be auto provisioned in this batch. ThezimbraAutoProvLdapSearchFiltershould include an assertion that will only hit entries in the external directory that have not yet been provisioned in Zimbra, otherwise it’s likely the same entries will be repeated pulled in to Zimbra. After an account is auto provisioned in Zimbra,com.zimbra.cs.account.Account.AutoProvisionListener.postCreate (Domain domain, Account acct, String external DN)will be called by the auto provisioning framework. Customer can implement the AutoProvisionListener interface in a Zimbra server extension and get theirAutoProvisionListener.postCreate()get called. The implementation of customer’s post Create method can be, for example, setting an attribute in the external directory on the account just provisioned in Zimbra. The attribute can be included as a condition in thezimbraAutoProvLdapSearchFilter, so the entry won’t be returned again by the LDAP search in the next interval. zimbraAutoProvBatchSize-
Domain | Global setting to define the maximum number of accounts to process in each interval for EAGER auto provision.
zimbraAutoProvScheduledDomains-
Server attribute that lists the domains scheduled for EAGER auto provision on this server. Scheduled domains must have EAGER mode enabled in
zimbraAutoProvMode. Multiple domains can be scheduled on a server for EAGER auto provision. Also, a domain can be scheduled on multiple servers for EAGER auto provision. zimbraAutoProvPollingInterval-
Domain | Global setting to define the interval between successive polling and provisioning accounts in EAGER mode. The actual interval might take longer since it can be affected by two other factors:
zimbraAutoProvBatchSizeand number of domains configured inzimbraAutoProvScheduledDomains.At each interval, the auto provision thread iterates through all domains in
zimbraAutoProvScheduledDomainsand auto creates accounts up todomain.zimbraAutoProvBatchSize. If that process takes longer thanzimbraAutoProvPollingIntervalthan the next iteration starts immediately instead of waiting forzimbraAutoProvPollingIntervalamount of time.-
If set to 0 when server starts up, the auto provision thread will not start.
-
If changed from a non-0 value to 0 while server is running, the auto provision thread will be shutdown.
-
If changed from 0 to a non-0 value while server is running, the auto provision thread will be started.
-
Placeholders
| Tag | Description | Result |
|---|---|---|
%/n |
User name and the @ symbol |
This returns user1@example.com |
%u |
User name without the @ symbol |
This returns user1. |
%d |
Domain |
This returns example.com |
%D |
Domain as dc |
This returns example,dc=com |
Eager Mode Configuration
With Eager mode, Zimbra polls the external directory for accounts to auto provision. You configure how often the external directory is polled for new users, the maximum number of users to process at each interval, and the domains to be scheduled for account auto-provisioning on specified servers.
-
Log in to the Zimbra server as zimbra and type
zmprovat the command prompt.zmprov -
Enable EAGER mode on the domain.
md <example.com> zimbraAutoProvMode EAGER -
Set the maximum number of accounts to process in each interval
md <example.com> zimbraAutoProvBatchSize <#> -
Configure the interval (in minutes) between polling and provisioning of accounts. This must be set to a non-0 value for the auto provisioning thread to start. Default = 15 minutes.
ms <server.com> zimbraAutoProvPollingInterval <x minutes> -
Select the domains to be scheduled for auto provisioning. Multiple domains can be scheduled on the server.
A domain can be scheduled on multiple servers.
ms <server.com> +zimbraAutoProvScheduledDomains <domain1.com> \ +zimbraAutoProvScheduledDomains <domain2.com> -
Configure the external LDAP settings:
-
LDAP URL
md <example.com> zimbraAutoProvLdapURL "ldap://xxx.xxx.xxx.xxx:<port>"The LDAP port is typically 389.
-
(Optional) Enable StartTls.
md <example.com> zimbraAutoProvLdapStartTlsEnabled TRUE -
LDAP admin bind DN for auto provision:
md <example.com> zimbraAutoProvLdapAdminBindDn "cn=admin, dc=autoprov, dc=company, dc=com" -
Administrator’s LDAP search bind password for auto provision.
md <example.com> zimbraAutoProvLdapAdminBindPassword <password> -
Search template to use when searching for users to auto provision.
Example using the LDAP search filter:
md <example.com> zimbraAutoProvLdapSearchFilter "(uid=<%placeholder>)"Refer to Placeholders for supported placeholders.
-
LDAP search base for auto provisioning
This is the location in the directory from which the LDAP search begins. This is used with
zimbraAutoProvLdapSearchFilter. If this is not set, the LDAP directory root,rootDSE, is the starting point.md <example.com> zimbraAutoProvLdapSearchBase "dc=autoprov,dc=company,dc=com" md <example.com> zimbraAutoProvLdapBindDn <"placeholder1">Refer to Placeholders for supported placeholders.
-
-
(Optional) Define the attribute name that is mapped to the local part of the account name on the external directory. This is used to define the account name on Zimbra. If this is not specified, the local part of the account name is the principal user name used to authenticate to Zimbra.
md <example.com> zimbraAutoProvAccountNameMap <value> -
(Optional) Map the attribute values from the external entry to the Zimbra account attributes. If this is not set up, no attributes from the external directory are populated in the Zimbra directory. The value is mapped in the form of
{external attribute}={zimbra attribute}.Invalid mapping configuration will cause the account creating to fail. To map the "sn" value on the external entry to "displayName" on the Zimbra account and map description value on the external entry to description on the Zimbra account, type
md <example.com> +zimbraAutoProvAttrMap sn=displayName +zimbraAutoProvAttrMap description=description -
(Optional) If you want to send a Welcome email to new accounts, enter the from address of the originator.
md <example.com> zimbraAutoProvNotificationFromAddress <name@example.com> -
To exit zmprov, type
exit
Lazy Mode Configuration
Lazy mode auto provisioning automatically creates a new account after a user authenticates from an external authentication mechanisms (LDAP, preauth, Kerberos 5, and/or SPNEGO).
-
Log in to the Zimbra server as zimbra and type
zmprovat the command prompt. -
Enable LAZY mode,
md <example.com> zimbraAutoProvMode LAZY -
Select the external authentication mechanism for the LAZY mode: LDAP, PREAUTH, KRB5, SPNEGO. You can specify multiple authentication mechanisms.
md <example.com> zimbraAutoProvAuthMech <type> +zimbraAutoProvAuthMech <type2> -
Configure the external LDAP settings
-
LDAP URL:
md <example.com> zimbraAutoProvLdapURL "ldap://xxx.xxx.xxx.xxx:<port>"The LDAP port is usually 389.
-
(Optional) Enable StartTls
md <example.com> zimbraAutoProvLdapStartTlsEnabled TRUE -
LDAP Admin bind DN for auto provision in the format
cn=<LDAPadmin_name>, dc=autoprov, dc=<company_name>, dc=<com>md <example.com> zimbraAutoProvLdapAdminBindDn <"bindDN">For example,
"cn=admin, dc=autoprov, dc=company, dc=com" -
Administrator’s LDAP search bind password for auto provision.
md <example.com> zimbraAutoProvLdapAdminBindPassword <password> -
(Optional) Search template to use when searching for users to auto provision.
Example: using LDAP search filter:
md <example.com> zimbraAutoProvLdapSearchFilter <"placeholder">Refer to Placeholders for supported placeholders.
zimbraAutoProvLdapSearchFilter or zimbraAutoProvLdapBindDn MUST be configured for LAZY mode. -
LDAP search base for auto provision. This is the location in the directory from which the LDAP search begins. This is used with
zimbraAutoProvLdapSearchFilter. If this is not set, the LDAP directory root,rootDSE, is the starting point.md <example.com> zimbraAutoProvLdapSearchBase <"location">For example,
"dc=autoprov,dc=company,dc-com" -
(Optional) Define the LDAP external DN template for account provisioning.
md <example.com> zimbraAutoProvLdapBindDn "uid=%<placeholder1>, %<placeholder2>"Refer to Placeholders for supported placeholders.
-
-
(Optional) Identify the attribute name on the external entry that contains the local part of the account name to be provisioned in Zimbra. If this is not specified, the local part of the account name is the principal user used to authenticate to Zimbra.
md <example.com> zimbraAutoProvAccountNameMap <value> -
(Optional) Map the attribute values from the external entry to the Zimbra account attributes. If this is not set up, no attributes from the external directory are populated in the Zimbra directory. Value is in the form of
{external attribute}={zimbra attribute}.To map the sn value on the external entry to displayName on the Zimbra account and map description value on the external entry to description on the Zimbra account, type as
md <example.com> +zimbraAutoProvAttrMap sn=displayName +zimbraAutoProvAttrMap description=description -
(Optional) If you want to send a Welcome email to new accounts, enter the from address of the originator.
md <example.com> zimbraAutoProvNotificationFromAddress <name@example.com> -
Exit zmprov, type
exit.
Manual Mode Configuration
Use the Manual Mode setting to disable auto provisioning with an external LDAP server.
-
Log in to the Zimbra server as zimbra and type
zmprovat the command prompt. -
Enable MANUAL mode:
md <example.com> zimbraAutoProvMode MANUAL
Managing Resources
A resource is a location or equipment that can be scheduled for a meeting. Each meeting room location and other non-location specific resources such as AV equipment is set up as a resource account. The Manage → Resources section in the Administration Console shows all resources that are configured for Zimbra Collaboration.
User accounts with the Calendar feature can select these resources for their meetings. The resource accounts automatically accept or reject invitations based on availability.
Administrators do not need to monitor these mailboxes on a regular basis. The contents of the resource mailboxes are purged according to the mail purge policies.
A Resource Wizard guides you through the resource configuration. You can configure the account with the following details about the resource:
-
Type of resource, either location or equipment
-
Scheduling policy
-
Forwarding address to receive a copy of the invite
-
Description of the resource
-
Contact information, which can be a person to contact if there are issues
-
Location information, including room name, specific building location including building and address, and room capacity
-
Customize auto response message and signatures to be used in the reply email messages
When you create a resource account, a directory account is created in the LDAP server.
To schedule a resource, users invite the equipment resource and/or location to a meeting. When they select the resource, they can view the description of the resource, contact information and free/busy status for the resource, if these are set up.
When the meeting invite is sent, an email is sent to the resource account, and, based on the scheduling policy, if the resource is free the meeting is automatically entered in the resource’s calendar and the resource is shown as Busy.
Set Up the Scheduling Policy
The scheduling policy establishes how the resource’s calendar is maintained. The following resource scheduling values can be set up:
-
Auto decline all recurring appointments — This value is enabled when the resource can be scheduled for only one meeting at a time. No recurring appointments can be scheduled for this resource.
-
Auto accept if available, auto-decline on conflict — When this option is selected, the resource account automatically accepts appointments unless the resource is already scheduled. The free/busy times can be viewed. You can modify the auto-decline rule to accept some meetings that conflict.
-
Manual accept, auto decline on conflict — When this option is selected, the resource account automatically declines all appointments that conflict. Appointment requests that do not conflict are marked as tentative in the resource calendar and must be manually accepted. If you set this up, configure the forwarding address so a copy of the invite is sent to the account that can manually accept the invitation. You can modify the auto-decline rule to accept some meetings that conflict.
-
Auto accept always — The resource account automatically accepts all appointments that are scheduled. In this case, free/busy information is not maintained, thus more than one meeting could schedule the resource at the same time. Because the resource always accepts the invitation, the suggested use for this policy would be for a frequently used location off premises that you want the location address to be included in the invite to attendees.
-
No auto accept or decline — The resource account is manually managed. A delegated user must log into the resource account and accept or decline all requests.
Conflict Rules — For accounts that include the auto decline on conflict value, you can set up a threshold, either as a number of conflicts or as a percentage of all the recurring appointments to partially accept recurring appointments.
Maximum allowed number of conflicts and/or Maximum allowed percent of conflicts are configured to allow a recurring resource to be scheduled even if it is not available for all the requested recurring appointment dates.
The resource accepts appointments even if there are conflicts until either the number of conflicts reaches the maximum allowed or the maximum percentage of conflicts allowed. In order for partial acceptance of a series to work, both fields must be set to nonzero values.
Manage Resource Accounts
You can log on to the resource account and set preferences for the resource. The Resource Accounts Preference → Calendar can be configured to let users manage the Resource’s Calendar. You can configure the following options to manage the resource.
-
An address to forward invites. If the forwarding address was set up when the account was provisioned, you can change the address
-
Who can use this resource. In the Permissions section, Invites, select Allow only the following internal users to invite me to meetings and add the appropriate users' email addresses to the list.
You can share the resource calendar with a user and give the user Manager rights. Users delegated as Manager have full administrative rights for that calendar. They can view, edit, add, remove, accept or decline the invites.
Managing User Accounts
Status of User Accounts
- Admin Console:
-
Home → Manage → Accounts
The status of an account determines whether a user can log in and receive mail. The account status is displayed on the Accounts pane of the Administration Console.
| Status | Description |
|---|---|
Active |
The normal state for a mailbox account. Mail is delivered and users can log in to the client interface. |
Maintenance |
Logging is disabled and any mail addressed to this account is queued at the MTA. Note that this state is automatically set for the account during a backup or when importing/exporting/ restoring the account. |
Pending |
Assignment for an account when it is created but not yet ready to become active. While pending, the login is disabled and messages are bounced. |
Locked |
The user cannot log in but mail continues to be delivered to the account. The locked state can be set if you suspect that a mail account has been compromised (used in an unauthorized manner). |
Closed |
Login is disabled and messaged are bounced. This status is used to soft-delete the account before deleting it from the server. A closed account does not change the account license. |
LockOut |
The automatic state that occurs if the user attempts to log in with an incorrect password. A LockOut cannot be administratively assigned but will occur after the number of user attempts exceeds the configured number of attempts allowed. The duration of the lockout is also configurable. The administrator can remove the locked out status at any time. |
Deleting an Account
- Admin Console:
-
Home → Manage → Accounts
You can delete accounts from the Administration Console. This removes the account from the server, deletes the messages in the message store, and changes the number of accounts used against your license.
| Before you delete an account, run a full backup of that account to save the account information. See also Backup and Restore. |
Viewing an Accounts Mailbox
You can view a selected account’s mailbox content, including all folders, calendar entries, and tags from the Administration Console.
- Admin Console:
-
Home → Manage → Accounts → account
Select an account, from the Gear icon select View Mail. The user’s Zimbra account opens in a new browser window.
This feature can be used to assist users who are having trouble with their mail account as you and the account user can be logged on to the account at the same time.
Any View Mail action to access an account is logged to the audit.log
file.
Using an Email Alias
An email alias is an email address that redirects all mail to a specified mail account. An alias is not an email account. Each account can have unlimited numbers of aliases.
When you select Aliases from the Manage Aliases navigation pane, all aliases that are configured are displayed in the content pane. You can create an alias, view the account information for a specific alias, move the alias from one account to another, and delete the alias.
Hide Alias in GAL
10.1.1 release onwards, you can hide the aliases in GAL. Once hidden, they will not appear in autocomplete when composing mail or searching inbox.
The feature can be controlled on account level. By default, the feature is disabled.
The feature can be controlled through following ways:
-
Admin Console
-
Login to Admin Console.
-
Go to Home → Manage → Accounts → <account_name> → General Information → Account Name → Hide aliases in GAL
-
A checkbox to enable/disable the feature is available.
-
-
Command Line
A new LDAP attribute zimbraHideAliasesInGal is added to control the feature.
-
As a
zimbrauser, execute the following command to enable the feature for an account:zmprov ma <account_name> zimbraHideAliasesInGal TRUE -
As a
zimbrauser, execute the following command to force sync the changes and make the changes effective:zmgsautil forceSync -a <galsync@domain.com> -n InternalGAL
Working with Distribution Lists
A distribution list is a group of email addresses contained in a list with a common email address. When users send to a distribution list, they are sending the message to everyone whose address is included in the list. The address line displays the distribution list address; the individual recipient addresses cannot be viewed.
You can create distribution lists that require an administrator to manage the member list and you can create dynamic distribution lists that automatically manages adding and deleting members in the list. For more information about dynamic distribution lists, see Using Dynamic Distribution Lists.
You can see which distribution lists a user is a member of from the user’s account "Member of" page. When a Zimbra user’s email address is added to a distribution list, the user’s account Member Of page is updated with the distribution list name. When a distribution list is deleted, the distribution list name is automatically removed from the account’s "Member Of" page.
Setting Subscription Policies for Distribution Lists
Subscription policies can be set up to manage a distribution list’s membership. Owners of the list manage the subscription policy from the Properties page of a distribution list.
| Distribution Option | Description |
|---|---|
New Subscription Requests |
|
Unsubscription Requests |
|
Management Options for Owners of Distribution Lists
You can add owners to distribution lists and they manage the list from their Zimbra account’s Address Book, Distribution List folder. Owners of a list can right-click a distribution list and click the Edit Group link to edit a list.
Besides adding and deleting members, distribution list properties that owners can configure include:
-
Marking the list as private so it is hidden in the Global Address List
-
Managing who can send messages to the list
-
Setting a member subscription policy
-
Adding additional owners
Creating a Distribution List
Use steps in this section to create a distribution list:
- Admin Console:
-
Home → Manage → Distribution Lists
-
From the Gear icon, click New.
-
On the Members page, add the distribution list name. Do not use spaces. The other fields are optional.
-
Find members to add to the distribution list in the right column. Select the members to add and click Add Selected. If you want to add all addresses on the page, click Add This Page. If you want to add members that are not in the company list, in the Or enter addresses below section, type a complete mail address.
-
Click Next to configure the Properties page.
Table 48. Distribution Properties Options Distribution Properties Options Description Can receive mail
Enabled by default. If this distribution list should not receive mail select this box.
Hide user in GAL
Enable to create distribution lists that do not display in the Global Address List (GAL). You can use this feature to limit the exposure of the distribution list to only those that know the address.
Mail Server
This is set to auto by default. To select a specific mail server, uncheck auto and select a specific server from the list.
Dynamic Group
If you check this box, the Member URL field displays and you create a dynamic distribution list.
New Subscription Requests
Select from:
-
Automatically accept
-
Require list owner approval
-
Automatically reject
Unsubscription Requests
Select from:
-
Automatically accept
-
Require list owner approval
-
Automatically reject
-
-
In the Members Of page, select distribution lists that should be direct or indirect members of the list.
-
If the distribution list should have an alias, create it.
-
If this distribution list can be managed by other users, enter these email addresses in the Owners page.
-
Set how messages received to the distribution list should be replied to.
-
Click Finish. The distribution list is enabled and the URL is created.
-
Managing Access to Distribution Lists
After a distribution list is created, you can manage who can view members of a distribution list and who can send messages to a distribution list. The default is all users have access to all distribution lists. This section describes how to use the CLI to manage access.
To limit who can access distribution lists, grant rights to individual users on a domain or if you want only members of a domain to access distribution lists, you can grant rights on the domain. When you grant the right on the domain, all distribution lists on the domain inherit the grant.
You can grant the right on individual distribution lists and configure specific users that are allowed to access the distribution list.
You can restrict access to a distribution list from the CLI zmprov grantRight (grr) command.
| For more information about how granting rights works, see Delegated Administration. |
Who Can View Members of a Distribution List
The default is that all users can view members addresses in a distribution list. A distribution list address displays a + in the address bubble. Users can click on this to expand the distribution list. A list of the addresses in the distribution list is displayed. Users can select individual addresses from the expanded list.
Restricting who can view addresses in a distribution list to individuals or to a domain:
-
For individual users:
zmprov grr domain <domain_name> usr <user1@example.com> viewDistList -
For all users in a domain:
zmprov grr domain <domain_name> dom <example.com> viewDistList -
To grant rights on a distribution list and let specific users view the list:
zmprov grr dl <dll_name@example.com> usr <user1@example.com>
Who Can Send to a Distribution List
The default is that all users can send messages to all distribution lists. You can grant rights to a distribution list or to a domain that defines who can send messages to a distribution list. When users attempt to send to a distribution list that they are not authorized to use, a message is sent stating that they are not authorized to send messages to the recipient distribution list.
| The Milter Server must be enabled from Home → Configure → Global Settings → MTA. |
Restricting who can send messages to a distribution list to individuals or to a domain:
-
Granting rights to an individual user in a domain to send messages to all distribution lists.
zmprov grr domain <domain_name> usr <user1@example.com> sendToDistList -
Granting rights to all users in a domain to send messages to all distribution lists.
zmprov grr domain <domain_name> dom <example.com> sendToDistList
Restricting access and to remove the restriction to individual distribution lists for different user types.
-
Access to specific internal users:
zmprov grr dl <dlname@example.com> usr <username@example.com> sendToDistListRevoke access
zmprov rvr dl <dlname@example.com> usr <username@example.com> sendToDistList -
Access only to members of the distribution list:
zmprov grr dl <dlname@example.com> grp <dlname2@example.com> sendToDistListRevoke access
zmprov rvr dl <dlname@example.com> grp <dlname2@example.com> sendToDistList -
Access only to all users in a domain:
zmprov grr dl <dlname@example.com> dom <example.com> sendToDistListRevoke access
zmprov rvr dl <dlname@example.com> dom <example.com> sendToDistList -
Access only to all users in an external domain:
zmprov grr dl <dlname@example.com> edom <example.com> sendToDistListRevoke access
zmprov rvr dl <dlname@example.com> edom <example.com> sendToDistList -
Access only to internal users:
zmprov grr dl <dlname@example.com> all sendToDistListRevoke access
zmprov rvr dl <dlname@example.com> all sendToDistList -
Access only to all public email addresses:
zmprov grr dl <dlname@example.com> pub sendToDistListRevoke access
zmprov rvr dl <dlname@example.com> pub sendToDistList -
Access only to specific external email address:
zmprov grr dl <dlname@example.com> gst <someone@foo.com> "" sendToDistListRevoke access
zmprov rvr dl <dlname@example.com> gst <someone@foo.com> "" sendToDistList
Enabling View of Distribution List Members for AD Accounts
To view Active Directory distribution list members in messages or in the address book, the GAL group handler for Active Directory must be configured in the Zimbra GALsync account for each Active Directory.
Use steps in this section to update the GALsync account for each Active Directory. This configuration requires that you know the GALsync account name and all data sources on that GALsync account.
-
Display the Zimbra ID of the GAL sync account:
zmprov gd {domain} zimbraGalAccountIdTo find the name:
zmprov ga {zimbraId-of-the-GAL-sync-account} name -
Display data sources for the GALsync account:
zmprov gds {gal-sync-account-name-for-the-domain} -
Enable the group handler for the Active Directory:
zmprov mds {gal-sync-account-name-for-the-domain} {AD-data-source-name} \ zimbraGalLdapGroupHandlerClass com.zimbra.cs.gal.ADGalGroupHandler
Using Dynamic Distribution Lists
Dynamic distribution lists automatically manage their membership. Users are added and removed from the distribution list automatically. When you create a dynamic distribution list, a member URL is specified. This member URL is used to identify who should be members of the list. You can view this URL from the Administration Console distribution list’s Properties page.
You can create dynamic distribution lists from the Administration Console or from the CLI. In the URL, you specify specific object classes that identify the type of users to be added to the dynamic distribution list. For example, you can configure a dynamic distribution list with the object class= zimbraAccount. In this case, when accounts are provisioned or accounts are deleted, the dynamic distribution list is updated.
You can create dynamic distribution lists for all mobile users or POP/IMAP users.
You can modify a distribution list to change the filter rules. When you modify a distribution list, the members in the list are changed to reflect the new rule.
Create Dynamic Distribution Lists
You can create a dynamic distribution list with the admin console or with the CLI, as described in this section.
- Admin Console:
-
Home → Manage → Distribution Lists.
-
From the Gear icon, click New.
-
On the Members page, add the dynamic distribution list name. Do not use spaces. Do not add members to the list.
-
Click Next to configure the Properties page.
Table 49. Dynamic Distribution Lists Options Option Description Can receive mail
Enabled by default. If this distribution list should not receive mail select this box.
Hide user in GAL
Enable to create distribution lists that do not display in the Global Address List (GAL). You can use this feature to limit the exposure of the distribution list to only those that know the address.
Mail Server
This is set to auto by default. To select a specific mail server, uncheck auto and select a specific server from the list.
Dynamic Group
Check this box.
Can be used in right management
Uncheck this box.
Member URL
The Member URL is an LDAP-type URL defining a filter that determines which users are added to and removed from the list.
Type the URL for this list. In the command,
ldap://??sub?is the URL. You can add any combination of filters to this to create different types of dynamic distribution lists.Example 10. All users, GAL account names, and spam/ham account listldap:///??sub?(objectClass=zimbraAccount)
Example 11. Delegated administrators listldap:///??sub?(&(objectClass=zimbraAccount)(zimbraIsDelegatedAdminAccount=TRUE))
Example 12. All active accountsldap:///??sub?(&(objectClass=zimbraAccount)(ZimbraAccountStatus=active))
Example 13. All users with the title managerThe title is taken from the account’s Contact Information Job Title field. In this example, this field would be set to "Manager".
ldap:///??sub?(&(objectClass=zimbraAccount)(title=Manager))
New Subscription Requests
Select Automatically reject.
Unsubscription Requests
Select Automatically reject.
-
If the dynamic distribution list should have an alias, create it.
-
If this dynamic distribution list can be managed by other users, enter these email addresses in the Owners page.
-
If you want to set up a reply to address, enter it here. Any replies to this distribution list are sent to this address.
-
Click Finish. The dynamic distribution list is created.
-
Users are added automatically to the list based on the filter you specified. If you add or delete users, the list is updated.
If you use the CLI to modify a dynamic distribution list originally created on the Administration Console, you must set zimbraIsACLGroup FALSE for that dynamic distribution list.
|
Use the CLI zmprov command to manage dynamic distribution lists.
In the command, ldap:///??sub? is the URL.
You can add any combination of filters to this to create different types of dynamic distribution lists.
-
Creating a dynamic distribution list of all new and existing accounts
All users, GAL account names, and spam/ham account names are included. When user accounts are deleted, they are removed from the list.
zmprov cddl <all@domain.com> zimbraIsACLGroup FALSE \ memberURL 'ldap:///??sub?(objectClass=zimbraAccount)' -
Creating a COS and Assign Users
If you create COSs and assign users to the COS based on specific criteria, such as all managers, you can quickly modify a dynamic distribution list to be used for a specific COS.
Example 14. A dynamic distribution list that includes all users that have active accounts in a specific COSzmprov cddl <allusers@domain.com> zimbraIsACLGroup FALSE \ memberURL 'ldap:///??sub?(&(objectClass-zimbraAccount) (zimbraCOSId=513e02e-9abc-4acf-863a-6dccf38252e3) (zimbraAccountStatus=active))'Example 15. A dynamic distribution list that includes all users based on job titlesTo use this, the account’s Contact Information Job Title field must include the title. In this example it would be set to "Manager".
zmprov cddl <allmanagers@domain.com> zimbraIsACLGroup FALSE' \ memberURL ldap:///??sub?(&(objectClass-zimbraAccount) (zimbraCOSId=513e02e-9abc-4acf-863a-6dccf38252e3) (title=Manager))'Example 16. A dynamic distribution list for all delegated administratorszmprov cddl <alldelegatedadmins@domain.com> zimbraIsACLGroup FALSE \ memberURL 'ldap:///??sub?(&(objectClass-zimbraAccount) (zimbraCOSId=513e02e-9abc-4acf-863a-6dccf38252e3) (zimbraIsDelegatedADminAccount=TRUE))'
Moving a Mailbox
Mailboxes can be moved between Zimbra servers that share the same LDAP server.
You can move a mailbox from either the Administration Console or use the CLI command zmmboxmove to reposition a mailbox from one server to another, without taking down the servers.
The destination server manages the mailbox move process. The move runs in the background and the account remains in active mode until most of the data has been moved. The account is locked briefly to move the last data and then returned to active mode.
The mailbox move process goes through the following steps:
-
Mailbox blobs are moved to the new server
-
When most of the content has been moved, the account is put into maintenance mode
-
Database tables, index directories, and any changed blobs are moved
-
The account is put back into active mode
After the mailbox is moved to a new server, a copy still remains on the older server, but the status of the old mailbox is closed. Users cannot log on and mail is not delivered. Check to see that all the mailbox content was moved successfully before purging the old mailbox.
-
Moving a mailbox to a new server
zmmboxmove -a <email@address> --from <servername> --to <servername> -
Purging the mailbox from the old server
zmpurgeoldmbox -a <email@address> -s <servernamee>
Global Configuration Options for Moving Mailboxes
Global configuration options for moving a mailbox can be set to exclude search indexes, blobs, and SM blobs when mailboxes are moved. The following configuration options can be set on either the exporting server or the destination server:
-
zimbraMailboxMoveSkipSearchIndex— If you do not include the search index data, the mailbox will have to be reindexed after the move. -
zimbraMailboxMoveSkipBlobs— Blobs associated with the mailbox, including primary and secondary volumes (SM) are excluded. -
zimbraMailboxMoveSkipHsmBlobs— This is useful when SM blobs already exist for the mailbox being moved. Set this ifzimbraMailboxMoveSkipBlobsis not configured, but you want to skip blobs on SM volumes.
Monitoring Zimbra Servers
The Zimbra Collaboration (Zimbra) includes the following to help you monitor the Zimbra servers, usage, and mail flow:
-
Zimbra Logger package to capture and display server statistics and server status, and to create nightly reports
-
Mailbox quota monitoring
-
MTA mail queue monitoring
-
Log files
Also, selected error messages generate SNMP traps, which can be monitored using an SNMP tool.
| Checking the overall health of the system as a whole is beyond the scope of this document. |
Zimbra Logger
The Logger includes tools for syslog aggregation and reporting. Installing the Logger is optional, but if you do not install it, server statistics and server status information are not captured.
In environments with more than one Zimbra Collaboration server, Logger is enabled on one mailbox server only. This server is designated as the monitor host. The Zimbra Collaboration monitor host is responsible for checking the status of all the other Zimbra Collaboration servers and presenting this information on the Zimbra administration console. Real-time service status, MTA, spam, virus traffic and performance statistics can be displayed. The Logger creates a daily report about mail activity, such as the number of messages, average delivery delay, and errors generated.
| In a multi-server installation, you must set up the syslog configuration files on each server to enable Logger to display the server statistics on the Administration Console, and you must enable the Logger host. If you did not configure this when you installed Zimbra Collaboration, do so now. |
Enabling Server Statistics
Enable server statistics to show both system- wide and server specific data about the inbound message volume, inbound message count, anti-spam/anti-virus activity and disk usage for messages processed in the last 48 hours, 30 days, 60 days, and the last year.
-
On each server, as root, type
/opt/zimbra/libexec/zmsyslogsetup. This updates the syslog configuration to enable gathering server statistics. -
On the logger monitor host, you must configure syslog to accept syslog messages from remote machines. See https://wiki.zimbra.com/wiki/Configuring-Logger-Host for details.
| These steps are not necessary for a single-node installation. |
Reviewing Server Status
- Admin Console:
-
Home → Monitor
The Server Status page lists all servers and services, their status, and when the server status was last checked. The servers include the MTA, LDAP, and mailbox server. The services include MTA, LDAP, Mailbox, SNMP, Anti-Spam, Anti-Virus, Spell checker, and Logger.
To start a server if it is not running, use the zmcontrol CLI command. You
can stop and start services from the Administration Console.
Enabling or Disabling Server Services
- Admin Console:
-
Home → Configure → Servers → server
Server services are enabled or disabled from the Servers → server page. Select Services in the Navigation pane and select to enable or disable services.
Viewing Server Performance Statistics
If the Logger package is installed on a Zimbra mailbox server, Server Statistics shows bar graphs of the message count, message volume, anti-spam, and anti-virus activity. The information is displayed for the last 48 hours, and 30 days, 60 days, and 365 days.
When Server Statistics is selected in the Navigation pane, consolidated statistics for all mailbox servers is displayed. Selecting a specific server in the expanded view shows statistics for that server only. Server specific information also includes disk usage, session information, and mailbox quota details.
The following display system-wide information:
-
Message Count — counts message transactions. A transaction is defined as either the SMTP receipt of a message per person (by Postfix) or a LMTP delivery of it (by mailboxd) per person. For example, if a message is sent to three people, six transactions are displayed. Three for SMTP to Postfix and three for LMTP to mailboxd. The message count is increased by six.
-
Message Volume — displays the aggregate size in bytes of transactions sentand received per hour and per day. Graphs show the total inbound data by volume in bytes.
-
Anti-Spam/Anti-Virus Activity — displays the number of messages that werechecked for spam or viruses and the number of messages that were tagged as spam or deemed to contain a virus. The AS/AV count is increased by one per message scanned. One message sent to three people counts as only one message processed by AS/AV.
The Message Count and the Anti-spam/Anti-virus Activity graphs display a different message count because:
-
Outbound messages may not go through the Amavisd filter, as the system architecture might not require outbound messages to be checked.
-
Messages are received and checked by Amavisd for spam and viruses before being delivered to all recipients in the message. The message count shows the number of recipients who received messages.
-
Server-specific statistics also include the following details:
-
Disk — for a selected server displays the disk used and the disk space available. The information is displayed for the last hour, day, month, and year.
-
Session — displays information about the active Web client, administrator and IMAP sessions. You can see how many active sessions are opened, who is logged on, when the session was created and the last time the session was accessed.
-
Mailbox Quota — displays information about each account sorted by mailbox size in descending order. See Monitoring Mailbox Quotas.
Configuring Logger Mail Reports
The Logger generates a report about mail activity daily at 11:30 p.m. and sends it to the administrator’s email address.
You can configure the number of accounts to include in the report. The default is 25 sender and 25 recipient accounts.
-
Changing the number of recipients to add to the report:
zmlocalconfig -e zimbra_mtareport_max_recipients=<number> -
Changing the number of senders to add to the report:
zmlocalconfig -e zimbra_mtareport_max_senders=<number>
Configuring Disk Space Notifications
You should regularly review your disk capacity and when disks are getting full, take preventative measures to maintain service. A warning alert email notification is sent to the administrator account when disk space is low. The default is to send a warning alert when the threshold reaches 85% and a critical alert when the threshold reaches 95%.
You can change these values. Use zmlocalconfig to configure the
disk warning thresholds.
-
Warning alerts
zmdisklog_warn_threshold -
Critical alert:
zmdisklog_critical_threshold
When starting services with zmcontrol, if the threshold is exceeded a
warning is displayed before the services are started. You should clean up
your disk to free up space.
Monitoring Servers
The Zimbra Collaboration server collects many performance related statistics that can help you diagnose problems and load issues.
- Admin Console:
-
Home → Monitor → Advanced Statistics
The Advanced Statistics page includes advanced graphing options that lets you generate various charts based on statistical information for the CPU, IO, mailboxd, MTA queue, MariaDB and other components.
To chart the graphics in Advanced Statistics, select one of these groups and then select from the list of specific counters for the type of information to display.
The information covers a wide array of data:
-
cpu.csv — CPU utilization. This group contains counters to keep track ofCPU usage (iowait, idle, system, user, time etc.). CPU information can be tracked both at the server level and the process level.
-
df.csv — Captures disk usage. Disk utilization is tracked for each diskpartition.
-
fd.csv — file descriptor count. Keeps track of system file descriptor usageover time. This is primarily used to track down "out-of-file descriptor" errors.
-
mailboxd.csv — Zimbra Collaboration server and JVM statistics. Mailboxdstores almost all of its statistics here. Interesting numbers to keep track of are heap_used, heap_free, imap_conn, soap_sessions, pop_conn, db_conn_count.
-
mtaqueue.csv — Postfix queue. This measures the mail queue size innumber of messages and the size in bytes.
-
proc.csv — Process statistics for Zimbra processes. For example mailboxd/java, MariaDB, OpenLDAP, etc.)
-
soap.csv — SOAP request processing time.
-
threads.csv — JVM thread counts. Counts the number of threads with acommon name prefix.
-
vm.csv — Linux VM statistics (from the vmstat command).
-
io-x.csv and io.csv — store data from the
iostat(1)command (io-x.csvwithiostat -x).
Configuring Denial of Service Filter Parameters
The denial-of-service filter (DoSFilter) limits exposure to requests flooding over HTTP/HTTPS. The DoSFilter throttles clients sending a large number of requests over a short period of time.
DosFilter is only applied to HTTP and HTTPS requests, in other words, it does not affect requests for any other protocols like POP3, IMAP or SMTP. You can modify the configuration to accommodate your specific environmental needs. DoSFilter is enabled by default on Zimbra. Disabling the DoSFilter is not recommended. For information on preventing multiple failed login attempts see Password Policy
Identifying False Positives
Sometimes Zimbra Connector for Outlook (ZCO), mobile ActiveSync clients, or
running some zmprov commands trigger the DoSFilter. When this happens, the
Zimbra mailbox service is unavailable. You can review the following logs
to see if the DoSFilter was applied.
-
/opt/zimbra/log/sync.log.
sync.log entry showing the DoSFilter2021-01-15 15:52:20,426 WARN [qtp1635701107-91:https://x.x.x.x/
Microsoft-Server-ActiveSync?User=zsupport2&DeviceId=Appl5ddddd3NR&DeviceType=iPhone&Cmd=FolderSync][name=zsupport2@domain.com;mid=64;ip=10.1.2.3;Cmd=FolderSync;DeviceID=Appl5K0113UN3NR;Version=12.1;] sync - Service exception com.zimbra.common.service.ServiceException: error while proxying request to target server: HTTP/1.1 503 Service Unavailable
ExceptionId:qtp1635701107-91:https://10.10.0.54:443/Microsoft-Server-ActiveSync?User=zsupport2&DeviceId=Appl5K0113UN3NR&DeviceType=iPhone&Cmd=FolderSync:1358286740426:c5ca7f36bb0a038f Code:service.PROXY_ERROR Arg:(url, STR,"http://mail.domain.com:80/service/soap/SyncRequest"-
/opt/zimbra/log/zmmailboxd.out
zmmailboxd.out entry showing the DoSFilter2021-01-15 15:57:32.537:WARN:oejs.DoSFilter:DOS ALERT:ip=127.0.1.1,session=null,user=nullCustomizing DoSFilter Configuration
The following attributes are used with zmprov to configure the DoSFilter.
These attributes can be configured as global settings and as server
settings. If these attributes are set in the server, the server settings
override the global settings.
You can modify these settings, but the default configuration is recommended.
| Attribute | Description |
|---|---|
DoSFilter Delay |
The delay given to all requests over the rate limit before they are considered. The default is -1.
|
DoSFilter Maximum Requests Per Second |
The maximum number of requests from a connection per second. Requests in excess of this are throttled. The default is 30 and the minimum is 1. |
DoSFilter IP Addresses Whitelist |
IP addresses to ignore when applying the DosFilter. This attribute does not have a default value, however the following loopback IPs are whitelisted by default.
The IP addresses should be comma separated. |
A mailbox server restart is required after modifying these attributes. Type:
zmmailboxdctl restartTuning Considerations for Zimbra Collaboration 8.0.3 and later
-
Zimbra Member Servers — Zimbra servers under the control of a single masterLDAP server are automatically whitelisted by IP address. These hosts are discovered using a GetAllServersRequest. Type as
zmprov gas. -
External Provisioning Hosts/SOAP API — External provisioning hosts can be added to the IP whitelist to ensure that the DoSFilter does not block some requests. For example, a mailbox reindex might make several calls per second that can trigger the DoSFilter.
Working with Mail Queues
When the Zimbra MTA receives mail, it routes the mail through a series of queues to manage delivery; incoming, active, deferred, held, and corrupt.
The incoming message queue holds the new mail that has been received. Each message is identified with a unique file name. Messages are moved to the active queue when there is room. If there are no problems, message move through this queue very quickly.
The active message queue holds messages that are ready to be sent. The MTA sets a limit to the number of messages that can be in the active queue at any one time. From here, messages are moved to and from the anti-virus and anti-spam filters before being delivered to another queue.
Messages that cannot be delivered are placed in the deferred queue. The reasons for the delivery failures are documented in a file in the deferred queue. This queue is scanned frequently to resend the message. If the message cannot be sent after the set number of delivery attempts, the message fails. The message is bounced back to the original sender. The default for the bounce queue lifetime is five days.
The held message queue keeps mail that could not be processed. Messages stay in this queue until the administrator moves them. No periodic delivery attempts are made for messages in the held queue.
The corrupt queue stores damaged unreadable messages.
Change the Bounce Queue Lifetime
-
The MTA server’s bounce queue lifetime is set for five days. To change the default queue lifetime setting
zmlocalconfig -e bounce_queue_lifetime={#} -
To permanently have messages bounced back to the sender, instead of being sent to the deferred queue first
zmlocalconfig -e zimbraLmtpPermanentFailureWhenOverQuota=TRUE
Notifying Senders of Bounced Messages
Before the bounce queue lifetime sends the message back to the sender, senders can be notified that the message they sent is in the deferred queue and has not been delivered.
Configure the following attributes to send a warning message to the sender.
-
Configure the time after which the sender receives the message headers of email that is still queued.
zmlocalconfig -c postfix_delay_warning_time=0h -
Configure the recipient of postmaster notifications with the message headers of mail that the MTA did not deliver.
zmlocalconfig -c postfix_bounce_notice_recipient=postmaster -
Configure the list of error classes that are reported to the postmaster.
zmlocalconfig -c postfix_notify_classes=resource,software
| See Postfix documentation for details on the impact of changes to these Postfix attributes. |
You can monitor the mail queues for delivery problems from the Administration Console.
Viewing Mail Queues
- Admin Console:
-
Home → Monitor → Mail Queues
If you are having problems with mail delivery, you can view the mail queues from the Mail Queues page in the Administration Console to see if you can fix the mail delivery problem. When you open mail queues, the content of the deferred, incoming, active, hold, and corrupt queues at that point in time can be viewed. You can view the number of messages and where they are coming from and going to.
For each queue, the Summary pane shows a summary of messages by receiver domain, origin IP, sender domain, receiver address, sender address, and for the deferred queue, by error type. You can select any of the summaries to see detailed envelope information by message in the Messages pane.
The Messages pane displays individual message envelope information for search filters selected from the Summary pane.
The following mailbox queue functions can be performed for all the messages in a queue:
-
Hold to select a set of messages that you want to hold. Incoming, active,deferred, and corrupt messages can be moved to the Held queue. Messages stay in this queue until the administrator moves them.
-
Release to remove all message from the Held queue. Messages are moved to the Deferred queue.
-
Requeue all messages in the queue being viewed. Requeuing messages can be used to send messages that were deferred because of a configuration problem that has been fixed. Messages are re-evaluated and earlier penalties are forgotten.
-
Delete all messages in the queue being viewed.
The Zimbra MTA, Postfix queue file IDs are reused. If you requeue or delete a message, note the message envelope information, not the queue ID. It is possible that when you refresh the mail queues, the queue ID could be used on a different message.
Flushing Message Queues
You can flush the server of all messages. When you click Flush on the Mail Queue toolbar, delivery is immediately attempted for all messages in the Deferred, Incoming and Active queues.
Monitoring Mailbox Quotas
Mailbox quotas apply to email messages, attachments, calendar appointments, and tasks in a user’s account. When an account quota is reached, all mail messages are rejected. Users must delete mail from their account to get below their quota limit - this includes emptying their Trash, or you can increase their quota.
Viewing Quota
You can check mailbox quotas for individual accounts from Server Statistics on the Administration Console. Mailbox Quota gives you an instant view of the Mailbox Size and Quota Used information for each account.
- Admin Console:
-
Home → Monitor → Server Statistics
-
Select the server for which you want to view statistics.
-
In the Navigation pane, select Mailbox Quota. The Mailbox Quota page displays with the following information:
-
Quota column shows the mailbox quota allocated to the account. Quotas are configured either in the COS or by account.
-
Mailbox Size column shows the disk space used.
-
Quota Used column shows what percentage of quota is used.
-
Increase or Decrease Quota
From a COS or Account, you can configure a quota threshold that, when reached, sends a message alerting users that they are about to reach their mailbox quota.
- Admin Console:
-
Home → Configure → Class of Service → COS → Advanced
Home → Manage → Accounts → account → Advanced
-
Scroll down to the Quota section.
-
Modify the quota settings.
-
Click Save.
Viewing MobileSync Statistics
The MobileSync Statistics page in the Monitor section in the admin console displays the number of currently connected ActiveSync devices that are on the Zimbra Collaboration system.
Monitoring Authentication Failures
To protect against dictionary-based and distributed attacks, you can
configure the zmauditwatch. The script attempts to detect more advanced
attacks by looking at where the authentication failures are coming from and
how frequently they are happening for all accounts on a Zimbra mailbox
server and sends an email alert to the administrator’s mailbox.
The types of authentication failures checked include:
-
IP/Account hash check — The default is to send an email alert if 10authenticating failures from an IP/account combination occur within a 60 second window.
-
Account check — The default is to send an email alert if 15 authentication failures from any IP address occur within a 60 second window. This check attempts to detect a distributed hijack based attack on a single account.
-
IP check — The default is to send an email alert if 20 authentication failures to any account occur within a 60 second window. This check attempts to detect a single host based attack across multiple accounts.
-
Total authentication failure check — The default is to send an email alert if1000 auth failures from any IP address to any account occurs within 60 seconds. The default should be modified to be 1% of the active accounts on the mailbox server.
The default values that trigger an email alert are changed in the following
zmlocalconfig parameters:
-
IP/Account value, change
zimbra_swatch_ipacct_threshold -
Account check, change
zimbra_swatch_acct_threshold -
IP check, change
zimbra_swatch_ip_threshold -
Total authentication failure check, change
zimbra_swatch_total_threshold
Configure zimbra_swatch_notice_user with the email address that should
receive the alerts.
Viewing Log Files
Zimbra Collaboration logs its activities and errors to a combination of system logs through the syslog daemon as well as Zimbra specific logs on the local file system. The logs described below are the primary logs that are used for analysis and troubleshooting.
Local logs containing Zimbra Collaboration activity are in the /opt/zimbra/log
directory.
-
audit.log — This log contains authentication activity of users and administrators and login failures. In addition, it logs admin activity to be able to track configuration changes.
-
clamd.log — This log contains activity from the anti-virus application clamd.
-
freshclam.log — This log contains log information related to the updating of the clamd virus definitions.
-
mailbox.log — This log is a mailboxd log4j server log containing the logs from the mailbox server. This includes the mailbox store, LMTP server, IMAP and POP servers, and Index server.
-
myslow.log — This slow query log consists of all SQL statements from the mailbox server that took more then
long_query_timeseconds to execute.long_query_timeis defined in/opt/zimbra/conf/my.cnf. -
spamtrain.log — This log contains output from
zmtrainsaduring regularly scheduled executions from the cron. -
sync.log — This log contains information about Zimbra Collaboration mobilesync operations.
Other logs include:
-
/opt/zimbra/jetty/logs/ — This is where Jetty-specific activity is logged.
-
/opt/zimbra/db/data/<hostname>.err — This is the message store database error log.
-
/opt/zimbra/logger/db/data/<hostname>.err — This is the Logger database error log.
Zimbra Collaboration activity logged to System syslog
-
/var/log/zimbra.log — The Zimbra syslog details the activities of the ZimbraMTA (Postfix, amavisd, anti-spam, anti-virus), Logger, Authentication (cyrus-sasl), and Directory (OpenLDAP). By default LDAP activity is logged to
zimbra.log.
Syslog
Zimbra Collaboration modifies the systems syslog daemon to capture data from the mail and
local syslog facility to /var/log/zimbra.log. This allows syslogd to
capture data from several Zimbra Collaboration components including
Postfix, Amavis, ClamAV, mailboxd, zmconfigd, and logger. The SNMP module
uses the data from the log file to generate traps for critical errors. The
zmlogger daemon also collects a subset of the data in this file to provide
statistics on the utilization of Zimbra Collaboration via the
Administration Console.
By default, mailboxd is configured to log its output to
/opt/zimbra/log/mailbox.log. You can enable mailboxd to take advantage
of a centralized syslogd infrastructure by enabling the following either
globally or by server:
zmprov mcf zimbraLogToSysLog TRUEUsing log4j to Configure Logging
The Zimbra Collaboration server uses log4j, a Java logging package as the
log manager. By default, the Zimbra Collaboration server has log4j
configured to log to the local file system. You can configure log4j to
direct output to another location. Go to the
Log4j website for information about
using log4j.
Zimbra does not check the log4j changes. To remove all account loggers and
reloads in /opt/zimbra/conf/log4j.properties, use the zmprov
resetAllLoggers command.
Logging Levels
The default logging level is set to include logs that are generated for INFO, WARNING, ERROR and FATAL. When problems start to occur, you can turn on the DEBUG or TRACE log levels.
To change the logging levels, edit the log4j properties,
log4j.properties, log4j.logger.zimbra.
When enabling DEBUG, you can specify a specific category to debug. For
example, to see debug details for POP activity, you would type
logger.zimbra.pop=DEBUG.
The following categories are predefined in log4j:
|
Account operations |
|
ACL operations |
|
Backup and restore |
|
Inmemory cache operations |
|
Calendar operations |
|
DAV operations |
|
Database connection tracing |
|
Server extension loading |
|
Mail filtering |
|
GAL operations |
|
IMAP protocol operations |
|
Index operations |
|
Filesystem operations |
|
LDAP operations |
|
LMTP operations (incoming mail) |
|
General mailbox operations |
|
Miscellaneous |
|
Changes to mailbox state |
|
POP protocol operations |
|
Redo log operations |
|
Security events |
|
User session tracking |
|
SMTP operations (outgoing mail) |
|
SOAP protocol |
|
SQL tracing |
|
Mail store disk operations |
|
Sync client operations |
|
Startup/shutdown and other system messages |
|
Wiki operations |
|
Zimlet operations |
| Changes to the log level take affect immediately. |
| Level | Local? | Syslog | SNMP Trap | When Used |
|---|---|---|---|---|
FATAL |
Y |
Y |
Y |
Designates very severe error events that the application to abort or impact a large number of users. For example, being unable to contact the MariaDB database. |
ERROR |
Y |
Y |
N |
Designates error events that might still allow the application to continue running or impact a single user. For example, a single mailbox having a corrupt index or being unable to delete a message from a mailbox. |
WARN |
Y |
N |
N |
Designates potentially harmful situations but are usually recoverable or can be ignored. For example, user log in failed. |
INFO |
Y |
N |
N |
Designates information messages that highlight the progress of the application, basic transaction-level logging. For example, server start-ups, mailbox creation/deletion, account creation. |
DEBUG |
Y |
N |
N |
Events that would generally be useful to help a customer debug problems. |
(*) A few non-critical messages such, as service startup messages, will generate traps.
Protocol Trace
Protocol trace is available in the following logging categories:
zimbra.smtp zimbra.lmtp zimbra.soap zimbra.imap zimbra.imap-client zimbra.pop zimbra.pop-client
Reviewing mailbox.log Records
The mailbox.log file contains every action taken on the mailbox server,
including authentication sessions, LMTP, POP3, and IMAP servers, and Index
server. Review the mailbox.log to find information about the health of
your server and to help identify problems.
mailbox.log records valid and invalid login attempts, account activity
such as opening email, deleting items, creating items, indexing of new
mail, server activities including start and stop. The progress of an
activity on the mail server is logged as INFO. If the expected results of
the activity fails and errors occurs, an exception is written to the log.
You can set up logging options for a single account in order to trace
account activity for one user without filling up mailbox.log with log
messages for unrelated accounts. See Command-Line
Utilities, the zmprov miscellaneous section.
Log pattern
by default log entries in mailbox.log have the following Log4j pattern:
%d %-5p [%t] [%z] %c{1} - %m%n
This pattern consists of 6 blocks of data:
-
Date and time (e.g.:
2021-01-22 19:23:07,100) -
Log level (e.g.
INFO) -
Thread name (e.g.
[qtp1043351526-547:https:https://localhost:7071/service/admin/soap/DeleteAccountRequest],[Index-9], etc.) -
Zimbra Collaboration context
-
Component name (e.g.
soap,mailbox,mbxmgr, etc.) -
Log message. Note: the log message section may span multiple lines. When a log message contains an exception, the stack trace will always start on a new line below the error message.
You can read more about Log4j patterns in Log4j PatternLayout documentation.
Thread name in mailbox.log
Thread names in mailbox.log are prefixed to identify internal components. Most threads have one of the following naming convention: "{thread prefix}-{thread number}" or "{thread prefix}-{thread number}:{url}".
The following {thread prefix} values are currently used for thread names in Zimbra Collaboration: btpool, pool, LmtpServer, ImapServer,ImapSSLServer, Pop3Server, Pop3SSLServer, ScheduledTask, Timer, AnonymousIoService, CloudRoutingReaderThread, GC, SocketAcceptor, Thread, qtp.
Threads with prefix qtp are created by Jetty QueuedThreadPool and have the following naming convention: "qtp{hash code}-{thread number}:{url}" where {hash code}` is the hash code value of the instance of QueuedThreadPool that owns the thread (see Object::hashCode in Java platform documentation).
{thread number} in thread names is an integer that monotonically increases within each thread factory. Thread numbers are reset when mailboxd process is stopped or restarted.
Log records reported by threads that serve SOAP requests will usually contain URL of the request being served in {url} part of thread name, as in the following example:
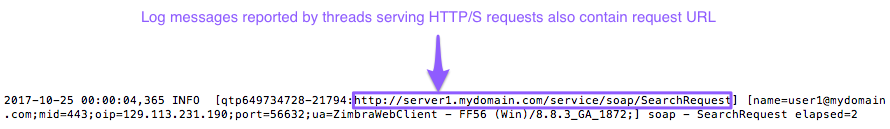
Due to a known bug in Zimbra Collaboration {url} part of the thread name may contain duplicate protocol identifier, as in the following example:
[qtp1043351526-547:https:https://localhost:7071/service/admin/soap/DeleteAccountRequest]
Zimbra Collaboration Context in mailbox.log
[%z] section in the log pattern describes Zimbra Collaboration context and consists of key-value pairs in the format key=value, separated by semi-colons (;). In cases where a value contains a semi-colon, the semi-colon is replaced with a double semi-colon (;;). E.g., browser UserAgent strings often include semi-colons, such as this one "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.100 Safari/537.36". In mailbox.log, this UserAgent string will appear as following:
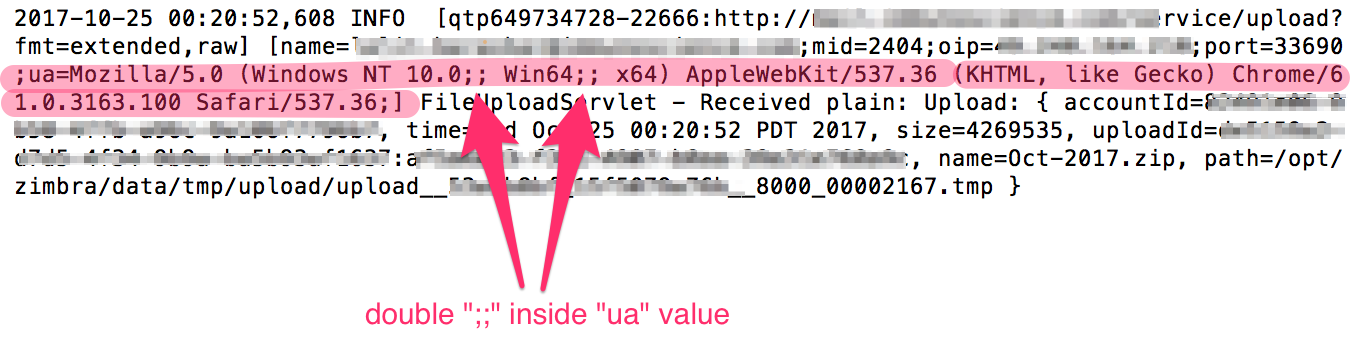
The following key value pairs are currently supported and may be recorded in log entries in any order and any combination:
-
ip— IP of the TCP/IP client making a request -
oip— originating IP address. When a request is made through NGINX proxy, this value will contain the IP address of the client application, whileipvalue will contain the IP address of the proxy server -
cid— connection id of a server that is monotonically increasing - useful for tracking individual connections -
id— ID of the target account -
name— name of the target account (email address) -
aid— ID of the authenticated account. Only present if target account is different then authenticated account -
aname— name of the authenticated account. Only present if target account is different then authenticated account -
mid— ID of requested mailbox. Only present if request is dealing with a mailbox -
ua— name of the client application (i.e. User Agent) -
via— list of IP addresses and user-agents of the request’s proxy chain -
soapId— ID assigned to a SOAP request to track proxied hops for a particular request -
msgid— value of Message-ID header of the message being operated on -
ds— name of the Data Source being operated on -
port— server port to which the client connected -
oport— originating port number of request -
oproto— originating protocol of request. This can be passed by internal components that make SOAP requests on behalf of a user (e.g. MTA)
The example below is a record showing that
on October 25, 2021, 28 minutes after midnight, a POP3 client with IP address 222.173.186.17 has contacted the Zimbra Collaboration server and that the request was proxied through a local proxy server with IP 10.1.1.136.
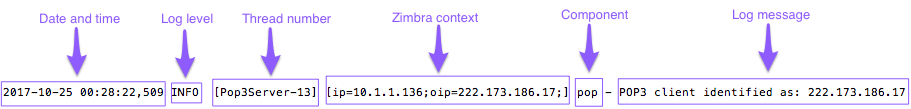
The following example shows a record of a failed IMAP STATUS request sent by user1@mydomain.com using AquaMail mobile app. The user’s device has IP address 72.83.144.255 (as reported in oip field). The request came to IMAP server via Zimbra Collaboration nginx proxy, which has IP address 10.4.4.138 (as reported in ip and via fields).
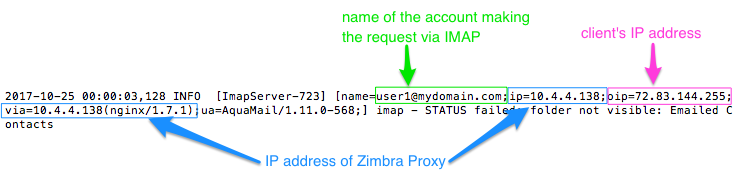
The following example shows a record of LMTP server delivering a message. The IP address in this log message most likely belongs to Zimbra Collaboration MTA running on local network.
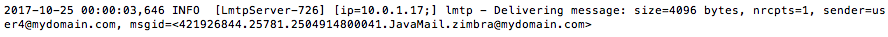
The next example shows a record of MailboxPurge thread purging message with ID 462 from the mailbox of test@mydomain.net. This log message does not have ip, oip, port or via fields, because it originates from an internal process rather than from an external request.
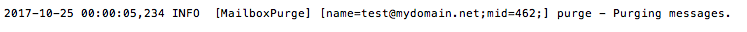
Handler Exceptions and Stack Traces
If an error occurs during the progress of an activity, a handler exception is added to the end of the log record to notify you that an event occurred during the execution of the process that disrupted the normal flow. This signals that some type of error was detected.
007-06-25 00:00:10,379 INFO [btpool0-1064] [name=nriers@example.com;mid=228;ip=10.2.3.4;ua=zimbra Desktop/0.38;] SoapEngine - handler exceptionSometimes a stack trace is displayed after the exceptions notification. A stack trace reports the threads and monitors in Zimbra’s mailboxd service. This information aids in debugging, because the trace shows where the error occurred. The last few entries in the stack often indicate the origin of the problem. When the caused by descriptor is included in the log line, this is the root of the error. In the example below, the error was caused by 501, bad address syntax.
com.example.cs.mailbox.MailServiceException: Invalid address: Jon R
at com.example.cs.mailbox.MailServiceException.internal_SEND_FAILURE (MailServiceException.java:412)
at com.example.cs.mailbox.MailServiceException.SEND_ABORTED_ADDRESS_FAILURE MailServiceException.java:416)
...
at org.mortbay.thread.BoundedThreadPool$PoolThread.run(BoundedThreadPool.java:442)
Caused by: com.example.cs.mailbox.MailSender$SafeSendFailedException: 501 Bad address syntax; chained exception is: com.sun.mail.smtp.SMTPAddressFailedException: 501 Bad address syntax
at com.sun.mail.smtp.SMTPTransport.rcptTo(SMTPTransport.java:1196)
at com.sun.mail.smtp.SMTPTransport.sendMessage(SMTPTransport.java:584)
at javax.mail.Transport.send0(Transport.java:169)
at javax.mail.Transport.send(Transport.java:98)
at com.example.cs.mailbox.MailSender.sendMessage(MailSender.java:409)
at com.example.cs.mailbox.MailSender.sendMimeMessage(MailSender.java:262)
... 30 moreMailbox log files
The mailbox.log files rotate daily. The mailbox log files are saved in
/opt/zimbra/log. Previous mailbox.log file names include the date the
file was made. The log without a date is the current log file. You can
back up and remove these files.
Troubleshooting Mail Problems
To review the mailbox.log for errors, search for the email address or the
service that is experiencing the problem. Also, search for WARN or ERROR
log levels, read the text of the message. When you find the error, review
the records, tracing the events that happened before the problem was
recorded.
System Crashing
When your system crashes, locate the startup message and then look for errors before the startup message date. This example shows an out-of-memory error on June 17, 2021.
2021-06-25 01:56:18,725 INFO [main] [] soap - Servlet SoapServlet starting upLook for errors before the startup message.
2021-06-17 20:11:34,194 FATAL [btpool0-3335] [name=samd@example.com;aname=abcadmin@example.com;mid=142;ip=10.3.4.5;ua=zimbraConnectorForBES/5.0.207;] system - handler exception java.lang.OutOfMemoryError: PermGen spaceMail Delivery Problem
Locate the "LmtpServer" service. This example includes a stack trace report with a caused by explanation that the recipient address was rejected as the address must be a fully-qualified address.
2021-06-25 10:47:43,008 INFO [LmtpServer-250]
[name=bigen@example.com;mid=30;msgid=<1291804360.35481182793659172.JavaMail.root@example.com>;] lmtp - rejecting message bigen@example.com: exception occurred
com.zimbra.cs.mailbox.MailServiceException: redirect to too failed
at com.zimbra.cs.mailbox.MailServiceException.internal_SEND_FAILURE (MailServiceException.java:412)
at com.zimbra.cs.mailbox.MailServiceException.SEND_FAILURE(MailServiceException.java:424)
at com.zimbra.cs.filter.zimbraMailAdapter.executeActions(zimbraMailAdapter.java:286)
at org.apache.jsieve.SieveFactory.evaluate(SieveFactory.java:151)
at com.zimbra.cs.filter.RuleManager.applyRules(RuleManager.java:177)
at com.zimbra.cs.lmtpserver.zimbraLmtpBackend.deliverMessageToLocalMailboxes(zimbraLmtpBackend.java:325)
at com.zimbra.cs.lmtpserver.zimbraLmtpBackend.deliver(zimbraLmtpBackend.java:140)
at com.zimbra.cs.lmtpserver.LmtpHandler.doDATA(LmtpHandler.java:441)
at com.zimbra.cs.lmtpserver.LmtpHandler.processCommand(LmtpHandler.java:205)
at com.zimbra.cs.tcpserver.ProtocolHandler.processConnection(ProtocolHandler.java:231)
at com.zimbra.cs.tcpserver.ProtocolHandler.run(ProtocolHandler.java:198)
at EDU.oswego.cs.dl.util.concurrent.PooledExecutor$Worker.run(Unknown Source)
at java.lang.Thread.run(Thread.java:619)
Caused by:
com.zimbra.cs.mailbox.MailSender$SafeSendFailedException: 504 <too>: Recipient address rejected: need fully-qualified address ;
chained exception is: com.sun.mail.smtp.SMTPAddressFailedException: 504 <too>: Recipient address rejected: need fully-qualified address
at com.sun.mail.smtp.SMTPTransport.rcptTo(SMTPTransport.java:1196)
at com.sun.mail.smtp.SMTPTransport.sendMessage(SMTPTransport.java:584)
at javax.mail.Transport.send0(Transport.java:169)
at javax.mail.Transport.send(Transport.java:120)
at com.zimbra.cs.filter.zimbraMailAdapter.executeActions(zimbraMailAdapter.java:281)
... 10 moreAccount Error - Login error
mailbox.log logs any successful or unsuccessful login attempts from IMAP,
POP3 or ZWC. When you are looking for a login error, start by looking for
"Auth." This example shows that someone from IP address 10.4.5.6 was
trying to log in as admin on the Zimbra Classic Web App, using Firefox in a
Windows OS. Permission was denied because it was not an admin account.
2021-06-25 09:16:11,483 INFO [btpool0-251] [ip=10.4.5.6;ua=zimbraWebClient - FFX.X (Win);] SoapEngine - handler exception
com.zimbra.common.service.ServiceException: permission denied: not an admin account
at com.zimbra.common.service.ServiceException.PERM_DENIED(ServiceException.java:205)
at com.zimbra.cs.service.admin.Auth.handle(Auth.java:103)Account Errors - IMAP or POP related
When you are looking for a log because of an IMAP or POP issue, look for "ImapServer/Pop3Server." This example shows a fatal IMAP server error occurred while trying to connect siress@example.com.
mailbox.log.2021-06-19:2021-06-19 15:33:56,832 FATAL [ImapServer-2444] [name=sires@example.com;ip=127.0.0.1;] system - Fatal error occurred while handling connectionReading a Message Header
Each email message includes a header that shows the path of an email from its origin to destination. This information is used to trace a message’s route when there is a problem with the message. The Zimbra email message header can be viewed from the Zimbra Classic Web App Message view. Right-click on a message and select Show Original.
The following lines are in the message header:
-
Date — The date and time the message was sent. When you specify time, you can specify range by adding start and stop time to search for messages.
-
From — The name of the sender and the email address
-
To — The name of the recipient and the email address. Indicates primary recipients.
-
Message-ID — Unique number used for tracing mail routing
-
In-Reply-To — Message ID of the message that is a reply to. Used to link related messages together.
-
Received: from — The name and IP address the message was sent from. The header displays Received: from information from the MTA to the LMTP and from the local host.
Fixing Corrupted Mailbox Index
Mail messages and attachments are automatically indexed before messages are deposited in a mailbox. Each mailbox has an index file associated with it. This index file is required to retrieve search results from the mailbox.
If a mailbox’s index file becomes corrupt or is accidentally deleted, you can re-index the messages in the mailbox from the Administration Console.
Text searches on an account might or might not fail with errors when the index is corrupt. You cannot count on a user reporting a failed text search to identify that the index is corrupt. You must monitor the index log for messages about corrupt indexes. If the server detects a corrupt index, a message is logged to the Zimbra mailbox.log at the WARN logging level. The message starts with Possibly corrupt index. When this message is displayed, the administrator must correct the problem. In many cases correcting the problem might mean reindexing the mailbox.
Reindexing a mailbox’s content can take some time, depending on the number of messages in the mailbox. Users can still access their mailbox while reindexing is running, but because searches cannot return results for messages that are not indexed, searches may not find all results.
Checking for Index Corruption
Run a sanity check on a specific mailbox index using the zmprov
verifyIndex command.
zmprov verifyIndex <user@example.com>If problems are detected, a failure status is returned and a repair can be performed on the index.
Repairing and Reindexing a Corrupt Index
Use the reIndexMailbox command to repair and reindex a corrupt index.
zmprov reIndexMailbox <user@example.com> startThis returns a status of started.
SNMP Monitoring and Configuration
SNMP Monitoring Tools
You will probably want to implement server monitoring software in order to monitor system logs, CPU and disk usage, and other runtime information.
Zimbra Collaboration uses swatch to watch the syslog output to generate SNMP traps.
SNMP Configuration
Zimbra Collaboration includes an installer package with SNMP monitoring. This package should be run on every server (Zimbra Collaboration, OpenLDAP, and Postfix) that is part of the Zimbra Collaboration configuration.
The only SNMP configuration is the destination host to which traps should be sent.
Errors Generating SNMP Traps
The Zimbra Collaboration error message generates SNMP traps when a service is stopped or is started. You can capture these messages using third-party SNMP monitoring software and direct selected messages to a pager or other alert system.
Checking MariaDB
The MariaDB database is automatically checked weekly to verify the health of the database. This check takes about an hour. If any errors are found, a report is sent to the administrator’s account. The report name that runs the MariaDB check is zmbintegrityreport, and the crontab is automatically configured to run this report once a week.
| When the MariaDB database is checked, running this report can consume a significant amount of I/O. This should not present a problem, but if you find that running this report does affect your operation, you can change the frequency with which zmbintegrityreport is run. See Zimbra Crontab Jobs. |
Checking for Zimbra Collaboration Software Updates
When Zimbra Collaboration is installed, the Zimbra Collaboration software update utility is automatically configured to check for the latest Zimbra Collaboration version once a day and if there is an update, to send notification to the address that is configured in the Administration Console’s Server Updates.
The dates and times Zimbra Collaboration checked for updates is saved to the Updates tab and an email notification is sent out until you update the Zimbra version. If you do not want to receive an email notification of updates, disable Send notification email when updates are available.
You can configure the following:
-
Server that checks for updates — Available servers are listed and only one server is configured. The selected server checks for updates and the result of the update response from www.zimbra.com is stored in LDAP.
-
Check for updates every x — The default is to check once a day. You can change the frequency interval to check every x hours, minutes, or seconds. A cron job is configured to check for new updates. If the frequency interval is less than 2 hours, the crontab file must be modified.
-
Updates URL — This address is the URL that the server connects to when checking for updates. When a Zimbra Collaboration server checks for updates, it transmits its version, platform, and build number to Zimbra. Normally, this URL is not changed.
-
To be notified of updates, check the Send notification email when updates are available and enter the send to and send from addresses. The default address is the administrator’s address.
-
A generic email is created. The subject and content of the email can be changed.
-
When a server polls the URL specified, the response is displayed.
Updating Zimbra Connector for Microsoft Outlook
The Zimbra Connector for Microsoft Outlook (ZCO) msi file is available from
the Zimbra Utilities Downloads page on the Administration Console. When a
newer version of ZCO is released before a new version of Zimbra, you can
upload the newer ZCO msi file to the Zimbra server from the Administration
Console. The file is uploaded to the
/opt/zimbra/jetty/webapps/zimbra/downloads folder.
- Admin Console:
-
Home → Tools and Migration → Client Upload
-
Download the new ZCO file to a computer that you can access from Client Upload in the Administration Console
-
Click Browse to locate the ZCO file to upload.
-
Restart Zimbra:
zmcontrol restartor run
/opt/zimbra/libexec/zmupdatedownload
-
The downloads/index.html file is updated with the latest ZCO client
version. This new file can be downloaded from the ZCO link on the
Administration Console Home → Tools and Migration → Download page.
| If you do not restart the server, the ZCO download link on the Zimbra Utilities Download page does not select the newer version to download. |
Notifications and Alerts Sent by Zimbra Collaboration
Service status change notification
This notification is sent when service are stopped or restarted.
Server Start Notification Message
Subject: Service <service_name> started on <zimbra_host> Service status change: <zimbra_host> <service> changed from stopped to running
Server Stop Notification Message
Subject: Service <service_name> stopped on <zimbra_host> Service status change: <zimbra_host> <service> changed from running to stopped
Disk usage notification
A warning alert email notification is sent to the admin account when disk space is low. The default is to send a warning alert when the threshold reaches 85% and a critical alert when the threshold reaches 95%
Subject: Disk <volume> at ##% on <zimbra_host> Disk warning: <zimbra_host> <volume> on device <device_name> at ##%
Duplicate mysqld processes running notification
A script is executed to see if mysqld process is running to detect cases where corruption is likely to be caused. An email is generated if it finds more than 1 mysqld process running.
Subject: ZCS: Duplicate mysqld processes detected! PID:$pid PPID:$ppid PGRP:$pgrp CMD: $cmdline More then $maxcnt mysqld processes are running Parent processes include: $procs This should be investigated immediately as it may lead to database corruption
SSL certificates expiration notification
A report runs on the first of each month and warns of certificates expiring with the next 30 days.
Subject: ZCS: SSL Certificates approaching expiration! The Administration Console and CLI Certificate Tools guide provides instructions on how to replace you self-signed or commercial certificate. https://wiki.zimbra.com/index.php?title=Administration_Console_and_CLI_Certificate_Tools SSL Certificate expiration checked with $0 on <zimbra_host>.
Daily report notification
When the logger package is installed, a daily mail report is automatically scheduled in the crontab. The report is sent daily to the administrator’s mailbox.
Subject: Daily mail report for <day> <daily report data>
Database integrity check notification
The MariaDB database can be checked by running the zmdbintegrityreport automatically scheduled in the crontab to run on a weekly basis. A report is sent to the administrator’s mailbox.
Subject: Database Integrity check report for <zimbra_host> Generating report can't run $cmd: $! Database errors found. $cmd --password=XXXXXXXX <cmd output> No errors found command failed $!
Backup completion notification
When configuring the type of backups that should be run, you can set up to receive notification about the results of a backup session.
Subject: ZCS BackupReport:SUCCESS Server: <server> Type: incremental Status: completed Started: Fri, 2021/07/13 01:00:05.488 PDT Ended: Fri, 2021/07/13 01:10:09.842 PDT Redo log sequence range: 2 .. 2 Number of accounts: 500
Archiving and Discovery
Zimbra Archiving and Discovery is an optional feature that enables archiving of messages that were delivered to or sent by Zimbra Collaboration and to search across mailboxes.
The installation of the archiving feature provides the Zimbra Collaboration discovery tool (also known as cross mailbox search) and sets the attributes that allow archiving to be enabled on the Zimbra MTAs.
Archiving is configured on a per account basis. Each account enabled for archiving requires a Zimbra archive license. When archiving is enabled for an account, a copy of all email from or to that account is forked at the MTA and a copy of the message is delivered to a predefined archive mailbox. The archiving process is transparent to account users.
Discovery allows you to conduct a search for email messages across live and archived mailboxes and copy the results to a specified mailbox.
How Archiving Works
When a message is sent or received by a user, the message is always routed through the Postfix MTA. The Postfix MTA allows integrating software that can perform actions on messages that are in flight. When archiving is enabled for the sender or the recipient of messages, Zimbra Archiving integrates with an MTA hook and the Amavisd-New utility to fork a copy of the message.
The “does recipient or sender have archiving enabled” check is performed on the SMTP standard envelope and not on the From or To/Cc headers. Since checks are performed on the envelope, Bcc copies and messages sent to distribution lists are captured.
For example, if User A sends a message to User B, and if User B has archiving enabled, the MTA delivers two messages — one to User B’s mailbox and one to User B’s archive mailbox. The message received in User B’s mailbox looks normal, as shown in the following example:
Received: from localhost (localhost.localdomain [127.0.0.1])… From: userA@example.com To:userB@example.com Subject: New License Key Message-ID: <015f01c717fe$70f042d1$b1d6f61d@thom> Date: Mon, 04 Nov 2021 23:48:18 -0000 Hi B, Can you send me the license key for the software again? Thanks, A
The message received in User B’s archive mailbox contains additional X-Envelope-From and X-Envelope-To headers. These headers show the real email address the message was sent from and each of the email addresses that the message was sent to.
Received: from localhost (localhost.localdomain [127.0.0.1])… From: userA@example.com To:userB@example.com Subject: New License Key Message-ID: <015f01c717fe$70f042d1$b1d6f61d@thom> X-Envelope-From: userA@example.com X-Envelope-To: userB@example.com Date: Mon, 04 Nov 2021 23:48:18 -0000 Hi B, Can you send me the license key for the software again? Thanks, A
Zimbra archiving can be set up to create archiving accounts that are maintained within Zimbra Collaboration or to work with third-party archiving systems using SMTP forwarding to send messages to a third-party archive server. For third-party archiving, Zimbra Collaboration is configured to act as the forwarding agent.
How Discovery Works
The discovery feature of Archiving and Discovery is used to search across live* and archive mailboxes for email messages and attachments. The discovery tool can be run from the Administration Console and the results are copied to a target mailbox that you specify.
* A live mailbox is an account on the system other than archive accounts and system accounts.
You can search outgoing and incoming email by date, from, to, cc, subject, keywords, and attachments. You can also create queries to search by name, dates and time ranges, distribution list, aliases.
Search results are placed in a target mailbox. You can organize your search results by creating different target mailboxes or by creating individual folders within a target mailbox for each search you run. X-zimbra-Source header information is added to each message header that is copied to the targeted mailbox. This header label includes the account ID, the account name, and the server that the account resides on.
You can see the results of the search by logging on to the target mailbox address.
Installing the Archiving Package
You can install the archiving package on an existing single-server deployment or on a multi-server deployment.
If the mailbox server and the MTA server reside on the same node, you
configure and enable archiving as a single process. If your mailbox and MTA
servers are on separate nodes, the zimbra-archive package is installed
first on at least one mailbox server and then the archiving component is
enabled on each MTA in the deployment.
Installing zimbra-archiving in a Single-Server Environment
The following scenario assumes that the LDAP, MTA, mailstore and archiving servers are on the same node.
-
Refer to the Zimbra Collaboration Single Server Installation Guide to open an SSH connection to the Zimbra Collaboration server. Log on to the server as root and run the
./install.shcommand to begin the upgrade process. -
Accept the license agreement and type Yes to run the upgrade.
-
Type Yes for
zimbra-archivingwhen presented with the packages to be installed.
The upgrade process begins and the archiving package is installed. At this point, the Discovery feature is installed and can be used.
To enable archiving, switch to the zimbra user and enable archiving on the MTA server.
zmprov ms <zmhostname> +zimbraServiceEnabled archivingRestart the server.
zmcontrol restartInstalling zimbra-archiving in a Multi-Server Environment
The following upgrade scenario is adding a new server that is dedicated as an archiving server to your Zimbra Collaboration environment.
Before beginning the install process, record the following information.
You need this information when you install the archiving server. Run the
zmlocalconfig -s command to find the information.
LDAP Admin Password _____________________ LDAP Hostname _____________________ LDAP Port _____________________
Refer to the Multiple-Server Installation chapter in the Zimbra Collaboration Multi-Server Installation guide for detailed steps on installing the packages.
-
Open an SSH connection to the mailbox server that is being configured for archiving. Log on to the server as root and unpack the Zimbra software. Run the
./install.shcommand to begin the install process. -
Type y and press Enter to install the following packages:
-
zimbra-store -
zimbra-archivingThe
zimbra-corepackage is installed by default.
-
-
Type y and press Enter to modify the system.
-
The Main menu displays the default entries for the Zimbra component you are installing. To expand the menu, type x and press Enter.
-
Select the Common Configuration menu and configure the LDAP Hostname, LDAP password, and LDAP port.
-
Select the zimbra-store menu and configure the Admin password and the License file location.
Complete the installation process following the steps in the Multi-server Installation guide, under Installing Zimbra Mailbox Server.
At this point, the Discovery feature is installed and can be used.
Manage Archiving From the Administration Console
After Archiving is installed, you can set up archiving and manage it from the Administration Console.
Enable Archiving
- Admin Console:
-
Home → Configure → Global Settings → MTA, from Archiving Configuration check Enable archiving
Restart Zimbra from the command line
zmcontrol restartCreating a Dedicated Archive COS
You can configure attributes in the COS to set mailbox features, quotas, and passwords, turn off spam and virus checks, and hide the archive accounts from GAL.
- Admin Console:
-
Home → Configure → Class of Service, from the Gear icon select New
-
Change Features and Preferences as required for an Archiving COS.
-
If you have a dedicated archive server, in the Server Pool page, deselect the archiver server from the list. In a multi-server deployment with a dedicated archive server, the server should be removed from the COS server pool so that the archive server is not randomly assigned to new accounts.
These steps to remove the server from the server pool are not done in a single-server deployment. Creating a dedicated archiving COS is a good idea as this makes it easy to create archive mailboxes that are configured the same. -
Modify the options on the Advanced page if required.
-
In the Archiving page, check the Enable archiving box to make this COS an archiving cos.
-
If you want to change the format for the naming scheme for archive accounts, modify the two template fields. See the Setting Up an Archive Account Name section for more information.
-
Click Finish.
-
Setting Up an Archive Account Name
You use attributes to create and manage the naming scheme for archive accounts. You can set up these attributes either by COS or by account. For COS, these attributes can be changed from the Administration Console, COS or individual account’s Archiving page.
-
Account date template. Sets the date format used in the name template. The default is
yyyyMMdd. Adding the date to the account name makes it easier to roll off older data from the system to backups. -
Account name template. Sets up how the archive mailbox name is created. The default value is
${USER} ${DATE}@${DOMAIN}.archive.
The archive account address would be similar to the following example:
user-20210510@example.com.archive
If you change the default value, you must use syntax that creates a valid
email address. We recommend that you add .archive to all archive accounts
to create archive mailboxes in a non-routable domain to prevent spoofing of
the archives.
When the template based on the zimbraArchiveAccountDateTemplate attribute
is set up, amavisArchiveQuarantineAccount is updated to the new template
name when zmconfigarchive is run.
Administering the archive server
The amavisd-new server process controls account archiving as well as
antivirus and anti-spam processes. The zmarchivectl command can be used to
start, stop, restart or obtain the status of the amavisd-new server process
that controls account archiving. Caution should be taken when starting or
stopping the archiving process as it is a shared server process between
archiving, antivirus, and anti-spam processes. Performing actions on any of
them affect any of the other services that may be enabled in your
deployment.
If you want to disable archiving but not antivirus or anti-spam services, disable the respective service either through the CLI or through the Administration Console.
Set Up Archiving for a Users Mailbox
Four attributes are related to the archive feature for accounts. Two that configure a mailbox and two template attributes to construct the archive account names.
To set up archiving for a mailbox two attributes are configured on the primary user’s mailbox. One attributed enables archiving and the second shows where messages are being archived.
-
Currently archived to — The current archive address. Archiving is to a single account. If this is unset, archiving is not enabled.
-
Archived accounts — Any previous and current archive addresses that this mailbox was archived to. containing all the accounts that have been archived for the given account.
Archive Mailboxes
You can create an archive mailbox with or without an assigned COS. You can also forward archive email to a third-party.
|
Accounts with archiving enabled are counted against the number of
Zimbra licenses purchased for archiving. Archive mailboxes are listed
in the Administration Console along with the live accounts. To see
current license information, go to the Administration Console: Home → Configure → Global Settings → License. |
Creating an archive mailbox and assigning a COS
Archive accounts are created based on the Zimbra Archive name templates.
-
The attribute —
zimbraIsSystemResource— is added to the archive account and set to TRUE. -
The archive account is displayed in the Administration Console.
-
When a message is received in a mailbox with archiving enabled, a copy of the message is sent to the archive mailbox.
Log on as zimbra, and use the zmarchiveconfig command:
zmarchiveconfig enable <account@example.com> archive-cos <archive>Creating an Archive Mailbox with No COS or Password
If the archive account is not assigned a COS, the following settings are set by default.
-
Mailbox quota is set to 0, unlimited quota.
-
Spam and virus checks are disabled.
-
Hide user in GAL is enabled, so the archive account does not display in the GAL
Log on as zimbra, and use the zmarchiveconfig command:
zmarchiveconfig enable <user@example.com>Enabling Archive Forwarding to a Third-party Archiving Server
If the archive account is not maintained within Zimbra Collaboration, you do not need to set a password, COS, or other attributes.
Log on as zimbra, and use the zmarchiveconfig command:
zmarchiveconfig enable <account@example.com> \
archive-address account-archive@offsite.com \
archive-create falseSearching Across Mailboxes
When the archiving and discovery feature is installed, you can search across mailboxes either from the Administration Console or through the command line interface.
| You do not need to have any archive mailboxes configured to search across mailboxes, but the Archive package must be installed. |
You can assign a user to run the mailbox searches from the Administration Console by creating a delegated administrator with rights to access the mailbox search tool.
Cross Mailbox Search from the Administration Console
The discovery tool, Search Mail, is added to Tools and Migration on the Navigation pane when the archiving package is added. To set up a cross-mailbox search you configure the following information.
- Admin Console:
-
Home → Tools and Migration → Search Mail, from the Gear icon select New
-
Server name. The server name to be searched.
-
Target mailbox and folders. One target mailbox and folder are created automatically. You can use this mailbox for all your search results and create new folders for each search, or you can create a new target mailbox for each separate search.
A target mailbox is like any other mailbox and can have any features or preferences that are defined by the COS or by account. Target mailboxes are listed in the Administration Console Accounts list. You might want to give the target mailboxes account names that identify them as target mailboxes for cross-mailbox searches and configure a COS specific for target mailboxes to be able to manage access.
-
Limit the number of messages returned by the search. The default is 500 results.
-
You can select to send an email notification when the search is completed. The email notification includes the search task ID and status on the subject line and you can specify the type of information to include in the message, such as the number of messages found, the list of addresses resulting from the search and the search query used.
-
Select which mailboxes to search. When you check Select accounts to search, you select which account addresses to search.
-
Create the search query. You can search outgoing and incoming email by date, from, to, cc, subject, keywords, and attachments. Advanced can be used to quickly create a query to search by name, dates and time ranges, distribution list, aliases.
When searching archive messages, you can search by the envelope address using the envfrom and envto query language extensions.
-
As the search runs, the Search Mailbox Content pane lists the search and the status. Click Refresh to update this page.
Delete the search task when it is completed because it occupies server memory. When the server is restarted, past searches are deleted.
When you use the discovery feature in the Administration Console, the tool makes copies of messages in the target mailbox you create. The messages occupy server space, increasing the size of your server. You might want to delete these messages from the target mailbox when they are no longer needed.
Legal Requests for Information
The Legal Intercept feature makes copies of email messages sent, received, or saved as drafts from targeted accounts and sends these messages to a designated “shadow” email address.
Legal Intercept can be configured to send the complete content of the message or to send only the header information. When a targeted account sends, receives, or saves a draft message, an intercept message is automatically created to forward copies of the messages as attachments to the specified email address.
Legal Intercept Settings
The Legal Intercept feature can be configured either for a Class of Service or an individual account.
The feature is configured from the CLI, using zmprov.
The only required configuration to set up Legal Intercept is to enable the feature — zimbraInterceptAddress — on target accounts or COS.
You can enable the attribute zimbraInterceptSendHeadersOnly to send only the header information of the email message instead of sending the complete message.
Setting Up Legal Intercept
Specify the intercept address to receive intercepted messages.
-
If enabling intercept by COS:
zmprov mc <cosname> zimbraInterceptAddress <account@intercept.example.com> -
If enabling Intercept for an account:
zmprov ma <accountname@example.com> zimbraInterceptAddress <account@intercept.example.com>
If you are going to use the default intercept message template and From address (postmaster@<yourdomain.com>`), a Legal Intercept is set up.
Setting Up Legal Intercept to Forward the Message Header
To forward the header information, instead of the complete message for an account:
zmprov ma <accountname@example.com> zimbraInterceptSendHeadersOnly TRUEModifying the Intercept Cover Email Message
An email message is automatically created to forward copies of the intercepted messages as attachments. The default message includes:
-
From address is “postmaster@<yourdomain.com>”
-
Subject line “Intercept message for <account@yourdomain.com> <interceptedmessage subject>”
-
Message “Intercept message for <account@yourdomain.com>.
Operation=<type of message>, folder=<foldername>, folder ID=<#>”.
The cover email message can be modified. Use the following parameters to modify the email message.
ACCOUNT_DOMAIN |
Domain of the account being intercepted. |
ACCOUNT_ADDRESS |
Address being intercepted |
MESSAGE_SUBJECT |
Subject of the message being intercepted. |
OPERATION |
Operation that the user is performing, “add message”, “send message”, or “save draft”. |
FOLDER_NAME |
Name of the folder to which the message was saved. |
FOLDER_ID |
ID of the folder to which the message was saved. |
NEWLINE |
Used for formatting multi-line message bodies. |
Use steps in this section to change the from-name, the subject line, or text in the message body:
-
To change the From name:
zmprov ma <accountname@example.com> zimbraInterceptFrom '<newname@example.com>' -
To change the text of the Subject line:
zmprov ma <accountname@example.com> zimbraInterceptSubject \ '<Intercepted message subject text> parameter <text> parameter' -
To change the text in the message body:
zmprov ma <accountname@example.com> zimbraInterceptBody \ '<Intercepted message text> parameter <text> parameter'
To modify by COS, type zmprov mc {cosname} ….
|
Creating Mailbox Snapshots for Legal Discovery
You can create a query for the user’s mailbox using the REST URL format to search for specific types of email messages and attachments and have these messages zipped and saved to your computer.
This zip file can be forwarded to a requesting law enforcement agency.
The email message appears as an .eml file name after the subject line.
The attachments get saved in the format that they were delivered.
Creating a Mailbox Snapshot zip File
You must be logged into the Zimbra Administration Console to create the zip file. You create a query for one account at a time.
-
In the Administration Console address field of the browser, after the port number 7071/, type:
home/<username>?fmt=zip&query=<searchquerystring>For example:
In the above example, the search query is requesting a
zipfile of all accounts calleduser1.You can use any search operators supported for searching in Zimbra. For example, you can search by folder (
in:folder_name), by sender’s name (from:<someone>), and you can use multiple search terms. See the Search Tips wiki page for keyword examples, https://wiki.zimbra.com/wiki/Search_Tips. -
Press Enter or the arrow to create the zip. A Confirm box displays, asking if you want to navigate away from this page.
-
Click OK.
-
Choose where you want to save the
zipfile. Thiszipfile is ready to be delivered.
Color and Logo Management
You can change the logo and base colors of the Zimbra Classic Web App themes without having to customize individual Zimbra Collaboration themes. This can be done from the administration console or the CLI.
Changing Theme Color and Logos on the Zimbra Classic Web App
| This sections deals with customizations related to Classic Web App. For customizations related to the Modern Web App, refer to Customizing Modern Web App |
Base colors for themes, and custom logos can be configured as a global setting or as a domain setting.
-
When the global settings are changed, the changes apply to themes on all servers.
-
When the domain settings are changed, the base color and logos for themes on the domain are changed.
If global settings and domain-level settings for theme base colors or logos are not identical, the domain values are displayed for the domain.
| If the logo and base colors are customized in multi-domain Zimbra Collaboration environments, you must set a virtual host as the base color: logo attributes are displayed based on the Host header sent by the browser. |
| Various themes are included with Zimbra Collaboration. Some of these themes - such as lemongrass, Hot Rod, and Waves - have been designed with graphics or color codes that do not change when you modify the base color. You might want to disable those themes from user’s Theme preferences selection. |
Customizing Base Theme Colors
The following base colors in Zimbra Classic Web App themes can be changed:
-
The primary background color displayed in the client. This color is the background of the page. Variants of the color are used for buttons, background color of the Content and panes, tabs, and selection highlight. In the following image, the background color displays with the logo, the variant of the background color displays in the login area.
-
The secondary color is the color used for the toolbar.
-
The selection color is the color displayed for a selected item such as a message or an item in the Overview pane.
-
The foreground color is the text color displayed. The default text color is black. The text color usually does not need to be changed.
Replacing the Classic Web App Logo
You can replace the logo with your company’s logo globally or per domain.
Graphics to Replace
The following logo files can be changed. Your logos must be the same size as specified here or the image might not display correctly. These graphic files can be saved on another server or in a directory that is not overwritten when Zimbra Collaboration is upgraded.
-
Company logo that displays on the login and splash screens for Zimbra Classic Web App and the Zimbra Collaboration administration console. The dimension of the graphic must be exactly 300 x 30.
-
Small company logo in the upper-left of the Zimbra Classic Web App application and the administration console. The dimension of the graphic must be exactly 170 x 35.
-
Company Web address that links from the company logos.
Graphics not replaced
The icon that displays in the Advanced search toolbar and the favicon.ico that displays in the URL browser address field cannot be changed at this time.
Using the Admin Console to Modify Theme Colors and Logo
On the administration console, the Global Settings and the Domains settings include a Themes page that can be configured to customize the color scheme and to add a company logo and logo URL. You upload your company logo to be used on the Zimbra Classic Web App and administration console pages.
Changing Base Theme Colors
You can either select colors from popup view of predefined colors, or enter the six-digit hexadecimal color value for an exact color match to set theme colors for the following categories:
-
Foreground, which is the text color.
-
Background, which is the primary background color displayed in the client.
-
Secondary, which is the color used for the toolbar and selection headers in the pane.
-
Selection, which is the color displayed for a selected item such as a message, right-click, or drop down menu selection.
| Changes to theme settings require the server theme cache to be flushed. To flush a server, go to Home → Configure → Servers to get the list of servers. Right-click on a server and select Flush Cache from the popup menu. |
Use the Customize the theme colors container to set colors for your theme categories:
- Admin Console:
-
Home → Configure → Global Settings → Themes or
Home → Configure → Domains → domain → Themes-
Click on the field alongside the theme category to be modified, then use the popup color selector to define the color for your selection.
You can either click directly on a color, or use the entry field to write the hexadecimal value of the color. In either case, your selection will be displayed in the field. If you opt out of your color selections, click reset all theme colors to discard your settings.
-
Navigating away from this page results in query for save of the settings.
Click Yes (to save) or No (to discard your settings).
-
Adding Your Logo
You can replace the Zimbra Collaboration logo with your company’s logo globally or per domain from the appropriate Themes page. Your logos must be the same size as specified in the Graphics to Replace section or the images might not display correctly. The graphic files are saved on another server or in a directory that is not overwritten when Zimbra Collaboration is upgraded.
| When you configure the Customize the logo of the themes section in the Global Settings → Theme page, all fields in this section must be completed to display the graphics correctly. |
The Zimlet icon that displays in the Advanced search toolbar and the favicon.ico that displays in the URL browser address field are not changed.
Use the Customize the logo of the themes container to a logo to accompany the theme:
- Admin Console:
-
Home → Configure → Global Settings → Themes or
Home → Configure → Domains → domain → Themes
| Option | Description |
|---|---|
Logo URL of the themes |
The company web address to be linked from the logo. |
Application logo banner URL of the themes |
The company logo that displays on the login and splash screens for the Zimbra Classic Web App and admin console. the dimension of the graphic must be exactly 450x100. |
Application logo banner preview (200x35) |
The company logo in the upper-left of the Zimbra Classic Web App application and the administration console. the dimension of the graphics must be exactly 120x35. |
Login logo banner URL of the themes |
|
Login logo banner preview (440x60) |
Using the CLI to Change Theme Colors and Logo
To change the Zimbra Classic Web App theme base colors and logos, use the zmprov command. The following attributes are configured either as a global config setting or as a domain settings. Color values are entered as a six-digit hexadecimal codes.
| Attribute | Description |
|---|---|
|
The hex color value for the primary background color displayed in the client. |
|
The hex color value for the toolbar and selected tabs. |
|
The hex color value for the color of the selected item. |
|
The hex color value for the text. This usually does not need to be changed as the default is black. |
Changing base colors for themes
Before you begin, identify the six-digit hexadecimal base color values for the various elements you are changing. You will be using these in your command entries.
zmprov modifyConfig <attribute-name> [“#HEX_6digit_colorcode”]zmprov modifyDomain <domain> <attribute-name> [“#HEX_6digit_colorcode”]Modifying a domain
The example in this section demonstrates how to change to the following base colors:
-
Background color = Coral, #FF7F50
-
Secondary color = turquoise, #ADEAEA
-
Selection color = yellow, #FFFF00
-
Specify the skin colors: Log in as the
zimbrauser and usezmprovto modify the domain:zmprov modifyDomain example.com \ zimbraSkinBackgroundColor "#FF7F50" \ zimbraSkinSecondaryColor "#ADEAEA" \ zimbraSkinSelectionColor "#FFFF00"The quote marks,
"", are required so the use of the#sign does not comment out the text that follows. -
Use the zmmailboxdctl command to apply the changes by restarting the mailbox server process:
zmmailboxdctl restart
Reload the Classic Web App, and Zimbra Collaboration themes for that domain should now display these colors.
-
Adding Your Logos
You add the company logo information and URL by modifying these the following attributes for logos:
| Attribute | Description |
|---|---|
|
The company Web address that you want linked from the logo. |
|
The company logo file name that is displayed on the login and splash screens for the Classic Web App and the Zimbra Collaboration administration console. |
|
The logo graphic file name for the graphic in the upper-left of the Classic Web App application and the administration console. |
To add logos for a domain
If logo files are saved in the Zimbra Collaboration server, they must be
in a subdirectory of /opt/zimbra/jetty/webapps/zimbra.
If the logos are hosted on another machine, enter the full URL when identifying the logo.
Use steps in this section to update the logo(s) displayed over a domain:
-
Change the URL link:
zmprov modifyDomain example.com zimbraSkinLogoURL https://url.example.com/
-
Modify the logo display:
To change the logo displayed in the login and splash screens:
mkdir /opt/zimbra/jetty/webapps/zimbra/logos/
Upload your logos to that new folder and change the files privileges to Zimbra. Then specify the path after the
/opt/zimbra/jetty/webapps/zimbrazmprov modifyDomain example.com zimbraSkinLogoLoginBanner /logos/loginlogo.png
To change the logo displayed on the Zimbra Classic Web App main page:
zmprov modifyDomain example.com zimbraSkinLogoAppBanner /logos/applogo.png
-
Stop/start the server:
zmmailboxdctl restart
| Not currently supported: Logo modification for the Zimbra Classic Web App. |
Customizing Modern Web App
This section is applicable only for Modern Web App.
In this section, we guide you through customizing Modern Web App and deploying your customization. We’re going to address customization by overriding dynamic layouts.
| Review your organization’s branding guidelines for icons and colors to use in the Zimbra’s Modern Web App. |
What can be customized
As a general rule, you can customize the following within the branding framework:
-
Logos
-
Color and border of various widgets such as Buttons, links, and Tabs
-
Text fonts, colors, and sizes
-
The basic appearance of the Modern Web App
What cannot be customized
There are several sections of the Modern Web App user interface that require a significant amount of Javascript coding to change. Customizing these segments is beyond the scope of this document:
-
Changing the behavior of something (e.g., a button)
-
Order of application tabs
-
Order of toolbar buttons
-
Adding new toolbar buttons
-
Adding search locations to the Search toolbar
Setup
Before we start customizing the Modern Web App, we need to create an empty Modern Web App bundle.
You should also have the following knowledge and skillsets:
-
Familiarity with usage of linux terminal and commands
-
Familiarity with basic HTML and CSS concepts and associated terminologies
-
Familiarity with terms like font, font size, and line-height
-
Familiarity with logos, images, color codes, and other styling elements
-
Familiarity with your organization’s branding guidelines
Creating an Empty Bundle
We first create an empty folder and its contents locally. Once done, we copy the folder to the Zimbra server.
Folder Name
Naming the folder is a crucial first step.
-
Keeping the folder name same as the hostname, the customizations reflect on all domains and, by extension, all the accounts on those domains.
-
If the folder name is the same as the domain name, the customizations appear on all accounts on that domain.
-
In case there is a virtual host setup, the folder name must be the domain name on which you have configured the virtual host.
For Example, consider a domain named
example.comthat has a virtual hostmail.example.com; in such a case, you must create a folder mail.example.com.- Finding hostname
-
-
Log in using
sshto your Zimbra server. -
Switch to user
zimbra.su - zimbra
-
Run this command to get the hostname.
zmhostname
-
- Finding Domain Name
-
-
Log in using
sshto your Zimbra server. -
Switch to user
zimbra.su - zimbra
-
Run this command to get the domain name(s).
zmprov gad
-
For this document, we consider mail.example.com as the folder name.
Folder contents
The folder (mail.example.com in our case) must have the following hierarchy and contents.
Use mkdir to create new directories and touch to create new files.
|
mail.example.com
├── config.json
├── index.css
├── palette.css
├── assets
│ ├── favicon.ico
│ ├── icon.png
│ ├── icon.svg
│ ├── login-page-background.png
│ └── logo.svg
└── pwa
├── manifest.json
└── icons
├── icon_300x300.svg
├── ios
│ ├── icon_16x16.png
│ ├── icon_32x32.png
│ ├── icon_57x57.png
│ ├── icon_72x72.png
│ ├── icon_114x114.png
│ └── icon_180x180.png
└── non-ios
├── icon_16x16.png
├── icon_32x32.png
├── icon_36x36.png
├── icon_48x48.png
├── icon_72x72.png
├── icon_96x96.png
├── icon_144x144.png
├── icon_150x150.png
├── icon_192x192.png
├── icon_256x256.png
└── icon_512x512.png
Customize Logos
The Zimbra’s Modern Web App uses the primary logo of your organization unless you specify a secondary logo.
-
Save the primary logo as
logo.svg. -
Save the secondary logo as
secondarylogo.svg.
Along with the logo, you also need your organization’s emblem to use it as an icon.
Create multiple icons — of different sizes — using this emblem. Refer to the below table for the file name, size, and destination of each icon.
| Icon File name | Icon Size (in px) | Destination Folder |
|---|---|---|
|
48x48 |
|
|
512x512 |
|
|
NA |
|
|
NA |
|
|
NA |
|
|
16x16x |
|
|
32x32x |
|
|
57x57 |
|
|
72x72 |
|
|
114x114 |
|
|
180x180 |
|
|
16x16x |
|
|
32x32x |
|
|
36x36 |
|
|
48x48 |
|
|
72x72 |
|
|
96x96 |
|
|
144x144 |
|
|
150x150 |
|
|
192x192 |
|
|
256x256 |
|
|
512x512 |
|
Customizable Segments
Consider the below Zimbra’s Modern Web App screenshot.
This labeled screenshot shows the customizable segments of Modern Web App.
-
Title
-
Navigation bar containing the links
-
Left-side links on the navigation bar
-
Right-side links on the navigation bar
-
Left Sidebar
-
Right Sidebar
-
Header
The items marked 1, 2, 3, and 4 are text and links. Instructions to change them are in the section Customize Text & Links.
The colors for items marked 5, 6, and 7 are customizable. Instructions to change these, and other colors, are in Customize Colors & Sizes.
Customize Text & Links
-
Copy and paste Sample config.json in
mail.example.com/config.json -
To change the title text ( marked 1 in Customizable components) edit the value against
"title"in Sample config.json. -
To replace the text Zimbra with your organization’s name (
"Example"in this case) throughout the application, change the value against`"clientName"` in Sample config.json. -
To hide and remove the Forgot Password link, set
"disableForgotPassword"as"true"in Sample config.json. -
To insert links and hypertext in the navigation bar (2) edit
"left"(3) and"right"(4) under"nav"in Sample config.json.-
To remove the navigation bar altogether remove the below snippet:
-
"nav":
{
.
.
.
}
{
"title": "Example Mail",
"version": "1",
"clientName": "Example",
"userHelpPath": "https://www.example.com/userguide/",
"nav": {
"left": [
{
"name": "Example Link 1",
"href": "https://www.example.com/1"
},
{
"name": "Example Link 2",
"href": "https://www.example.com/2"
}
],
"right": [
{
"name": "Example Link 1",
"href": "https://www.example.com/1"
},
{
"name": "Example Link 2",
"href": "https://www.example.com/2"
}
]
}
}Customize Colors & Sizes
This section handles colors and sizes of fonts, logos, and sidebars — among other things.
Palette.css
This file helps you to create a palette of colors to use throughout the application.
-
Navigate to palette generator and enter the hex code for Primary, Secondary and Tertiary colors.
-
Specify hex code for colors associated with Success, Informative, Warning, and Danger messages.
-
Click Generate.
-
A ready styling template with color codes appears.
-
Click Copy.
-
Paste the contents generated in
mail.example.com/palette.css.
Index.css
Copy the below segment and paste as is in the mail.example.com/index.css file.
Change the values to change various aspects of the Modern Web App as it appears to the user.
:root {
--sidebar-bg-color: var(--gray-lightest);
--rightbar-bg-color: var(--gray-lightest);
--line-height-base: 1.42857143;
--link-color: var(--brand-primary-500);
--link-hover-color: var(--brand-primary-800);
--link-hover-decoration: underline;
--logo-height: 32px;
--logo-max-width: 200px;
--header-bg: var(--gray-lightest);
--header-fg: var(--gray-darker);
--external-header-bg: var(--brand-tertiary-700);
--external-header-fg: #FFFFFF;
}The various variable names used are self-explanatory. However, the below table offers a brief description. The number against some of the variables refer to the figure Customizable components.
| Parameters | Description |
|---|---|
|
Changes the background color of the pane that lists email and contact folders. |
|
Change the background color of the right sidebar. |
|
Change the base line-height that changes the line-height everywhere in the application. |
|
Change the link color. |
|
Change the link color on mouse hover. |
|
Change the way link behaves (underline, overline, or strikethrough) when mouse hovers. |
|
Change the logo height. This value cannot be more than 72px. |
|
Change the maximum width of the logo. |
|
Change the header background color. |
|
Change header’s text color. |
|
Change the navigation bar’s background color. |
|
Change the navigation bar’s text color. |
Make all color customizations (overrides) in index.css and not in palette.css to avoid palette overwrites.
|
Customizing the PWA
This section helps customize certain aspects of Progressive Web App (PWA). For more information on PWAs, refer What is a Progressive Web App.
{
"icons": [
{
"src": "/pwa/icons/icon_300x300.svg",
"sizes": "300x300",
"type": "image/svg+xml"
},
{
"src": "/pwa/icons/non-ios/icon_512x512.png",
"sizes": "512x512",
"type": "image/png"
},
{
"src": "/pwa/icons/non-ios/icon_256x256.png",
"sizes": "256x256",
"type": "image/png"
},
{
"src": "/pwa/icons/non-ios/icon_192x192.png",
"sizes": "192x192",
"type": "image/png"
},
{
"src": "/pwa/icons/non-ios/icon_150x150.png",
"sizes": "150x150",
"type": "image/png"
},
{
"src": "/pwa/icons/non-ios/icon_144x144.png",
"sizes": "144x144",
"type": "image/png"
},
{
"src": "/pwa/icons/non-ios/icon_96x96.png",
"sizes": "96x96",
"type": "image/png"
},
{
"src": "/pwa/icons/non-ios/icon_72x72.png",
"sizes": "72x72",
"type": "image/png"
},
{
"src": "/pwa/icons/non-ios/icon_48x48.png",
"sizes": "48x48",
"type": "image/png"
},
{
"src": "/pwa/icons/non-ios/icon_36x36.png",
"sizes": "36x36",
"type": "image/png"
},
{
"src": "/pwa/icons/non-ios/icon_32x32.png",
"sizes": "32x32",
"type": "image/png"
},
{
"src": "/pwa/icons/non-ios/icon_16x16.png",
"sizes": "16x16",
"type": "image/png"
},
{
"src": "/pwa/icons/ios/icon_180x180.png",
"sizes": "180x180",
"type": "image/png"
},
{
"src": "/pwa/icons/ios/icon_114x114.png",
"sizes": "114x114",
"type": "image/png"
},
{
"src": "/pwa/icons/ios/icon_72x72.png",
"sizes": "72x72",
"type": "image/png"
},
{
"src": "/pwa/icons/ios/icon_57x57.png",
"sizes": "57x57",
"type": "image/png"
},
{
"src": "/pwa/icons/ios/icon_32x32.png",
"sizes": "32x32",
"type": "image/png"
},
{
"src": "/pwa/icons/ios/icon_16x16.png",
"sizes": "16x16",
"type": "image/png"
}
],
"name": "Example Mail",
"short_name": "Example Mail",
"orientation": "portrait",
"display": "standalone",
"start_url": "/",
"background_color": "#ffffff",
"theme_color": "#e92d28"
}-
Copy and paste Sample manifest.json in
mail.example.com/pwa/manifest.json. -
Edit all instances of
mail.example.comto the folder name as decided in the section Folder Name. -
Edit
"name"and"short_name"to have the same value as"title"from Sample config.json.-
"name"represents the name of the web application as it appears to users in list of mobile applications. -
"short_name"represents the name of the web application as it appears to users if there is not enough space to display"name".
-
-
Set the
"background_color"tobackground-colorin Palette.css. -
Set the
"theme_color"to the same value as primary color in Palette.css.
Do not change the values of "orientation", "display" and "start_url".
|
Customizing the Login Page
This section helps you change the way Zimbra Modern Web App login page appears to users.
Before you begin login (or ssh) on the Zimbra server.
Changing the Background Image
-
Copy a background image to
/opt/zimbra/jetty_base/webapps/zimbra/img/
-
Open and edit
/opt/zimbra/jetty_base/webapps/zimbra/skins/_base/base3/skin.properties
-
Locate the entry
LoginScreen. -
Replace
new-back-ground-image.pngwith the file name of the image you just copied.
Changing the Logo
The Modern Web App references the logo it uses from :
/opt/zimbra/jetty_base/webapps/zimbra/img/new-logo.png
You have to overwrite this file with the logo you prefer to use.
To keep provisions for reverting to the default logo, rename the above file (add .old to the filename).
|
-
Rename your organization’s logo that you have as
new-logo.png. -
Copy this file to :
/opt/zimbra/jetty_base/webapps/zimbra/img/
Deployment Instructions
-
Navigate to and open the
mail.example.comfolder. -
Edit
config.jsonto change theversion. Do not use a previously used value.-
Enter a unique positive number.
-
Use a new value every time for your customizations to reflect on users' Modern Web App.
-
Enclose the text in quotes.
-
-
Save the file.
All instances of mail.example.comshould be replaced with the folder name as decided in the section Folder Name. -
Copy
mail.example.comto/opt/zimbra/jetty/webapps/zimbra/modern/clients/on Zimbra server.
Restart Zimbra mailbox server
To apply the changes you have made, restart Zimbra’s mailbox server.
-
Login to your Zimbra installation as
root. -
Switch to user
zimbra.su - zimbra
-
Restart Zimbra’s mailbox server.
zmmailboxdctl restart
-
Refresh Zimbra’s Modern Web App login page to see the changes
| You might need to clear the cache if the changes do not appear. |
Storage Management
Storage Management (SM) feature is where you configure storage volumes for primary, secondary data stores and indexing. SM supports local and external storage for the following providers (Amazon S3, Ceph, EMC, Netapp StorageGrid, Scality, OpenIO). SM through the scheduler also provides the ability to move older data from primary higher cost to secondary lower cost storage based on age at the scheduled time. In most instances, end users will not experience any performance differences when accessing the data stored on external storage.
Storage Management can be managed within the Administrator UI within the global and server level or from the command line.
Unified Storage
From Daffodil 10.0.5 Patch onwards, support for Unified Storage has been added in the Storage Management module.
Unified Storage is designed to streamline data management by consolidating data from multiple mailbox servers under the same directory structure within a single S3 bucket. This approach simplifies storage, enhances accessibility, and reduces operational complexity.
Unified Storage feature is suitable for you if:
-
Your environment is a multi-server environment with more than 1 mailbox server.
-
Your organization has substantial data storage and access needs benefit from the centralized, scalable approach.
Structure
In the following example, the mailbox server’s - Mailbox-1, Mailbox-2, Mailbox-3 use the same bucket on the external storage. The users - d8bd3037-38d0-4c45-ade4-a6866f2912bd, 91fee523-4841-400f-9dc9-0d1e41f4c61b, and a8bd3037-4841-400f-ade4-bf1e41f4c61h use the same directory structure irrespective of on which Mailbox server the account is hosted.
|-- Mailbox-1
|-- Mailbox-2
|-- Mailbox-3
\
|-- /BucketName/DestinationPath/Prefix/
\
|-- d8bd3037-38d0-4c45-ade4-a6866f2912bd
\
|-- D3S78JHDD8BD303738D04C45ADE4A6866F2912BD000001BD
|-- AD87H7YD8BD303738D04C45ADE4A6866F2912BD000001BD
|-- 91fee523-4841-400f-9dc9-0d1e41f4c61b
\
|-- 5D5D494CD8BD303738D04C45ADE4A6866F2912BD000001BD
|-- 2BF41B87D8BD303738D04C45ADE4A6866F2912BD000001BD
|-- 1CC67854D8BD303738D04C45ADE4A6866F2912BD000001BD
|-- 90AA2503D8BD303738D04C45ADE4A6866F2912BD000001BD
|-- 73AC6101D8BD303738D04C45ADE4A6866F2912BD000001BD
|-- a8bd3037-4841-400f-ade4-bf1e41f4c61h
\
|-- F3545DA7D8BD303738D04C45ADE4A6866F2912BD000001BD
|-- DB88EE7BD8BD303738D04C45ADE4A6866F2912BD000001BD
|-- 4CC67854D8BD303738D04C45ADE4A6866F2912BD000001BD
|-- 2D5D494CD8BD303738D04C45ADE4A6866F2912BD000001BD
|-- 1D5D494CD8BD303738D04C45ADE4A6866F2912BD000001BD
|-- 3CC67854D8BD303738D04C45ADE4A6866F2912BD000001BDAdvantages of using Unified Storage
Following are some of the advantages of using Unified Storage:
-
Mailbox movement: Since the data from multiple mailbox servers are stored under a single S3 bucket, it becomes easier to move user’s mailboxes from one server to another without moving the data stored in S3.
-
Simplified Data Management: Unified Storage eliminates the need to manage multiple storage locations for mailbox servers. All data is consolidated into a single S3 bucket, making it easier to manage, and maintain.
-
Scalability: The unified approach allows for easier scaling as the organization grows, reducing the complexity of data expansion.
Limitations of using Unified Storage
-
Support only S3 providers: Unified Storage is only supported on S3 providers.
-
Message duplication: Message duplication is lost and is not supported when data is moved to external S3.
How to setup Unified Storage
The Unified Storage based volume can be created through Administrator UI or CLI.
To optimize the utilization of the feature, when creating an external volume with S3, it is essential to ensure that the same volume path (same volumePrefix) is consistently set across all mailbox servers.
Administrator UI
When creating volumes through Home → Configure → Server → Storage Management → Manage Volumes → Add, select Unified Storage checkbox which will enable Unified Storage feature.
Please refer to External Storage Type section for detailed steps on creating volumes through Administrator UI.
CLI
An option --unified or -un can be used with zmvolume command to enable Unified Storage feature.
Please refer to External volume for S3 section for detailed steps on creating S3 volumes through CLI
Volume Management
On a server’s Storage management page you can manage storage volumes on each Zimbra Mailbox server:
Home → Configure → Server → Storage ManagementWhen Zimbra Collaboration Server is installed, one index volume and one message volume are configured on each mailbox server.
-
The Index volume is /opt/zimbra/index
-
The Message volume is /opt/zimbra/store
Within the Storage Management location, you can add new volumes, set the volume type, and set the compression threshold.
Index Volume
Each Zimbra mailbox server is configured with one current index volume. Each mailbox is assigned to a permanent directory on the current index volume. When an account is created, the current index volume is automatically defined for the account. You cannot change which index volume the account is assigned.
As volumes become full, you can create a new current index volume for new accounts. You can add new volumes, set the volume type, and set the compression threshold.
Index volumes not marked current are still actively in use for the accounts assigned to them. Any index volume that is referenced by a mailbox as its index volume cannot be deleted.
Message Volume
When a new message is delivered or created, the message is saved in the current message volume. Message volumes can be created, but only one is configured as the current volume where new messages are stored. When the volume is full, you can configure a new current message volume. The current message volume receives all new messages. New messages are never stored in the previous volume.
A current volume cannot be deleted, and message volumes that have messages referencing the volume cannot be deleted.
Admin Console: Storage Management Page
The Storage Management page contains five sections:
-
Manage Volumes section shows all configured and allows the Admin the ability to create, edit and delete volumes.
-
Volume Name is the name that is assigned to each volume. The initial volumes are named index1 and message1.
-
Volume Root Path is the location in the file system where volume data is stored.
-
Volume Type defines the type of volume that was set when the volume was created. It can be set to index, primary or secondary and once set, it can not be changed.
-
Compress Blobs When this box is checked, message blobs whose size is above the compression threshold are compressed. If blob compression is turned on, the disk space used is decreased. Note: Turning on blob compression also increases memory requirements for the server.
-
Compression Threshold. Messages larger than the threshold are compressed. The default threshold is 4096 bytes.
-
Current defines which volume is currently set to default with a check mark.
-
-
Assign Current Volumes section is the location where you will set which volume will be currently used for primary message, secondary message, or index volume’s.
-
Current primary message volume The current primary volume name. New messages are saved in this current message volume.
-
Current secondary message volume The current secondary message volume name. Older data is stored on the secondary message volume.
-
Current index volume. The current index volume name. As volumes become full, you can create a new current index volume for new accounts
-
-
Storage Management Policies Section:
-
SM Session Scheduling gives the Admin the ability to enable and schedule when the SM policy will occur on a daily bases.
-
Manage SM Session gives the Admin the ability to manually execute the Storage Management policies.
-
-
Item to Move section defines the SM policies used to manage when data is migrated from the primary to secondary store. SM policies can be set at the global or on each mailbox server.
-
Types of items to move. You can select messages, tasks, appointments, contacts, and briefcase items to move from a primary volume to the current secondary volume.
-
| If you are using an external storage provider for Secondary storage, please exclude the Documents from the policy as it appears garbled after it is moved to external storage. |
-
Move items older than. The default global SM policy is to move messages and files more than 30 days old to the secondary volume. The age of items to be moved can be specified by a number of days, months, weeks, hours, or minutes.
-
Policy String. You can use the search query language to set up other SM policies. For example, if you wanted all messages marked as junk to be included in messages moved to the current secondary volume, you would add the following to the policy: message:in:junk before:-[x] days.
Types Of Volumes
Zimbra provides two types of volume that can be configured and linked for data storage.
-
Internal
-
External
Internal Storage Type
Internal Storage Type is the store located on the zimbra Servers.
For adding the Internal storage volume follow the below steps:
-
Go to Home → Configure → Server → Storage Management
-
Scroll to Manage Volumes, then click on Add button.
-
Select Volume as Internal. Click Next.
-
Select the appropriate volume type i.e. Primary, Secondary, or Index.
-
Enter the volume name and volume root path.
-
If you want to compress blobs, check Compress Blobs and set the Compression Threshold.
-
Use custom store manager is the optional field. Do not click on Enable checkbox if you want to use the default zimbra store manager.
-
Compress Blobs: When this box is checked, message blobs whose size is above the compression threshold is compressed. If blob compression is turned on, the disk space used is decreased.
Turning on blob compression will increase the memory requirements for the Servers. -
Compression Threshold: Messages that exceed the defined threshold are compressed. The default threshold is 4096 bytes.
-
Click Finish.
External Storage Type
External storage type is storage that is accessible locally but which is hosted externally from the mailbox server. Currently Zimbra supports the following providers:
-
Amazon S3.
-
Ceph.
-
Custom S3 - Option to create any unsupported external storage.
-
EMC.
-
NetApp StorageGrid.
-
OpenIO.
-
Scality.
Amazon S3
Following are the steps to add the Amazon S3 Storage:
-
Go to Home → Configure → Servers.
-
Select the server, right-click and select Edit.
-
Go to Storage Management → Manage Volumes page and click on Add button.
-
Select provider Amazon S3. Click Next.
-
Select the Volume Type. i.e. Primary or Secondary.
There is no support for the Index volume on External Stores. -
Enter the Volume Name, Volume Prefix.
-
For add an S3 compatible bucket. Click on Create a new bucket.
-
Enter the Bucket name, Access key, Secret, Destination path and URL
AWS services are accessed using the Access Key Id and Secret Key. These are available through the AWS Management Console. -
Select the appropriate Region and click Next.
All the above fields must be filled correctly to validate the bucket. The Next button will be disabled till all the credentials are entered correctly. The bucket credentials will be validated after cliking the Next button. An error will be displayed in case any errors encountered with the credentials. -
The bucket will be created once it is validated successfully.
-
-
Select the created bucket from the S3 compatible bucket dropdown.
-
Use custom store manager is the optional field. Do not click on Enable checkbox if you want to use the default zimbra store manager.
-
Select the checkbox to enable the Infrequent access. Enter the threshold for infrequent access. Optionally you can select the checkbox to enable the Intelligent tiering.
Infrequent Access: S3 Standard-IA is for data accessed less frequently but requires rapid access when needed.
Infrequent Access Threshold: The threshold is used to set any file larger than the Infrequent Access Threshold value for this storage class.
Intelligent Tiering: This will set the appropriate Intelligent Tiering flag on all files of the volume.
The official Amazon S3 documentation on Infrequent Access and Intelligent Tiering. To enable Unified Storage support on this volume, select the Unified Storage checkbox. -
Click Finish to add the Amazon S3 storage type.
NOTE:
Ceph
Following are the steps to add the Ceph Storage:
-
Go to Home → Configure → Servers.
-
Select the server, right-click and select Edit.
-
Go to Storage Management → Manage Volumes page and click on Add button.
-
Select provider Ceph. Click Next.
-
Select the Volume Type. i.e. Primary or Secondary
-
Enter the Volume Name, Volume Prefix.
-
For add an S3 compatible bucket. Click on Create a new bucket.
-
Enter the Bucket name, Access key, Secret, Destination path and URL
-
Click Next.
-
The bucket will be created once it is validated successfully.
-
-
Select the created bucket from the S3 compatible bucket dropdown.
-
Use custom store manager is the optional field. Do not click on Enable checkbox if you want to use the default zimbra store manager.
To enable Unified Storage support on this volume, select the Unified Storage checkbox. -
Click Finish to add the Ceph storage.
Custom S3
Following are the steps to add the Custom S3 Storage:
-
Go to Home → Configure → Servers.
-
Select the server, right-click and select Edit.
-
Go to Storage Management → Manage Volumes page and click on Add button.
-
Select provider Custom S3. Click Next.
-
Select the Volume Type. i.e. Primary or Secondary
-
Enter the Volume Name, Volume Prefix.
-
For add an S3 compatible bucket. Click on Create a new bucket.
-
Enter the Bucket name, Access key, Secret, Destination path and URL
-
Click Next.
-
The bucket will be created once it is validated successfully.
-
-
Select the created bucket from the S3 compatible bucket dropdown.
-
Use custom store manager is the optional field. Do not click on Enable checkbox if you want to use the default zimbra store manager.
To enable Unified Storage support on this volume, select the Unified Storage checkbox. -
Click Finish to add the Custom S3 storage.
EMC
Following are the steps to add the EMC Storage:
-
Go to Home → Configure → Servers.
-
Select the server, right-click and select Edit.
-
Go to Storage Management → Manage Volumes page and click on Add button.
-
Select provider EMC. Click Next.
-
Select the Volume Type. i.e. Primary or Secondary
-
Enter the Volume Name, Volume Prefix.
-
For add an S3 compatible bucket. Click on Create a new bucket.
-
Enter the Bucket name, Access key, Secret, Destination path and URL
-
Click Next.
-
The bucket will be created once it is validated successfully.
-
-
Select the created bucket from the S3 compatible bucket dropdown.
-
Use custom store manager is the optional field. Do not click on Enable checkbox if you want to use the default zimbra store manager.
To enable Unified Storage support on this volume, select the Unified Storage checkbox. -
Click Finish to add the EMC storage.
NetApp StorageGrid
Following are the steps to add the NetApp StorageGrid:
-
Go to Home → Configure → Servers.
-
Select the server, right-click and select Edit.
-
Go to Storage Management → Manage Volumes page and click on Add button.
-
Select provider NetApp StorageGrid. Click Next.
-
Select the Volume Type. i.e. Primary or Secondary
-
Enter the Volume Name, Volume Prefix.
-
For add an S3 compatible bucket. Click on Create a new bucket.
-
Enter the Bucket name, Access key, Secret, Destination path and URL
-
Click Next.
-
The bucket will be created once it is validated successfully.
-
-
Select the cretaed bucket from the S3 compatible Bucket dropdown.
-
Use custom store manager is the optional field. Do not click on Enable checkbox if you want to use the default zimbra store manager.
To enable Unified Storage support on this volume, select the Unified Storage checkbox. -
Click Finish to add the NetApp StorageGrid storage.
OpenIO
| Unified Storage is not supported for OpenIO provider. |
Following are the steps to add the OpenIO storage:
-
Go to Home → Configure → Servers.
-
Select the server, right-click and select Edit.
-
Go to Storage Management → Manage Volumes page and click on Add button.
-
Select Volume Type as OpenIO. Click Next.
-
Select the Volume Type. i.e. Primary or Secondary
-
Enter the Volume Name, URL, Account, Namespace, Proxy Port and Account Port.
-
Use custom store manager is the optional field. Do not click on Enable checkbox if you want to use the default zimbra store manager.
-
Click Finish to add the OpenIO storage.
Scality
Following are the steps to add the Scality Storage:
-
Go to Home → Configure → Servers.
-
Select the server, right-click and select Edit.
-
Go to Storage Management → Manage Volumes page and click on Add button.
-
Select provider Scality. Click Next.
-
Select the Volume Type. i.e. Primary or Secondary
-
Enter the Volume Name, Volume Prefix.
-
For add an S3 compatible bucket. Click on Create a new bucket.
-
Enter the Bucket name, Access key, Secret, Destination path and URL
-
Click Next.
-
The bucket will be created once it is validated successfully.
-
-
Select the created bucket from the S3 compatible bucket dropdown.
-
Use custom store manager is the optional field. Do not click on Enable checkbox if you want to use the default zimbra store manager.
To enable Unified Storage support on this volume, select the Unified Storage checkbox. -
Click Finish to add the Scality storage.
How to Assign a Volume as a Secondary Volume
Before you can assign an SM volume, the volume must exist. Please refer to Adding a New Storage Volume to the Servers for an overview on adding volumes. Once the volume has been created, follow the below steps:
-
Go to Home → Configure → Server → Storage Management
-
Scroll to Assign Current Volumes section
-
Click the dropdown list for Current secondary message volume and select the appropriate volume.
-
Click Save.
-
The selected volume is now configured as the Secondary message volume.
After the new volume has been set to Secondary Message volume, messages will be moved to the secondary storage volume based on the SM policy.
Adding a New Storage Volume to the Servers
Each Zimbra mailbox Servers is configured with one primary message volume and an index volume. Refer to Volume Management section for more details. Additionally the Zimbra Data Store configuration allows the creation of new primary, secondary and index stores.
To access the volume page, follow the below steps.
-
Go to Home → Configure → Server → Storage Management
-
By default, the Index and Primary Data volumes are configured.
Storage Management Policies
Storage Management Policy is a process of moving older data to a secondary storage device. To manage your email storage resources, you can implement an SM policy that defines what items are moved and at what age they should be moved. Messages and attachments are moved from a primary volume to the current secondary volume based on the age of the message. The messages are still accessible. Users are not aware of any change and do not see any noticeable differences when opening older items that have been moved.
You can implement the SM policy globally or at the server level.
Home → Configure → Global Settings → Storage Management
Home → Configure → Sever → Storage ManagementThe policy configured within individual servers overrides the global policy.
The default global SM policy moves messages and briefcase files (over 30 days from the date of receipt) to the secondary volume. Also, you can move the tasks, appointments, contacts, and notes manually.
You can change the 30-day age policy to a specific age of months, weeks, hours, or minutes.
Setup or Editing SM Policies
Within the storage management window within the Global or Server level, scroll to Items to Move and edit or create a new rule by:
-
Selecting on the existing rule then clicking Edit or clicking Add.
-
Select or modify the policies you wish to assign.
-
Click Save
The following are the rules that can be configured when creating or editing a policy rule.
| Option | Description |
|---|---|
Types of items to move |
The default is to move messages briefcase files, but you can select other items |
Options |
If you want to include items in the junk and trash folder, check the box. |
Move items older than |
Select the time frame to move older items. |
Policy string |
This shows the policy string that you have configured. |
Delete the Existing Policy
Deleting an existing policy will remove the rule from future runs of SM Sessions.
-
To delete an existing policy, select the policy you want to delete.
-
Click the Delete button.
-
Select Yes.
If a rule was accidentally deleted, recreating the rule will be applied to all data within the define configuration at the next SM session. If an SM session is initiated manually, please be aware there could be higher server and IO load.
Storage Management CLI Utilities
Manage Global S3 Configurations using zms3config CLI
The zms3config is the CLI utility to manage the Global S3 buckets which can be shared across mailstore nodes. Bucket configurations can be created from any node and it is available across the nodes.
| The Global S3 Buckets can be deleted from the Administration Console at Home → Configure → Global Settings → Storage Management. |
Here are some of the important aspects of S3 Global Configurations:
-
The bucket name should be unique within the provider.
-
The same bucket can be used for multiple volumes, just follow different paths (check volume prefix option in
zmvolumecommand) for each volume. -
Following providers are supported: Amazon AWS, Ceph, Custom S3, EMC, NetApp-StorageGrid, OpenIO and Scality
Syntax:
zms3config {-a | -d | -l | -h} <options>Options
| Operations | Long Name | Short Name | Description |
|---|---|---|---|
Display Help |
--help |
-h |
Display Help |
Add new S3 config |
--add |
-a |
Create a new S3 bucket with further options. |
--storeProvider |
-t |
Store Provider to add s3BucketConfig, Valid Values are: AWS_S3, CEPH_S3, CUSTOM_S3, EMC_S3, STORAGE_GRID_S3, SCALITY_S3. |
|
--bucketName |
-bn |
Name of the bucket |
|
--accessKey |
-ak |
Access key |
|
--secretKey |
-sk |
Secret key |
|
--destPath |
-dp |
Destination path, root path in S3 bucket for storing volume data. |
|
--region |
-r |
S3 bucket region |
|
--url |
-url |
Endpoint URL for S3 bucket |
|
Delete S3 bucket |
--delete |
-d |
Delete S3 bucket |
--bucketID |
-bid |
Id of a bucket, which is used to delete the S3 bucket. |
|
List Bucket |
--list |
-l |
List all buckets |
Add S3 Configuration
-
To create an AWS bucket configuration with long option names, use the command:
zms3config --add --storeProvider AWS_S3 --bucketName <bucket_name> --accessKey <secret_key> --destPath <destination_path> --region <valid_aws_region> --url <aws_valid_endpoint_url> -
To create a Ceph bucket configuration with short option names, use the command:
zms3config -a -t CEPH_S3 -bn <bucket_name> -ak <secret_key> -dp <destination_path> --url <valid_endpoint_url> -
To create a Custom S3 bucket configuration with short option names, use the command:
zms3config -a -t CUSTOM_S3 -bn <bucket_name> -ak <secret_key> -dp <destination_path> --url <valid_endpoint_url> -
To create a EMC bucket configuration with short option names, use the command:
zms3config -a -t EMC_S3 -bn <bucket_name> -ak <secret_key> -dp <destination_path> --url <valid_endpoint_url> -
To create a StorageGrid bucket configuration with short option names, use the command:
zms3config -a -t STORAGE_GRID_S3 -bn <bucket_name> -ak <secret_key> -dp <destination_path> --url <valid_endpoint_url> -
To create a Scality bucket configuration with short option names, use the command:
zms3config -a -t SCALITY_S3 -bn <bucket_name> -ak <secret_key> -dp <destination_path> --url <valid_endpoint_url>
List S3 bucket configuration
List all the S3 buckets which are configured on the setup.
zms3config -lDelete S3 Configuration
| Be careful when performing this operation since the bucket is used on global level and can be referred in multiple volumes across the nodes. |
zms3config -d -bid <bucket_unique_id>Managing Internal and External Volumes using zmvolume CLI
The zmvolume command is used to create, edit and delete storage volumes. It supports creating Internal and External volumes. Internal volume is the default storage which is located on server directory whereas external volume uses S3 buckets/OpenIO setup provided by external store providers.
Syntax:
zmvolume {-a|-d|-l|-e|-dc|-sc} [options]Description
| Operation | Long Name | Short Name | Description |
|---|---|---|---|
Add new volume |
--add |
-a |
Adds a volume. |
--account |
-acc |
<arg> Name of Account for OpenIO Volume. |
|
--accountPort |
-ap |
<arg> Account Port for OpenIO Volume. It should be a numeric value. |
|
--bucketId |
-bid |
<arg> S3 Bucket ID. Note the bucket should be created globally and fetched by using |
|
--compress |
-c |
<arg> Compress BLOBs value is either true or false. The default value is false. |
|
--compressionThreshold |
-ct |
<arg> Compression threshold. The default value is 4KB. |
|
--name |
-n |
<arg> Volume name. It can contain only alphanumeric characters, _ (underscore), - (hyphen), and . (period) but can start with a begin with a letter or number. |
|
--nameSpace |
-ns |
<arg> Namespace for OpenIO Volume. |
|
--path |
-p |
<arg> Root path. |
|
--proxyPort |
-pp |
<arg> Proxy port for OpenIO Volumehttp://port.it[.] It should be a numeric value. |
|
--storageType |
-stp |
<arg> Name of the store provider (S3, OPENIO) |
|
--storeType |
-st |
<arg> Store type: internal or external |
|
--storeManagerClass |
-smc |
<arg> Optional parameter to specify non-default store manager classpath.Available only for S3 providers. |
|
--type |
-t |
<arg> Volume type (primaryMessage, secondaryMessage, or index) |
|
--url |
-url |
<arg> Endpoint URL for OpenIO Volume. |
|
--useIntelligentTiering |
-uit |
<arg> Use Intelligent tiering storage class only for AWS. The default value is false. |
|
--useInFrequentAccess |
-ufa |
<arg> Use Infrequent access storage class only for AWS. |
|
--useInFrequentAccThreshold |
-ufat |
<arg> Use Infrequent access storage class blob size threshold. The default value is 64KB. |
|
--volumePrefix |
-vp |
<arg> Volume Prefix. It must start with "/" and cannot contain other special characters except "-" and "/". |
|
--unified |
-un |
<arg> Parameter to enable Unified Storage support for the volume. If not specified, the default value is false. |
|
Delete a Volume |
--delete |
-d |
Deletes a volume. Provide volume ID as well. |
--id |
-id |
<arg> Volume ID. |
|
Display Current Volume |
--displayCurrent |
-dc |
Displays the current volume. |
Edit a Volume |
--edit |
-e |
Edits the volume w.r.t the provided volume ID (-id). Any of the options listed under "-a" can also be specified to have its value modified for vole type Internal. Note that only the Volume name can be edited for external volumes. |
Help option |
--help |
-h |
Shows the help for the usage options for this tool. |
List Volume |
--list |
-l |
Lists all the volumes. |
--server |
-s |
<arg> Mail server hostname. The default is localhost. |
|
Set volume as current volume |
--setCurrent |
-sc |
Set the current volume. |
Turn off the secondary volume |
--turnOffSecondary |
-ts |
Turns off the current secondary message volume. |
Add New Volume
Internal volume
To create Internal volume the required parameters are -n, -t, and -p, and the optional parameters are -c, -ct, and -st.
zmvolume -a -n <volumeName> -t <storageType> -p <pathOfVolume>External volume for OpenIO
To create a primary or secondary OpenIO volume, execute the following command:
zmvolume -a -n <volumeName> -t <storageType> -vp <volumePrefix> -st external -stp OPENIO -pp <proxyPort> -ap <accountPort> -url <URL> -acc <accountName> -ns <nameSpace>External volume for S3
To create a primary or secondary S3 (Amazon S3, NetApp StorageGrid, Ceph) volume, execute the following command:
zmvolume -a -n <volumeName> -t <storageType> -vp <volumePrefix> -st external -stp S3 -bid <bucketId>To create a primary or secondary S3 (Amazon S3, NetApp StorageGrid, Ceph) volume with Unified Storage support, execute the following command:
zmvolume -a -n <volumeName> -t <storageType> -vp <volumePrefix> -st external -stp S3 -bid <bucketId> -un trueEdit a Volume
Internal volume
Admin can edit all the parameters of the internal volumes used when creating it:
zmvolume -e -id <volumeId> -n <volumeName> -p <volumePath> -t <type> -c <compress> -ct <compressionThreshold>External volume
Only the name of the external volume can be edited:
zmvolume -e -id <volumeId> -n <volumeName>List Volume
To list all the volumes created:
zmvolume -lDelete a Volume
| Be careful when deleting the volume as it may cause data loss: |
zmvolume -d -id <volumeId>Set current volume
Sets the volume id as the current volume to be used as per the configured volume type:
zmvolume -sc -id <volumeId>Display current volume:
Display Primary and Secondary volume details set as current:
zmvolume -dcTurn off secondary
To disable the secondary volume:
zmvolume -tsHelp section
To display the help section:
zmvolume -hManage scheduling of the policies using zmschedulesmpolicy CLI
The zmschedulesmpolicy command is used for scheduling a Storage Management poilcy execution. To track the progress of the SM session, use the zmhsm -u command.
-
The scheduler supports a single SM session which can contain a single or multiple policies. If a new SM session is scheduled, it will override the existing session, if one exists.
-
The scheduled SM policy will execute once a day at the scheduled time and will execute every day until it is removed.
-
The time format used for scheduling a session is a 24-hour format. Minutes can not be specified while scheduling the SM session.
-
Even if the admin hasn’t defined any policy, a default global policy i.e. message, document:before:-30days will be executed while starting an SM session manually.
Syntax
zmschedulesmpolicy [-l|-h|-f|-e { <hours:00> } ]Options
| Operations | Long Name | Short Name | Description |
|---|---|---|---|
Help |
--help |
-h |
Get help about zmschedulesmpolicy (default command). |
List schedule |
--list |
-l |
Print existing scheduled SM policy. |
Flush/Cancel schedule |
--flush |
-f |
Remove current schedule (cancel all the scheduled SM policy execution) |
Add/Edit schedule |
--edit |
-e |
Edit current scheduled time with a specified time. If there is no existing scheduled policy then it will schedule a new SM policy at a given time. |
Help - zmchedulesmpolicy
Prints help page:
zmschedulesmpolicy --help
zmschedulesmpolicy -hList - Print the current scheduled SM policy
List the schedule SM policy execution. If there is no output regarding the scheduled SM policy it means no SM policy is currently scheduled.
zmschedulesmpolicy --list
zmschedulesmpolicy -lFlush/Cancel - Remove the current scheduled SM policy
The current scheduled SM policy is cancelled if available.
zmschedulesmpolicy --flush
zmschedulesmpolicy -fAdd/Edit - Schedule SM policy at a specified time
It accepts 24-hour format time as an argument which is a time to schedule SM policy.
This option will schedule a new SM policy if there are no scheduled policy execution or edit the existing schedule.
zmschedulesmpolicy --edit 15:00
zmschedulesmpolicy -e 15:00Manage SM Session using the zmhsm CLI
The zmhsm command is used to start, stop, abort and view the status of an SM session. SM session executes on the SM policy created for the particular server and starts moving blobs from the primary volume to the current secondary volume.
Syntax
zmhsm {abort|start|status} {server} <servername>Description
| Long Name | Short Name | Description |
|---|---|---|
--abort |
-a |
Abort the current SM session but not immediately. First, it completes the in-progress mailboxes and stop processing the proceeding mailboxes and then aborts the current SM session. The processed mailboxes will not be rolled back. |
--help |
-h |
Shows the help for the usage options for zmhsm. |
--server |
-s |
<arg> The mail server hostname. By default it is localhost [args]. |
--start |
-t |
Starts the SM process. |
--status |
-u |
The status of the SM session is displayed. |
Examples:
-
Start the SM Session
To start the SM session, execute the following command:
zmhsm -t -s localhost-
Abort the SM Session
To initiate the SM abort sequence, execute the following command:
zmhsm -a -s localhost-
Status of SM session
To view the SM status, execute the following command:
zmhsm -u -s localhostIt only shows the last SM session status. Following are some examples:
Example 1:
Start time: Thu Sep 08 01:57:04 EDT 2022 End time: Thu Sep 08 01:57:04 EDT 2022 Query :before:-1minute Not currently running. Moved 1 blob to volume 12. Mailboxes processed: 7 out of 7.
Example 2:
Last SM Session Stats Start time: Tue Aug 16 07:32:16 EDT 2022 Query :before:-1minute is:anywhere Currently running. Moved 0 blobs to volume 3. Mailboxes processed: 0 out of 61.
Manage Storage Management Policies
The Storage Management(SM) Policy is a set of rules that will be applied to define what items will be moved from the Primary Store to the Secondary Store when the zmhsm command is triggered, either manually or by scheduling zmchedulesmpolicy.
SM policies can be configured at global and server levels, since it is stored in the global and server LDAP attribute zimbraHSMPolicy.
Configure at Global Level (Default policies)
Use + prefix with the zimbraHSMPolicy attribute when adding multiple policies to the attribute.
zmprov mcf +zimbraHSMPolicy 'message:before:-1day in:Trash'
zmprov mcf +zimbraHSMPolicy 'message,document:before:-5day is:anywhere has:attachment larger:5m is:read'When multiple values are desired, the attribute can also be specified multiple times in a single provisioning command.
zmprov mcf zimbraHSMPolicy 'message:before:-129600minutes' zimbraHSMPolicy 'document,wiki:before:-10080minutes'| Specifying a single attribute value in a single provisioning command will wipe out the other instances of the value before running the command. Always retrieve the current configuration before setting the values to see what values exist. |
zmprov gcf zimbraHSMPolicyServer level Policies
A similar format can also be used to set up the policies at the server level.
zmprov ms `zmhostname` zimbraHSMPolicy 'message:before:-129600minutes'
zmprov gs `zmhostname` zimbraHSMPolicyCustom Storage Manager
Overview
The Zimbra StoreManager SDK is used to connect Zimbra to external data storage which is not available in Storage Management feature. By default, Zimbra uses a StoreManager implementation which writes files to local disk. Using this SDK it is possible to write files to a cloud data storage provider, a remote database, or any other storage technology.
| The source code examples are provided for illustration purposes only. They are not meant to be used directly in a production environment. |
| Code examples have been trimmed for readability. Imports, package declarations, and other details not directly related to StoreManager extension have been omitted. The complete code is available in Zimbra source control. |
Configuration
zimbra_class_store
The zimbra_class_store zmlocalconfig option configures the class used for the StoreManager. The default StoreManager class is the standard filesystem-based blob store:
Default:
zimbra_class_store = com.zimbra.cs.store.file.FileBlobStoreThis class can be replaced with a custom class to write the message blobs to the Store Manager of choice.
Example:
zmlocalconfig -e zimbra_class_store=com.zimbra.examples.extns.storemanager.MyStoreManagerzmlocalconfig options
external_store_delete_max_ioexceptions = 25
external_store_local_cache_max_bytes = 1073741824
external_store_local_cache_max_files = 10000
external_store_local_cache_min_lifetime = 60000configuration example
-
Copy
zimbra-extns-storemanager.jarto /opt/zimbra/lib/ext/storemanager dir -
Execute:
zmlocalconfig -e zimbra_class_store=com.zimbra.examples.extns.storemanager.ExampleStoreManager -
Restart server
-
Perform any write operations such as sending mail, uploading files, etc. Blobs should be written to /tmp/examplestore/blobs
Basic Integration
The minimum code for integration requires overriding ExternalStoreManager and implementing ExternalBlobIO. This interface contains methods for writing data, reading data, and deleting data.
/**
* Interface for the simplest blob store integration possible
* The implementor must provide functionality for reading, writing, and deleting blobs
*/
public interface ExternalBlobIO {
/**
* Write data to blob store
* @param in: InputStream containing data to be written
* @param actualSize: size of data in stream, or -1 if size is unknown. To be used by implementor for optimization where possible
* @param mbox: Mailbox which contains the blob. Can optionally be used by store for partitioning
* @return locator string for the stored blob, unique identifier created by storage protocol
* @throws IOException
* @throws ServiceException
*/
String writeStreamToStore(InputStream in, long actualSize, Mailbox mbox) throws IOException, ServiceException;
/**
* Create an input stream for reading data from blob store
* @param locator: identifier string for the blob as returned from write operation
* @param mbox: Mailbox which contains the blob. Can optionally be used by store for partitioning
* @return InputStream containing the data
* @throws IOException
*/
InputStream readStreamFromStore(String locator, Mailbox mbox) throws IOException;
/**
* Delete a blob from the store
* @param locator: identifier string for the blob
* @param mbox: Mailbox which contains the blob. Can optionally be used by store for partitioning
* @return true on success false on failure
* @throws IOException
*/
boolean deleteFromStore(String locator, Mailbox mbox) throws IOException;
}
Here is an example of a minimalist StoreManager implementation which writes to local disk using java.io.File and related classes. The details of getNewFile() are omitted for brevity and would typically involve creating a new empty file in a predefined directory.
This class also overrides three methods from ExternalStoreManager
-
startup() - called during initialization, can be used to setup any paths, background threads, or other resources needed by the store implementation. Must call super.startup() to initialize parent resources
-
shutdown() - called during application shutdown, can be used to cleanup any temporary resources and terminate background threads. Must call super.shutdown() to cleanup parent resources
-
isCentralized() - A boolean value which is used in multi-server configurations. If true then the store is global and locators from one Zimbra server can be accessed from another Zimbra server, otherwise locators are only valid within the server where they are created. An example of a centralized store would be a cloud file storage system, and an example of a non-centralized store would be a local filesystem
public class SimpleStoreManager extends ExternalStoreManager {
@Override
public void startup() throws IOException, ServiceException {
super.startup();
//initialize any local resources such as storage directory
}
@Override
public void shutdown() {
super.shutdown();
//cleanup any resources and background threads
}
@Override
protected boolean isCentralized() {
//this store writes to local disk, so blobs cannot be accessed from other Zimbra servers
return false;
}
private File getNewFile(Mailbox mbox) throws IOException {
//generate a new file on disk
}
@Override
public String writeStreamToStore(InputStream in, long actualSize, Mailbox mbox) throws IOException {
File destFile = getNewFile(mbox);
FileUtil.copy(in, false, destFile);
return destFile.getCanonicalPath();
}
@Override
public InputStream readStreamFromStore(String locator, Mailbox mbox) throws IOException {
return new FileInputStream(locator);
}
@Override
public boolean deleteFromStore(String locator, Mailbox mbox) throws IOException {
File deleteFile = new File(locator);
return deleteFile.delete();
}
HTTP Storage
Another common use case is writing to an external HTTP API, i.e. a cloud file store. If the HTTP API allows anonymous uploads, this can be accomplished by extending HttpStoreManager. The implementor need only provide the code for the methods which define the URL which is used to POST new content, the process of extracting the HTTP server’s unique identifier from the POST response, and the URLs for getting and deleting previously stored content. The Zimbra Mailbox object is provided for optional usage; depending on the HTTP API semantics it can be used to construct part of the URL, or it can be ignored. The size, SHA-256 digest, and Mailbox object are provided in the getLocator() method, as is the Apache Commons HttpClient PostMethod which can be used to extract response headers and the response body. For complete details on HttpClient see http://hc.apache.org/httpclient-3.x/
protected abstract String getPostUrl(Mailbox mbox);
protected abstract String getGetUrl(Mailbox mbox, String locator);
protected abstract String getDeleteUrl(Mailbox mbox, String locator);
protected abstract String getLocator(PostMethod post, String postDigest, long postSize, Mailbox mbox) throws ServiceException, IOException;
The full listing of HttpStoreManager is below. Note that isCentralized() returns true since there will typically be a single HTTP store which all Zimbra servers connect to. The store must generate globally unique locators which can be accessed from any Zimbra server.
public abstract class HttpStoreManager extends ExternalStoreManager {
protected abstract String getPostUrl(Mailbox mbox);
protected abstract String getGetUrl(Mailbox mbox, String locator);
protected abstract String getDeleteUrl(Mailbox mbox, String locator);
protected abstract String getLocator(PostMethod post, String postDigest, long postSize, Mailbox mbox) throws ServiceException, IOException;
@Override
public String writeStreamToStore(InputStream in, long actualSize, Mailbox mbox) throws IOException,
ServiceException {
MessageDigest digest;
try {
digest = MessageDigest.getInstance("SHA-256");
} catch (NoSuchAlgorithmException e) {
throw ServiceException.FAILURE("SHA-256 digest not found", e);
}
ByteUtil.PositionInputStream pin = new ByteUtil.PositionInputStream(new DigestInputStream(in, digest));
HttpClient client = ZimbraHttpConnectionManager.getInternalHttpConnMgr().newHttpClient();
PostMethod post = new PostMethod(getPostUrl(mbox));
try {
HttpClientUtil.addInputStreamToHttpMethod(post, pin, actualSize, "application/octet-stream");
int statusCode = HttpClientUtil.executeMethod(client, post);
if (statusCode == HttpStatus.SC_OK || statusCode == HttpStatus.SC_CREATED || statusCode == HttpStatus.SC_NO_CONTENT) {
return getLocator(post, ByteUtil.encodeFSSafeBase64(digest.digest()), pin.getPosition(), mbox);
} else {
throw ServiceException.FAILURE("error POSTing blob: " + post.getStatusText(), null);
}
} finally {
post.releaseConnection();
}
}
@Override
public InputStream readStreamFromStore(String locator, Mailbox mbox)
throws IOException {
HttpClient client = ZimbraHttpConnectionManager.getInternalHttpConnMgr().newHttpClient();
GetMethod get = new GetMethod(getGetUrl(mbox, locator));
int statusCode = HttpClientUtil.executeMethod(client, get);
if (statusCode == HttpStatus.SC_OK) {
return new UserServlet.HttpInputStream(get);
} else {
get.releaseConnection();
throw new IOException("unexpected return code during blob GET: " + get.getStatusText());
}
}
@Override
public boolean deleteFromStore(String locator, Mailbox mbox)
throws IOException {
HttpClient client = ZimbraHttpConnectionManager.getInternalHttpConnMgr().newHttpClient();
DeleteMethod delete = new DeleteMethod(getDeleteUrl(mbox, locator));
try {
int statusCode = HttpClientUtil.executeMethod(client, delete);
if (statusCode == HttpStatus.SC_OK || statusCode == HttpStatus.SC_NO_CONTENT) {
return true;
} else if (statusCode == HttpStatus.SC_NOT_FOUND) {
return false;
} else {
throw new IOException("unexpected return code during blob DELETE: " + delete.getStatusText());
}
} finally {
delete.releaseConnection();
}
}
}
Content based storage
Some external storage systems may maintain identifiers based on data content. For example, a store may use SHA-256 or another hash as the primary key for stored objects. The ContentAddressableStoreManager abstract class may be used as a starting point for integration with this type of store.
The implementer must provide code to generate a byte[] hash and a String locator.
/**
* Generate content hash for the blob using the hash algorithm from the remote store
* @param blob - Blob which has been constructed locally
* @return byte[] representing the blob content
* @throws ServiceException
* @throws IOException
*/
public abstract byte[] getHash(Blob blob) throws ServiceException, IOException;
/**
* Generate a locator String based on the content of blob
* @param blob - Blob which has been constructed locally
* @return String representing the blob content, e.g. hex encoded hash
* @throws ServiceException
* @throws IOException
*/
protected abstract String getLocator(Blob blob) throws ServiceException, IOException;
/**
* Return the locator string for the content hash by hex encoding or other similar encoding required by the store
* @param hash: byte[] containing the content hash
* @return the locator String
*/
public abstract String getLocator(byte[] hash);
Here is an example implementation which uses SHA-256 as the hash and appends .blob to generate the locator.
@Override
protected String getLocator(Blob blob) throws ServiceException, IOException {
return getLocator(getHash(blob));
}
@Override
public String getLocator(byte[] hash) {
return Hex.encodeHexString(hash).toUpperCase() + ".blob";
}
@Override
public byte[] getHash(Blob blob) throws ServiceException, IOException {
MessageDigest digest = MessageDigest.getInstance("SHA-256");
DigestInputStream dis = new DigestInputStream(blob.getInputStream(), digest);
while (dis.read() >= 0) {
}
return digest.digest();
}
The full listing of ContentAddressableStoreManager is below. Several methods from ExternalStoreManager are overridden so the content locator can be included in the upstream write requests.
/**
* Abstract framework for StoreManager implementations which require content hash or other content-based locator
* The base implementation here handles the more common cases where blob is cached locally by storeIncoming and then pushed to remote store during stage operation
*/
public abstract class ContentAddressableStoreManager extends ExternalStoreManager {
@Override
public String writeStreamToStore(InputStream in, long actualSize,
Mailbox mbox) throws IOException, ServiceException {
//the override of stage below should never allow this code to be reached
throw ServiceException.FAILURE("anonymous write is not permitted, something went wrong", null);
}
/**
* Generate content hash for the blob using the hash algorithm from the remote store
* @param blob - Blob which has been constructed locally
* @return byte[] representing the blob content
* @throws ServiceException
* @throws IOException
*/
public abstract byte[] getHash(Blob blob) throws ServiceException, IOException;
/**
* Generate a locator String based on the content of blob
* @param blob - Blob which has been constructed locally
* @return String representing the blob content, e.g. hex encoded hash
* @throws ServiceException
* @throws IOException
*/
protected abstract String getLocator(Blob blob) throws ServiceException, IOException;
/**
* Return the locator string for the content hash by hex encoding or other similar encoding required by the store
* @param hash: byte[] containing the content hash
* @return the locator String
*/
public abstract String getLocator(byte[] hash);
/**
* Write data to blob store using previously generated blob locator
* @param in: InputStream containing data to be written
* @param actualSize: size of data in stream, or -1 if size is unknown. To be used by implementor for optimization where possible
* @param locator string for the blob as returned by getLocator()
* @param mbox: Mailbox which contains the blob. Can optionally be used by store for partitioning
* @throws IOException
* @throws ServiceException
*/
protected abstract void writeStreamToStore(InputStream in, long actualSize, Mailbox mbox, String locator) throws IOException, ServiceException;
@Override
public StagedBlob stage(Blob blob, Mailbox mbox) throws IOException, ServiceException {
if (supports(StoreFeature.RESUMABLE_UPLOAD) && blob instanceof ExternalUploadedBlob && blob.getRawSize() > 0) {
ZimbraLog.store.debug("blob already uploaded, just need to commit");
String locator = ((ExternalResumableUpload) this).finishUpload((ExternalUploadedBlob) blob);
ZimbraLog.store.debug("staged to locator %s", locator);
localCache.put(locator, getContent(blob));
return new ExternalStagedBlob(mbox, blob.getDigest(), blob.getRawSize(), locator);
} else {
InputStream is = getContent(blob);
String locator = getLocator(blob);
try {
StagedBlob staged = stage(is, blob.getRawSize(), mbox, locator);
if (staged != null) {
ZimbraLog.store.debug("staged to locator %s", staged.getLocator());
localCache.put(staged.getLocator(), getContent(blob));
}
return staged;
} finally {
ByteUtil.closeStream(is);
}
}
}
@Override
public StagedBlob stage(InputStream in, long actualSize, Mailbox mbox) throws ServiceException, IOException {
Blob blob = storeIncoming(in);
try {
return stage(blob, mbox);
} finally {
quietDelete(blob);
}
}
protected StagedBlob stage(InputStream in, long actualSize, Mailbox mbox, String locator) throws ServiceException {
MessageDigest digest;
try {
digest = MessageDigest.getInstance("SHA-256");
} catch (NoSuchAlgorithmException e) {
throw ServiceException.FAILURE("SHA-256 digest not found", e);
}
ByteUtil.PositionInputStream pin = new ByteUtil.PositionInputStream(new DigestInputStream(in, digest));
try {
writeStreamToStore(pin, actualSize, mbox, locator);
return new ExternalStagedBlob(mbox, ByteUtil.encodeFSSafeBase64(digest.digest()), pin.getPosition(), locator);
} catch (IOException e) {
throw ServiceException.FAILURE("unable to stage blob", e);
}
}
Resumable Upload (Octopus only)
In the Octopus REST API it is possible for clients to partially upload documents and then resume them later. With a default ExternalStoreManager implementation, the blobs are staged within the Octopus server and only sent to the external store once fully uploaded. This can lead to undesirable delay for the client upon completion of an upload. In order to optimize this process, integrators may implement the ExternalResumableUpload interface, then provide ExternalResumableIncomingBlob and ExternalResumableOutputStream implementation which interacts with the store in a resumable manner.
public interface ExternalResumableUpload {
/**
* Create a new ExternalResumableIncomingBlob instance to handle the upload
* of a single object. The implementation should compute all remote metadata
* such as remote id, size, and content hash inline with the upload process
* so that finishUpload() does not need to traverse the data again
*
* @param id: local upload ID. Used internally; must be passed to super constructor
* @param ctxt: local upload context. Used internally; must be passed to super constructor
* @return initialized ExternalResumableIncomingBlob instance ready to accept a new data upload
* @throws IOException
* @throws ServiceException
*/
public ExternalResumableIncomingBlob newIncomingBlob(String id, Object ctxt) throws IOException, ServiceException;
/**
* Finalize an upload. Depending on store semantics this may involve a
* commit, checksum, or other similar operation.
*
* @param blob: The ExternalUploadedBlob which data has been written into
* @return String identifier (locator) for the permanent storage location for the uploaded content
* @throws IOException
* @throws ServiceException
*/
public String finishUpload(ExternalUploadedBlob blob) throws IOException, ServiceException;
}
/**
* IncomingBlob implementation which streams data directly to external store during upload
* The store must support resumable upload, otherwise it should use the default BufferingIncomingBlob implementation
*
*/
public abstract class ExternalResumableIncomingBlob extends BufferingIncomingBlob {
public ExternalResumableIncomingBlob(String id, BlobBuilder blobBuilder, Object ctx) throws ServiceException, IOException {
super(id, blobBuilder, ctx);
}
@Override
public OutputStream getAppendingOutputStream() throws IOException {
lastAccessTime = System.currentTimeMillis();
return getAppendingOutputStream(blobBuilder);
}
@Override
public long getCurrentSize() throws IOException {
long internalSize = super.getCurrentSize();
long remoteSize = getRemoteSize();
if (remoteSize != internalSize) {
throw new IOException("mismatch between local (" + internalSize + ") and remote (" + remoteSize + ") " +
"content sizes. Client must restart upload", null);
} else {
return internalSize;
}
}
@Override
public Blob getBlob() throws IOException, ServiceException {
return new ExternalUploadedBlob(blobBuilder.finish(), id);
}
/**
* Retrieve an OutputStream which can be used to write data to the remote upload location
* @param blobBuilder: Used to create local Blob instance inline with upload. Must be passed to super constructor
* @return ExternalResumableOutputStream instance which can write data to the upload session/location encapsulated by this IncomingBlob instance
* @throws IOException
*/
protected abstract ExternalResumableOutputStream getAppendingOutputStream(BlobBuilder blobBuilder) throws IOException;
/**
* Query the remote store for the size of the upload received so far. Used for consistency checking during resume
* @return: The number of bytes which have been stored remotely.
* @throws IOException
* @throws ServiceException
*/
protected abstract long getRemoteSize() throws IOException;
}
/**
* OutputStream used to write to an external store during resumable upload.
*
*/
public abstract class ExternalResumableOutputStream extends BlobBuilderOutputStream {
protected ExternalResumableOutputStream(BlobBuilder blobBuilder) {
super(blobBuilder);
}
@Override
public void write(byte[] b, int off, int len) throws IOException {
writeToExternal(b, off, len);
super.write(b, off, len);
}
/**
* Append data to remote upload location
* @param b: byte array holding the data to upload
* @param off: offset to start the upload from
* @param len: length of the data to copy from the byte array
* @throws IOException
*/
protected abstract void writeToExternal(byte[] b, int off, int len) throws IOException;
}
The following example illustrates the key functionality involved in resumable upload. The example is intentionally arbitrary and uses local disk storage.
public class SimpleStreamingStoreManager extends SimpleStoreManager implements ExternalResumableUpload {
String uploadDirectory = "/tmp/simplestore/uploads";
@Override
public void startup() throws IOException, ServiceException {
super.startup();
FileUtil.mkdirs(new File(uploadDirectory));
}
@Override
public String finishUpload(ExternalUploadedBlob blob) throws IOException,
ServiceException {
ZimbraLog.store.info("finishing upload to "+blob.getUploadId());
return blob.getUploadId();
}
@Override
public ExternalResumableIncomingBlob newIncomingBlob(String id, Object ctxt) throws IOException, ServiceException {
return new SimpleStreamingIncomingBlob(id, getBlobBuilder(), ctxt);
}
private class SimpleStreamingIncomingBlob extends ExternalResumableIncomingBlob {
private final File file;
public SimpleStreamingIncomingBlob(String id, BlobBuilder blobBuilder,
Object ctx) throws ServiceException, IOException {
super(id, blobBuilder, ctx);
String baseName = uploadDirectory+"/upload-"+id;
String name = baseName;
synchronized (this) {
int count = 1;
File upFile = new File(name+".upl");
while (upFile.exists()) {
name = baseName+"_"+count++;
upFile = new File(name+".upl");
}
if (upFile.createNewFile()) {
ZimbraLog.store.debug("writing to new file %s",upFile.getName());
file = upFile;
} else {
throw new IOException("unable to create new file");
}
}
}
@Override
protected ExternalResumableOutputStream getAppendingOutputStream(BlobBuilder blobBuilder) throws IOException {
return new SimpleStreamingOutputStream(blobBuilder, file);
}
@Override
protected long getRemoteSize() throws IOException {
return file.length();
}
@Override
public Blob getBlob() throws IOException, ServiceException {
return new ExternalUploadedBlob(blobBuilder.finish(), file.getCanonicalPath());
}
}
private class SimpleStreamingOutputStream extends ExternalResumableOutputStream {
private final FileOutputStream fos;
public SimpleStreamingOutputStream(BlobBuilder blobBuilder, File file) throws IOException {
super(blobBuilder);
this.fos = new FileOutputStream(file, true);
}
@Override
protected void writeToExternal(byte[] b, int off, int len)
throws IOException {
fos.write(b, off, len);
}
}
Zimbra Chat
This section will give an overview of Zimbra’s Chat feature.
Zimbra Chat is a secure, real-time messaging solution integrated into the Zimbra Daffodil version 10.1.7 onwards, designed to enhance team communication while adhering to Zimbra’s core principles of privacy, data sovereignty, and user control. This chat service is offered in two distinct variants.
Chat Variants
-
Basic Chat: A lightweight one-to-one messaging solution, ideal for users who need quick, person-to-person communication embedded within the UI.
-
Advanced Chat: A full-featured messaging platform, enabling threaded group conversations, extensive search, channels, and additional collaboration tools. Built using an open-source platform, this variant supports advanced use cases and is suited for organizations needing rich communication experiences.
Zimbra Daffodil version 10.1.7 - Both variants are integrated directly into Zimbra’s Modern Web Client (Modern UI) and support secure on-premises deployment.
Zimbra Daffodil version 10.1.8 - Classic UI support for Chat. From 10.1.8 onwards both variants are integrated into Zimbra’s Classic Web Client (Classic UI) and support secure on-premises deployment.
Basic Chat Vs. Advanced Chat Comparison
| Feature | Basic Chat | Advanced Chat |
|---|---|---|
1. Direct Messaging (One to one chat) |
✓ |
✓ |
2. Notifications |
✓ |
✓ |
3. User Presence |
✓ |
✓ |
4. User Preference |
Limited |
✓ |
5. Customization |
✗ |
Limited |
6. Localization |
Limited |
Limited |
7. Emoji support |
✓ |
✓ |
8. Scalability (total users) |
50k+ |
50k+ |
9. Multi-domain support |
✓ |
✓ |
10. Zimbra Chat Server OS support |
Ubuntu 22/24 Only |
Ubuntu 22/24 Only |
11. LDAP based authentication |
✓ |
✓ |
12. Auto-provisioning |
✓ |
✓ |
13. Platform support |
Web-client only |
Web-client only |
14. Comprehensive documentation |
✓ |
✓ |
15. Message History search |
✗ |
✓ |
16. Ad-hoc Groups |
✗ |
✓ |
17. Channels |
✗ |
✓ |
18. Topic based threading |
✗ |
✓ |
19. File sharing |
✗ |
✓ |
20. Voice |
✗ |
In-built integration with public instance of Jitsi |
21. Expressive formatting (bold, lists, etc.) |
✓ |
✓ |
22. Advanced features (send later, mark unread) |
✗ |
✓ |
23. Role based access control |
✗ |
✓ |
24. Domain level Custom Branding |
✗ |
✓ |
25. Import data from other chat products |
✗ |
✓ |
26. Desktop application |
✗ |
✓ |
27. Mobile application |
✗ |
✓ |
Licensing Guide
Zimbra’s new Chat solution offers two distinct tiers:
-
Basic One To One Chat – free of charge as introductory pricing, lightweight messaging.
-
Advanced Chat – paid tier with extended features.
To begin using Zimbra Chat, ensure your system is on Zimbra Daffodil version 10.1.7 version or later and follow the relevant guidance below.
Prerequisite
The Zimbra license must have the following entitlements enabled:
-
BasicOneToOneChatAccountsLimit- To enable basic one to one chat. -
ChatAccountsLimit- To enable advanced chat.
Both entitlements work independently of each other.
|
Zimbra Chat is an add-on module and is not included in any existing editions or bundles. It must be purchased separately, even for customers with current Zimbra licenses. Please reach out to your Zimbra representative to get these entitlements. |
For New Customers (Starting with Zimbra Daffodil version 10.1.7 or later)
-
A license is issued as part of the onboarding process.
-
Chat features (Basic or Advanced) are included based on your selected plan.
-
Once licensed:
-
Chat features will be enabled automatically.
-
You’ll receive the license key via email.
-
-
If you have not received chat functionality or wish to upgrade, please reach out to your Zimbra representative.
For Existing Customers Already on Zimbra Daffodil 10.1.x version older than 10.1.7
Basic One to One Chat (Free)
-
This is available at no cost but is not enabled by default.
-
To enable:
-
Contact your Zimbra representative and request Basic Chat to be enabled for your license.
-
Once updated, restart your mailbox servers to activate the chat functionality.
-
Advanced Chat (Paid)
-
Contact your Zimbra representative and upgrade your license to enable Advanced Chat.
-
Upon license update:
-
Restart all mailbox servers to ensure chat extensions are loaded.
-
Chat will be available within your Zimbra interface.
-
|
If you’re upgrading from version 10.1.6 to 10.1.7:
|
For Customers on Older Versions (8.8.15, 9.0.x, 10.0.x)
-
Your older license (v2) must be migrated to the new format (v3) before you proceed with the upgrade.
-
Please contact your Zimbra representative and request the v3 license to get the updated entitlements.
-
-
Upgrade to Zimbra Daffodil version 10.1.7 or later.
-
Once on a latest Zimbra version:
-
Basic Chat can be enabled free of cost.
-
Advanced Chat is available via a paid upgrade.
-
You will now be able to access the new Chat features.
For Customers with existing Zimbra Talk Entitlement (8.8.15, 9.0.x)
-
Your older license (v2) must be migrated to the new format (v3) before you proceed with the upgrade.
-
Please contact your Zimbra representative and request the v3 license to get the updated entitlements.
-
-
Upgrade to Zimbra Daffodil version 10.1.7 or later.
-
Once on a latest Zimbra version:
-
Basic Chat will be enabled at no additional cost.
-
Advanced Chat is available under following conditions:
-
Advanced Chat Limit will by default be set to
ZTalkAccountsLimit. -
Available till Support end date for ZTalk SKU/contract.
-
New Zimbra Chat SKUs will be provided to such customers at no additional cost.
-
-
You will now be able to access the new Chat features.
Things to know before installing Zimbra Chat
Before proceeding with the installation, administrators should be aware of the following prerequisites and limitations:
-
Separate Server Requirement: Zimbra Chat must be installed on a dedicated server. It cannot be co-hosted with the Zimbra Collaboration Suite components.
-
Version Compatibility: Zimbra Chat is supported only on Zimbra Daffodil version 10.1.7 and above. Customers on earlier versions must upgrade their ZCS environment.
-
Modern UI: Chat is supported for the Modern UI from Zimbra Daffodil version 10.1.7.
-
Classic UI: Chat is supported for the Classic UI from Zimbra Daffodil version 10.1.8.
-
LDAP Integration: Zimbra Chat uses LDAP authentication from Zimbra Collaboration Suite (ZCS) for secure user login and provisioning.
-
No Built-In Video: This is a chat only solution, and does not include video conferencing solution. However, an integration with open source video solution has been provided. For more details, refer to Chat Administrator → Video section.
-
No support for Migration: There is no support for migration from earlier chat solutions like Zimbra Talk, or Hosted chat and video.
-
Performance considerations: While the solution is tested for 50k+ total users and up to 10k users on a single server, the actual performance might vary depending on usage patterns, online users, users per domain, infrastructure used for chat etc. Refer to the Scaling and Infrastructure guide section for more information on best practices for scaling the solution effectively.
-
Supported OS: Only Ubuntu 22 and 24 are officially supported for installation of Zimbra Chat server.
-
Add-On Model: Zimbra Chat is not bundled with Zimbra Collaboration Suite (ZCS) by default—it is offered as an add-on feature, enabling customers to choose the level of functionality needed.
Zimbra Chat Architecture Overview
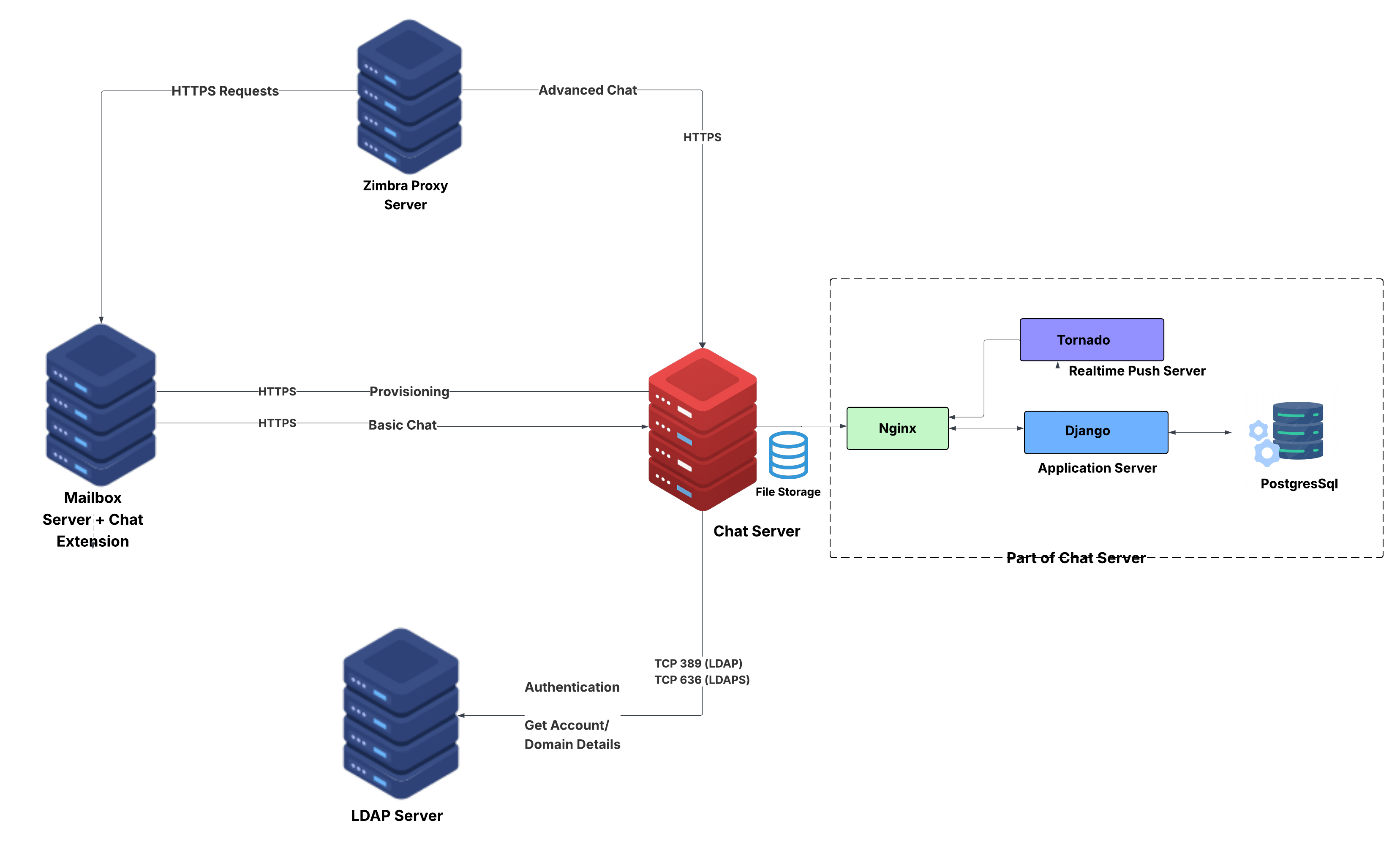
-
Mailbox Server + Chat Extension: Initiates provisioning and Basic Chat requests via HTTPS.
-
Zimbra Proxy Server: Routes HTTPS requests and forwards Advanced Chat requests to the Chat Server.
-
Chat Server: Interacts with mailbox and LDAP servers, and forwards requests to application components.
-
LDAP Server: Provides user authentication and domain/account information over LDAP/LDAPS.
Scaling and Infrastructure Guide
This section outlines scaling guidelines and configurations, offering recommendations for selecting the appropriate compute resources to ensure optimal performance, scalability across different deployment sizes.
Resource Sizing
Active users include web clients performing passive background tasks (For example: presence for online status) against Zulip for Zimbra.
Implement vertical scaling to fit machine resources for an expected active user count. The following sample sizes may require adjustment depending on the chat service activity levels.
|
Favor a dedicated PostgreSQL setup if significant growth in number of active users is anticipated. |
-
~500 Active Users Instance
-
Provision compute instance for all-in-one - Zulip and PostgreSQL DB (4 vCPU, 16 GB RAM, 200 GB disk)
-
-
~1k Active Users Instance
-
Provision compute instance for Zulip’s PostgreSQL DB (2 vCPU, 16 GB RAM,100 GB disk)
-
Provision compute instance for Zulip (4 vCPU, 32 GB RAM,200 GB disk)
-
-
~3k Active Users Instance
-
Provision compute instance for Zulip’s PostgreSQL DB (2 vCPU, 16 GB RAM,200 GB disk)
-
Provision compute instance for Zulip (8 vCPU, 32 GB RAM,300 GB disk)
-
-
~5k Active Users Instance
-
Provision compute instance for Zulip’s PostgreSQL DB (2 vCPU, 16 GB RAM,300 GB disk)
-
Provision compute instance for Zulip (12 vCPU, 32 GB RAM,400 GB disk)
-
Network Bandwidth
-
When establishing network bandwidth guidelines between different systems, such as Zimbra, Zulip, and PostgreSQL, it’s essential to consider several factors such as expected volume of traffic, the number of concurrent users.
-
The following sample sizes may require adjustment depending on the specific size of your organisation, the volume of data exchanged, concurrent user load.
Network Bandwidth between Zimbra and Chat Server:
-
Recommended Bandwidth:
-
A minimum of 100 Mbps would be suitable for small(upto ~500 Active Users) and medium-sized organizations(~500 to ~3k Active Users) where integration involves basic text messages.
-
For larger deployments (more than 3k Active Users) where chat data is heavily used (for example- large message history, frequent queries), 1 Gbps is recommended to handle high-frequency database requests and ensure low latency.
-
|
Continuously monitor network performance and adjust bandwidth allocation as needed based on usage patterns and traffic spikes. |
Network Bandwidth between Zulip and PostgreSQL Server:
PostgreSQL is often used as a backend database for chat, storing user data, messages, chat history, and configuration settings.
-
Recommended Bandwidth:
-
For smaller organizations(upto ~500 Active Users) with moderate database usage (for example: less frequent queries or fewer users), 100 Mbps should be sufficient. This bandwidth can handle regular database queries and writes without causing performance degradation.
-
For larger deployments(more than 3k Active Users) chat data is heavily used (for example: large message history, frequent queries), 1 Gbps is recommended to handle high-frequency database requests and ensure low latency.
-
|
Continuously monitor network performance and adjust bandwidth allocation as needed based on usage patterns and traffic spikes. |
Scaling Process
When deploying multiple Zulip instances, consider the following approaches:
-
Balanced Distribution (Recommended): Distribute domains evenly, by user count, across Zulip servers to optimize resource usage
-
Incremental Deployment (Acceptable): Deploy domains gradually, adding new Zulip instances as needed
-
Local and General Zimbra Config Customisation
-
Adjust the relevant Zimbra options to support Zulip
-
-
For each Zulip instance
-
Determine Zulip instance capacity and sizing
-
Deploy and configure Zulip
-
Provision domains and users
-
Configure Zulip
-
-
Repeat step 2, deploying a fresh Zulip instance as more total user limit is needed.
See sections below for details.
Tornado Sharding
The Tornado service is responsible for handling real-time events in Zulip.
In general each Tornado process may account for approximately 1000 event queues. Thus in a scenario where there are more than 1000 consistently active users, multiple Tornado processes may be needed to handle the traffic.
For Example:
-
2k active users would expect about 2 to 3 tornado shards.
-
3k active users would expect about 3 to 4 tornado shards.
Shard by User Id
The Zulip config may be adjusted to shard tornado by user id. This may be useful for spreading load across a few tornado services for a Zulip instance.
Adjust and add the following to /etc/zulip/zulip.conf to shard user id on the local Zulip instance.
-
In the following example: all users in
big-realm, by user id, over 4 tornado services that will be accessible (by the subsequent refresh script) on ports 9800, 9801, 9802, and 9803:
[tornado_sharding]
9800_9801_9802_9803 = big-realm-
After modifying the configuration specified in above section, run the following scripts with
rootuser to apply the changes, stand up the instances, update config files, refresh components, and restart nginx:
/home/zulip/deployments/current/scripts/zulip-puppet-apply
# accept prompt: y
/home/zulip/deployments/current/scripts/refresh-sharding-and-restartYou may then verify the new tornado services are accessible with nc on the configured ports on zulip server. For example: nc -zv <hostname> <port_no>
Tornado Sharding beyond 10 processes
Tornado sharding scales properly till 9 processes. Scaling tornado shards to 10 or more than 10 processes may fail with exception TornadoQueueClient couldn’t connect to RabbitMQ in zulip’s /var/log/zulip/server.log.
The reason being port 9810 was already in use by smokescreen.
Please follow below steps to resolve this issue:
-
Stop the smokescreen with
zulipuser usingsupervisorctl stop smokescreen -
Start the chat services with
zulipuser using/home/zulip/deployments/current/scripts/start-server -
Check the status if all services are up with
zulipuser usingsupervisorctl status -
If you find any service in stopped state, please try bringing them up individually with
zulipuser. For example:-
If
zulip-djangois not up, usesupervisorctl start zulip-djangoto bring it up -
If
zulip-tornado:zulip-tornado-port-9810is not up, usesupervisorctl start zulip-tornado:zulip-tornado-port-9810to bring it up.
-
Zimbra Configuration
Adjust the relevant max_total_connections options on each mailstore to support proxy traffic:
zmlocalconfig -e httpclient_internal_connmgr_max_host_connections=2000
zmlocalconfig -e httpclient_external_connmgr_max_host_connections=2000
zmlocalconfig -e httpclient_internal_connmgr_max_total_connections=2000
zmlocalconfig -e httpclient_external_connmgr_max_total_connections=2000
zmmailboxdctl restart|
May require further increases to accommodate increased proxy traffic to Zulip instances. |
Adjust the zimbraHttpNumThreads config to support proxy traffic:
zmprov mcf zimbraHttpNumThreads 2000|
May require further increases to accommodate increased proxy traffic to Zulip instances. |
Django
The Django service is responsible for Zulip’s core APIs.
A single Django service is usually enough to handle the traffic for each of the supported sizes in a non-HA capacity. It may be necessary to increase the number of processes to speed things up in cases where the baseline incoming traffic drastically exceeds the processed traffic.
Configure Django
Configure /etc/zulip/uwsgi.ini to fit Zulip instance resources
-
processes-
Number of processes for web application.
-
Increasing this value increases the number of concurrent operations that may be processed by the web application, while also increasing the resource consumption of the web application.
-
Increase the number of processes to twice as the number of vCPU for zulip instance :
-
2 * vCPU
-
-
listen-
Size of listen queue.
-
Increasing this value increases the maximum number of requests that may be in the listen queue. Increasing this value beyond a size large enough to handle spike traffic is unlikely to be useful. If the maximum queue size is consistently hit, it indicates that the web application is processing requests too slowly to keep up with the incoming traffic’s generation of requests.
-
May require adjustment to OS system configuration for
net.core.somaxcon
-
Restart the Zulip service using -
su zulip -c '/home/zulip/deployments/current/scripts/restart-server'Check the status of chat services using -
su zulip -c 'supervisorctl status'Installation Guide
Prerequisite
To enable Basic Chat and/or Advanced Chat in Zimbra, ensure the following requirements are met:
License Activation
The Zimbra license must have the following entitlements enabled:
-
BasicOneToOneChatAccountsLimit - To enable basic one to one chat.
-
ChatAccountsLimit - To enable advanced chat.
Zimbra Collaboration Server (ZCS) Version Requirement
-
Zimbra Daffodil version 10.1.7 or later
Zimbra Chat Server Hardware Requirements
Minimum Requirements:
CPU: Dual-core processor (Intel/AMD)
RAM: 2 GB
Disk Space: 10 GB of free disk spaceRecommended Requirements:
CPU: Quad-core processor (Intel/AMD)
RAM: 4 GB or more
Disk Space: 20 GB or more (depends on expected data storage needs)For more details refer to Scaling and Infrastructure guide section.
Zimbra Chat Server Operating System Requirements
Compatible Linux Distributions:
-
Ubuntu 22.04
-
Ubuntu 24.04
Supported CPU Architectures:
-
x86-64
-
aarch64
Zimbra Chat Server Additional Requirements
-
A dedicated machine or VM.
-
The installer expects the Zimbra Chat server application (Zulip) and/or PostgreSQL to be the only thing running on the system; it will install system packages with apt (like nginx, PostgreSQL, and Redis) and configure them for its own use. We strongly recommend using either a fresh machine instance in a cloud provider, a fresh VM, or a dedicated machine.
-
A connection to the Internet.
SSL Certificate Requirements
A valid SSL certificate is required for the Chat server to ensure secure HTTPS communication, allowing the Zimbra mailstore to access it correctly.
For more details refer: Installation Guide → Install Zimbra Chat server section.
Domain & URL Configuration
Suppose that Zimbra Chat server hostname and Zimbra domain have been applied as follows:
Chat server hostname is chat1.mydomain.com
Zimbra domain (the domain of an email address) is @domain1.example.com
The following requirements needs to be met:
-
Chat server will be accessed on https (https://chat1.mydomain.com) for provisioning and some other purposes. The hostname chat1.mydomain.com must be resolvable by Zimbra proxy and mailstore servers.
-
The Chat access URL for this domain will be: https://domain1examplecom.chat1.mydomain.com. The FQDN domain1examplecom.chat1.mydomain.com must be resolvable by proxy and mailstore servers.
Notes:
-
DNS A record for domain1examplecom.chat1.mydomain.com should resolve to same IP as chat1.mydomain.com
Network & Firewall Configuration
-
Hostname registered in DNS for the Chat server.
-
Zimbra LDAP (or External LDAP or Active Directory, depending on your environment) hostname is resolvable by the Chat server.
-
The Chat server hostname and FQDN for realms (domains) must be resolvable by Zimbra servers.
-
Zimbra LDAP server allows 389 port access (or 636 port access if ldaps (LDAP over SSL) is used) from Chat server.
-
Zimbra Proxy server allows admin proxy port (9091 by default) access from Chat server and PostgreSQL server for Chat and PostgreSQL installation.
-
PostgreSQL server allows 5432 port access from Chat server only.
-
Chat server allows 443 port access from Zimbra proxy and mailstore servers only.
-
🔒 Security Requirements:
-
IMPORTANT: Restrict access to the Chat web application by blocking unauthorized machines. Chat web application must always be accessed through Zimbra web client. It MUST NOT be accessible from any machine except Zimbra proxy and mailstore servers.
-
If you want to make Chat web application accessible by administrator for management purpose, you must configure network access to allow the access from a specified machine only using iptables, firewalld, network firewall or any network access control module.
-
Restrict access to the PostgreSQL database by blocking unauthorized machines.
-
Install Zimbra Chat modules
-
Install ZCS 10.1.7 or later
-
Please proceed with the patch installation using wiki Zimbra Releases/10.1.0/patch installation - Zimbra :: Tech Center
-
-
Install chat modules on all mailstore servers:
zimbra-zimlet-chatandzimbra-zimlet-classic-chatcontains Chat modules for Modern UI and for Classic UI, respectively.
Ubuntu:
apt install zimbra-zimlet-chat
apt install zimbra-zimlet-classic-chat
RHEL:
yum install zimbra-zimlet-chat
yum install zimbra-zimlet-classic-chat
Common:
su - zimbra
zmmailboxdctl restartInstall Zimbra Chat server
SSL Certificate Requirements
A valid SSL certificate is required for the chat server to ensure secure HTTPS communication, allowing the Zimbra mailstore to access it correctly.
The installer supports three options: Commercial, Let’s Encrypt, and Self-Signed. You must select one of these options when prompted during installation.
Commercial Certificate:
-
Requires a valid SSL certificate to be pre-installed before running the Chat installer.
-
DNS registration is required for the Chat server.
-
Certificates must be deployed manually in the following locations:
-
Private Key:
/etc/ssl/private/zulip.key -
Certificate Chain:
/etc/ssl/certs/zulip.combined-chain.crt
-
-
The certificate must be able to verify the chat server’s hostname and all Fully Qualified Domain Names (FQDNs), e.g., chat1.mydomain.com, domain1examplecom.chat1.mydomain.com, etc.
Let’s Encrypt:
-
The Chat installer uses the
--certbotoption to automatically obtain and configure an SSL certificate. -
By selecting this option, you must agree to the Let’s Encrypt Subscriber Agreement when prompted by the installer. Please read the latest Let’s Encrypt Subscriber Agreement at Policy and Legal Repository
-
DNS registration is mandatory.
Self-Signed Certificate:
-
The Chat installer uses the
--self-signed-certoption to generate a self-signed certificate. -
Not recommended for production use.
Prepare data for installation
The following details are required for installation.
-
Zimbra Proxy Host: Hostname (FQDN) of Zimbra admin console proxy URL to send admin SOAP requests.
-
Zimbra Proxy Admin Port: The port for the Zimbra admin console proxy on the proxy server (typically
9071). -
Zulip Admin Email & Password: The email address and password of an existing administrator account in Zimbra. The email address will be used as an administrator on Zulip application as well.
-
Zimbra JWT Authentication Key: The value of
zimbraChatJwtSecretconfigured in Zimbra. -
Zimbra Web Client URLs: A comma-separated list of all accessible Zimbra web client URLs (e.g.,
https://web.mydomain.com,https://virtual_domain1.example.com). Do not add a trailing slash likehttps://web.mydomain.com/.
The installer will prompt you to choose an authentication source: Zimbra LDAP, External LDAP, or Active Directory (AD).
If LDAP Source is Zimbra LDAP:
-
Zimbra LDAP Host: Hostname of the Zimbra LDAP server. If you have multiple LDAP servers, choose one of them to use.
-
Zimbra LDAP Port: Port used by the Zimbra LDAP server.
-
Zimbra LDAP Password: Password for connecting to Zimbra LDAP.
-
Zimbra LDAP Protocol: Choose between
ldaporldaps.
If LDAP Source is External LDAP/AD:
-
External LDAP/AD Host: Hostname of the external LDAP or Active Directory server. If you have multiple LDAP/AD servers, choose one of them to use.
-
External LDAP/AD Port: Port used for LDAP/AD communication.
-
External LDAP/AD Password: External LDAP or Active Directory server password for authentication.
-
External LDAP/AD Protocol: Choose between
ldaporldaps. -
External LDAP/AD Auth Bind DN: Distinguished Name (DN) for authentication.
-
External LDAP/AD Email Attribute: The LDAP/AD attribute storing the user’s email address.
-
External LDAP/AD Full Name Attribute: The LDAP/AD attribute storing the user’s full name.
Deployment Modes
Single-node Setup
Install Chat server application (Zulip) and PostgreSQL on a single server .
Multi-node Setup
Install Chat server application (Zulip) and PostgreSQL on different nodes. There are two options for the order of installation.
Option 1: Install Zulip First, Then PostgreSQL
-
Install Standalone Zulip
-
When prompted:
Have you installed PostgreSQL on another VM, and is it ready for use? (yes/no)→ selectno
-
-
Install Standalone PostgreSQL
-
Reconfigure Standalone Zulip to connect with the Standalone PostgreSQL instance
-
When prompted again:
Have you installed PostgreSQL on another VM, and is it ready for use?→ selectyes
-
Option 2: Install PostgreSQL First, Then Zulip
-
Install Standalone PostgreSQL
-
Install Standalone Zulip
-
When prompted:
Have you installed PostgreSQL on another VM, and is it ready for use?→ selectyes -
Provide the details of the Standalone PostgreSQL server
-
Inputs required by installer
-
Zulip Service Type: Choose based on your deployment mode. Options: Standalone PostgreSQL, Standalone Zulip, Combined.
-
Zimbra Proxy Host: Hostname (FQDN) of Zimbra admin console proxy URL.
-
Zimbra Proxy Admin Port: Admin console proxy port on the Zimbra proxy server (typically 9071).
-
Zulip Admin Email & Password: Credentials of an existing administrator account in Zimbra.
-
Zulip/Chat Server Hostname: Fully Qualified Domain Name (FQDN) of the Zulip/Chat server.
-
Chat Server SSL Certificate Type: Choose based on your requirement. Options: commercial, letsencrypt, self-signed.
-
LDAP/AD Source: Select as per your environment. Options: Zimbra LDAP, External LDAP, AD.
-
Zimbra JWT Authentication Key: The value of
zimbraChatJwtSecretconfigured in Zimbra. -
Zimbra Web Client URLs: One or more Zimbra client URLs (comma-separated), e.g.,
https://web.mydomain.com,https://virtual_domain1.example.com. -
Zulip Server IP: Private IP address of the Zulip server, used by PostgreSQL to recognize the connection source.
-
PostgreSQL Host: Hostname or IP address of the PostgreSQL server.
-
PostgreSQL Port: Port number of the PostgreSQL service (typically 5432).
-
PostgreSQL Password: Password to be set for the zulip user in the PostgreSQL database.
-
PostgreSQL Version: The version number of the PostgreSQL server. Retrieve the PostgreSQL version from the
/etc/zulip/zulip.conffile from PostgreSQL Server. -
PostgreSQL SSL Mode: SSL mode for connecting to PostgreSQL.
-
For more details refer: 32.19. SSL Support
-
Install Zulip and PostgreSQL on a single server
| If you are upgrading from Zimbra Daffodil version 10.1.7 to 10.1.8 - Refer to the Upgrade Guide → Update Customizations section. |
If you are upgrading from Chat 9.2 to 10.2 - Refer to the Upgrade → Upgrade Chat section.
-
Download the Chat Installer .tgz from the link below. Kindly verify the SHA256 and MD5 checksums as well.
https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz.md5 https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz.sha256 -
Switch to the
rootuser. -
Extract the archive:
tar xf zfzi-2.0.0.tgz cd zfzi-2.0.0 ./install.pl -
The installer will prompt you to enter the
Zulip Service Type(Standalone PostgreSQL,Standalone Zulip,Combined), chooseCombined.[2025-04-04 04:14:53] [INFO] Logging initialized. Operations will be logged to /etc/zulip-installer/log/zulip.install.log.20250404_041453 [2025-04-04 04:14:53] [INFO] Detected OS: ubuntu:24.04, Architecture: x86_64. Proceeding. [2025-04-04 04:14:53] [INFO] All required commands are already installed. Enter Zulip Service Type (Available: Standalone PostgreSQL, Standalone Zulip, Combined): Combined -
The installer will prompt you to provide the
Zimbra Proxy Host,Zimbra Proxy Admin Port,Zulip Admin Email, andZulip Admin Email Account Password. Please enter your inputs accordingly.Enter Zimbra Proxy Host: zimbra.com Enter Zimbra Proxy Admin Port: 9071 Enter Zulip Admin Email: admin@domain1.example.com Enter Zulip Admin Email Account Password: PASSWORD -
The installer will then verify connectivity to the Zimbra Proxy Host and validate the license using the information you provided.
[2025-04-04 04:15:13] [INFO] Checking connectivity to zimbra.com:9071 [2025-04-04 04:15:13] [INFO] Connected to zimbra.com:9071. [2025-04-04 04:15:13] [INFO] Fetching Zimbra admin authentication token... [2025-04-04 04:15:13] [INFO] Admin Auth Token fetched. [2025-04-04 04:15:13] [INFO] Fetching Zimbra license information. [2025-04-04 04:15:13] [INFO] License information retrieved. [2025-04-04 04:15:13] [INFO] Chat services are supported by the existing Zimbra license. -
The installer will prompt you to enter the
Chat Server Hostname.Enter Chat Server Hostname: chat1.mydomain.com [2025-04-04 04:15:20] [INFO] Checking resolution for hostname: chat1.mydomain.com [2025-04-04 04:15:20] [WARN] Hostname 'chat1.mydomain.com' is not resolvable via DNS. Checking /etc/hosts. [2025-04-04 04:15:20] [INFO] Hostname 'chat1.mydomain.com' found in /etc/hosts. Proceeding. -
The installer will prompt you to enter the Chat Server SSL Certificate Type`,
LDAP/AD Source,Zimbra JWT Auth Key,URLs of Zimbra web client. Please enter your inputs accordingly.Enter Chat Server SSL Certificate Type (commercial, letsencrypt, self-signed): letsencrypt Enter LDAP/AD Source (Zimbra LDAP, External LDAP, AD): Zimbra LDAP Enter Zimbra JWT Auth Key: SECRET_KEY Enter URLs of Zimbra web client (comma-separated if multiple): https://zimbra.com -
If you selected
letsencryptas theChat Server SSL Certificate Type, the installer will prompt you to accept the Let’s Encrypt Subscriber Agreement. You must agree to proceed with the installation.Please read the latest Let's Encrypt Subscriber Agreement at: https://letsencrypt.org/repository/#let-s-encrypt-subscriber-agreement You must agree in order to register with the ACME server. You must agree to the Let's Encrypt Subscriber Agreement to proceed. Do you agree? (yes/no): yes -
If you selected
letsencryptorcommercialas the Chat Server SSL Certificate Type, the installer will check whether the Chat Server Hostname is publicly resolvable.[2025-04-04 04:14:32] [INFO] Let’s Encrypt certificate selected. DNS registration is mandatory for Chat Server Hostname. [2025-04-04 04:14:33] [INFO] Chat Server Hostname is publicly resolvable. -
The installer will prompt for LDAP details based on the LDAP/AD Source you specified. Please provide the requested information accordingly. If you have multiple LDAP servers, choose one of them to use.
Enter Zimbra LDAP Host: zimbra.com Enter Zimbra LDAP Port: 389 Enter Zimbra LDAP Password: LDAP_PASSWORD Enter Zimbra LDAP Protocol (ldap/ldaps): ldap -
The installer will check connectivity to the LDAP server and prompt you to confirm whether to proceed. You must enter
yesto continue with the installation.[2025-04-04 04:15:50] [INFO] Checking connectivity to ldap server at zimbra.com:389 [2025-04-04 04:15:50] [INFO] Connected to ldap server at zimbra.com:389 [2025-04-04 04:15:50] [INFO] Package already exists: /etc/zulip-installer/package/zulip-server-10.2.tar.gz [2025-04-04 04:15:50] [INFO] The following configuration will be used: [2025-04-04 04:15:50] [INFO] Zulip service type: Combined [2025-04-04 04:15:50] [INFO] Zulip/Chat server hostname: chat1.mydomain.com [2025-04-04 04:15:50] [INFO] Chat server SSL certificate type: letsencrypt [2025-04-04 04:15:50] [INFO] Zulip admin email: admin@domain1.example.com [2025-04-04 04:15:50] [INFO] LDAP/AD Source: Zimbra LDAP [2025-04-04 04:15:50] [INFO] URL's of Zimbra web client: https://web.mydomain.com The system will be modified - continue? (yes/no): yes -
The installation process will begin and may take some time to complete. Please wait while the setup finishes.
-
The installation output will look like the following (it may vary depending on the inputs provided):
[2025-04-04 04:14:53] [INFO] Logging initialized. Operations will be logged to /etc/zulip-installer/log/zulip.install.log.20250404_041453 [2025-04-04 04:14:53] [INFO] Detected OS: ubuntu:24.04, Architecture: x86_64. Proceeding. [2025-04-04 04:14:53] [INFO] All required commands are already installed. Enter Zulip Service Type (Available: Standalone PostgreSQL, Standalone Zulip, Combined): Combined Enter Zimbra Proxy Host: zimbra.com Enter Zimbra Proxy Admin Port: 9071 Enter Zulip Admin Email: admin@domain1.example.com Enter Zulip Admin Email Account Password: PASSWORD [2025-04-04 04:15:13] [INFO] Checking connectivity to zimbra.com:9071 [2025-04-04 04:15:13] [INFO] Connected to zimbra.com:9071. [2025-04-04 04:15:13] [INFO] Fetching Zimbra admin authentication token... [2025-04-04 04:15:13] [INFO] Admin Auth Token fetched. [2025-04-04 04:15:13] [INFO] Fetching Zimbra license information. [2025-04-04 04:15:13] [INFO] License information retrieved. [2025-04-04 04:15:13] [INFO] Chat services are supported by the existing Zimbra license. Enter Chat Server Hostname: chat1.mydomain.com [2025-04-04 04:15:20] [INFO] Checking resolution for hostname: chat1.mydomain.com [2025-04-04 04:15:20] [WARN] Hostname 'chat1.mydomain.com' is not resolvable via DNS. Checking /etc/hosts. [2025-04-04 04:15:20] [INFO] Hostname 'chat1.mydomain.com' found in /etc/hosts. Proceeding. Enter Chat Server SSL Certificate Type (commercial, letsencrypt, self-signed): letsencrypt Enter LDAP/AD Source (Zimbra LDAP, External LDAP, AD): Zimbra LDAP Enter Zimbra JWT Auth Key: SECRET_KEY Enter URLs of Zimbra web client (comma-separated if multiple): https://web.mydomain.com Please read the latest Let's Encrypt Subscriber Agreement at: https://letsencrypt.org/repository/#let-s-encrypt-subscriber-agreement You must agree in order to register with the ACME server. You must agree to the Let's Encrypt Subscriber Agreement to proceed. Do you agree? (yes/no): yes [2025-04-04 04:14:32] [INFO] Let’s Encrypt certificate selected. DNS registration is mandatory for Chat Server Hostname. [2025-04-04 04:14:33] [INFO] Chat Server Hostname is publicly resolvable. Enter Zimbra LDAP Host: zimbra.com Enter Zimbra LDAP Port: 389 Enter Zimbra LDAP Password: LDAP_PASSWORD Enter Zimbra LDAP Protocol (ldap/ldaps): ldap [2025-04-04 04:15:50] [INFO] Checking connectivity to ldap server at zimbra.com:389 [2025-04-04 04:15:50] [INFO] Connected to ldap server at zimbra.com:389 [2025-04-04 04:15:50] [INFO] Package already exists: /etc/zulip-installer/package/zulip-server-10.2.tar.gz [2025-04-04 04:15:50] [INFO] The following configuration will be used: [2025-04-04 04:15:50] [INFO] Zulip service type: Combined [2025-04-04 04:15:50] [INFO] Zulip/Chat server hostname: chat1.mydomain.com [2025-04-04 04:15:50] [INFO] Chat server SSL certificate type: letsencrypt [2025-04-04 04:15:50] [INFO] Zulip admin email: admin@domain1.example.com [2025-04-04 04:15:50] [INFO] LDAP/AD Source: Zimbra LDAP [2025-04-04 04:15:50] [INFO] URL's of Zimbra web client: https://web.mydomain.com The system will be modified - continue? (yes/no): yes [2025-04-03 06:47:51] [INFO] Saving user inputs to config file: /etc/zulip-installer/config/config.20250403_064751 [2025-04-03 06:47:51] [INFO] User inputs saved to config file. [2025-04-03 06:47:51] [INFO] Starting: Adding universe repository. Please wait. [2025-04-03 06:48:00] [INFO] Completed: Adding universe repository [2025-04-03 06:48:00] [INFO] Starting: Updating package lists. Please wait. [2025-04-03 06:48:02] [INFO] Completed: Updating package lists [2025-04-03 06:48:02] [INFO] Starting: Extracting Zulip package. Please wait. [2025-04-03 06:48:03] [INFO] Completed: Extracting Zulip package [2025-04-03 06:48:03] [INFO] Starting: Zulip and PostgreSQL installation. Please wait. [2025-04-03 06:48:52] [INFO] Zulip and PostgreSQL installation is still in progress [2025-04-03 06:49:22] [INFO] Zulip and PostgreSQL installation is still in progress [2025-04-03 07:30:28] [INFO] Completed: Zulip and PostgreSQL installation [2025-04-03 07:30:28] [INFO] Package downloaded: /etc/zulip-installer/package/chat-customizations-10.2.tar.gz [2025-04-03 07:30:28] [INFO] Applying Zulip customizations... [2025-04-03 07:30:29] [INFO] Zulip customizations applied successfully. [2025-04-03 07:30:29] [INFO] Updated /etc/zulip/settings.py. [2025-04-03 07:30:29] [INFO] Updated /etc/zulip/zulip-secrets.conf. [2025-04-03 07:30:29] [INFO] Restarting nginx.service... [2025-04-03 07:30:29] [INFO] Starting: Restarting nginx.service. Please wait. [2025-04-03 07:30:29] [INFO] Completed: Restarting nginx.service [2025-04-03 07:30:29] [INFO] Restarting zulip... [2025-04-03 07:30:29] [INFO] Starting: Restarting zulip. Please wait. [2025-04-03 07:31:06] [INFO] Completed: Restarting zulip ! IMPORTANT: Admins should ensure that databases are on a private network and not publicly accessible! ! IMPORTANT: Admins should ensure that zimbra mailstore servers can resolve the Chat server hostname and access Chat server on 443 port! ! IMPORTANT: Please visit admin guide to proceed to realm setup Configuration complete
Install Standalone Zulip
-
Download the Chat Installer .tgz from the link below. Kindly verify the SHA256 and MD5 checksums as well.
https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz.md5 https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz.sha256 -
Switch to the
rootuser. -
Extract the archive:
tar xf zfzi-2.0.0.tgz cd zfzi-2.0.0 ./install.pl -
The installer will prompt you to enter the
Zulip Service Type(Standalone PostgreSQL,Standalone Zulip,Combined), chooseStandalone Zulip.[2025-04-02 09:20:48] [INFO] Logging initialized. Operations will be logged to /etc/zulip-installer/log/zulip.install.log.20250402_092048 [2025-04-02 09:20:48] [INFO] Detected OS: ubuntu:24.04, Architecture: aarch64. Proceeding. [2025-04-02 09:20:48] [INFO] All required commands are already installed. Enter Zulip Service Type (Available: Standalone PostgreSQL, Standalone Zulip, Combined): Standalone Zulip -
The installer will prompt you to provide the
Zimbra Proxy Host,Zimbra Proxy Admin Port,Zulip Admin Email, andZulip Admin Email Account Password. Please enter your inputs accordingly.Enter Zimbra Proxy Host: zimbra.com Enter Zimbra Proxy Admin Port: 9071 Enter Zulip Admin Email: admin@domain1.example.com Enter Zulip Admin Email Account Password: PASSWORD -
The installer will then verify connectivity to the
Zimbra Proxy Hostand validate the license using the information you provided.[2025-04-02 09:21:09] [INFO] Checking connectivity to zimbra.com:9071 [2025-04-02 09:21:09] [INFO] Connected to zimbra.com:9071. [2025-04-02 09:21:09] [INFO] Fetching Zimbra admin authentication token... [2025-04-02 09:21:09] [INFO] Admin Auth Token fetched. [2025-04-02 09:21:09] [INFO] Fetching Zimbra license information. [2025-04-02 09:21:09] [INFO] License information retrieved. [2025-04-02 09:21:09] [INFO] Chat services are supported by the existing Zimbra license. -
The installer will prompt you to enter the
Chat Server Hostname.Enter Chat Server Hostname: chat1.mydomain.com [2025-04-04 04:15:20] [INFO] Checking resolution for hostname: chat1.mydomain.com [2025-04-04 04:15:20] [WARN] Hostname 'chat1.mydomain.com' is not resolvable via DNS. Checking /etc/hosts. [2025-04-04 04:15:20] [INFO] Hostname 'chat1.mydomain.com' found in /etc/hosts. Proceeding. -
The installer will prompt you to enter the
Chat Server SSL,Certificate Type,LDAP/AD Source,Zimbra JWT Auth Key,URLs of Zimbra web client. Please enter your inputs accordingly.Enter Chat Server SSL Certificate Type (commercial, letsencrypt, self-signed): letsencrypt Enter LDAP/AD Source (Zimbra LDAP, External LDAP, AD): Zimbra LDAP Enter Zimbra JWT Auth Key: SECRET_KEY Enter URLs of Zimbra web client (comma-separated if multiple): https://web.mydomain.com -
If you selected
letsencryptas theChat Server SSL Certificate Type, the installer will prompt you to accept the Let’s Encrypt Subscriber Agreement. You must agree to proceed with the installation.Please read the latest Let's Encrypt Subscriber Agreement at: https://letsencrypt.org/repository/#let-s-encrypt-subscriber-agreement You must agree in order to register with the ACME server. You must agree to the Let's Encrypt Subscriber Agreement to proceed. Do you agree? (yes/no): yes -
If you selected
letsencryptorcommercialas theChat Server SSL Certificate Type, the installer will check whether the Chat Server Hostname is publicly resolvable.[2025-04-02 09:21:20] [INFO] Let’s Encrypt certificate selected. DNS registration is mandatory for Chat Server Hostname. [2025-04-02 09:21:21] [INFO] Chat Server Hostname is publicly resolvable. -
The installer will prompt for LDAP details based on the
LDAP/AD Sourceyou specified. Please provide the requested information accordingly. If you have multiple LDAP servers, choose one of them to use.Enter Zimbra LDAP Host: zimbra.com Enter Zimbra LDAP Port: 389 Enter Zimbra LDAP Password: LDAP_PASSWORD Enter Zimbra LDAP Protocol (ldap/ldaps): ldap -
The installer will check connectivity to the LDAP server.
[2025-04-02 09:21:51] [INFO] Checking connectivity to ldap server at zimbra.com:389 [2025-04-02 09:21:51] [INFO] Connected to ldap server at zimbra.com:389 [2025-04-02 09:21:51] [INFO] Creating package directory: /etc/zulip-installer/package [2025-04-02 09:21:52] [INFO] Package downloaded: /etc/zulip-installer/package/zulip-server-10.2.tar.gz -
The installer will ask,
Have you installed PostgreSQL on another VM, and is it ready for use? (yes/no). You should answerno, as we’re first installing Standalone Zulip and the standalone PostgreSQL setup is not yet complete.Have you installed PostgreSQL on another VM, and is it ready for use? (yes/no): no ! IMPORTANT: Once the current installation is complete, install and configure Remote PostgreSQL. Then, rerun the script with option `--use-remote-db` to finish setup. -
The installer will prompt with "The system will be modified - continue? (yes/no):". You need to enter
yesto proceed with the installation.[2025-04-02 09:21:54] [INFO] The following configuration will be used: [2025-04-02 09:21:54] [INFO] Zulip service type: Standalone Zulip [2025-04-02 09:21:54] [INFO] Zulip/Chat server hostname: chat1.mydomain.com [2025-04-02 09:21:54] [INFO] Chat server SSL certificate type: letsencrypt [2025-04-02 09:21:54] [INFO] Zulip admin email: admin@domain1.example.com [2025-04-02 09:21:54] [INFO] LDAP/AD Source: Zimbra LDAP [2025-04-02 09:21:54] [INFO] URL's of Zimbra web client: https://web.mydomain.com The system will be modified - continue? (yes/no): yes -
The installation process will begin and may take some time to complete. Please wait while the setup finishes.
-
The installation output will look like the following (it may vary depending on the inputs provided):
[2025-04-02 09:20:48] [INFO] Logging initialized. Operations will be logged to /etc/zulip-installer/log/zulip.install.log.20250402_092048 [2025-04-02 09:20:48] [INFO] Detected OS: ubuntu:24.04, Architecture: aarch64. Proceeding. [2025-04-02 09:20:48] [INFO] All required commands are already installed. Enter Zulip Service Type (Available: Standalone PostgreSQL, Standalone Zulip, Combined): Standalone Zulip Enter Zimbra Proxy Host: zimbra.com Enter Zimbra Proxy Admin Port: 9071 Enter Zulip Admin Email: admin@domain1.example.com Enter Zulip Admin Email Account Password: [2025-04-02 09:21:09] [INFO] Checking connectivity to zimbra.com:9071 [2025-04-02 09:21:09] [INFO] Connected to zimbra.com:9071. [2025-04-02 09:21:09] [INFO] Fetching Zimbra admin authentication token... [2025-04-02 09:21:09] [INFO] Admin Auth Token fetched. [2025-04-02 09:21:09] [INFO] Fetching Zimbra license information. [2025-04-02 09:21:09] [INFO] License information retrieved. [2025-04-02 09:21:09] [INFO] Chat services are supported by the existing Zimbra license. Enter Chat Server Hostname: chat1.mydomain.com [2025-04-02 09:21:19] [INFO] Checking resolution for hostname: chat1.mydomain.com [2025-04-02 09:21:19] [WARN] Hostname 'chat1.mydomain.com' is not resolvable via DNS. Checking /etc/hosts. [2025-04-02 09:21:19] [INFO] Hostname 'chat1.mydomain.com' found in /etc/hosts. Proceeding. Enter Chat Server SSL Certificate Type (commercial, letsencrypt, self-signed): letsencrypt Enter LDAP/AD Source (Zimbra LDAP, External LDAP, AD): Zimbra LDAP Enter Zimbra JWT Auth Key: SECRET_KEY Enter URLs of Zimbra web client (comma-separated if multiple): https://web.mydomain.com Please read the latest Let's Encrypt Subscriber Agreement at: https://letsencrypt.org/repository/#let-s-encrypt-subscriber-agreement You must agree in order to register with the ACME server. You must agree to the Let's Encrypt Subscriber Agreement to proceed. Do you agree? (yes/no): yes [2025-04-02 09:21:20] [INFO] Let’s Encrypt certificate selected. DNS registration is mandatory for Chat Server Hostname. [2025-04-02 09:21:21] [INFO] Chat Server Hostname is publicly resolvable. Enter Zimbra LDAP Host: zimbra.com Enter Zimbra LDAP Port: 389 Enter Zimbra LDAP Password: Enter Zimbra LDAP Protocol (ldap/ldaps): ldap [2025-04-02 09:21:51] [INFO] Checking connectivity to ldap server at zimbra.com:389 [2025-04-02 09:21:51] [INFO] Connected to ldap server at zimbra.com:389 [2025-04-02 09:21:51] [INFO] Creating package directory: /etc/zulip-installer/package [2025-04-02 09:21:52] [INFO] Package downloaded: /etc/zulip-installer/package/zulip-server-10.2.tar.gz Have you installed PostgreSQL on another VM, and is it ready for use? (yes/no): no ! IMPORTANT: Once the current installation is complete, install and configure Remote PostgreSQL. Then, rerun the script with option `--use-remote-db` to finish setup. [2025-04-02 09:21:54] [INFO] The following configuration will be used: [2025-04-02 09:21:54] [INFO] Zulip service type: Standalone Zulip [2025-04-02 09:21:54] [INFO] Zulip/Chat server hostname: chat1.mydomain.com [2025-04-02 09:21:54] [INFO] Chat server SSL certificate type: letsencrypt [2025-04-02 09:21:54] [INFO] Zulip admin email: admin@domain1.example.com [2025-04-02 09:21:54] [INFO] LDAP/AD Source: Zimbra LDAP [2025-04-02 09:21:54] [INFO] URL's of Zimbra web client: https://web.mydomain.com The system will be modified - continue? (yes/no): yes [2025-04-02 09:21:56] [INFO] Saving user inputs to config file: /etc/zulip-installer/config/config.20250402_092156 [2025-04-02 09:21:56] [INFO] User inputs saved to config file. [2025-04-02 09:21:56] [INFO] Starting: Adding universe repository. Please wait. [2025-04-02 09:22:01] [INFO] Completed: Adding universe repository [2025-04-02 09:22:01] [INFO] Starting: Updating package lists. Please wait. [2025-04-02 09:22:03] [INFO] Completed: Updating package lists [2025-04-02 09:22:03] [INFO] Starting: Extracting Zulip package. Please wait. [2025-04-02 09:22:05] [INFO] Completed: Extracting Zulip package [2025-04-02 09:22:05] [INFO] Starting: Standalone Zulip installation. Please wait. [2025-04-02 09:28:27] [INFO] Standalone Zulip installation is still in progress [2025-04-02 09:28:57] [INFO] Standalone Zulip installation is still in progress [2025-04-02 09:29:27] [INFO] Standalone Zulip installation is still in progress [2025-04-02 09:42:41] [INFO] Completed: Standalone Zulip installation [2025-04-02 09:42:41] [INFO] Package downloaded: /etc/zulip-installer/package/chat-customizations-10.2.tar.gz [2025-04-02 09:42:41] [INFO] Applying Zulip customizations... [2025-04-02 09:42:42] [INFO] Zulip customizations applied successfully. [2025-04-02 09:42:42] [INFO] Updated /etc/zulip/settings.py. [2025-04-02 09:42:42] [INFO] Updated /etc/zulip/zulip-secrets.conf. [2025-04-02 09:42:42] [INFO] Restarting nginx.service... [2025-04-02 09:42:42] [INFO] Starting: Restarting nginx.service. Please wait. [2025-04-02 09:42:43] [INFO] Completed: Restarting nginx.service ! IMPORTANT: Admins should ensure that zimbra mailstore servers can resolve the Chat server hostname and access Chat server on 443 port! ! IMPORTANT: Please visit admin guide to proceed to realm setup
Install Standalone PostgreSQL
-
Download the Chat Installer
.tgzfrom the link below. Kindly verify the SHA256 and MD5 checksums as well.https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz.md5 https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz.sha256 -
Switch to the
rootuser. -
Extract the archive:
tar xf zfzi-2.0.0.tgz cd zfzi-2.0.0 ./install.pl -
The installer will prompt you to enter the
Zulip Service Type(Standalone PostgreSQL,Standalone Zulip,Combined), chooseStandalone PostgreSQL.[2025-03-23 17:04:57] [INFO] Logging initialized. Operations will be logged to /etc/zulip-installer/log/zulip.install.log.20250323_170457 [2025-03-23 17:04:57] [INFO] Detected OS: ubuntu:22.04, Architecture: aarch64. Proceeding... [2025-03-23 17:04:57] [INFO] All required commands are already installed. Enter Zulip Service Type (Available: Standalone PostgreSQL, Standalone Zulip, Combined) : Standalone PostgreSQL -
The installer will prompt you to provide the
Zimbra Proxy Host,Zimbra Proxy Admin Port,Zulip Admin Email, andZulip Admin Email Account Password. Please enter your inputs accordingly.Enter Zimbra Proxy Host: zimbra.com Enter Zimbra Proxy Admin Port: 9071 Enter Zulip Admin Email: admin@domain1.example.com Enter Zulip Admin Email Account Password: PASSWORD -
The installer will then verify connectivity to the
Zimbra Proxy Hostand validate the license using the information you provided.[2025-03-23 17:05:01] [INFO] Checking connectivity to zimbra.com:9071... [2025-03-23 17:05:01] [INFO] Successfully connected to zimbra.com:9071. [2025-03-23 17:05:01] [INFO] Fetching Zimbra admin authentication token... [2025-03-23 17:05:01] [INFO] Admin Auth Token fetched successfully. [2025-03-23 17:05:01] [INFO] Fetching Zimbra license information... [2025-03-23 17:05:01] [INFO] License information retrieved successfully. [2025-03-23 17:05:01] [INFO] Chat services are supported by the existing Zimbra license. -
The installer will prompt you to enter the Zulip server IP that will be visible when connected to the PostgreSQL instance, as well as the PostgreSQL server password to set for the zulip user. Please provide these details accordingly.
Enter Zulip server IP visible when connected to this PostgreSQL instance : IP_ADDRESS Enter PostgreSQL server password to set for the zulip user: ZULIP_USER_PASSWORD -
The installer will display:
The system will be modified - continue? (yes/no):Enteryesto proceed.[2025-03-23 17:05:10] [INFO] Package downloaded : /etc/zulip-installer/package/zulip-server-10.2.tar.gz [2025-03-23 17:05:11] [INFO] The following configuration will be used: [2025-03-23 17:05:11] [INFO] Zulip server ip: IP_ADDRESS [2025-03-23 17:05:11] [INFO] Zulip service type: Standalone PostgreSQL The system will be modified - continue? (yes/no): yes -
The installation process will begin and may take some time to complete. Please wait while the setup finishes.
-
The installation output will look like the following (it may vary depending on the inputs provided):
[2025-03-23 17:04:57] [INFO] Logging initialized. Operations will be logged to /etc/zulip-installer/log/zulip.install.log.20250323_170457 [2025-03-23 17:04:57] [INFO] Detected OS: ubuntu:22.04, Architecture: aarch64. Proceeding... [2025-03-23 17:04:57] [INFO] All required commands are already installed. Enter Zulip Service Type (Available: Standalone PostgreSQL, Standalone Zulip, Combined) : Standalone PostgreSQL Enter Zimbra Proxy Host : zimbra.com Enter Zimbra Proxy Admin Port : 9071 Enter Zulip Admin Email: admin@domain1.example.com Enter Zimbra Admin Account Password: PASSWORD [2025-03-23 17:05:01] [INFO] Checking connectivity to zimbra.com:9071... [2025-03-23 17:05:01] [INFO] Successfully connected to zimbra.com:9071. [2025-03-23 17:05:01] [INFO] Fetching Zimbra admin authentication token... [2025-03-23 17:05:01] [INFO] Admin Auth Token fetched successfully. [2025-03-23 17:05:01] [INFO] Fetching Zimbra license information... [2025-03-23 17:05:01] [INFO] License information retrieved successfully. [2025-03-23 17:05:01] [INFO] Chat services are supported by the existing Zimbra license. Enter Zulip server IP visible when connected to this PostgreSQL instance : IP_ADDRESS Enter PostgreSQL server password to set for the zulip user: ZULIP_USER_PASSWORD [2025-03-23 17:05:10] [INFO] Package downloaded : /etc/zulip-installer/package/zulip-server-10.2.tar.gz [2025-03-23 17:05:11] [INFO] The following configuration will be used: [2025-03-23 17:05:11] [INFO] Zulip server ip: IP_ADDRESS [2025-03-23 17:05:11] [INFO] Zulip service type: Standalone PostgreSQL The system will be modified - continue? (yes/no): yes [2025-03-23 17:05:14] [INFO] Saving user inputs to config file: /etc/zulip-installer/config/config.20250323_170514 [2025-03-23 17:05:14] [INFO] User inputs saved successfully to config file. [2025-03-23 17:05:14] [INFO] Starting: Adding universe repository [2025-03-23 17:05:21] [INFO] Completed: Adding universe repository [2025-03-23 17:05:21] [INFO] Starting: Updating package lists [2025-03-23 17:05:24] [INFO] Completed: Updating package lists [2025-03-23 17:05:24] [INFO] Removing existing extracted zulip directory: /tmp/zulip-server-10.2 [2025-03-23 17:05:24] [INFO] Starting: Removing old extracted zulip [2025-03-23 17:05:24] [INFO] Completed: Removing old extracted zulip [2025-03-23 17:05:25] [INFO] Starting: Extracting Zulip package [2025-03-23 17:05:26] [INFO] Completed: Extracting Zulip package [2025-03-23 17:05:26] [INFO] Starting: Running Standalone PostgreSQL installation [2025-03-23 17:05:35] [INFO] Completed: Running Standalone PostgreSQL installation [2025-03-23 17:05:35] [INFO] Starting: Running PostgreSQL create database [2025-03-23 17:05:35] [INFO] Completed: Running PostgreSQL create database [2025-03-23 17:05:35] [INFO] PostgreSQL create database completed. [2025-03-23 17:05:35] [INFO] Detected PostgreSQL version: 17 ! IMPORTANT: Added a rule to allow the `zulip` user to connect to the `zulip` database from 10.0.0.224 using scram-sha-256 authentication. ! IMPORTANT: If changes are needed to the PostgreSQL authentication configuration, please modify the /etc/postgresql/17/main/pg_hba.conf file. [2025-03-23 17:05:35] [INFO] Restarting postgresql.service... [2025-03-23 17:05:38] [INFO] postgresql.service restarted successfully. [2025-03-23 17:05:38] [INFO] Checking if PostgreSQL is accessible on host: localhost... [2025-03-23 17:05:38] [INFO] PostgreSQL is accessible on localhost. [2025-03-23 17:05:38] [INFO] Setting Zulip database user password... [2025-03-23 17:05:38] [INFO] Zulip database password set successfully. ! IMPORTANT: Admins should ensure that databases are on a private network and not publicly accessible! ! IMPORTANT: Admins should ensure that Chat server can access the PostgreSQL server on port 5432! Configuration complete
Configure Standalone Zulip Server with Standalone PostgreSQL
-
Return to Standalone Zulip Server
-
run
./install.pl --use-remote-dbto configure Standalone Zulip Server with Standalone PostgreSQL. -
The installer will prompt with
Have you installed PostgreSQL on another VM, and is it ready for use? (yes/no):. You should enteryes, as PostgreSQL has already been installed and is ready for use.[2025-03-26 11:41:05] [INFO] Logging initialized. Operations will be logged to /etc/zulip-installer/log/zulip.configure-remote-db.log.20250326_114105 [2025-03-26 11:41:05] [INFO] Detected OS: ubuntu:24.04, Architecture: x86_64. Proceeding. Have you installed PostgreSQL on another VM, and is it ready for use? (yes/no): yes -
The installer will prompt you to enter the PostgreSQL server details. Please provide the information accordingly.
Enter Name or IP address of the PostgreSQL server: POSTGRESQL_SERVER Enter PostgreSQL server port: 5432 Enter PostgreSQL server password for the zulip user: PASSWORD Enter PostgreSQL server version: 17 Enter desired SSL mode for the PostgreSQL connection (disable, allow, prefer, require, verify-ca, verify-full): require -
The installer will check whether the PostgreSQL server is accessible and proceed accordingly based on the result.
[2025-03-26 11:41:35] [INFO] Checking if PostgreSQL is accessible on host: . [2025-03-26 11:41:35] [INFO] PostgreSQL is accessible on . [2025-03-26 11:41:35] [INFO] Configuring Zulip to use remote PostgreSQL. [2025-03-26 11:41:35] [INFO] Updated /etc/zulip/settings.py with remote PostgreSQL details. [2025-03-26 11:41:35] [INFO] Updated /etc/zulip/zulip-secrets.conf with PostgreSQL password. [2025-03-26 11:41:35] [INFO] Updated /etc/zulip/zulip.conf with PostgreSQL version. [2025-03-26 11:41:36] [INFO] Configured Zulip for remote PostgreSQL. [2025-03-26 11:41:35] [INFO] Starting: Initializing the PostgreSQL database. Please wait. [2025-03-26 11:41:37] [INFO] Completed: Initializing the PostgreSQL database [2025-03-26 11:41:38] [INFO] Starting: Generating realm creation link. Please wait. [2025-03-26 11:41:39] [INFO] Completed: Generating realm creation link Configuration complete. -
The configuration output will look like the following (it may vary depending on the inputs provided):
[2025-03-26 11:41:05] [INFO] Logging initialized. Operations will be logged to /etc/zulip-installer/log/zulip.configure-remote-db.log.20250326_114105 [2025-03-26 11:41:05] [INFO] Detected OS: ubuntu:24.04, Architecture: x86_64. Proceeding. Have you installed PostgreSQL on another VM, and is it ready for use? (yes/no): yes Enter Name or IP address of the PostgreSQL server: POSTGRESQL_SERVER Enter PostgreSQL server port: 5432 Enter PostgreSQL server password for the zulip user: PASSWORD Enter PostgreSQL server version: 17 Enter desired SSL mode for the PostgreSQL connection (disable, allow, prefer, require, verify-ca, verify-full): require [2025-03-26 11:41:35] [INFO] Checking if PostgreSQL is accessible on host: . [2025-03-26 11:41:35] [INFO] PostgreSQL is accessible on . [2025-03-26 11:41:35] [INFO] Configuring Zulip to use remote PostgreSQL. [2025-03-26 11:41:35] [INFO] Updated /etc/zulip/settings.py with remote PostgreSQL details. [2025-03-26 11:41:35] [INFO] Updated /etc/zulip/zulip-secrets.conf with PostgreSQL password. [2025-03-26 11:41:35] [INFO] Updated /etc/zulip/zulip.conf with PostgreSQL version. [2025-03-26 11:41:36] [INFO] Configured Zulip for remote PostgreSQL. [2025-03-26 11:41:35] [INFO] Starting: Initializing the PostgreSQL database. Please wait. [2025-03-26 11:41:37] [INFO] Completed: Initializing the PostgreSQL database [2025-03-26 11:41:38] [INFO] Starting: Generating realm creation link. Please wait. [2025-03-26 11:41:39] [INFO] Completed: Generating realm creation link Configuration complete.
Configuration & Logging
-
User Inputs Storage:
/etc/zulip-installer/config/ -
Passwords are not stored in config, including:
-
Zulip Admin Password
-
PostgreSQL Password
-
LDAP/AD Password
-
-
Log Files Locations:
-
Installer Logs : /etc/zulip-installer/log/
-
Zulip Logs : /var/log/zulip/
-
PostgreSQL Logs : /var/log/postgresql/
-
Installation using config file
The installer supports non-interactive mode via a specified configuration file.
Use the following command to install using a specific configuration file in non-interactive mode:
./install.pl --config=<file>
All configuration keys must be defined in the config file according to the requirements of the selected service type.
Config file keys descriptions
-
ZULIP_SERVICE_TYPE: Type of Zulip service to install. Options:
Standalone PostgreSQL,Standalone Zulip, orCombined. -
ZIMBRA_PROXY_HOST: Hostname (FQDN) of Zimbra admin console proxy URL.
-
ZIMBRA_PROXY_ADMIN_PORT: Admin console proxy port on the Zimbra proxy server (typically
9071). -
ZIMBRA_JWT_AUTH_KEY: The
zimbraChatJwtSecretvalue configured in your Zimbra environment. -
CSRF_TRUSTED_ORIGINS: Comma-separated list of all accessible Zimbra web client URLs (e.g., https://web.mydomain.com, https://virtual_domain1.example.com).
-
ZULIP_ADMIN_EMAIL: Email address of an existing administrator in Zimbra.
-
ZULIP_ADMIN_PASSWORD: Password of the above admin account in Zimbra.
-
ZULIP_SERVER_IP: Private IP address of the Zulip server, used by PostgreSQL to allow trusted connections.
-
CHAT_SERVER_HOSTNAME: Fully Qualified Domain Name (FQDN) of the Zulip/Chat server.
-
SSL_CERT_TYPE: SSL certificate type. Options:
commercial,letsencrypt,self-signed. -
LETS_ENCRYPT_AGREEMENT: Must be set to
yesifSSL_CERT_TYPEis letsencrypt. Indicates agreement to the Let’s Encrypt Subscriber Agreement. -
LDAP_AD_SOURCE: Directory source for user authentication. Options:
Zimbra LDAP,External LDAP, orAD. -
ZIMBRA_LDAP_HOST: Hostname of the Zimbra LDAP server. If you have multiple LDAP servers, choose one of them to use.
-
ZIMBRA_LDAP_PORT: Port used to connect to the Zimbra LDAP server.
-
ZIMBRA_LDAP_PASSWORD: Password used for Zimbra LDAP authentication.
-
ZIMBRA_LDAP_PROTOCOL: Protocol for Zimbra LDAP connection. Options:
ldap,ldaps. -
EXTERNAL_LDAP_HOST: Hostname of the external LDAP or Active Directory server. If you have multiple LDAP/AD servers, choose one of them to use.
-
EXTERNAL_LDAP_PORT: Port used by the external LDAP/AD server.
-
EXTERNAL_LDAP_PASSWORD: Password for connecting to the external LDAP/AD server.
-
AUTH_LDAP_BIND_DN: Distinguished Name (DN) used for LDAP/AD binding.
-
LDAP_EMAIL_ATTRIBUTE: Attribute name that holds the user’s email in LDAP/AD.
-
LDAP_FULLNAME_ATTRIBUTE: Attribute name that holds the user’s full name in LDAP/AD.
-
EXTERNAL_LDAP_PROTOCOL: Protocol used for external LDAP/AD. Options: ldap, ldaps.
-
REMOTE_POSTGRES_READY:
yesorno. Indicates whether PostgreSQL is already installed and ready on another VM. -
POSTGRES_HOST: Hostname or IP address of the remote PostgreSQL server.
-
POSTGRES_PORT: Port on which PostgreSQL is running (typically
5432). -
POSTGRES_VERSION: Version of the PostgreSQL server. Can be retrieved from
/etc/zulip/zulip.confon the PostgreSQL host. -
POSTGRES_PASSWORD: Password to assign for the Zulip user in the PostgreSQL database.
-
POSTGRES_SSL_MODE: SSL mode to use when connecting to PostgreSQL.
-
For more details refer official PostgreSQL docs: SSL modes - SSL Modes.
-
Config File Examples
Combined (Zulip + PostgreSQL)
ZULIP_SERVICE_TYPE=Combined
ZIMBRA_PROXY_HOST=
ZIMBRA_PROXY_ADMIN_PORT=
ZULIP_ADMIN_EMAIL=
ZULIP_ADMIN_PASSWORD=
CHAT_SERVER_HOSTNAME=
SSL_CERT_TYPE=commercial/letsencrypt/self-signed
ZIMBRA_JWT_AUTH_KEY=
CSRF_TRUSTED_ORIGINS=
LDAP_AD_SOURCE=Zimbra LDAP / External LDAP / ADIf SSL_CERT_TYPE=letsencrypt, include:
LETS_ENCRYPT_AGREEMENT=yesIf LDAP_AD_SOURCE=Zimbra LDAP, include:
ZIMBRA_LDAP_HOST=
ZIMBRA_LDAP_PORT=
ZIMBRA_LDAP_PASSWORD=
ZIMBRA_LDAP_PROTOCOL=If LDAP_AD_SOURCE=External LDAP / AD, include:
EXTERNAL_LDAP_HOST=
EXTERNAL_LDAP_PORT=
EXTERNAL_LDAP_PASSWORD=
AUTH_LDAP_BIND_DN=
LDAP_EMAIL_ATTRIBUTE=
LDAP_FULLNAME_ATTRIBUTE=
EXTERNAL_LDAP_PROTOCOL=Standalone PostgreSQL
ZULIP_SERVICE_TYPE=Standalone PostgreSQL
ZIMBRA_PROXY_HOST=
ZIMBRA_PROXY_ADMIN_PORT=
ZULIP_ADMIN_EMAIL=
ZULIP_ADMIN_PASSWORD=
ZULIP_SERVER_IP=
POSTGRES_PASSWORD=Standalone Zulip
ZULIP_SERVICE_TYPE=Standalone Zulip
ZIMBRA_PROXY_HOST=
ZIMBRA_PROXY_ADMIN_PORT=
ZULIP_ADMIN_EMAIL=
ZULIP_ADMIN_PASSWORD=
CHAT_SERVER_HOSTNAME=
SSL_CERT_TYPE=commercial/letsencrypt/self-signed
ZIMBRA_JWT_AUTH_KEY=
CSRF_TRUSTED_ORIGINS=
LDAP_AD_SOURCE=Zimbra LDAP / External LDAP / ADIf SSL_CERT_TYPE=letsencrypt, include:
LETS_ENCRYPT_AGREEMENT=yesIf LDAP_AD_SOURCE=Zimbra LDAP, include:
ZIMBRA_LDAP_HOST=
ZIMBRA_LDAP_PORT=
ZIMBRA_LDAP_PASSWORD=
ZIMBRA_LDAP_PROTOCOL=If LDAP_AD_SOURCE=External LDAP / AD, include:
EXTERNAL_LDAP_HOST=
EXTERNAL_LDAP_PORT=
EXTERNAL_LDAP_PASSWORD=
AUTH_LDAP_BIND_DN=
LDAP_EMAIL_ATTRIBUTE=
LDAP_FULLNAME_ATTRIBUTE=
EXTERNAL_LDAP_PROTOCOL=For remote PostgreSQL support, set:
REMOTE_POSTGRES_READY=yes/noIf REMOTE_POSTGRES_READY=yes, include:
POSTGRES_HOST=
POSTGRES_PORT=
POSTGRES_PASSWORD=
POSTGRES_VERSION=
POSTGRES_SSL_MODE=Configure Standalone Zulip Server with Standalone PostgreSQL
Run the installer with --use-remote-db and config file:
./install.pl --use-remote-db --config=<file>Including the following in the config:
REMOTE_POSTGRES_READY=yes
POSTGRES_HOST=
POSTGRES_PORT=
POSTGRES_PASSWORD=
POSTGRES_VERSION=
POSTGRES_SSL_MODE=Configure Chat server
Major settings are defined in /etc/zulip/settings.py on Chat server. It is configured during the installation.
Configuration for authentication
If you face an issue on user authentication, check the following settings:
## Specify URI
## If port number is not 389, specify port number as well.
## If ldap over ssl is used, replace "ldap://" with "ldaps://"
AUTH_LDAP_SERVER_URI = "ldap://LDAP_HOST(:PORT)"
## Set a right BIND DN on your environment
AUTH_LDAP_BIND_DN = "uid=zimbra,cn=admins,cn=zimbra"
## Configure user search query
## Specify right objectClass(es) to search user accounts only.
AUTH_LDAP_USER_SEARCH = LDAPSearch(
"", ldap.SCOPE_SUBTREE, "(&(mail=%(user)s)(objectClass=zimbraAccount))"
)
## Specify an attribute which stores user's email address
LDAP_EMAIL_ATTR = "mail"
AUTH_LDAP_USERNAME_ATTR = "mail"
## Specify the same objectClass(es) in search query as AUTH_LDAP_USER_SEARCH
## Note that "%(email)s" is used here. AUTH_LDAP_USER_SEARCH uses "%(user)s".
AUTH_LDAP_REVERSE_EMAIL_SEARCH = LDAPSearch("",
ldap.SCOPE_SUBTREE, "(&(mail=%(email)s)(objectClass=zimbraAccount))")
## Specify an attribute which stores user's full name
AUTH_LDAP_USER_ATTR_MAP = {
"full_name": "cn",
...
}Only a single ldap server can be set in AUTH_LDAP_SERVER_URI. If Multi-Master Replication (MMR) is configured on your ldap servers, you can choose one of them for AUTH_LDAP_SERVER_URI.
Passwords are stored in /etc/zulip/zulip-secrets.conf. It is configured during the installation.
## Zimbra LDAP Password specified at installation
## It must be the same as zimbra_ldap_password in localconfig. (i.e. "zmlocalconfig -s zimbra_ldap_password")
auth_ldap_bind_password = LDAP_BIND_PASSWORD
## Zimbra JWT Auth Key specified at installation
zimbra_jwt_auth_key = RANDOM_STRING_SECRET_KEYYou can confirm that the Chat server can search an account on the ldap. Make sure that both full_name and email are returned.
manage.py is a command to manage various items on the Chat server. query_ldap is one of options and sends ldap search query to a ldap server specified in AUTH_LDAP_SERVER_URI.
(Run as zulip on Chat server)
$ /home/zulip/deployments/current/manage.py query_ldap user1@mydomain.com
...
full_name: user1
email: user1@mydomain.comIf settings.py or zulip-secrets.conf is modified, Chat server application needs to be restarted.
(Run as zulip on Chat server)
$ /home/zulip/deployments/current/scripts/restart-server|
Note :If your ldap server uses a self-signed certificate, LDAP access from Chat server will fail because of an untrusted certificate. To resolve this issue, a commercial certificate should be deployed on ldap servers. If obtaining a commercial certificate is not feasible, you can disable certificate verification using the following setting. However, it is insecure. It is not recommended on production. |
|
Warning: Please make sure permission 640 (or 600) is set. Please consider to plan to change If you install a Chat server with Chat Server SSL Certificate Type: Self-signed, Zimbra mailstore server cannot communicate with the Chat server because of an untrusted certificate. To resolve this issue, you need to set ssl_allow_untrusted_certs to false on all mailstore servers so that each mailstore server does not check SSL certificate. However, it will affect not only on communication with Chat server but also all communication initiated from the mailstore server. It will cause security issue. Do not apply it on production. |
Configuration to allow access from Zimbra web client
CSRF_TRUSTED_ORIGINS in /etc/zulip/settings.py must include all Zimbra web client URLs.
## URLs of Zimbra web client specified at installation.
## If virtual hostname is used on Zimbra for domain(s), all access urls need to be listed.
## If access by IP address URL is allowed, it needs to be added as well.
(example 1)
CSRF_TRUSTED_ORIGINS = ["https://web.mydomain.com"]
(example 2)
CSRF_TRUSTED_ORIGINS = ["https://web.mydomain.com", "https://virtual_domain1.example.com", "https://10.0.0.2"]If it is modified, Chat server application needs to be restarted.
(Run as zulip on Chat server)
$ /home/zulip/deployments/current/scripts/restart-serverConfiguration for external LDAP and Active Directory
Here are examples of configuration for external LDAP and Active Directory.
External LDAP
## Replace values of the following keys.
## Specify URI
AUTH_LDAP_SERVER_URI = "ldap://YOUR_EXTERNAL_LDAP_HOST"
## If port number is not 389, specify port number as well.
## If ldap over ssl is used, replace "ldap://" with "ldaps://"
AUTH_LDAP_SERVER_URI = "ldap://YOUR_EXTERNAL_LDAP_HOST:12345"
## Replace BIND DN to a right one on your environment
AUTH_LDAP_BIND_DN = "uid=zimbra,cn=admins,cn=zimbra"
## Configure user search query
## Specify right objectClass(es), depending on your ldap structure
AUTH_LDAP_USER_SEARCH = LDAPSearch(
"", ldap.SCOPE_SUBTREE, "(&(mail=%(user)s)(objectClass=zimbraAccount))"
)
## Specify an attribute which stores user's email address
LDAP_EMAIL_ATTR = "mail"
AUTH_LDAP_USERNAME_ATTR = "mail"
## Specify the same objectClass(es) in search query as AUTH_LDAP_USER_SEARCH
## Note that "%(email)s" is used here. AUTH_LDAP_USER_SEARCH specifies "%(user)s".
AUTH_LDAP_REVERSE_EMAIL_SEARCH = LDAPSearch("",
ldap.SCOPE_SUBTREE, "(&(mail=%(email)s)(objectClass=zimbraAccount))")
## Specify an attribute which stores user's full name
AUTH_LDAP_USER_ATTR_MAP = {
"full_name": "cn",
...
}It is similar to external LDAP configuration on Zimbra. For more details refer: LDAP Authentication - Zimbra :: Tech Center
Active Directory
## Replace values of the following keys.
## Specify URI
AUTH_LDAP_SERVER_URI = "ldap://YOUR_AD_HOST:PORT"
## Replace BIND DN to a right one on your environment
## If "Administrator" is an account to access your AD,
AUTH_LDAP_BIND_DN = "Administrator"
## Configure user search query
## Replace "mail" with an attribute which stores user's email address
## Specify right objectClass(es), depending on your directory structure
AUTH_LDAP_USER_SEARCH = LDAPSearch(
"", ldap.SCOPE_SUBTREE, "(&(objectclass=organizationalPerson)(objectclass=person)(objectclass=user)(mail=%(user)s))"
)
## Specify an attribute which stores user's email address
LDAP_EMAIL_ATTR = "mail"
AUTH_LDAP_USERNAME_ATTR = "mail"
# Note that "%(email)s" is used here. AUTH_LDAP_USER_SEARCH specifies "%(user)s".
# To access by Active Directory email address
AUTH_LDAP_REVERSE_EMAIL_SEARCH = LDAPSearch(
"", ldap.SCOPE_SUBTREE, "(mail=%(email)s)"
)
## Specify an attribute which stores user's full name
AUTH_LDAP_USER_ATTR_MAP = {
"full_name": "cn",
...
}For another example, if userPrincipalName has an email address of a user
AUTH_LDAP_USER_SEARCH = LDAPSearch(
"", ldap.SCOPE_SUBTREE, "(&(objectclass=organizationalPerson)(objectclass=person)(objectclass=user)(userPrincipalName=%(user)s))"
)
LDAP_EMAIL_ATTR = "userPrincipalName"
AUTH_LDAP_USERNAME_ATTR = "userPrincipalName"
AUTH_LDAP_REVERSE_EMAIL_SEARCH = LDAPSearch(
"", ldap.SCOPE_SUBTREE, "(mail=%(email)s)"
)It is similar to external Active Directory configuration on Zimbra. For more details refer: Configure authentication with Active Directory - Zimbra :: Tech Center
Common setting
Password for external LDAP or Active Directory access needs to be added to /etc/zulip/zulip-secrets.conf in the same way as using Zimbra LDAP.
auth_ldap_bind_password = LDAP_BIND_PASSWORDConfigure LDAP attributes
After you can confirm that the Chat server can search an account on the ldap, some ldap attributes need to be configured.
A value of zimbraChatJwtSecret must be the same as the one of zimbra_jwt_auth_key configured on Chat server.
(Run as zimbra on a Zimbra mailstore server)
$ zmprov mcf zimbraChatBaseHost chat1.mydomain.com
$ zmprov mcf zimbraChatJwtSecret RANDOM_STRING_SECRET_KEY
$ zmprov fc -a allIf you want to configure a different Chat server for domain(s), refer: (Optional) Multiple domains and multiple chat servers section.
Create a realm for an existing domain
-
A "realm" is an internal term of Chat server; it is corresponds to an individual Zimbra “domain”. This “realm” has a unique URL (a realm URL) that the proxy and mailstore servers use to communicate with Chat server. When you install the Chat server, you need to create manually realms for the domains which already exist on the Zimbra server. A realm for a domain created after the Chat server installation can be automatically propagated to the Chat server when the domain is created with
zimbraFeatureZulipChatEnabled TRUE. -
The format of a realm URL is
https://[zimbraZulipChatDomainId].[zimbraChatBaseHost]. zimbraChatBaseHostmust be set before a realm is created.zimbraZulipChatDomainIdis set during realm creation.zimbraZulipChatDomainIddoes not need to be set manually. For example, whenzimbraChatBaseHostischat1.mydomain.comandzimbraZulipChatDomainIdisdomain1example.comfor a domaindomain1.example.com, the realm URL for the domain ishttps://domain1examplecom.chat1.mydomain.com. Before realm creation, a hostname set inzimbraChatBaseHost(chat1.mydomain.comin this case) must be resolvable on proxy and mailstore servers, and a valid SSL certificate forchat1.mydomain.commust have been deployed on the Chat server. In addition, the FQDN of a realm URL (domain1examplecom.chat1.mydomain.comin this case) must be resolvable by proxy and mailstore servers. -
It may take some time to reflect a change on DNS.
-
As described in Administrator Guide → Network & Firewall Configuration, a realm URL must be accessible from Zimbra proxy and mailstore servers only. It must not be accessed by end users.
You can create a realm for an existing domain in the following steps:
-
Confirm zimbraChatBaseHost and zimbraChatJwtSecret have been configured on a domain
(Run as zimbra on a Zimbra mailstore server) zmprov gd DOMAIN zimbraChatBaseHost zimbraChatJwtSecret -
Confirm a FQDN of a creating realm URL can be resolved by proxy and mailstore servers
-
Create a realm for an existing domain
-
It is better to set a domain name removing dots (.) in @id for consistency.
(Run as zimbra on a Zimbra mailstore server) $ zmsoap -vv -z -type admin CreateChatRealmRequest @id="domain1examplecom" / domain="domain1.example.com" @by="name"
When a domain is created after Chat server is integrated, a realm can be created automatically on Chat server. zimbraFeatureZulipChatEnabled TRUE needs to be specified at domain creation.
(Run as zimbra on a Zimbra mailstore server) ## Realm is not created automatically $ zmprov cd DOMAIN ## Realm is created automatically $ zmprov cd DOMAIN zimbraFeatureZulipChatEnabled TRUEA realm id (
zimbraZulipChatDomainId) will be a string which removes dots from a domain name. e.g.another.domain.example.net⇒anotherdomainexamplenetMake sure that a FQDN of a realm URL for new domain can be resolved by proxy and mailstore servers before a domain is created.
If multiple Chat servers are deployed (i.e. if
zimbraChatBaseHostandzimbraChatJwtSecrethave not been set in globalConfig),zimbraChatBaseHostandzimbraChatJwtSecretneed to be specified as well.## Realm is created automatically $ zmprov cd DOMAIN zimbraFeatureZulipChatEnabled TRUE zimbraChatBaseHost CHAT_HOSTNAME zimbraChatJwtSecret SECRET -
-
Confirm that
zimbraZulipChatDomainIdhas been set on the domain(Run as zimbra on a mailstore server) $ zmprov gd DOMAIN zimbraZulipChatDomainId zimbraZulipChatDomainId: domain1examplecom -
Confirm that a realm has been created on Chat server
(Run as zulip on Chat server) $ /home/zulip/deployments/current/manage.py list_realms id string_id name domain -- --------- ---- ------ ... N domain1examplecom domain1.example.com https://domain1examplecom.chat1.mydomain.com -
Run
proxyconfgencommand and reload proxy so that Zimbra proxy can forward a request to Zimbra Chat server with a right url.(Run as zimbra on all Zimbra proxy servers) $ /opt/zimbra/libexec/zmproxyconfgen $ zmproxyctl reload
If you see the following error message,
$ zmproxyctl reload
Reloading proxy...nginx: [emerg] could not build map_hash, you should increase map_hash_bucket_size: 64
done.configure the value of proxy_web_map_hash_bucket_size in localconfig (default: 64). Zimbra proxy needs to be restarted.
(Run as zimbra on all proxy servers)
$ zmlocalconfig -e proxy_web_map_hash_bucket_size=128
$ /opt/zimbra/libexec/zmproxyconfgen
$ zmproxyctl restart
The reason we need to set proxy_web_map_hash_bucket_size to 128 is because the length of domain+hash keys generated in chat configuration in nginx file exceeds 64 and the proxy restart fails.
|
If you see the following error message,
Reloading proxy...nginx: [emerg] host not found in upstream "domain1examplecom.chat1.mydomain.com:443" in /opt/zimbra/conf/nginx/includes/nginx.conf.chat.upstream:66
done.The proxy server cannot resolve the FQDN of a realm URL https://domain1examplecom.chat1.mydomain.com. You need to check DNS record, or refresh DNS cache on the server.
It may take some time to reflect a change on DNS. If it needs be fixed immediately, you can add an entry to /etc/hosts on the server as a workaround.
Provision accounts on the realm
For more details refer: Administrator Guide
-
Login to admin console
-
Go to Configure > Domain > the domain
-
Click “Provision all accounts” button
-
Click “Get accounts” button and confirm accounts have been deployed on Chat server
|
When an account is created after Chat server is integrated, a chat account is automatically created on Chat server.
Note: |
Enable Basic Chat
Modern Web Client - Zimbra Daffodil 10.1.7 version
-
Enable
zimbraFeatureZulipChatEnabledandzimbraFeatureBasicOneToOneChatEnabledat domain, COS or account level(Run as zimbra on a Zimbra mailstore server) (Example) $ zmprov mc default zimbraFeatureZulipChatEnabled TRUE zimbraFeatureBasicOneToOneChatEnabled TRUE -
Enable
zimbra-zimlet-chatzimlet in domain, COS or account level -
Login to an account on Modern Web Client. Basic Chat is shown at right side of the page (in sidebar).
-
For more details refer separate document: “User’s Guide For Modern Web App → Zimbra Chat”.
-
Classic Web Client - Zimbra Daffodil 10.1.8 onwards
-
Enable
zimbraFeatureZulipChatEnabledandzimbraFeatureBasicOneToOneChatEnabledat domain, COS or account level(Run as zimbra on a Zimbra mailstore server) (Example) $ zmprov mc default zimbraFeatureZulipChatEnabled TRUE zimbraFeatureBasicOneToOneChatEnabled TRUE -
Enable zimbra-zimlet-classic-chat zimlet in domain, COS or account level
-
Login to an account on Classic Web Client. Basic Chat is shown at right side of the page (in sidebar).
-
. For more details refer separate document: “User’s Guide For Modern Web App → Zimbra Chat”.
Enable Advanced Chat
Modern Web Client - Zimbra Daffodil 10.1.7 version
-
Enable
zimbraFeatureZulipChatEnabledandzimbraFeatureAdvancedChatEnabledat domain, COS or account level(Run as zimbra on a Zimbra mailstore server) (Example) $ zmprov mc default zimbraFeatureZulipChatEnabled TRUE zimbraFeatureAdvancedChatEnabled TRUE -
Enable
zimbra-zimlet-chatzimlet in domain, COS or account level -
Login to an account on Modern Web Client. Messaging icon is shown in Navigation bar at the top of the page.
-
For more details refer separate document: “User’s Guide For Modern Web App → Zimbra Chat”
-
Classic Web Client - Zimbra Daffodil 10.1.8 onwards
-
Enable
zimbraFeatureZulipChatEnabledandzimbraFeatureAdvancedChatEnabledat domain, COS or account level(Run as zimbra on a Zimbra mailstore server) (Example) $ zmprov mc default zimbraFeatureZulipChatEnabled TRUE zimbraFeatureAdvancedChatEnabled TRUE -
Enable zimlets -
zimbra-zimlet-classic-chatandzimbra-zimlet-chatfor domain, COS or account level. -
Login to an account on Classic Web Client. 'Advanced Chat' tab is shown in Navigation bar at the top of the page.
-
For more details refer separate document: “User’s Guide For Modern Web App → Zimbra Chat”
-
(Optional) Multiple domains and multiple chat servers
You can deploy multiple domains on a single Chat server or distribute multiple domains across different Chat servers. This can be configured using zimbraChatBaseHost
| A single domain cannot be deployed across multiple Chat servers. Each domain must be deployed on a specific Chat server. |
A Chat server can connect to a single LDAP server (AUTH_LDAP_SERVER_URI), which can support multiple domains. However, if any domain requires a different LDAP server for authentication, a separate Chat server must be set up for it.
|
(Run as zimbra on a Zimbra mailstore server)
## set globalConfig zimbraChatBaseHost to empty to avoid misconfiguration
$ zmprov mcf zimbraChatBaseHost ""
## set zimbraChatBaseHost per domain.
## In this case, domain1 and domain2 are hosted on chat1, and others on chat2.
$ zmprov md domain1.mydomain.com zimbraChatBaseHost chat1.mydomain.com
$ zmprov md domain2.mydomain.com zimbraChatBaseHost chat1.mydomain.com
$ zmprov md domain3.mydomain.com zimbraChatBaseHost chat2.mydomain.com
$ zmprov md domain4.mydomain.com zimbraChatBaseHost chat2.mydomain.com
$ zmprov fc -a allAs optional, zimbraChatJwtSecret can be configured per Chat server. (i.e. either the same or different values can be set.)
(Run as zimbra on a Zimbra mailstore server)
## set globalConfig `zimbraChatJwtSecret` to empty to avoid misconfiguration
$ zmprov mcf zimbraChatJwtSecret ""
## set a value for chat1 server
$ zmprov md domain1.mydomain.com zimbraChatJwtSecret tx4BhsK9aGmPzyqAQ66jawN
$ zmprov md domain2.mydomain.com zimbraChatJwtSecret tx4BhsK9aGmPzyqAQ66jawN
## set a value for chat2 server
$ zmprov md domain3.mydomain.com zimbraChatJwtSecret bH94LxpaaC12jkyTgnmMcqs
$ zmprov md domain4.mydomain.com zimbraChatJwtSecret bH94LxpaaC12jkyTgnmMcqs
$ zmprov fc -a all| For each Chat Server deployment repeat the steps from Installation Guide: From Install Chat server to Enable Basic Chat and/or Enable Advanced Chat. |
(Optional) Install and enable PGroonga for full-text search in non-English languages on Advanced Chat
PGroonga is a PostgreSQL extension to use Groonga as index. PGroonga makes PostgreSQL fast full text search platform for all languages.
All steps should be run as root on Chat server. It does not need to be executed on PostgreSQL server.
-
Alter the deployment setting
crudini --set /etc/zulip/zulip.conf machine pgroonga enabled -
Update the deployment to respect that new setting
/home/zulip/deployments/current/scripts/zulip-puppet-apply -
Add the following setting to
/etc/zulip/settings.pyUSING_PGROONGA = True -
Apply the PGroonga migrations. Note that the migration may take a long time, and users will be unable to send new messages until the migration finishes.
su zulip -c '/home/zulip/deployments/current/manage.py migrate pgroonga' -
Restart Zulip
su zulip -c '/home/zulip/deployments/current/scripts/restart-server'
If you see the error below at step 2, run apt update and then do the step 2 again.
# /home/zulip/deployments/current/scripts/zulip-puppet-apply
...
Get:1 http://iad-ad-1.clouds.archive.ubuntu.com/ubuntu jammy/universe amd64 libmsgpackc2 amd64 3.3.0-4 [15.1 kB]
Err:2 http://ppa.launchpad.net/groonga/ppa/ubuntu jammy/main amd64 libgroonga0 amd64 15.0.2-1.ubuntu22.04.1
404 Not Found [IP: 185.125.190.80 80]
Get:3 http://iad-ad-1.clouds.archive.ubuntu.com/ubuntu jammy/universe amd64 libsimdjson9 amd64 1.0.2-2 [68.6 kB]
Get:4 https://packages.groonga.org/ubuntu jammy/universe amd64 postgresql-16-pgdg-pgroonga amd64 4.0.1-1 [789 kB]
Fetched 873 kB in 3s (265 kB/s)
E: Failed to fetch http://ppa.launchpad.net/groonga/ppa/ubuntu/pool/main/g/groonga/libgroonga0_15.0.2-1.ubuntu22.04.1_amd64.deb 404 Not Found [IP: 185.125.190.80 80]
E: Unable to fetch some archives, maybe run apt-get update or try with --fix-missing?
Error: /Stage[main]/Zulip::Postgresql_base/Package[postgresql-16-pgdg-pgroonga]/ensure: change from 'purged' to 'latest' failed: Could not update: Execution of '/usr/bin/apt-get -q -y -o DPkg::Options::=--force-confold install postgresql-16-pgdg-pgroonga' returned 100: Reading package lists...
...Upgrade Guide
Upgrade Chat
To upgrade Chat from version 9.2 to 10.2, follow the steps outlined below.
It is strongly recommended to take a backup of Zulip and PostgreSQL before starting the upgrade. For assistance, refer to the documentation: Backups, export and import — Zulip 10.2 documentation
The installer automatically checks whether an upgrade is required for Zulip, PostgreSQL, or both. The administrator is required to confirm each component upgrade as recommended. Partial upgrades, such as upgrading only Zulip or only PostgreSQL are not supported and will cause the upgrade process to be aborted.
Upgrade Zulip and PostgreSQL on a single server
-
Download the Chat Installer
.tgzfrom the link below. Kindly verify the SHA256 and MD5 checksums as well.https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz.md5 https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz.sha256 -
Switch to the
rootuser. -
Extract the archive:
tar xf zfzi-2.0.0.tgz cd zfzi-2.0.0 ./install.pl -
You’ll be prompted to enter the following, please provide your inputs accordingly.
Have you taken a backup of what you intend to upgrade? (yes/no): Do you want to proceed with the Zulip upgrade? (yes/no): Do you want to proceed with the PostgreSQL upgrade? (yes/no): -
The upgrade process will begin and may take some time to complete. Please wait while the setup finishes.
-
The upgrade output will look like the following (it may vary depending on the inputs provided):
[2025-06-05 06:01:04] [INFO] Logging initialized. Operations will be logged to /etc/zulip-installer/log/zulip.install.log.20250605_060104 [2025-06-05 06:01:04] [INFO] Detected OS: ubuntu:22.04, Architecture: x86_64. Proceeding. [2025-06-05 06:01:04] [INFO] All required commands are already installed. [2025-06-05 06:01:04] [INFO] The server has been identified as running both Zulip and PostgreSQL. [2025-06-05 06:01:04] [INFO] Upgrading the following components: [2025-06-05 06:01:04] [INFO] Zulip will be upgraded from 9.2 to 10.2 [2025-06-05 06:01:04] [INFO] PostgreSQL will be upgraded from 16 to 17 ! IMPORTANT: This appears to be an upgrade. Please ensure you have taken a backup of everything you intend to upgrade before proceeding. Have you taken a backup of what you intend to upgrade? (yes/no): yes Do you want to proceed with the Zulip upgrade? (yes/no): yes Do you want to proceed with the PostgreSQL upgrade? (yes/no): yes [2025-06-05 06:01:26] [INFO] Package downloaded: /etc/zulip-installer/package/zulip-server-10.2.tar.gz [2025-06-05 06:01:27] [INFO] Starting: Running Zulip upgrade. Please wait. [2025-06-05 06:01:30] [INFO] Running Zulip upgrade is still in progress [2025-06-05 06:01:40] [INFO] Running Zulip upgrade is still in progress [2025-06-05 06:01:41] [INFO] Completed: Running Zulip upgrade [2025-06-05 06:01:41] [INFO] Package downloaded: /etc/zulip-installer/package/chat-customizations-10.2.0.tar.gz [2025-06-05 06:01:41] [INFO] Applying Zulip customizations during upgrade... [2025-06-05 06:01:41] [INFO] Taking backup of existing chat customizations to /etc/zulip-installer/backup/chat-customizations/9.2_20250605_060532 [2025-06-05 06:01:41] [INFO] Zulip customizations applied successfully. [2025-06-05 06:05:31] [INFO] Updated /etc/zulip/settings-new.py. ! IMPORTANT: A new settings file has been generated at /etc/zulip/settings-new.py. ! IMPORTANT: You must manually compare /etc/zulip/settings-new.py with the existing /etc/zulip/settings.py. ! IMPORTANT: Back up the existing /etc/zulip/settings.py file. ! IMPORTANT: Apply necessary changes to /etc/zulip/settings-new.py based on comparison and rename it to /etc/zulip/settings.py ! IMPORTANT: This step is required to complete the upgrade. ! IMPORTANT: After updating the settings, restart the Zulip server using below command su zulip -c '/home/zulip/deployments/current/scripts/restart-server' [2025-06-05 06:05:31] [INFO] Restarting nginx.service... [2025-06-05 06:05:33] [INFO] Starting: Restarting nginx.service. Please wait. [2025-06-05 06:05:33] [INFO] Completed: Restarting nginx.service [2025-06-05 06:05:33] [INFO] Restarting zulip... [2025-06-05 06:05:35] [INFO] Starting: Restarting zulip. Please wait. [2025-06-05 06:05:37] [INFO] Completed: Restarting zulip Zulip upgrade finished [2025-06-05 06:06:16] [INFO] Package already exists: /etc/zulip-installer/package/zulip-server-10.2.tar.gz [2025-06-05 06:06:17] [INFO] Starting: Extracting package. Please wait. [2025-06-05 06:06:19] [INFO] Completed: Extracting package [2025-06-05 06:06:19] [INFO] Starting: Stopping services. Please wait. [2025-06-05 06:06:21] [INFO] Completed: Stopping services [2025-06-05 06:06:21] [INFO] Starting: Running PostgreSQL upgrade. Please wait. [2025-06-05 06:07:19] [INFO] Completed: Running PostgreSQL upgrade [2025-06-05 06:07:19] [INFO] Starting: Starting services. Please wait. [2025-06-05 06:07:49] [INFO] Completed: Starting services PostgreSQL upgrade finished -
Update
settings.pyafter upgrade - The installer outputs these instructions during the upgrade process, but they are reiterated here to ensure proper configuration ofsettings.py.
! IMPORTANT: A new settings file has been generated at /etc/zulip/settings-new.py.
! IMPORTANT: You must manually compare /etc/zulip/settings-new.py with the existing /etc/zulip/settings.py.
! IMPORTANT: Back up the existing /etc/zulip/settings.py file.
! IMPORTANT: Apply necessary changes to /etc/zulip/settings-new.py based on comparison and rename it to /etc/zulip/settings.py
! IMPORTANT: This step is required to complete the upgrade.
! IMPORTANT: After updating the settings, restart the Zulip server using below command
su zulip -c '/home/zulip/deployments/current/scripts/restart-server'Upgrade Standalone Zulip
-
Download the Chat Installer .tgz from the link below. Kindly verify the SHA256 and MD5 checksums as well.
https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz.md5 https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz.sha256 -
Switch to the
rootuser. -
Extract the archive:
tar xf zfzi-2.0.0.tgz cd zfzi-2.0.0 ./install.pl -
You’ll be prompted to enter the following, please provide your inputs accordingly.
Have you taken a backup of what you intend to upgrade? (yes/no): Do you want to proceed with the Zulip upgrade? (yes/no): -
The upgrade process will begin and may take some time to complete. Please wait while the setup finishes.
-
The upgrade output will look like the following (it may vary depending on the inputs provided):
[2025-06-08 04:23:59] [INFO] Logging initialized. Operations will be logged to /etc/zulip-installer/log/zulip.install.log.20250608_042359 [2025-06-08 04:23:59] [INFO] Detected OS: ubuntu:22.04, Architecture: x86_64. Proceeding. [2025-06-08 04:23:59] [INFO] All required commands are already installed. [2025-06-08 04:23:59] [INFO] The server has been identified as a standalone Zulip instance. [2025-06-08 04:23:59] [INFO] Upgrading the following components: [2025-06-08 04:23:59] [INFO] Zulip will be upgraded from 9.2 to 10.2 ! IMPORTANT: This appears to be an upgrade. Please ensure you have taken a backup of everything you intend to upgrade before proceeding. Have you taken a backup of what you intend to upgrade? (yes/no): yes Do you want to proceed with the Zulip upgrade? (yes/no): yes [2025-06-08 04:24:08] [INFO] Package downloaded: /etc/zulip-installer/package/zulip-server-10.2.tar.gz [2025-06-08 04:24:08] [INFO] Starting: Running Zulip upgrade. Please wait. [2025-06-08 04:25:24] [INFO] Running Zulip upgrade is still in progress [2025-06-08 04:25:54] [INFO] Running Zulip upgrade is still in progress [2025-06-08 04:28:08] [INFO] Completed: Running Zulip upgrade [2025-06-08 04:28:09] [INFO] Package downloaded: /etc/zulip-installer/package/chat-customizations-10.2.0.tar.gz [2025-06-08 04:28:09] [INFO] Applying Zulip customizations during upgrade... [2025-06-08 04:28:09] [INFO] Taking backup of existing chat customizations to /etc/zulip-installer/backup/chat-customizations/9.2_20250608_042809 [2025-06-08 04:28:12] [INFO] Zulip customizations applied successfully. [2025-06-08 04:28:13] [INFO] Updated /etc/zulip/zulip.conf with PostgreSQL version. [2025-06-08 04:28:13] [INFO] Updated /etc/zulip/settings-new.py ! IMPORTANT: A new settings file has been generated at /etc/zulip/settings-new.py. ! IMPORTANT: You must manually compare /etc/zulip/settings-new.py with the existing /etc/zulip/settings.py. ! IMPORTANT: Back up the existing /etc/zulip/settings.py file. ! IMPORTANT: Apply necessary changes to /etc/zulip/settings-new.py based on comparison and rename it to /etc/zulip/settings.py ! IMPORTANT: This step is required to complete the upgrade. ! IMPORTANT: After updating the settings, restart the Zulip server using below command su zulip -c '/home/zulip/deployments/current/scripts/restart-server' [2025-06-08 04:28:13] [INFO] Restarting nginx.service... [2025-06-08 04:28:13] [INFO] Starting: Restarting nginx.service. Please wait. [2025-06-08 04:28:18] [INFO] Completed: Restarting nginx.service [2025-06-08 04:28:18] [INFO] Restarting zulip... [2025-06-08 04:28:18] [INFO] Starting: Restarting zulip. Please wait. [2025-06-08 04:28:31] [INFO] Completed: Restarting zulip Zulip upgrade finished -
Update
settings.pyafter upgrade - The installer outputs these instructions during the upgrade process, but they are reiterated here to ensure proper configuration ofsettings.py.
! IMPORTANT: A new settings file has been generated at /etc/zulip/settings-new.py.
! IMPORTANT: You must manually compare /etc/zulip/settings-new.py with the existing /etc/zulip/settings.py.
! IMPORTANT: Back up the existing /etc/zulip/settings.py file.
! IMPORTANT: Apply necessary changes to /etc/zulip/settings-new.py based on comparison and rename it to /etc/zulip/settings.py
! IMPORTANT: This step is required to complete the upgrade.
! IMPORTANT: After updating the settings, restart the Zulip server using below command
su zulip -c '/home/zulip/deployments/current/scripts/restart-server'Upgrade Standalone PostgreSQL
Prior to upgrading Standalone PostgreSQL, ensure the Standalone Zulip server is stopped by executing the following command as the zulip user: /home/zulip/deployments/current/scripts/stop-server
-
Download the Chat Installer
.tgzfrom the link below. Kindly verify the SHA256 and MD5 checksums as well.https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz.md5 https://files.zimbra.com/downloads/zfzi/2.0.0/zfzi-2.0.0.tgz.sha256 -
Switch to the
rootuser. -
Extract the archive:
tar xf zfzi-2.0.0.tgz cd zfzi-2.0.0 ./install.pl -
You’ll be prompted to enter the following, please provide your inputs accordingly.
Have you taken a backup of what you intend to upgrade? (yes/no): Do you want to proceed with the PostgreSQL upgrade? (yes/no): -
The upgrade process will begin and may take some time to complete. Please wait while the setup finishes.
-
The upgrade output will look like the following (it may vary depending on the inputs provided):
[2025-06-08 04:44:46] [INFO] Logging initialized. Operations will be logged to /etc/zulip-installer/log/zulip.install.log.20250608_044446 [2025-06-08 04:44:46] [INFO] Detected OS: ubuntu:22.04, Architecture: x86_64. Proceeding. [2025-06-08 04:44:46] [INFO] All required commands are already installed. [2025-06-08 04:44:46] [INFO] The server has been identified as a standalone PostgreSQL instance. [2025-06-08 04:44:46] [INFO] Upgrading the following components: [2025-06-08 04:44:46] [INFO] PostgreSQL will be upgraded from 16 to 17 ! IMPORTANT: This appears to be an upgrade. Please ensure you have taken a backup of everything you intend to upgrade before proceeding. Have you taken a backup of what you intend to upgrade? (yes/no): yes Do you want to proceed with the PostgreSQL upgrade? (yes/no): yes [2025-06-08 04:44:55] [INFO] Package downloaded: /etc/zulip-installer/package/zulip-server-10.2.tar.gz [2025-06-08 04:44:55] [INFO] Starting: Extracting package. Please wait. [2025-06-08 04:44:56] [INFO] Completed: Extracting package [2025-06-08 04:44:56] [INFO] Starting: Running PostgreSQL upgrade. Please wait. [2025-06-08 04:45:19] [INFO] Completed: Running PostgreSQL upgrade PostgreSQL upgrade finished -
After completing the standalone PostgreSQL upgrade, switch back to the Standalone Zulip server and start it as the
zulipuser using the following command:/home/zulip/deployments/current/scripts/start-server
Upgrade using config file
The installer supports non-interactive mode via a specified configuration file.
Use the following command to install using a specific configuration file in non-interactive mode:
./install.pl --config=<file>
All configuration keys must be defined in the config file according to the requirements of the selected service type.
Config file keys descriptions
CONFIRM_BACKUP_DONE: yes or no . Confirms whether a backup has been completed prior to proceeding with the upgrade.
CONFIRM_ZULIP_UPGRADE: yes or no. Confirms whether the user wants to proceed with upgrading Zulip.
CONFIRM_DB_UPGRADE: yes or no. Confirms whether the user wants to proceed with upgrading Database.
CONFIRM_REINSTALL: yes or no . Confirms whether reinstallation should be performed. Reinstallation is generally not recommended as it may break the existing system. This option is provided to prevent accidental reinstallation if the user runs the installer again.
Config File Examples for Upgrade
Combined (Zulip + PostgreSQL) upgrade
CONFIRM_BACKUP_DONE=yes
CONFIRM_ZULIP_UPGRADE=yes
CONFIRM_DB_UPGRADE=yesStandalone Zulip upgrade
CONFIRM_BACKUP_DONE=yes
CONFIRM_ZULIP_UPGRADE=yesStandalone PostgreSQL upgrade
CONFIRM_BACKUP_DONE=yes
CONFIRM_DB_UPGRADE=yesFor re-install
Reinstallation is generally not recommended as it may break the existing system.
CONFIRM_REINSTALL=yesUpdate Customizations
-
When upgrading from Zimbra Daffodil version 10.1.7 to 10.1.8 for Zimbra Chat update customizations as mentioned below.
-
This step is intended only for updating existing customizations on the Chat server node.
| Do not run this on the Standalone PostgreSQL node, it will not work and will throw an error. |
-
The latest customizations are included in
zfzi-1.0.1. -
If you have previously installed
zfzi-1.0.0and are upgrading Zimbra to version 10.1.8, you must update the chat customizations using this new release.-
Download the Chat Installer
.tgzfrom the link below. Kindly verify the SHA256 and MD5 checksums as well.https://files.zimbra.com/downloads/zfzi/1.0.1/zfzi-1.0.1.tgz https://files.zimbra.com/downloads/zfzi/1.0.1/zfzi-1.0.1.tgz.md5 https://files.zimbra.com/downloads/zfzi/1.0.1/zfzi-1.0.1.tgz.sha256 -
Switch to the
rootuser. -
Extract the archive and update customizations
tar xf zfzi-1.0.1.tgz cd zfzi-1.0.1 ./install.pl --update-customizations -
The update customizations output will look like the following
[2025-05-07 08:17:43] [INFO] Logging initialized. Operations will be logged to /etc/zulip-installer/log/zulip.update-customizations.log.20250507_081743 [2025-05-07 08:17:43] [INFO] Detected OS: ubuntu:22.04, Architecture: x86_64. Proceeding. [2025-05-07 08:17:43] [INFO] Detected installed Zulip version: 9.2 [2025-05-07 08:17:43] [INFO] Zulip environment verified successfully for updating customizations. [2025-05-07 08:17:43] [INFO] Package already exists: /etc/zulip-installer/package/chat-customizations-9.2.1.tar.gz [2025-05-07 08:17:43] [INFO] Updating existing Zulip customizations... [2025-05-07 08:17:43] [INFO] Taking backup of existing chat customizations to /etc/zulip-installer/backup/chat-customizations/9.2.1_20250507_081743 [2025-05-07 08:17:48] [INFO] Zulip customizations updated successfully. [2025-05-07 08:17:48] [INFO] Restarting zulip... [2025-05-07 08:17:48] [INFO] Starting: Restarting zulip. Please wait. [2025-05-07 08:18:22] [INFO] Completed: Restarting zulip Zulip customizations update finished. The Zulip server is now running with the new customizations -
Administrator Guide
Admin Console
An administrator can manage Chat-related configuration and accounts on a Chat server. For more details refer: FAQs section for a domain admin or delegated admin.
Account, COS and domain settings:
-
Enable chat: whether chat feature is enabled or not. If it is FALSE, basic one to one chat and advanced chat is regarded as disabled.
-
Enable basic one to one chat: whether basic chat is enabled or not.
-
Enable advanced chat: whether advanced chat is enabled or not.
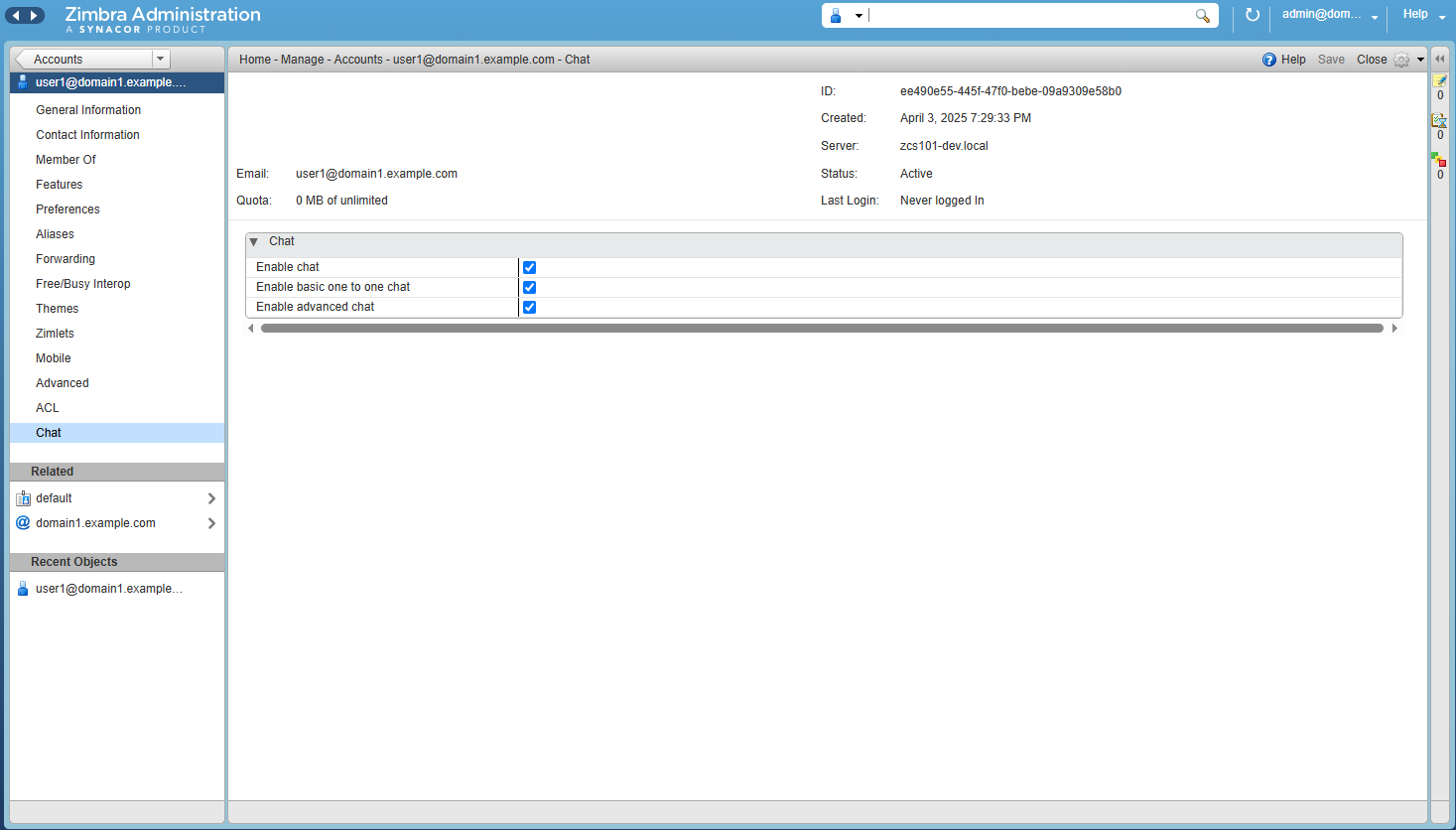
Chat accounts management in domain settings:
-
Get accounts: accounts created on a Chat server are shown in Activated accounts and Deactivated accounts field.
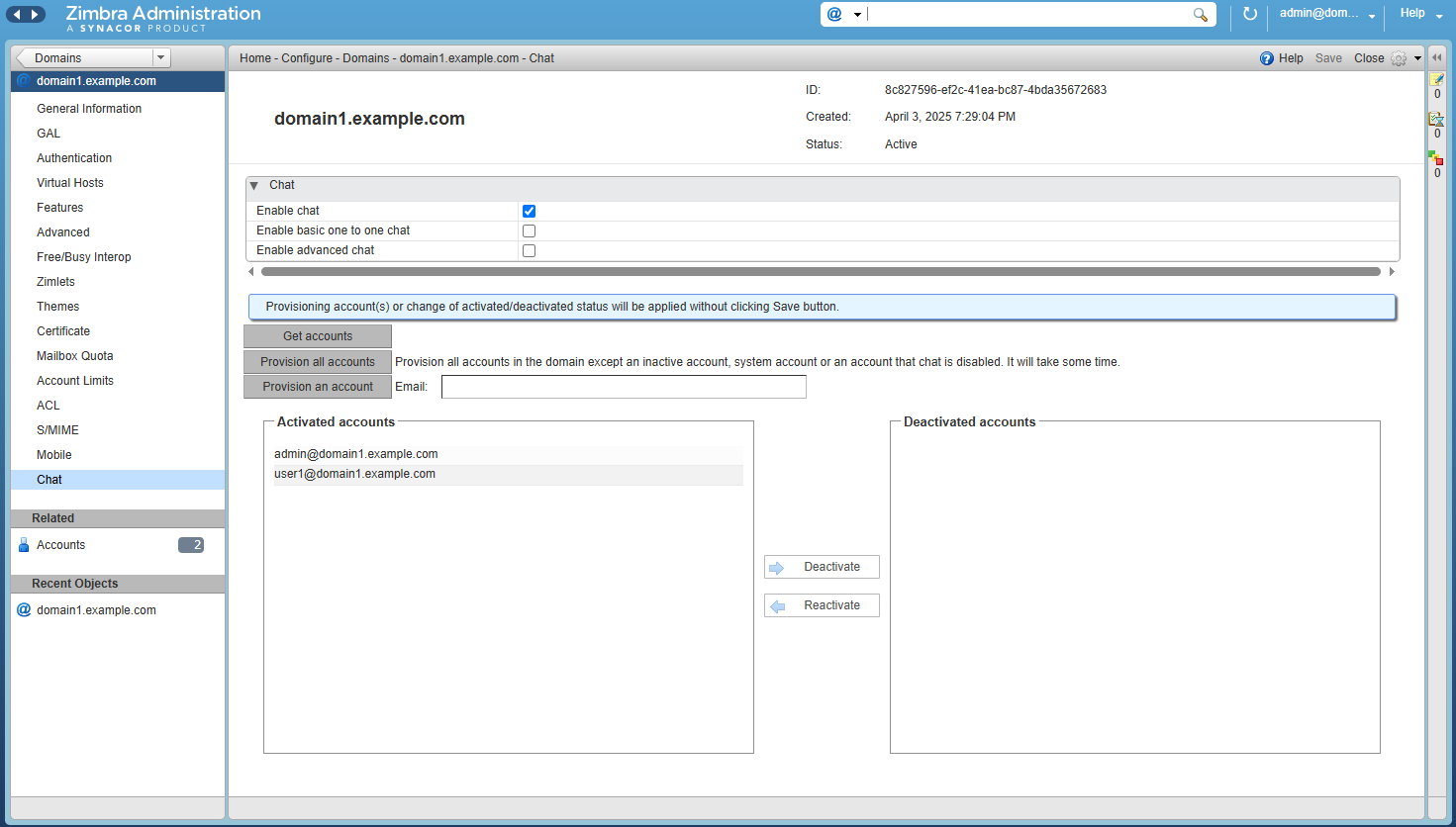
-
Deactivate/Reactivate: click an account in Activated accounts and click Deactivate, and then the user is deactivated. It can be reactivated by clicking an account in Deactivated accounts and click Reactivate.
| An account is deactivated on Chat server automatically when it is removed from Zimbra. |
For more details refer: FAQs section on how to remove an account from Chat server.
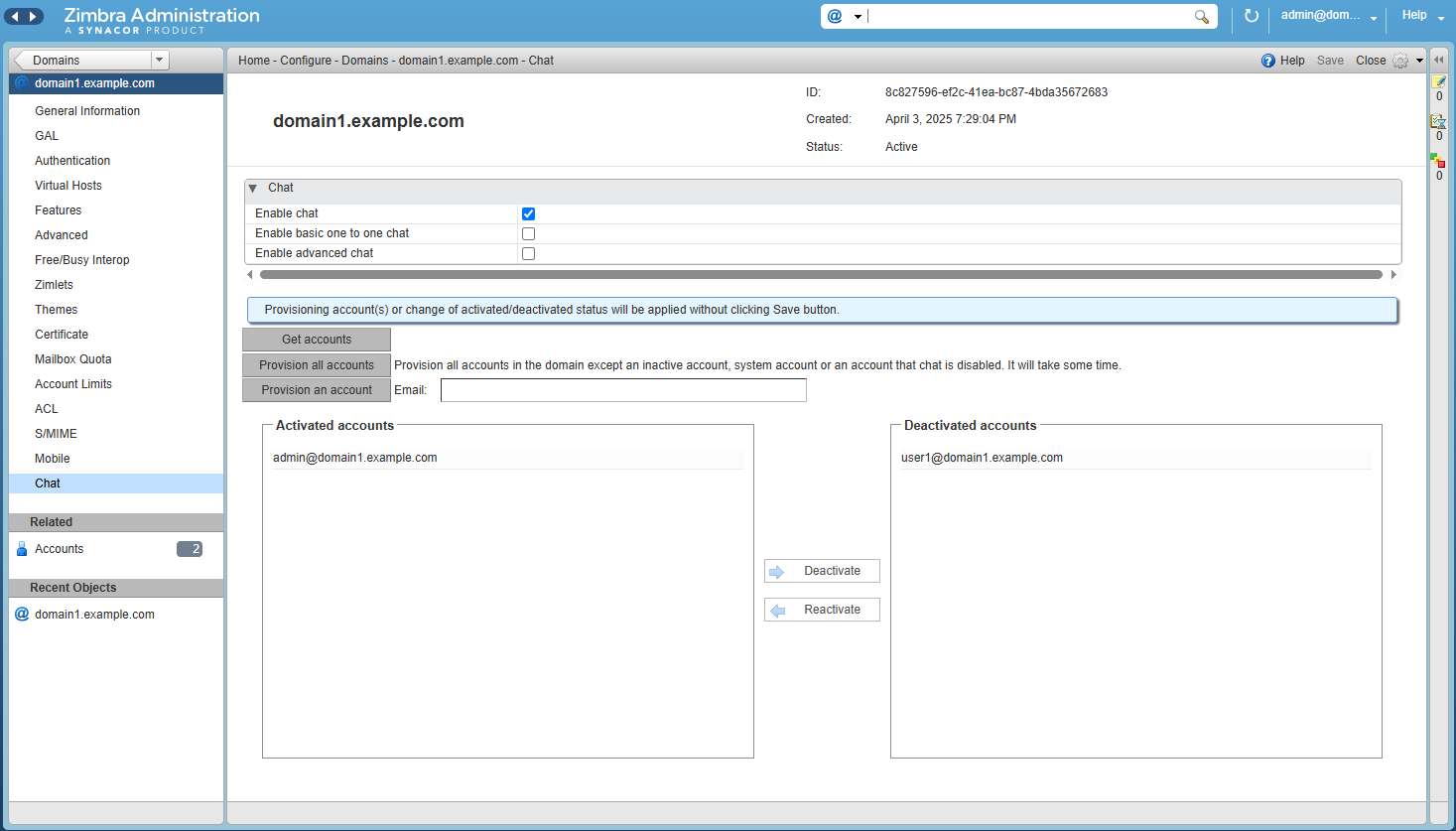
-
Provision all accounts: provision all accounts on the domain to a Chat server.
-
To provisoin multiple accounts we have developed a utility, refer: Provision Multiple Domains section below
-
-
Activated/Deactivated accounts lists are not updated automatically. Click Get accounts to show the latest list.
The number of successes and failures of account provisioning are shown in a dialog. When you see failures, the failure event log user creation failed: EMAIL_ADDRESS is written in /var/log/zulip/server.log on the Chat server. You can find the reason for the failure in the /var/log/zulip/server.log and/or /var/log/zulip/error.log.
|
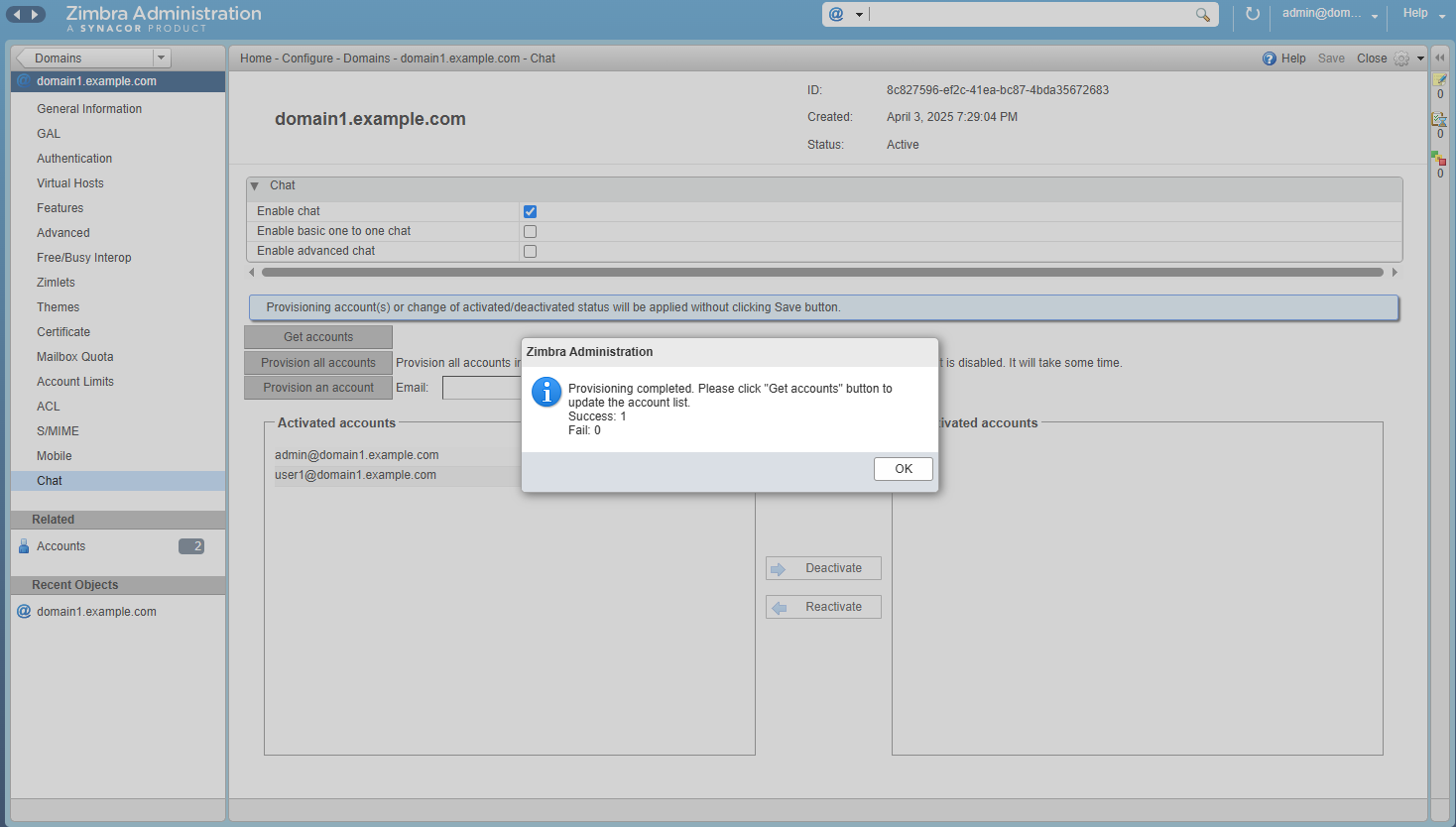
-
Provision an account: provision a single account on the domain to a Chat server. Enter an email address in text field and click Provision an account. Activated/Deactivated accounts lists are not updated automatically. Click Get accounts to show the latest list.
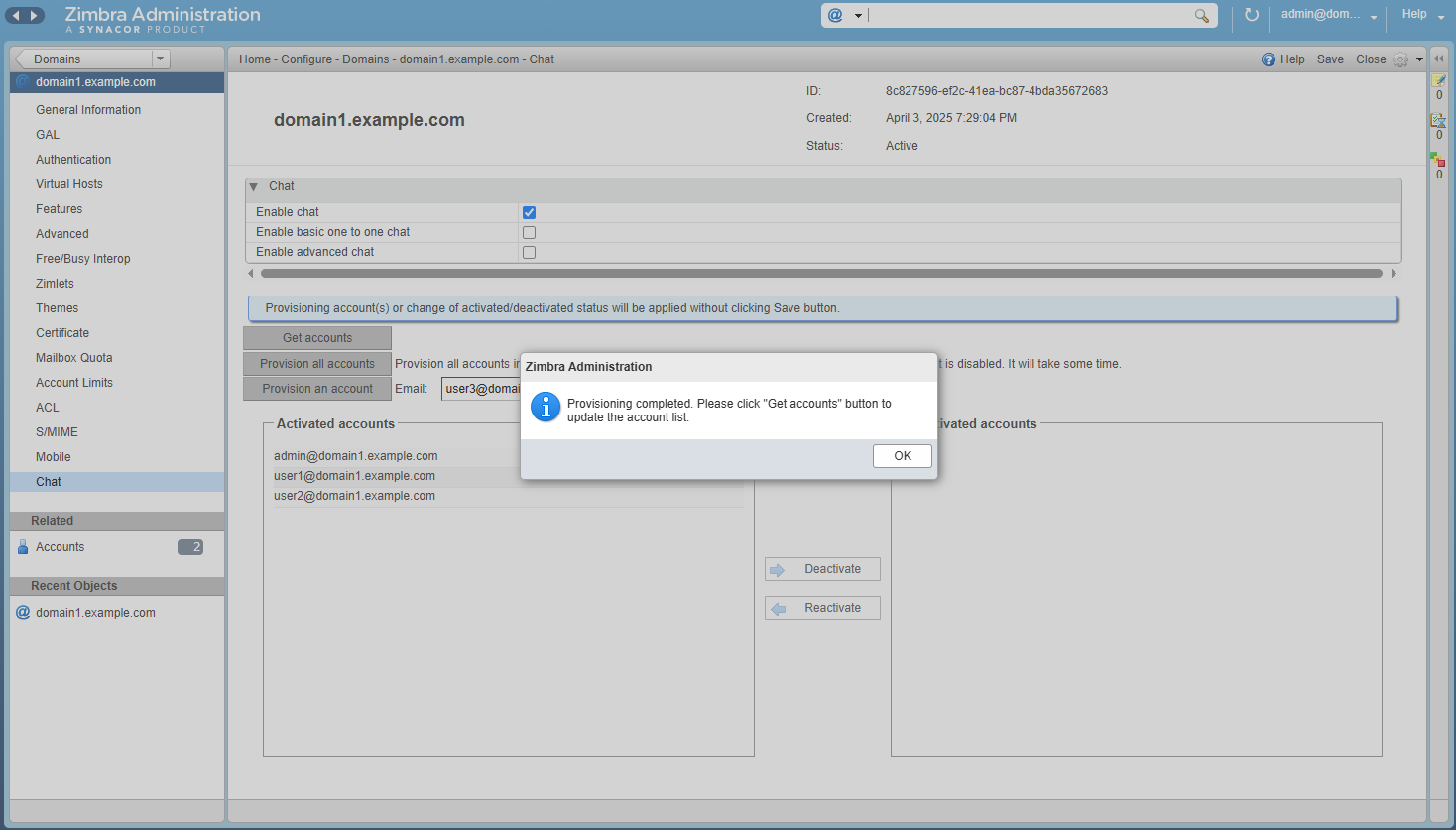
-
If a realm has not been created on Chat server, chat settings is unavailable on the domain.
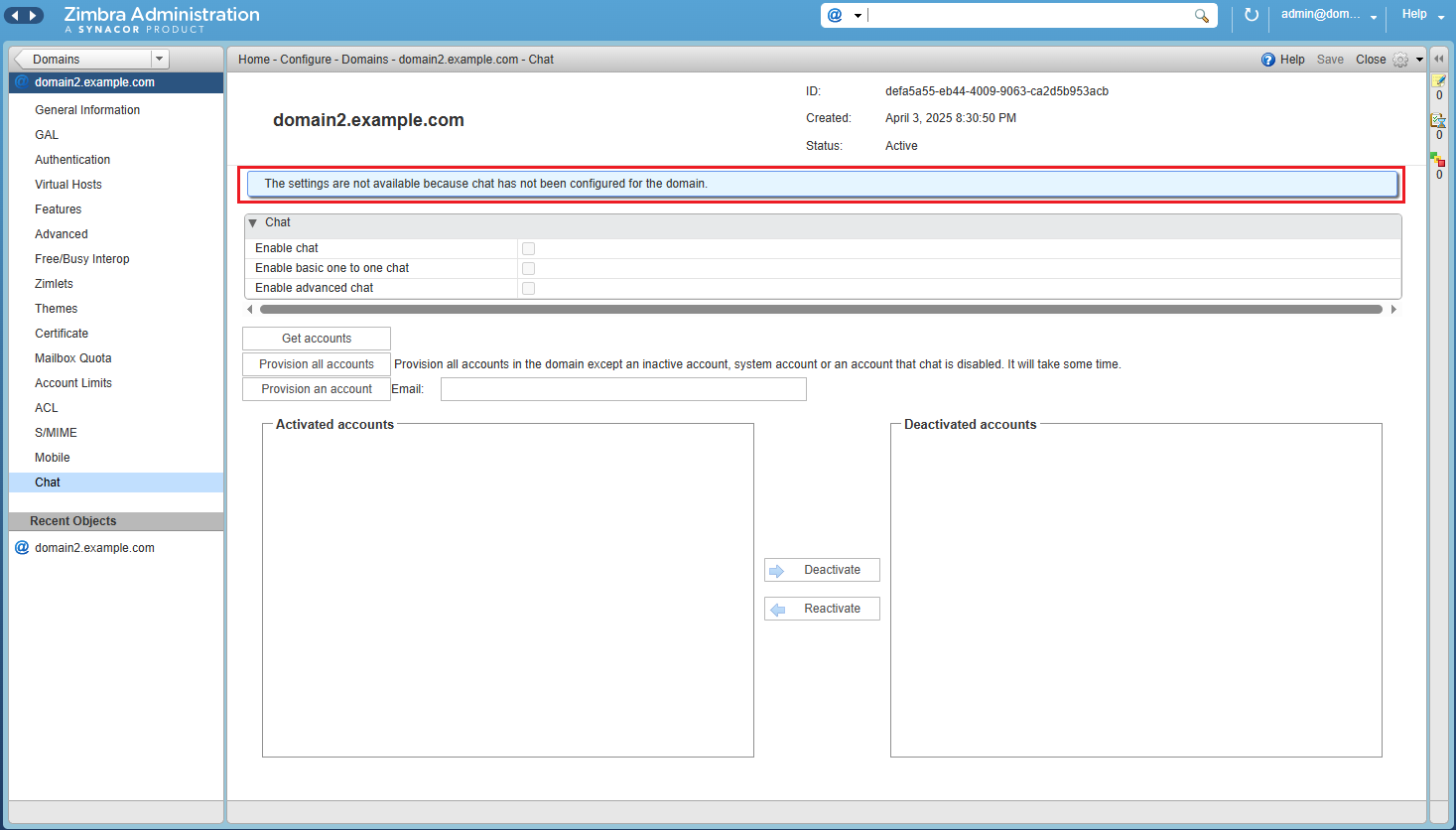
Provision Multiple Domains
Pre requisite
Zimbra Collaboration Suite version 10.1.10 or higher is required to run this script. This setting is recommended when there are more than 4 domains, each with 4,000 or more accounts.
-
Update Harakari Param on Chat server
-
vi /etc/zulip/uwsgi.ini -
locate harakari and update it to 300
-
-
Add
uwsgi_read_timeout-
vi /etc/nginx/zulip-include/app -
search for
include uwsgi_params -
Add line -
uwsgi_read_timeout 300;
-
Utility
The zmchatprovall utility provisions chat accounts for all Zimbra domains with the chat feature enabled. It supports optional input from a domain list file and allows parallel processing via the --parallelismFactor option. Domains without the chat feature are automatically skipped.
The following content provides help (zmchatprovall -h)
Usage: /opt/zimbra/bin/zmchatprovall [options]
Options:
-h, --help Show this help message
--filename=<file> <optional arg> Specify input file containing domain list
--parallelismFactor=<number> <optional arg> Number of parallel domain provisioning processes (default: 1)
Description:
This script provisions chat accounts for domains with the chat feature enabled.
If --filename option is provided, it provisions chat accounts for domains listed in the file (one domain per line)
that have the chat feature enabled.
If no --filename option is provided, it provisions chat accounts for all domains that have the chat feature enabled.
The parallelismFactor should be set to no more than 50% of the available CPU cores
on the most constrained component — either the Chat server or the Chat PostgreSQL server.
For example, if the Chat server has 6 cores and the Chat PostgreSQL server has 4 cores,
use the lower core count (i.e., 4) as the reference and set parallelismFactor to 2 (50% of 4).
NOTE:
Domains without the chat feature enabled will be skipped.
It is recommended to run this script in the background to avoid session timeouts.
Example:
/opt/zimbra/bin/zmchatprovall --filename=/path/to/chatdomains.txt --parallelismFactor=2 & disown
/opt/zimbra/bin/zmchatprovall & disownChat Directory
The /opt/zimbra/chat directory is used to store data related to chat services.
During the provisioning process, the provisionedChatDomainAccountsResult.txt file—containing the results—is saved in this directory.
To ensure successful provisioning, the zimbra user must have write access to this directory.
If the directory doesn’t exist or isn’t writable, the zmchatprovall command will stop and display the following message:
************************************************************
Chat directory not found or not writable.
Please run the following commands as root:
mkdir -p /opt/zimbra/chat
chown zimbra:zimbra /opt/zimbra/chat
Then re-run this script.
************************************************************How to decide parallelismFactor
The parallelismFactor should be configured to no more than 50% of the available CPU cores on the most resource-constrained system—either the Chat server or the Chat PostgreSQL server.
This ensures optimal performance and prevents system overload during parallel domain provisioning. For example, if the Chat server has 6 cores and the PostgreSQL server has 4 cores, use 4 as the reference and set the parallelismFactor to 2 (50% of 4).
If Chat and PostgreSQL share an 8-core server, set the parallelismFactor to 4 (50% of 8)
Functionality
The zmchatprovall script provisions chat accounts for domains that have the chat feature enabled. It accepts two optional parameters:
-
--filename: A file containing a list of domains to process (one per line). If not provided, all eligible domains are considered.
-
--parallelismFactor: Controls how many domains are provisioned concurrently. For example, if set to 2 and there are 10 domains, the script will process 2 domains in parallel; once one finishes, the next in queue is picked.
For each domain, account provisioning is done in batches of 100 by default. This batch size can be modified using:
zmlocalconfig -e chat_proxy_provisioning_batch_size=<new_size>A mailbox service restart is required for the new batch size to take effect. This batching helps manage system load and ensures smoother processing during large-scale provisioning.
If you face any issues, refer Troubleshooting Guide → Provision Multiple Domains Failures
Running provisioning in background
If the SSH session is disconnected, the script’s output will not be logged to: /opt/zimbra/chat/provisionedChatDomainAccountsResult.txt
To prevent this, run the script in the background using:
zmchatprovall --filename=/opt/zimbra/bin/chatdomains.txt & disownRetry Mechanism
A retry mechanism has been implemented: for example, if a batch of 100 accounts is sent and provisioning succeeds for 30 accounts but fails for the remaining 70, the batch will be retried. The script will attempt up to 3 retries for any failed batch.
Execution Summary
Execution summary is logged at /opt/zimbra/chat/provisionedChatDomainAccountsResult.txt
Example -
vi /opt/zimbra/chat/provisionedChatDomainAccountsResult.txt
Provisioning chat accounts for domain:
testdomain1.com
Accounts provisioned: 5000
Accounts not provisioned: 0
--------------------------------------------------
Provisioning chat accounts for domain:
testdomain2.com
Accounts provisioned: 5000
Accounts not provisioned: 0
--------------------------------------------------
Provisioning chat accounts for domain:
testdomain3.com
Accounts provisioned: 5000
Accounts not provisioned: 0
--------------------------------------------------
Provisioning chat accounts for domain:
testdomain4.com
Accounts provisioned: 5000
Accounts not provisioned: 0
--------------------------------------------------
Provisioning chat accounts for domain:
testdomain5.com
Accounts provisioned: 5000
Accounts not provisioned: 0
--------------------------------------------------Email Notification
Once execution starts admin will receive periodic notification at 1 hr frequency and upon execution completion.
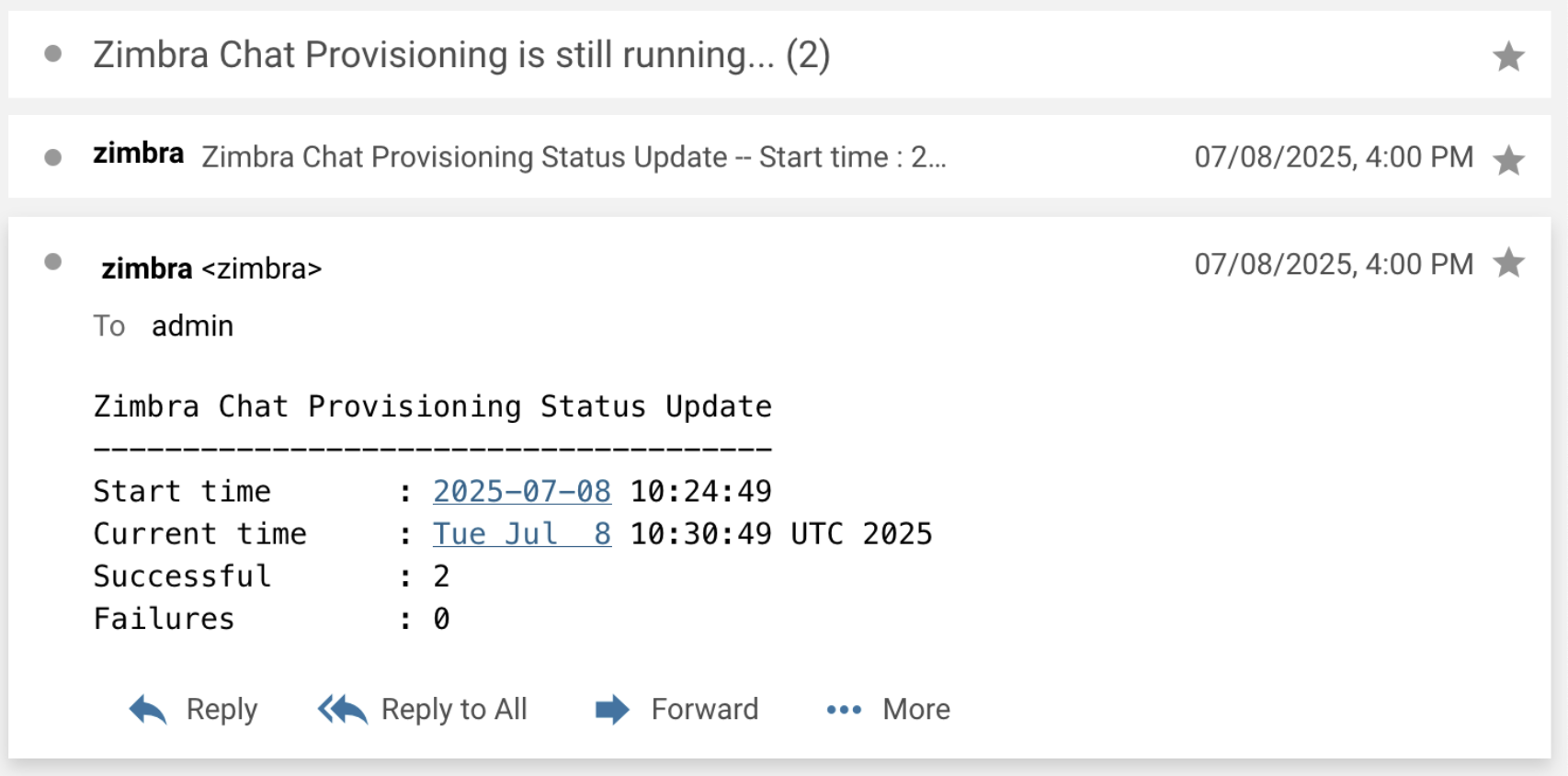
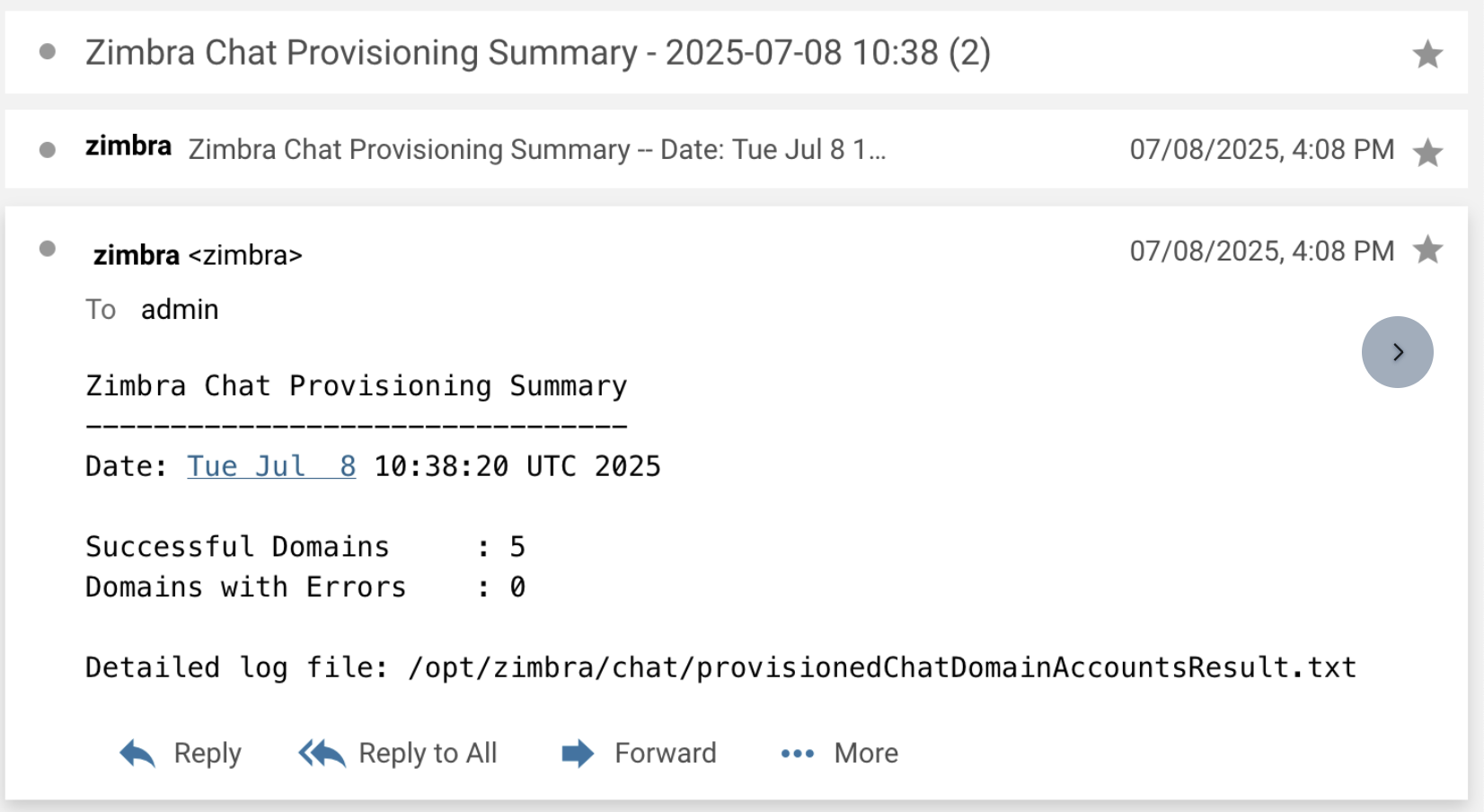
Performance Stats
The zmchatprovallscript was executed across multiple domains, each with a unique set of accounts. The goal was to measure performance in terms of system stability, parallel execution efficiency, and resource usage.
System Configuration
-
ZCS Server - 4 vCPU / 16 GB RAM
-
Chat Server - 4 vCPU / 16 GB RAM
-
PostgreSQL Server - 4 vCPU / 16 GB RAM
-
Network Bandwidth - 2 Gbps
Test Configuration
Test was run with default batch size set to 100 zmlocalconfig -e chat_proxy_provisioning_batch_size = 100
Performance Stats along with resource utilization
| Domain with accounts | Total Accounts | #parallelism | Time Taken | ZCS Server CPU | ZCS Server Mem | Chat Server CPU | Chat Server Mem | PostgreSQL CPU | PostgreSQL Mem |
|---|---|---|---|---|---|---|---|---|---|
Domain - 1 accounts- 5k |
5k |
1 |
58 mins |
10% |
51% |
20% |
24% |
22% |
8.7% |
Domain - 2 accounts- 10k |
20k |
2 |
1 hr 10 mins |
14% |
52% |
48% |
25% |
44% |
10% |
3 |
1 hr 31 mins |
12% |
53% |
69% |
26% |
60% |
11% |
||
Domain - 3 accounts- 10k |
30k |
2 |
2 hr 11 mins |
14% |
54% |
50% |
27% |
47% |
12.2% |
3 |
3 hr 38 mins |
15% |
55% |
70% |
28% |
57% |
13% |
||
Domain - 3 accounts- 30k |
90k |
3 |
5 hrs |
16% |
56% |
70% |
28% |
60% |
13% |
Observations
-
Parallelism Threshold: Increasing parallelism beyond 2 threads (50% of Chat & PostgreSQL CPU cores) results in CPU utilization rising to ~70%.
-
CPU Utilization: The provisioning process is CPU-intensive for both Chat and PostgreSQL servers. As parallelism increases, so does CPU load, which can lead to performance degradation if not managed.
Performance Recommendations
-
Parallelism Tuning
-
Use 50% of the available CPU cores on Chat and PostgreSQL servers as the parallelism factor when running provisioning for more than one domain concurrently. Refer to: How to decide parallelism section
-
-
Monitoring Continuously monitor CPU and memory utilization on both Chat and PostgreSQL servers during provisioning to avoid performance bottlenecks or system instability.
-
Recommended Execution Window
-
Run provisioning during maintenance windows or on weekends when system load is minimal.
-
Avoid running the provisioning script during business hours, as the CPU-intensive nature of the task could impact normal operations.
-
Zimlet Configuration Guide for one to one chat
Basic behavior
On one to one chat, presence data of all users in the same domain are fetched from Zimbra Chat server at initial loading process. After that, presence status (active or idle) of the user is sent to Chat server periodically (hereinafter called “presence update request”.) A response from the server includes presence data of other users whose last timestamp is updated. In addition, when other user(s) becomes active status, it is notified through a response of a events request (hereinafter called “presence event notification”.)
Possible performance issue on a large domain
If there are many users on a domain, it may increase some performance issues.
-
response size becomes large at initial loading process
-
the size of presence data included in a response of a presence update request becomes large, especially when many users are online. (i.e. many concurrent users)
-
the number of presence event notification becomes large
Configuration
A zimlet zimbra-zimlet-chat has some configuration.
config_template.xml is included in the zimlet. You can see additional information about the settings.
-
pingIntervalActiveInSeconds: default 180 (seconds)-
When the user is active, the status is sent to Chat server every 3 minutes. i.e. it is used on a presence update request at active status.
-
-
pingIntervalIdleInSeconds: default 900 (seconds)-
When the user is idle, the status is sent to Chat server every 15 minutes. i.e. it is used on a presence update request at idle status.
-
-
maxAllowedSecondsForNoActivity: default 240 (seconds)-
When the user has not used a keyboard or a mouse (touch action on mobile device) for 4 minutes, the user is regarded as idle status. After that,
pingIntervalIdleInSecondsis used to send the user’s presence status. -
When a user uses a keyboard or a mouse, the user status becomes from idle to active. After that,
pingIntervalActiveInSecondsis used.
-
-
presenceUpdateMinFreqInSeconds: default 60 (seconds)-
When many presence update requests are sent from a client (or a browser) in a short period of time, Chat server ignores them not to update database frequently.
-
By default, minimum update period is 55 seconds. For example, when Chat server receives 5 requests in 55 seconds from the same user, it accepts the first request and update the database, but ignores other 4 requests.
-
When the user becomes idle, the status is sent to Chat server. However, if it happens just after active status is sent to Chat server, the idle status notification is ignored on Chat server. The zimlet sends additional idle presence status after the specified value in consideration of the limitation.
The value must not be changed until the minimum update period 55 seconds is modified on Chat server.
-
-
idleEventCallDelay: default 60 (seconds)-
An event like receiving a message and status change to online on other users are checked through presence event notification. When the user is active, next events request is sent immediately after a previous presence event notification fulfilled.
-
When the user is idle, 1 minute wait time is added before next events request is sent. It means,
-
Receive presence event notification
-
Wait 1 minute
-
Send next events request
-
-
If the user receives a message from other user or other user becomes online during the wait time, the event is notified in a response of next events request and reflected in UI.
-
-
enablePresenceEvents: default:true-
When it is true:
-
Presence data of all users in the same domain are fetched from Chat server at initial loading process.
-
When other user(s) becomes active status, it is notified through a response of a events request.
-
A response of presence update request includes presence data of other users' whose timestamp is updated.
-
-
When it is false:
-
Presence data of all users are not loaded. Instead, presence data of only users shown in a sidebar (pinned and not pinned users) are fetched.
-
Presence status is NOT notified when other user(s) becomes active status.
-
A response of presence update request does NOT include presence data of other users' whose timestamp is updated.
-
Instead of using presence event notification and a response of presence update request, another http request to get presence data of only necessary users is sent together at sending presence update request. (hereinafter called “presence fetch request”.)
-
-
Advantage & Disadvantage
-
When it is true,
-
Advantage
-
When another user becomes active, it can be detected in shorter time
-
-
Disadvantage
-
All other users' presence data are fetched at initial loading process.
-
All other users' “active” status change are notified through presence event notification, even when the user communicates with some other users only.
-
It means that response size of the initial loading may be large and many presence event notification may occur.
-
It will increase memory use on a client machine, increase server load, and increase network traffic.
-
-
When it is false,
-
Advantage
-
Size of initial loading is smaller.
-
Presence data of only necessary users are fetched from Chat server.
-
It will achieve less memory use on a client, and less server load and network traffic especially on presence event notification in many case.
-
-
Disadvantage
-
When a user becomes active, it is not reflected on other users immediately. It will be reflected when next presence request is triggered.
-
Additional presence fetch request is sent. There might be some overhead on both client and server side. However, it should not be so much in comparison with fetching presence update through a response of presence update request in a large domain.
-
-
-
Constraints
-
The values for
pingIntervalActiveInSeconds,pingIntervalIdleInSeconds,maxAllowedSecondsForNoActivityandpresenceUpdateMinFreqInSecondsmust be provided in seconds. -
The minimum values required for
pingIntervalActiveInSeconds,pingIntervalIdleInSecondsandpresenceUpdateMinFreqSecondsmust be 60 seconds. -
presenceUpdateMinFreqInSecondsvalue must be less thanpingIntervalActiveInSecondsandpingIntervalIdleInSeconds. -
presenceUpdateMinFreqInSecondsmust not be changed unless a setting of minimum frequent seconds for presence update is modified on Zimbra Chat server. -
The maximum value required for
idleEventCallDelaymust be 60 seconds.
Recommended settings
On a small domain
-
Default values should be good
On a large domain
-
enablePresenceEventsis false -
If you see performance issue on Chat server, consider: a. increasing
pingIntervalActiveInSeconds, b. increasingpingIntervalIdleInSecondsand/or c. decreasemaxAllowedSecondsForNoActivityto reduce frequency of presence update request.
They are sort of tuning parameters. Efficiency of changes depend on the number of concurrent users, Chat server specification, network bandwidth and so on.
Configuration steps
Modify config_template.xml and apply the change after the zimlet is deployed.
All steps should be run as zimbra on a Zimbra mailstore server.
-
deploy the zimlet
-
check the current configuration
$ zmzimletctl info zimbra-zimlet-chat ... Config: <zimletConfig name="zimbra-zimlet-chat" version="1.0.0">...</zimletConfig> -
edit
config_template.xml. For example:$ cd /path/to/your-working-directory/ $ cp /opt/zimbra/zimlets-deployed/zimbra-zimlet-chat/config_template.xml ./ $ vi config_template.xml-
set upper version number
-
modify a value of setting(s)
-
-
apply the change
$ zmzimletctl configure config_template.xml -
confirm the change
$ zmzimletctl info zimbra-zimlet-chat -
run flushCache. Specify
-aoption on a multi-server environment.$ zmprov fc -a zimlet
Log files
Main log file of Chat server application is /var/log/zulip/server.log on a Chat server.
You can find other log files like django.log and tornado.log in /var/log/zulip/ directory, but major log events are gathered in server.log.
The log format of server.log is as follows:
-
Timestamp
-
Log level
-
Logger name, abbreviated as
zrfor these Zulip request logs -
IP address
-
HTTP method
-
HTTP status code
-
Time to process
-
(Optional performance data details)
-
Endpoint/URL from
zproject/urls.py
Nginx log files access.log and error.log exist in /var/log/nginx/ directory on a Chat server.
The format of access.log is defined in /etc/nginx/nginx.conf as follows:
log_format combined_with_host_and_time '$remote_addr - $remote_user [$time_local] '
'"$request" $status $body_bytes_sent '
'"$http_referer" "$http_user_agent" $host $request_time';
PostgreSQL log files exist in /var/log/postgresql directory.
It does not contain detailed logs but just statistics by default.
If you see an issue on database access, you may be able to find ERROR, FATAL or PANIC log in postgresql-16-main.log.
Zimbra Chat Administrator
Administration Organization basics
As a Zimbra Chat Administrator, understanding how to manage user roles and permissions is key to maintaining organized workspace. This section explains the different user roles available, how to manage them, and how to configure organization-wide permissions.
|
These roles are chat specific and not same as the Zimbra email administrator role. |
Overview of User Roles
Zimbra Chat supports multiple roles to help you assign the right permissions based on your organization’s needs:
| Role | Description |
|---|---|
Organization Owner |
Full control over settings, users, and other administrator. Only owners can deactivate the organization. |
Organization Administrator |
Can manage users, channels, settings. Cannot promote others to owner or modify owner roles. |
Moderator |
Can perform limited administrative functions. Permissions can be configured by Owner and Administrator. |
Member |
Default role for most users. Can access all public channels. |
Guest |
Can only access channels they are explicitly added to. Cannot see other users or channels. |
Managing User Roles
You can assign and change roles either through the user profile or via organization settings.
Via User Profile
-
Hover over the user’s name in the right sidebar.
-
Click the three-dot menu → Manage this user.
-
Under User role, select a new role.
-
Click Save changes.
Via Organization Settings
-
Go to Settings → Organization Settings → Users tab.
-
Use the dropdown next to the user’s name to assign a new role.
-
Click Save changes.
Organization Settings Management
Only Owner and Administrator can configure and view organization settings.
Common Settings:
-
Organization profile and type.
-
Organization logo can also be configured and customized.
-
Default user permissions.
-
Automated messages and email language.
To access: Go to Settings → Organization settings.
Managing User Access
Deactivate a User
Deactivation removes access across all devices, disables credentials, and bots.
Steps:
-
Open the user profile or go to Organization → Users tab.
-
Click Manage this user.
-
Click Deactivate user → Confirm.
-
Note:
Ownerrole cannot be deactivated byAdministrator.
Reactivate a User
-
Go to Settings → Organization → Users → Deactivated tab.
-
Click Reactivate next to the user.
The user retains all prior settings and roles upon reactivation.
Default Settings for New Users
Administrator can configure default preferences for new users, such as:
-
Theme, font size, time format.
-
Privacy options.
-
Notifications.
-
Home view (Inbox vs. Recent Conversations).
User Identity Controls
Configure these options under Organization settings → Organization permissions → User Identity:
Prevent users from changing: * Name, Email, Avatar.
Deactivating an Organization
This action is irreversible from the organization side.
Only Owners can deactivate:
-
Go to Organization settings → Organization profile.
-
Click Deactivate organization → Confirm.
|
To reverse a deactivation, contact your server administrator immediately. Deactivation cannot be undone through the Zimbra Chat interface. Only a Zimbra system administrator has the necessary access and tools to recover or restore the organization from the server side. |
Channel Management
As an Administrator, you have full control over how channels are created, managed, and used.
Control Who Can Create Channels
Go to: Settings → Organization settings → Organization permissions → Channel permissions
You can choose:
-
Administrator only
-
Administrator and Moderator
-
Administrator, Moderator, and Members
-
All full members
Limit creation to Administrator and/or Moderators if you want to keep things clean.
Enable/Disable Channel Types
Channel types:
-
Public – anyone can join, all messages visible.
-
Private – invite-only.
-
Web-public – read-only access via public link.
To grant web-public type to a channel:
Only Administrator and Moderator can create web-public channels.
-
Go to Organization settings → Organization permissions → Channel permissions.
-
Enable: Allow web-public channels.
Set Who Can Post in Channels
You can change this anytime—even for existing channels.
For each channel:
-
Open Channel settings → click on the channel name → Advanced configuration section.
-
Under Posting policy, choose: Everyone, Administrator & moderators, Only moderators, Administrator only.
Manage Subscribers
As an Administrator, you can:
-
Add/remove users from any channel - Channel settings → click on the Channel name → Subscribers tab.
-
Force users to subscribe to mandatory channels (via “default channels”).
-
Set Default Channels for New Users
-
Go to: Settings → Organization settings → Default channels.
-
These channels are auto-subscribed for new users. Ideal for:
#announcements,#company-news.
-
Rename Channel and Edit Channel Settings
Administrator can:
-
Change the channel name and description.
-
Make the channel public.
-
Set posting policies.
-
Delete channels.
Go to any channel → Channel settings → Make your changes.
Delete Channels
Administrator can:
-
Delete channels - Deleting channel will immediately unsubscribe everyone. This action cannot be undone.
Require Topics in Channel Messages
By default, users can send messages without choosing a topic — these show up as “(no topic)”.
As an Administrator, you can prohibit users from sending messages without a topic.
To enable this:
-
Go to Settings → Organization settings
-
Scroll to Other settings
-
Toggle Require topics in channel messages
-
Click Save changes
Control Who Can Edit Topics and Move Messages
As an Administrator, you can decide:
-
Who can edit message topics
-
Who can move topics to other channels
-
Whether there’s a time limit for editing or moving messages
To manage these permissions:
-
Go to Settings → Organization settings → Organization permissions
-
Under Moving messages, configure each of these:
-
Who can move messages to another topic
-
Time limit for editing topics
-
Who can move messages to another channel
-
Time limit for moving messages between channels
-
-
Click Save changes after each update
|
Administrator and Moderator are able to edit and move messages no matter how long ago they were written. |
Control Who Can Send Direct Messages (DMs)
As Owner or Administrator, you can control how DMs work in your organization.
There are two settings you can configure:
To set up DM permissions:
-
Go to Settings → Organization settings → Organization permissions
-
Scroll to Direct message permissions
-
Who can authorize a DM (At least one person in the conversation must be authorized to start it.)
-
Set Who can authorize a direct message conversation
-
Click Save changes
-
-
Who can start a DM (Defines who’s allowed to initiate new DM conversations.)
-
Set Who can start a direct message conversation
-
Click Save changes
-
-
To disable DMs completely:
-
Set Who can authorize a direct message conversation to
Direct messages disabled -
Click Save changes
-
Control Who Can Use Wildcard Mentions (@all, @channel, @topic)
As Owner or Administrator, you can manage who’s allowed to use wildcard mentions that notify large groups of people.
Wildcard mentions include:
-
@all,@channel, or@everyone→ Notifies everyone in a channel -
@topic→ Notifies everyone active in a topic
By default, these can notify a lot of users. You can limit this to avoid spamming large groups.
This setting only applies when the channel has more than 15 members, or the topic has more than 15 participants.
To restrict wildcard mentions:
-
Go to Settings → Organization settings → Organization permissions
-
Scroll to Channel permissions
-
Set Who can notify a large number of users with a wildcard mention
-
Click Save changes
Manage Message Editing, Deleting & Edit History
As an administrator, you control:
-
Who can edit or delete their own messages
-
Time limits for editing or deleting
-
Whether edit history is visible to users
Message Editing
-
Users can only edit their own messages.
-
Administrator can always delete any message.
To configure editing:
-
Go to Settings → Organization settings → Organization permissions
-
Under Message editing:
-
Toggle Allow message editing.
-
Toggle Enable message edit history.
-
Set Time limit for editing messages.
-
-
Click Save changes.
Message Deletion
-
Deleting a message permanently removes the message.
-
Users can delete their own messages.
-
Administrator can delete any message.
-
Users can also delete messages sent by bots they own.
To configure deletion:
-
Go to Settings → Organization settings → Organization permissions
-
Under Message deletion:
-
Set Who can delete their own messages.
-
Set Time limit for deleting messages (does not apply to Administrator).
-
-
Click Save changes.
Message Retention
As Administrator, you can also configure a global default message retention policy:
-
Go to Organization settings → Message retention.
-
Select message retention period.
-
By default all messages are kept indefinitely.
-
Use custom retention period and select Retention period (in days).
Media Preview Behaviour
Zimbra chat shows small previews of images, videos, and links to keep chats readable.
As an administrator you can turn off previews entirely for: * Uploaded and linked images/videos * Linked websites
-
Go to Settings → Organization settings
-
Under Other settings:
-
Toggle Show previews of uploaded and linked images and videos
-
Toggle Show previews of linked websites
-
Click Save changes
Video
Zimbra Chat is a chat only solution, and does not include any video conferencing solution. However, an integration with open source chat solution has been provided. By default, Zimbra Advanced Chat provides a built in integration with Jitsi Meet, 100% open source video conferencing solution. Users will be able to start a Jitsi Meet call and invite others using the add video call or add voice call button in the compose box.
Configure a self-hosted instance of Jitsi Meet
Administrators can use a self-hosted instance of Jitsi Meet. Zimbra Advanced Chat has cloud version of Jitsi Meet as its default video call provider. This is the community version of the Jitsi open source platform.
To configure self-hosted Jitsi Meet, as an Administrator:
-
Click on the gear icon in the upper right corner of the web or desktop app.
-
Select Organization settings.
-
On the left, click Organization settings.
-
Under Compose settings, confirm
Jitsi Meetis selected in the Call provider dropdown. -
Select Custom URL from the Jitsi server URL dropdown, and enter the URL of your self-hosted Jitsi Meet server.
-
Click Save changes.
Backup and Restore For Zimbra Chat
The Zimbra Chat server has a built-in backup tool which can be used to make a backup of chat data on the Chat server and restore it in case of disaster recovery, testing with production data, and hardware migrations.
| The backup and restore functionality here is not related to Zimbra Backup and Restore feature used for mailbox data backup. |
It is fast, robust, and minimizes disruption for your users. However, it has a few limitations:
-
Backups must be restored on a server running the same Zulip version.
-
Backups must be restored on a server running the same PostgreSQL version.
Backup
Zimbra Chat Administrator can create a backup of all data on the server using backup tool as:
# As the zulip user
/home/zulip/deployments/current/manage.py backupFollowing options can be used with above command:
--output=/tmp/backup.tar.gz: Filename to write the backup tarball to (default: write to a file in /tmp). On success, the console output will show the path to the output tarball.
--skip-uploads: If LOCAL_UPLOADS_DIR is set, user-uploaded files in that directory will be ignored. LOCAL_UPLOADS_DIR is the directory where user uploaded files are stored in Chat server. It is specified in /etc/zulip/settings.py
This will generate a .tar.gz archive containing all the data stored on your Chat server that would be needed to restore your Chat server’s state on another machine perfectly.
For example:
# su zulip -c '/home/zulip/deployments/current/manage.py backup --output=/home/zulip/zulip-backup.tar.gz'
+ /usr/lib/postgresql/16/bin/pg_dump --format=directory --file=/tmp/zulip-backup-2025-04-04-07-29-56-533sg975/zulip-backup/database --username=zulip --dbname=zulip --no-password --host=10.0.0.231 --port=5432
+ tar --directory=/tmp/zulip-backup-2025-04-04-07-29-56-533sg975 -cPzf /home/zulip/zulip-backup.tar.gz '--transform=s|^/etc/zulip(/.*)?$|zulip-backup/settings\1|x' -- zulip-backup/zulip-version zulip-backup/os-version zulip-backup/postgres-version /etc/zulip zulip-backup/database
Backup tarball written to /home/zulip/zulip-backup.tar.gzRestore backup
-
Create a new ZImbra Chat server setup using the same base OS and the same versions of Zulip and postgreSQL as the backup was taken on. Use the Zimbra Zulip installer to install and configure the setup.
-
Any upgrade related to OS, Zulip version or postgreSQL version should be done after successful restore of backup.
-
Ensure network security measures recommended in the Installation guide are safely in place for the new instances.
-
-
Copy backed-up .tar.gz file from the old Zimbra Chat server to the new Chat server.
-
Follow further restore steps based on your Zimbra Chat server setup.
Restoration on multi-node Chat server setup:
In case of multi-node Chat server setup, where PostgreSQL server is also new (i.e. PostgreSQL database also needs to be restored on the new PostgreSQL server):
-
Update following details in
/etc/zulip/settings.pyon Chat server node:
EXTERNAL_HOST = "new-chat-server-hostname"
REMOTE_POSTGRES_HOST = "<new-postgres-host-ip>"-
On PostgreSQL node, add the following entry at the bottom in
/etc/postgresql/*/main/pg_hba.confhost postgres zulip <zulip-server-host-ip>/32 trust-
Restart
postgresqlasrootuser.# Run on postgres node as root user systemctl restart postgresql -
Grant the
CREATEDBprivilege to the zulip user
# Run on postgres node su - postgres psql ALTER ROLE zulip CREATEDB; -
-
As root, restore the backup:
#Run On Chat server node
/home/zulip/deployments/current/scripts/setup/restore-backup --keep-settings /path/to/backup-
After successful restoration of Chat server and PostgreSQL server, remove the CREATEDB privilege for the Zulip user:
# Run on postgres node
su - postgres
psql
ALTER ROLE zulip NOCREATEDB;| CREATEDB privilege for the Zulip user should be revoked after restore is completed successfully. |
Restoration on combined Chat setup (Database and Zimbra Chat server on single node):
In case of combined setup, restore the backup as:
-
As root, restore the backup:
(Run as root on chat server) $ /home/zulip/deployments/current/scripts/setup/restore-backup `/path/to/backup.tar.gz`
-
After successful restoration, update the following details in
/etc/zulip/settings.py
EXTERNAL_HOST = "new-zulip-server-hostname"
-
Restart the Chat server
(Run as root on chat server) $ /home/zulip/deployments/current/scripts/restart-server
On Zimbra mailbox server, updated the zimbraChatBaseHost with the new Chat server hostname. Update it for domains or at global config level.
(Run as zimbra on a Zimbra mailstore server)
$ zmprov mcf zimbraChatBaseHost <new-chat-server-hostname>
$ zmprov fc -a allYou can confirm that the restored Chat server can search an account on the LDAP. Make sure that both full_name and email are returned.
(Run as zulip on chat server)
$ /home/zulip/deployments/current/manage.py query_ldap <account-email>
...
full_name: user1
email: <account-email>For more details, please refer to the following documentation: Backups, export and import — Zulip 9.2 documentation
Important Points to note regarding Zimbra Chat Backup and Zimbra Collaboration Suite (ZCS) Backup and Restore:
-
There is no account level backup and restore on Zimbra Chat server.
-
There is no built-in automatic backup schedule for the Zimbra Chat server but can be configured using crontab.
-
Zimbra Chat server backup is not integrated with ZCS’s backup and restore. Zimbra Chat backup and restore is managed separately.
-
Zimbra Chat Server logs are not backed up. Chat administrator should create backup of server log files manually if required.
-
Restoring a Zimbra Chat server from its backup does not create accounts on ZCS servers. If accounts are required to be restored on ZCS server, ZCS’s restore should be executed first.
Troubleshooting Guide
1. LDAP Connection Issues
1.1. Chat server cannot access LDAP server or search a user
If you see Can’t contact LDAP server error message at the following command execution,
$ /home/zulip/deployments/current/manage.py query_ldap EMAIL_ADDRESS
ldap.SERVER_DOWN: {'result': -1, 'desc': "Can't contact LDAP server", 'errno': 11, 'ctrls': [], 'info': 'Resource temporarily unavailable'}Check the following items:
-
ldap hostname can be resolved on the Chat server
-
ldap server allows 389 port access from the Chat server
-
AUTH_LDAP_SERVER_URIin/etc/zulip/settings.pyspecifies a correct ldap hostname (and port). For example,AUTH_LDAP_SERVER_URI="ldap://ldap.your.domain"orAUTH_LDAP_SERVER_URI="ldap://ldap.your.domain:389". Default port 389 can be omitted.
1.2. TLS Connection Issues
If you see Connect error at Initiating TLS like
$ /home/zulip/deployments/current/manage.py query_ldap EMAIL_ADDRESS
2025-03-28 07:29:10.948 DEBG [django_auth_ldap] Binding as uid=zimbra,cn=admins,cn=zimbra
2025-03-28 07:29:10.949 DEBG [django_auth_ldap] Initiating TLS
...
ldap.CONNECT_ERROR: {'result': -11, 'desc': 'Connect error', 'ctrls': [], 'info': '(unknown error code)'}You need to verify a valid SSL certificate has been deployed on ldap server.
1.3. Invalid Credentials
If you see ldap.INVALID_CREDENTIALS like
$ /home/zulip/deployments/current/manage.py query_ldap EMAIL_ADDRESS
ldap.INVALID_CREDENTIALS: {'msgtype': 97, 'msgid': 2, 'result': 49, 'desc': 'Invalid credentials', 'ctrls': []}Check the following items:
-
AUTH_LDAP_BIND_DNin/etc/zulip/settings.pyspecifies a correct value. -
auth_ldap_bind_passwordin/etc/zulip/zulip-secrets.confspecifies a correct password for theAUTH_LDAP_BIND_DN
1.4. Successful User Search
full_name and email should be returned when user search works correctly.
$ /home/zulip/deployments/current/manage.py query_ldap user1@mydomain.com
...
full_name: user1
email: user1@mydomain.comYou need to restart Chat server application to apply changes in /etc/zulip/settings.py and /etc/zulip/zulip-secrets.conf.
/home/zulip/deployments/current/scripts/restart-server2. Realm Creation Issues
2.1. A realm is not created on Chat server
If you created a domain with zimbraFeatureZulipChatEnabled TRUE or ran CreateChatRealmRequest but a realm is not created on a Chat server, check the following items:
-
Chat server hostname can be resolved on mailstore servers
-
The Chat server allows 443 port access from mailstore servers
-
zimbraChatBaseHostandzimbraChatJwtSecrethave been configured on the domain. If each attribute has been configured in globalConfig and not been configured in domain, the value in globalConfig is applied automatically. -
zimbraChatBaseHosthas a hostname of a Chat server -
zimbraChatJwtSecrethas a secret key, which has been set in/etc/zulip/zulip-secrets.confaszimbra_jwt_auth_keyon the Chat server -
A valid SSL certificate has been deployed on the Chat server
3. Chat Availability Issues
3.1. A realm has been created on Chat server, but Chat is unavailable on Modern Web App
If a realm has been created on a Chat server but chat feature is unavailable in Modern Web App, check the following items:
3.1.1. Zimbra license
-
a valid license is installed on Zimbra
-
the license is activated
-
the license is not expired
-
the following feature(s) is licensed
-
BOCAL (BasicOneToOneChatAccountsLimit)feature enabled for Basic one to one chat -
CAL (ChatAccountsLimit)feature enabled for Advanced Chat
-
-
you can see license status by executing
zmlicense -p
3.1.2. Other configuration issues
-
zimbra-zimlet-chatzimlet has been deployed and enabled on an account -
a hostname of a realm url is resolvable on zimbra proxy and mailstore servers
-
a valid SSL certificate for a hostname of a realm url has been deployed on the Chat server
-
zmproxyconfgenandzmproxyctlreload have been executed on all proxy servers -
zimbraFeatureZulipChatEnabledis enabled on a domain -
Basic Chat
-
zimbraFeatureZulipChatEnabledandzimbraFeatureBasicOneToOneChatEnabledare enabled on an account
-
-
Advanced Chat
-
zimbraFeatureZulipChatEnabledandzimbraFeatureAdvancedChatEnabledare enabled on an account
-
-
If there are multiple mailstore servers, run zmprov fc -a all
-
CSRF_TRUSTED_ORIGINSin/etc/zulip/settings.pyon a Chat server specifies a URL of Zimbra web app
| Chat server application needs to be restarted when it is modified. |
4. Account Provisioning Issues
4.1. I ran provision all accounts, but some accounts are not created on Chat server
Mailstore server does not ask Chat server to create an account if any of the following conditions are met:
-
zimbraAccountStatusis notactiveon an account -
zimbraIsSystemAccountisTRUEon an account -
zimbraFeatureZulipChatEnabledis notTRUEon a domain or an account
4.2. I saw HTTP response status 504 error when I run provisioning chat accounts.
If you run "Provision all accounts" on Admin Console, you may see the following error message in a dialog.
Server error encountered
-------------------------
Error code: CSFE_SVC_ERROR
Method: ProvChatAccountsRequest
Details: HTTP response status 504It occurs when it is taking a long time to provision accounts. A http connection between a mailstore server and a Chat server is closed due to timeout. However, the provisioning process may still be running on the Chat server. If creating user logs are being added to /var/log/zulip/server.log, the process is running. For example,
2025-04-04 02:08:20.833 INFO [] creating user: user925@mydomain.com
2025-04-04 02:08:20.883 INFO [] creating user: user926@mydomain.com
...You don’t need to (or should not) rerun "Provision all accounts". You can close the dialog on Admin Console, and just wait for the process to complete.
5. Chat Server Issues
5.1. Issue - chatlogin succeeds but register fails. Provisioning commands succeed.
Logs:
/var/log/zulip/errors.log
2025-04-02 05:53:42.735 WARN [zulip.queue:9800] TornadoQueueClient attempting to reconnect to RabbitMQ
2025-04-02 05:53:42.741 ERR [pika.adapters.utils.io_services_utils:9800] Socket failed to connect: <socket.socket fd=18, family=2, type=1, proto=6, laddr=('127.0.0.1', 59468)>; error=111 (Connection refused)
2025-04-02 05:53:42.742 ERR [pika.adapters.utils.connection_workflow:9800] TCP Connection attempt failed: ConnectionRefusedError(111, 'Connection refused'); dest=(<AddressFamily.AF_INET: 2>, <SocketKind.SOCK_STREAM: 1>, 6, '', ('127.0.0.1', 5672))
2025-04-02 05:53:42.742 ERR [pika.adapters.utils.connection_workflow:9800] AMQPConnector - reporting failure: AMQPConnectorSocketConnectError: ConnectionRefusedError(111, 'Connection refused')
2025-04-02 05:53:42.742 ERR [pika.adapters.utils.connection_workflow:9800] AMQP connection workflow failed: AMQPConnectionWorkflowFailed: 1 exceptions in all; last exception - AMQPConnectorSocketConnectError: ConnectionRefusedError(111, 'Connection refused'); first exception - None.
2025-04-02 05:53:42.742 ERR [pika.adapters.utils.connection_workflow:9800] AMQPConnectionWorkflow - reporting failure: AMQPConnectionWorkflowFailed: 1 exceptions in all; last exception - AMQPConnectorSocketConnectError: ConnectionRefusedError(111, 'Connection refused'); first exception - None
2025-04-02 05:53:42.742 ERR [pika.adapters.base_connection:9800] Full-stack connection workflow failed: AMQPConnectionWorkflowFailed: 1 exceptions in all; last exception - AMQPConnectorSocketConnectError: ConnectionRefusedError(111, 'Connection refused'); first exception - None
2025-04-02 05:53:42.742 ERR [pika.adapters.base_connection:9800] Self-initiated stack bring-up failed: AMQPConnectionError: (AMQPConnectionWorkflowFailed: 1 exceptions in all; last exception - AMQPConnectorSocketConnectError: ConnectionRefusedError(111, 'Connection refused'); first exception - None,)
2025-04-02 05:53:42.742 WARN [zulip.queue:9800] TornadoQueueClient couldn't connect to RabbitMQ, retrying in 2 secs.../var/log/zulip/server.log
2025-04-02 05:53:17.386 ERR [pika.adapters.base_connection:9800] Self-initiated stack bring-up failed: AMQPConnectionWorkflowFailed: 1 exceptions in all; last exception - AMQPConnectorAMQPHandshakeError: ProbableAccessDeniedError: Client was disconnected at a connection stage indicating a probable denial of access to the specified virtual host: ('ConnectionClosedByBroker: (530) "NOT_ALLOWED - access to vhost \'/\' refused for user \'zulip\'"',); first exception - None/var/log/rabbitmq/zulip@localhost.log
2025-04-02 05:53:15.590500+00:00 [info] <0.17977.0> accepting AMQP connection <0.17977.0> (127.0.0.1:60086 -> 127.0.0.1:5672)
2025-04-02 05:53:15.597951+00:00 [error] <0.17977.0> Error on AMQP connection <0.17977.0> (127.0.0.1:60086 -> 127.0.0.1:5672, state: starting):
2025-04-02 05:53:15.597951+00:00 [error] <0.17977.0> PLAIN login refused: user 'zulip' - invalid credentials
2025-04-02 05:53:15.603483+00:00 [info] <0.17977.0> closing AMQP connection <0.17977.0> (127.0.0.1:60086 -> 127.0.0.1:5672)Root cause: Tornade cannot access rabbitmq on zulip user due to invalid credentials. Password is stored in /etc/zulip/zulip-secrets.conf as rabbitmq_password. It should match actual password stored in rabbitmq. However, if it does not match for some reason, for example, accidentally rabbitmq_password in zulip-secrets.conf is modified and saved, authentication fails.
Fix: run the following commands to recreate zulip user on rabbitmq and restart rabbitmq and Chat server application.
(Run as root)
# /home/zulip/deployments/current/scripts/setup/configure-rabbitmq
Deleting user "zulip" ...
Deleting user "zulip" ...
Deleting user "guest" ...
Adding user "zulip" ...
Done. Don't forget to grant the user permissions to some virtual hosts! See 'rabbitmqctl help set_permissions' to learn more.
Setting tags for user "zulip" to [administrator] ...
Setting permissions for user "zulip" in vhost "/" ...
# systemctl restart rabbitmq-server.service
# systemctl status rabbitmq-server.service
# su - zulip
$ /home/zulip/deployments/current/scripts/restart-server6. Chat Scaling Issues
6.1. Tornado Sharding beyond 10 processes
Tornado sharding scales properly till 9 processes. Scaling tornado shards to 10 or more than 10 processes may fail with exception TornadoQueueClient couldn’t connect to RabbitMQ in zulip’s /var/log/zulip/server.log.
The reason being port 9810 was already in use by smokescreen.
Please follow below steps to resolve this issue:
-
Perform all below operations with zulip user
-
Stop the smokescreen using supervisorctl stop smokescreen
-
Start the chat services with zulip user using
/home/zulip/deployments/current/scripts/start-server -
Check the status if all services are up using supervisorctl status
-
If you find any services in stopped state, please try bringing them up individually. For example:
-
If
zulip-djangoisnot up, usesupervisorctl start zulip-djangoto bring it up -
If
zulip-tornado:zulip-tornado-port-9810is not up, usesupervisorctl start zulip-tornado:zulip-tornado-port-9810to bring it up.
-
7. Zimbra Server Issues
7.1. Issue - Proxy restart fails with “could not build map_hash” error
Logs:
zimbra@proxy:~$ zmproxyctl restart
Stopping proxy...nginx: [emerg] could not build map_hash, you should increase map_hash_bucket_size: 64 failed.Root cause: The hash created based on zimbraChatBaseHost and zimbraZulipChatDomainId exceeds 64 length
Fix: Increase the localconfig value
Reason: We need to set proxy_web_map_hash_bucket_size to 128 is because the length of domain+hash keys generated in chat configuration in nginx file exceeds 64 and the proxy restart fails.
zmlocalconfig -e proxy_web_map_hash_bucket_size=128
7.2. Issue - Proxy restart fails with “invalid number of arguments in map_hash_bucket_size directive” error
Logs:
zimbra@proxy:~$ zmproxyctl restart
Starting proxy...nginx: [emerg] invalid number of arguments in "map_hash_bucket_size" directive in /opt/zimbra/conf/nginx/includes/nginx.conf.web:16Root cause: map_hash_bucket_size is defined to refer the localconfig proxy_web_map_hash_bucket_size.
cat /opt/zimbra/conf/nginx/templates/nginx.conf.web.template
...
map_hash_bucket_size ${web.map_hash_bucket_size};The value can be modified and applied by executing zmproxyctl restart as described in Section 7.1.
However, there is a case that it is not referred correctly and then map_hash_bucket_size becomes empty for some reason.
cat /opt/zimbra/conf/nginx/includes/nginx.conf.web
...
map_hash_bucket_size ;Fix: Run zmcontrol restart on the proxy server instead of zmproxyctl restart.
7.3. Issue - Proxy restart fails with “host not found in upstream” error
Logs:
zimbra@proxy:~$ zmproxyctl reload
Reloading proxy...nginx: [emerg] host not found in upstream "domain1examplecom.chat1.mydomain.com:443" in /opt/zimbra/conf/nginx/includes/nginx.conf.chat.upstream:66Root cause: The hostname (FQDN) of Chat server or a realm URL for a domain cannot be resolved on the proxy server.
Fix:
-
Check that the hostname has been registered in DNS. If it does not exist, register the hostname in DNS.
-
Refresh DNS cache on the proxy server
-
It may take some time to reflect a change on DNS. If it needs be fixed immediately, you can add an entry to /etc/hosts on the proxy server as a workaround. Note that it needs to be applied on all proxy servers.
7.4. Issue - Hash not created in chat upstream file for a specific domain
Issue: an upstream for a domain is not generated in /opt/zimbra/conf/nginx/includes/nginx.conf.chat.upstream
Root cause: either zimbraChatBaseHost or zimbraZulipChatDomainId is missing for the domain due to which server hash is not generated.
Fix: Update zimbraChatBaseHost and zimbraZulipChatDomainId followed by /opt/zimbra/libexec/zmproxyconfgen command
7.5. Issue - CSRF token mismatch
Logs: CSRF token was invalid, rechecking with account object from LDAP.
Root cause: CSRF token configured on Zimbra and Chat server are not matching.
Fix: Match the CSRF
7.6. Issue - Unknown host exception
Logs: java.net.UnknownHostException: domain1examplecom.chat1.mydomain.com: Name or service not known
Root cause: The Url in the logs is not resolvable
Fix: Register the FQDN in DNS. As a temporary solution, update the required file (/etc/hosts) to make the URL resolvable.
7.7. Issue - Missing JWT key
Logs: SoapEngine - handler exception java.lang.IllegalArgumentException: Empty key
Root cause: JWT is not configured on Zimbra server
Fix: Update zimbraChatJwtSecret on Zimbra server
7.8. Issue - New account cannot be searched on Basic Chat
Account search on Basic Chat is based on gal search. If Basic Chat search does not return a newly added account, GAL may not be configured correctly on the domain. You need to check the following items:
-
If GAL mode is shown as “Internal” on Admin Console > domain setting > GAL, make sure zimbraGalMode is set to zimbra on CLI;
zmprov gd DOMAIN zimbraGalMode -
If GAL mode is “Internal” or “both”, make sure a galsync account has been configured.
-
If there are multiple mailstore servers on your environment, make sure a galsync account has been configured on each mailstore server
-
If account still cannot be searched, run the following command for all galsync accounts on the domain.
zmgsautil forceSync -a [GAL_SYNC_ACCOUNT] -n [DATA_SOURCE_NAME]
-
You can find
zimbraDataSourceNamefor theDATA_SOURCE_NAMEby runningzmprov gds [GAL_SYNC_ACCOUNT](getDataSources) command.
8. Advanced Chat UI Fails to Load for Domain with ~60K Users
The Advanced Chat UI was failing to load for a specific domain with ~60k chat users. After investigation, the issue was traced to memcached memory limitations.The issue was resolved by increasing the memory allocation in the memcached configuration.
Please refer to below config changes:
Configuration Change
To resolve the issue, the memory allocation for memcached was increased. Please find below steps:
-
Open
/etc/memcached.confwithrootuser on zulip server-
Add below line to end of file -
-
-I 2m # Increase slab page size to 2MB
The -I flag controls the max item size. Increasing it ensures that larger data structures (e.g., lists of users/messages) can be cached. -
-
Run -
systemctl restart memcached.service -
Check status of service using -
systemctl status memcached.service
Memory Usage Growth:
-
As users perform transactions (sending/receiving messages, logging in/out), memcached memory usage continues to grow.
-
Please check manual : Memcached Linux Man Page
-
Monitor the status using watch
systemctl status memcached.service
systemctl status memcached.service
● memcached.service - memcached daemon
Loaded: loaded (/lib/systemd/system/memcached.service; enabled; vendor preset: enabled)
Active: active (running) since Thu 2025-04-24 05:21:04 UTC;
Docs: man:memcached(1)
Main PID: 217874 (memcached)
Memory: 89.5M
CPU: 18.534s
CGroup: /system.slice/memcached.service
└─217874 /usr/bin/memcached -m 8036 -p 11211 -u memcache -l 127.0.0.1 -P /var/run/memcached/memcached.pid -S -I 2m9. Provision Multiple Domains Failures
9.1 Retry during chat user provisioning
During the provisioning of chat users, you may encounter failures caused by upstream timeouts, typically logged in the nginxerror.log from chat server. These failures trigger retries for creating user batches. This scenario often occurs when provisioning a large number of accounts (approximately 30,000) across multiple domains and when system resource usage particularly CPU and memory on the Chat and PostgreSQL servers is high.
During retries, the following warning may appear in chat server.log: WARN [] duplicate key value violates unique constraint "zerver_userprofile_realm_id_email_uniq" DETAIL: Key (realm_id, upper) user already exists
Solution -
-
Monitor server logs, CPU, memory, network, disk IOPS, and system load across Chat and PostgreSQL servers.
-
Tune the parallelismFactor parameter as per the recommended guidelines to reduce system strain during large-scale provisioning.
9.2 Mailbox Service Downtime During Provisioning
In some cases, the mailbox service on the ZCS server may go down unexpectedly while the zmchatprovall script is running.
Solution -
-
Restart / bring up the mailbox service on the affected ZCS server.
-
Review the provisioning status of domain accounts in the following file:
/opt/zimbra/chat/provisionedChatDomainAccountsResult.txt -
Re-run the
zmchatprovallscript for any domains marked with a failure status. -
Bring up the mailbox service on ZCS server. Check the status of domain accounts in
/opt/zimbra/chat/provisionedChatDomainAccountsResult.txt. Rerun thezmchatprovallscript for the domains marked in failure state.
Note -
-
Even if the mailbox service appears to be running, you may still encounter errors such as: "Mailbox is unresponsive. Please contact your administrator or try again later."
-
This may indicate an upstream timeout from the Chat nginx server. In such cases,
-
Review the following log for timeout messages:`/var/log/nginx/error.log`
-
Check the status of domain accounts in
/opt/zimbra/chat/provisionedChatDomainAccountsResult.txt. -
Re-run the
zmchatprovallscript for the domains affected by the timeout.
-
-
Below is an example of how the output in
/opt/zimbra/chat/provisionedChatDomainAccountsResult.txtmay appear in such scenarios :
Provisioning chat accounts for domain:
ni08.com
Accounts provisioned: 30000
Accounts not provisioned: 0
--------------------------------------------------
Provisioning chat accounts for domain:
ni09.com
Accounts provisioned: 30000
Accounts not provisioned: 0
--------------------------------------------------
Provisioning chat accounts for domain:
ni10.com
Mailbox is unresponsive please contact administrator or contact support and rerun later.
--------------------------------------------------
Provisioning chat accounts for domain:
ni11.com
Mailbox is unresponsive please contact administrator or contact support and rerun later.
--------------------------------------------------
Provisioning chat accounts for domain:
ni12.com
Mailbox is unresponsive please contact administrator or contact support and rerun later.
--------------------------------------------------
Domain(s) with failure -
ni10.com
ni11.com
ni12.comFAQs
General Questions
-
Is there any tool for Migration of chats and groups from Connect to the new Chat?
Migration is not supported from older chat solutions, and there is no plan to provide a migration tool in future.
-
Can multiple Zimbra servers connect to one Chat server?
No. Multiple authentication from two Zimbra servers to a single Chat server is not supported.
-
When is a Chat server restart required?
On configuration changes or if a component is down. For more details refer: Troubleshooting Guide.
-
Is uninstalling the Chat server supported?
Uninstallation is not supported by the underlying open source chat platform and hence not supported in Zimbra Chat.
-
Is chat supported in Classic UI?
Yes, it is supported from Zimbra Daffodil 10.1.8 release.
-
Are there benchmarks or required resources for Chat servers?
Yes, For more details refer: Scaling and Infrastructure guide section
| Performance of any chat solution heavily depends on the usage pattern of the users, so it may not match exactly with the benchmarks provided here. |
-
Can chat history be exported, erased, or edited?
Yes, chat history can be exported.
-
Is file sharing supported in Advanced Chat? Can it be restricted?
Yes. Administrators can configure restrictions in settings.py:
DISALLOWED_FILE_EXTENSIONS = ["exe", "bat", "sh", "cmd"]
MAX_FILE_UPLOAD_SIZE = 10
UPLOADED_FILES_EXPIRED_AFTER_DAYS = 30-
Is there a separate mobile application or desktop application available for Zimbra Chat?
Not yet but it is under consideration for the future roadmap.
-
Does Chat support external authentication if Zimbra does?
Yes. The chat installer will prompt for external auth details.
-
Does Chat work with LDAPS (port 636)?
Yes. It can be configured using chat installer.
Admin-Specific Questions
-
Can a domain admin manage Chat settings or manage chat accounts?
Yes, a domain admin can manage Chat settings and manage chat accounts on Admin Console. A global admin can configure grants on a domain admin as follows:
-
Create a domain admin account
-
Set admin views to see Chat settings in account, COS and domain:
-
Account List View
-
Class Of Service List View
-
Domain List View
-
-
Add the following grants to the domain admin:
adminConsoleAccountRights target type: domain, target name: DOMAIN_NAME domainAdminCosRights target type: cos, target name: COS_NAME adminConsoleDomainRights target type: domain, target name: DOMAIN_NAME listZimlet target type: zimlet, target name: zimbra-zimlet-admin-chat getZimlet target type: zimlet, target name: zimbra-zimlet-admin-chat
-
Account:
target type: domain, target name: DOMAIN_NAME set.account.zimbraFeatureZulipChatEnabled set.account.zimbraFeatureBasicOneToOneChatEnabled set.account.zimbraFeatureAdvancedChatEnabled
-
COS:
target type: cos, target name: COS_NAME set.cos.zimbraFeatureZulipChatEnabled set.cos.zimbraFeatureBasicOneToOneChatEnabled set.cos.zimbraFeatureAdvancedChatEnabled
-
Domain:
target type: domain, target name: DOMAIN_NAME set.domain.zimbraZulipChatDomainId set.domain.zimbraFeatureZulipChatEnabled set.domain.zimbraFeatureBasicOneToOneChatEnabled set.domain.zimbraFeatureAdvancedChatEnabled
-
Limitations: Regardless of whether the admin manages multiple domains on the Zimbra non-chat environment, the domain admin’s permissions allow them to manage Chat accounts (get, provision, activate, and deactivate) only within their own domain.
-
Example: You belong to
domainA(i.e. your email address isdomain_admin@domainA), and you have admin privilege to managedomainAand domainB on the Zimbra mailbox. In such case, you can manage the Chat accounts on domainA, but cannot ondomainB. If you want to manage the chat accounts ondomainB, you need to have an account ofdomainBwith a domain admin rights.
-
Can a domain administrator create a realm?
No, only a global administrator can create a realm on Chat server.
-
Can I access as Owner or Administrator of a realm on Advanced Chat?
When you log in to an admin account and go to Advanced Chat, Owner or Administrator role is applied under the following conditions:
-
Admin account with
zimbraIsDomainAdminAccount = TRUE: Owner of a realm -
Admin account with
zimbraIsAdminAccountorzimbraIsDelegatedAdminAccount = TRUE: Administrator of a realm -
Non-admin account: Member of a realm
-
Roles:
-
Owner can manage users, public channels and organization (i.e. domain or a realm) settings. Owners can do anything that an organization administrator can do.
-
Administrator can manage users, public channels and organization settings. Administrator cannot make someone an owner, or change an existing owner’s role.
-
Member has access to all public channels.
-
-
How can I restart Chat server process?
Run as root on Chat server:
# systemctl restart nginx.service
# su - zulip
$ /home/zulip/deployments/current/scripts/restart-server-
Can I see existing realms on Chat server?
Run as zulip on Chat server:
/home/zulip/deployments/current/manage.py list_realms-
Can I remove an account from Chat server completely?
When an account is removed from Zimbra, its chat account is deactivated automatically. To remove it completely: Run as zulip on Chat server:
# Dry run
/home/zulip/deployments/current/manage.py delete_user -u EMAIL_ADDRESS
# Delete user
/home/zulip/deployments/current/manage.py delete_user -u EMAIL_ADDRESS -fWarning: All chat conversation messages sent by the account will no longer be available.
-
Can I provision and manage accounts on Chat server using CLI?
Admin Console provides the following functions in domain settings:
-
Get all accounts in a realm on a Chat server
-
Provision all accounts in a domain to a Chat server
-
Provision a single account in a domain to a Chat server
-
Activate an account on a Chat server
-
Deactivate an account on a Chat server
You can do the same using CLI. Each command needs to run as zimbra user on a mailstore server. See SOAP API Reference Manual for more details.
Get all accounts in a realm on a Chat server:
$ zmsoap -z -type admin GetAllChatAccountsRequest / domain="domain1.example.com" @by="name"
<GetAllChatAccountsResponse xmlns="urn:zimbraAdmin">
<account>
<a n="is_active">false</a>
<a n="user_id">46</a>
<a n="email">deleteduser46@domain1examplecom.chat1.mydomain.com</a>
</account>
<account>
<a n="is_active">true</a>
<a n="user_id">436</a>
<a n="email">user1@domain1.example.com</a>
</account>
</GetAllChatAccountsResponse>If a user has been deleted (not deactivated), localpart has deleteduser prefix and domain reflects realm URL.
Provision all accounts in a domain to a Chat server:
$ zmsoap -z -type admin ProvChatAccountsRequest / domain="domain1.example.com" @by="name"
<ProvChatAccountsResponse xmlns="urn:zimbraAdmin">
<numSucceeded>10</numSucceeded>
<numFailed>0</numFailed>
</ProvChatAccountsResponse>Provision an account in a domain to a Chat server:
$ zmsoap -z -type admin ProvChatAccountsRequest / domain="domain1.example.com" @by="name" ../ account="user2@domain1.example.com" @by="name"
<ProvChatAccountsResponse xmlns="urn:zimbraAdmin">
<numSucceeded>1</numSucceeded>
<numFailed>0</numFailed>
</ProvChatAccountsResponse>Get an account on a Chat server:
$ zmsoap -z -type admin ManageChatAccountRequest @action="get" / account="user1@domain1.example.com" @by="name"
<ManageChatAccountResponse xmlns="urn:zimbraAdmin">
<a n="is_active">true</a>
<a n="user_id">436</a>
<a n="email">user1@domain1.example.com</a>
</ManageChatAccountResponse>Deactivate an account on a Chat server:
$ zmsoap -z -type admin ManageChatAccountRequest @action="deactivate" / account="user1@domain1.example.com" @by="name"
<ManageChatAccountResponse xmlns="urn:zimbraAdmin">
<a n="is_active">false</a>
<a n="user_id">436</a>
<a n="email">user1@domain1.example.com</a>
</ManageChatAccountResponse>Activate an account on a Chat server:
$ zmsoap -z -type admin ManageChatAccountRequest @action="activate" / account="user1@domain1.example.com" @by="name"
<ManageChatAccountResponse xmlns="urn:zimbraAdmin">
<a n="is_active">true</a>
<a n="user_id">436</a>
<a n="email">user1@domain1.example.com</a>
</ManageChatAccountResponse>-
Can I deploy Chat server without a valid SSL certificate for testing?
Yes, but not recommended for production use. If no valid SSL certificate or Let’s Encrypt is available:
-
Install Chat server with self-signed SSL type.
-
Set
ssl_allow_untrusted_certs=trueon all mailstore servers.
Run as zimbra on mailstore servers:
$ zmlocalconfig -e ssl_allow_untrusted_certs=true
$ zmmailboxdctl restartWarning: Affects all outbound communication from the mailstore server and poses a security risk. Do not use in production.
Zimbra Mobile Sync
Zimbra Mobile Sync provides over-the-air synchronization of mail, contacts, calendar and task data and device security policy enforcement between the mobile device and an account on the mailbox server.
Active Sync is a synchronization protocol defined by Microsoft. It is used to configure and sync the Zimbra mailbox server with the native client that is used on a user’s device.
Zimbra Mobile Sync is compatible with iPhone, iPod Touch, Android, Outlook (Mac and Windows), and many other phones that support the ActiveSync™ protocol.
Following are the highlights of Zimbra ActiveSync:
-
Supports protocol versions 12.1, 14.1 and 16.1.
-
Full sync support for Draft, Mail, Calendar and Contacts.
-
Supports Allow Block Quarantine Devices (a.k.a ABQ).
-
Supports Mobile Device Management (a.k.a MDM).
-
Supports configuring user-level ActiveSync protocol version.
Calendar Features:
-
Supports syncing of appointments created on Android, iOS (Changes to invitees, date/time, etc).
-
Support for recurring appointments (Modifying exceptions, whole series).
-
For Shared Calendar, supports modifications, permissions, etc.
Sharing Features:
Sharing support is available for Mail, Calendar, and Contact folders. By default the sharing is disabled. Following are the attributes to enable sharing:
zimbraMobileShareMailEnabled: Attribute to enable Mail folders sharing. Supported on cos and account levels.
zimbraMobileShareCalendarEnabled: Attribute to enable Calendar sharing. Supported on cos and account levels.
zimbraMobileShareContactEnabled: Attribute to enable Contact folders sharing. Supported on cos and account levels.
| Due to the limitation in Exchange ActiveSync protocol, it does not support implementing read-only sharing. So sharing a read-only folder/calendar is not recommended as it can cause inconsistencies between the client and server’s data. |
Following are the commands to enable sharing:
-
Mail folder sharing:
-
To enable for user:
zmprov ma <user@domain.com> zimbraMobileShareMailEnabled TRUE -
To enable for cos:
zmprov mc <cos_name> zimbraMobileShareMailEnabled TRUE
-
-
Calendar folder sharing:
-
To enable for user:
zmprov ma <user@domain.com> zimbraMobileShareCalendarEnabled TRUE -
To enable for cos:
zmprov mc <cos_name> zimbraMobileShareCalendarEnabled TRUE
-
-
Contact folder sharing:
-
To enable for user:
zmprov ma <user@domain.com> zimbraMobileShareContactEnabled TRUE -
To enable for cos:
zmprov mc <cos_name> zimbraMobileShareContactEnabled TRUE
-
| Currently, the sharing feature can only be enabled through CLI. Support in Admin Console will be added in the future release. |
Setting the ActiveSync protocol versions
Administrators can limit users' access to a specific ActiveSync protocol version by configuring it at the user, cos, and domain levels. A multi-value LDAP attribute zimbraActiveSyncVersionzimbra_activesync_versions
Syntax
Following are the details on the format to specify the versions:
-
android:14.1 - The android device will be connected over the 14.1 version.
-
iphone:16.1 - iPhone device will be connected over the 16.1 version.
-
14.1 - All device types will be connected over the 14.1 version.
-
DeviceID:14.1 - Replace DeviceID with the actual device id. The specified device id will be connected over the 14.1 version.
-
WindowsMail:14.0 - For apps sending user agent as WindowsMail, it will be connected over 14.0 version.
Examples to set the protocol versions:
-
To restrict a user to version 14.1 who is using an android device:
zmprov ma <user@domain.com> +zimbraActiveSyncVersion "android:14.1" -
To restrict a user by device id to version 16.0:
zmprov ma <user@domain.com> +zimbraActiveSyncVersion "<Device_ID>:16.0" -
To restrict users in cos to version 14.1 who are using an android device:
zmprov mc <cos_name> +zimbraActiveSyncVersion "android:14.1" -
To restrict users in a domain to version 16.0 who are using an iPhone device:
zmprov md <domain_name> +zimbraActiveSyncVersion "iphone:16.0" -
To restrict all the users in a domain to version 16.0 who are using any device:
zmprov md <domain_name> +zimbraActiveSyncVersion "16.0"
Mobile Device Security Policies
The administrator can configure mobile security policies to enforce security rules on compliant mobile devices that sync with Zimbra Collaboration accounts.
The following features can be configured to enhance the security of mobile devices.
-
Remote wipe to erase all data from the device if the mobile device is lost or stolen.
-
Device password policies to set up strong password enforcement including minimum password length, inactivity time, enforce password history, and wipe device after configured failed sign in attempts
-
S/MIME encryption policies to enable S/MIME usage and set the policies for sending and signing encrypted messages.
In addition, you can manage the following device usage options:
-
Sync settings for past calendar and email items, message size, formatting
-
Device settings, such as cameras, desktop sync, bluetooth, use of removable storage can be disabled.
Setting Up Mobile Policies in Zimbra
You can manage mobile device policies from the administration console as a Class of Service or for individual accounts.
Home → Configure → Class of Service → (COS) → Mobile Access → General
Home → Manage → Accounts → (account) → Mobile Access → GeneralThe policy configured on an individual account overrides the COS policy.
-
To set mobile policies from a COS, go to the Configure → Class of Service and double-click the COS you want to configure.
-
In order for mobile devices to sync to Zimbra, check Mobile → General → Enable Mobile Sync.
-
Check Enable Mobile Policy to set up mobile security policies that enforce security rules.
-
To support older devices that do not support some or all device security policies, check Allow non-provisionable devices.
-
If a device does not acknowledge or support all assigned policies, but you want to allow the device to download messages, check Allow partial policy enforcement on devices.
-
The refresh interval for policy refresh on a device’s default setting is 24 hours.
-
Configure the appropriate policies in the other sections. See Mobile Device Security Policies Attributes for a description of the settings you can configure. Managing Mobile Devices
-
Click Save.
Mobile Device Security Policies Attributes
The following attributes can be configured from the administration console to establish mobile policies.
General Settings
| Component | Deprecation Statement |
|---|---|
Enable Mobile Sync |
In order for mobile devices to sync to Zimbra Collaboration Server, Enable Mobile Sync must be checked. Users have two-way, over the air synchronization of mail, contacts, and calendar data between mobile devices and the Zimbra server. |
Enable Mobile Policy |
Check this box to set up mobile security policies that enforce security rules on compliant mobile devices. You can enforce general security policies including password rules and set up local wipe capability on compliant devices. After the mobile policy is set up, the next time a mobile device sends a request to the server, mobile devices that are capable of enforcing security policies automatically set up the rules you implement and immediately enforces them. |
Allow non-provisionable devices |
If this is enabled, old devices that do not support device security policy enforcement can still access the server. |
Allow partial policy enforcement on device |
If a device does not acknowledges all policies that are downloaded, Zimbra still allows the device to continue downloading messages. |
Refresh Interval (hours): |
Specifies the amount of time in minutes before Zimbra enforces the policy refresh on the device by sending "449 Retry after Provision" response to Sync request. Default is 24 hours. |
Password Settings
| Component | Deprecation Statement |
|---|---|
Require password |
User must create a password on the mobile device. |
Minimum password length |
Minimum number of characters for the password. Default is 4. The maximum length is 16 characters. |
Require alphanumeric password |
Requires that the password include both numeric and alpha characters. |
Minimum complex characters required |
Minimum number of complex characters that must be in the password. This is any character that is not a letter. Default is 0 (none) |
Allow simple password |
Simple passwords can be created. A simple device password is a password that has a specific pattern, such as 2468, 1111. Not enabled by default. |
Enable password recovery |
Device password is stored n the server and can be recovered. Enabled by default. |
Allow device encryption |
If enabled, device encryption is enabled on the mobile phone. Enabled by default; |
Require device encryption |
If enabled, encryption must be implement on the device to synchronize with the server. Not enabled by default. |
Password re-entry required after inactivity (min) |
Length of time the device remains inactive before the password must be entered to reactivate the device. Default is 15 minutes. |
Failed attempts allowed |
Specifies the number of failed log in attempts to the device before the device automatically initiates a local wipe. The device does not need to contact the server for this to happen. Default is 4. |
Expiration (days) |
Length of time in days that a password can be used. After this number of days, a new password must be created. Default is 0, the password does not expire. |
Passwords stored to prevent reuse |
Number of unique passwords that a user must create before an old password can be used. Default is 8. |
S/MIME Settings
| Component | Deprecation Statement |
|---|---|
Enable S/MIME public key encryption and signing |
In order to use S/MIME encryption on a mobile device this must be checked. The S/MIME feature must also be enabled in the COS Features page. |
Require device to send signed messages |
Device must send signed S/MIME messages. Not enabled by default. |
Require S/MIME algorithm for signing |
Algorithm must be used when signing a message. Not enabled by default. |
Require device to send encrypted messages |
Specifies whether S/MIME messages must be encrypted. Not enabled by default. |
Require S/MIME algorithm for encrypting |
A required algorithm must be used when signing a message. Not enabled by default. |
Algorithm negotiation |
How a messaging application on the device can negotiate the encryption algorithm if a recipient’s certificate does not support the specified encryption algorithm. Select from Block Negotiation; Strong Algorithm Only, or Allow Any Algorithm. Default is Allow Any Algorithm. |
Allow S/MIME software certificates |
Allow S/MIME software certificates. Default is to allow. |
Sync Settings
| Component | Deprecation Statement |
|---|---|
Past calendar items sync’d |
Maximum range of calendar days that can be synchronized to the device. Default is two weeks. |
Past email items sync’d |
Maximum number of days of email items to synchronize to the device. Default is 3 days. |
Limit plain text message size (KB) |
Maximum size at which email messages are truncated when synchronized to the device. Default is to not set a maximum size. |
Allow direct push while roaming |
Mobile device must synchronize manually while roaming. Default is not to. |
Allow HTML formatted messages |
Enables HTML email on the device. If this is disabled, all email is converted to plain text before synchronization occurs. Default is to enable HTML formatting. |
Limit HTML message size (KB) |
Maximum size at which HTML-formatted email messages are synchronized to the devices. The value is specified in KB. Default is to not set a maximum size. |
Device Settings
| Component | Deprecation Statement |
|---|---|
Allow removable storage |
Mobile device can access information stored on a storage card. Default is TRUE. |
Allow camera |
Specifies that the camera on the device can be used. Default is TRUE. |
Allow Wi-Fi |
Specifies that wireless Internet access is allowed on the device. Default is TRUE. |
Allow Infrared |
Specifies that an infrared connection is allowed on the device. Default is TRUE. |
Allow sharing |
Specifies that the mobile device can be used as a modem to connect a computer to the Internet. Default is TRUE. |
Allow remote desktop |
Specifies that the mobile device can initiate a remote desktop connection. Default is TRUE. |
Allow desktop sync |
Specifies that the mobile device can synchronize with a desktop computer through a cable. Default is TRUE. |
Allow bluetooth |
By default Bluetooth capabilities are allowed on the device. Select from Allow, Disable, Hands-Free Only. |
Device Applications
| Component | Deprecation Statement |
|---|---|
Allow browser |
Microsoft® Pocket Internet Explorer is allowed on the mobile device by default. This does not affect third-party browsers. |
Allow consumer mail |
Users can configure a personal email account on the mobile device. This parameter does not control access to emails using third-party mobile device email programs. |
Allow POP or IMAP mail |
Users can configure a POP3 or IMAP4 email account on the device. This parameter doe not control access by third-party email programs. |
Allow text messaging |
Allow users to use text messaging on the device. |
Allow unsigned applications |
Allows unsigned applications to be used on the device. |
Allow unsigned install packages |
Allows unsigned installation packages on the device. |
Approved Application Lists
| Component | Deprecation Statement |
|---|---|
Approved Applications |
This setting stores a list of approved applications that can be run on the mobile device. |
Blocked Applications |
This setting specifies a list of applications that cannot be run. |
Mobile Device Management
After the mobile policy is set up, the next time a mobile device sends a request to the server, mobile devices that are capable of enforcing security policies automatically set up the rules and immediately enforces them.
For example, if a password has not been set up on the device or the password is not as strong as required by the mobile policy, the user must fix the password before syncing with the server. Once the server confirms that the policy is enforced on the mobile device, the device can sync.
If a mobile device is lost or stolen, the device is protected by the following policy rules:
-
When the Password re-entry required after inactivity (min) is configured, after the number of minutes configured, the device is locked. To unlock the device, users must re enter their password.
-
When the Failure attempts allowed is configured, after the password is entered incorrectly more than the specified number of times, a locally (generated by the device) initiated wipe of the device is performed. This erases all data on the device.
In addition to the rules set up from the administration console to perform a local device wipe, users can initiate a remote wipe from their ZWC account to erase all data on lost, stolen, or retired devices.
Zimbra Mobile Device Management (a.k.a MDM) functionality is also found within the Admin Console where the mobile devices can be managed at the Global, COS, Domain and Account levels:
Configure → Global Settings → Mobile
Configure → COS → Mobile
Configure → Domain → Mobile
Configure → Manager → Accounts → (User) → Mobile-
Mobile policy and registered device management settings are located within COS’s and Account.
-
Only the registered device management settings is available within the Global and Domain sections.
Mobile Device Management Allow/Block Rules (ABQ)
Device Management Allow/Block Rules supports regular expression rules which can be created to allow or block devices from connecting to the Zimbra Collaboration server. These rules are applied using the command line and can be created at the global or domain level by using zimbraMobileAllowedDevices and zimbraMobileBlockedDevices multi-valued attributes. These attributes can be set at the Global or Domain level.
zimbraMobileAllowedDevices
Only devices that match what is configured within zimbraMobileAllowedDevices will be allowed to sync using the Activesync protocol, all other devices will be blocked. For example, if iPhone* is configured, then only devices that report as iPhone~ will be permitted to sync.
zimbraMobileBlockedDevices
Only devices that match what is configured within zimbraMobileBlockedDevices will be blocked, all other devices will be allowed to connect. For example, if iPhone* is added, then all devices that reports as iPhone~ will be blocked, and all other devices such as Android, and Windows will be permitted to sync.
Command Line Examples
The following are examples of how to create Allow and Block rules from the command line at the Global and Domain level:
Since these are multi-value attributes, you will need to use a + or - when adding or removing a rule. If neither are used, all current configuration will be replaced with the current executed rule.
|
-
Block only iPhone devices:
Global zmprov mcf +zimbraMobileBlockedDevices *iPhone*Domain zmprov md domain_name +zimbraMobileBlockedDevices *iPhone* -
Allow only iPhone devices:
Global zmprov mcf +zimbraMobileAllowedDevices *iPhone*Domain zmprov md domain_name +zimbraMobileAllowedDevices *iPhone* -
List all existing Allow or Blocked Rules at the global level:
Global zmprov gcf zimbraMobileAllowedDevices zmprov gcf zimbraMobileBlockedDevicesDomain zmprov gd domain_name zimbraMobileAllowedDevices zmprov gd domain_name zimbraMobileBlockedDevices
Quarantined Notification
A quarantine notification can be configured for a specific time interval for all new quarantined devices. This will need to be configured on each mailbox server using zmlocalconfig command.
Following are the attributes used to configure the notification email body and subject:
-
zimbra_mobile_mdm_notification_email_body : Attribute used to customize the notification email body. If not set, default body will be used.
-
zimbra_mobile_mdm_notification_email_subject : Attribute used to customize the notification email subject. If not set, default body will be used.
To view the email body, execute:
zmlocalconfig zimbra_mobile_mdm_notification_email_bodyTo change the notification email body, execute:
zmlocalconfig -e zimbra_mobile_mdm_notification_email_body "new notification body"To view the notification email subject, execute:
zmlocalconfig zimbra_mobile_mdm_notification_email_subjectTo change the notification email subject, execute:
zmlocalconfig -e zimbra_mobile_mdm_notification_email_subject "new notification subject"Setting the Quarantine Notification Interval
The zmmdmmailschedule command is used for setting the notification interval. By default, there is no notification interval set.
Syntax
zmmdmmailschedule [-l|-h|-f|-e]Options:
| Long Name | Short Name | Description |
|---|---|---|
-l |
list |
Print the existing schedule. |
-h |
help |
Get help about zmmdmmailschedule (default command). |
-f |
flush |
Remove the current schedule (cancel all Zimbra MDM devices email schedule policy). |
-e |
edit |
Edit the current schedule with a specified schedule. |
Syntax to edit the notification intervals:
zmmdmmailschedule -e {<45m | 6h | 1d | 0>} admin_emailCLI examples to set the notification intervals:
-
Minutes: To set the quarantine notification to be sent to admin@domain.com at every 45 minutes, execute the following command:
zmmdmmailschedule -e 45m admin@domain.com
Admin email is an optional input. If the admin email address is not provided then emails will be sent to all configured admins at every 45 minutes. For example: zmmdmmailschedule -e 45m.
|
-
Hours: To set the quarantine notification to be sent to admin@domain.com at every 6 hours, execute the following command:
zmmdmmailschedule -e 6h admin@domain.com -
Day: To set the quarantine notification to be sent to admin@domain.com at every 3 days, execute the following command:
zmmdmmailschedule -e 3d admin@domain.com -
Zero: To disable quarantine notification, execute the following command:
zmmdmmailschedule -e 0 admin@domain.com -
flush: To remove the quarantine notification schedule, execute the following command:
zmmdmmailschedule -f
Registered Devices
The Registered Devices section enables the Admin to take various action for the user.
Following are the supported actions
| Action Name | Description | Status after the action is executed | ||
|---|---|---|---|---|
Remove From List |
Remove the device from the list. This will not cause a reset of sync data, but will cause a reset of policies on the next sync. |
Waiting for device |
||
Suspend Sync |
Suspends the device. New messages will not be synced to the device. But the old messages will be accessible. |
Suspended |
||
Resume Sync |
Resumes the sync to the mobile device. |
Waiting for device. Once connected successfully and sync is resumed, the status is changed to Active. |
||
Wipe Device |
Resets the mobile Device.
|
Wipe Pending. Once the action is completed successfully, the status is changed to Wipe Completed. |
||
Cancel Wipe |
Cancel’s the Wipe Device operation.
|
Waiting for Device |
||
Block |
Blocks the device and removes the synced messages from the device. |
Blocked |
||
Remove Account |
Removes the account from the mobile |
Remove account pending. Once the account is removed successfully, the status is changed to Account Removed. |
||
Cancel Remove Account |
Cancels the Remove Account operation.
|
Once the device connects and syncs emails, the status is changed to Active. |
Supporting Autodiscover
Zimbra supports the Autodiscover service so that users can provision mobile devices for their Zimbra accounts without having to know the server settings. Autodiscover returns the required server settings after users enter their email address and password.
Autodiscover is enabled by default. For autodiscover to work, you must configure a valid SSL certificate from a certification authority.
The recommended type of certificate to use is a Unified Communications Certificate or UCC. This certificate lets you add multiple host names in the Subject Alternative Name field. For autodiscover to work, the Subject Alternative Name field must include the hostnames users are connecting to.
You must have a valid domain name service (DNS SRV record) for autodiscover.<domain>.com so that the client devices can locate and connect to the autodiscover service.
Use the Install Certificates wizard on the administration console to generate the certificate signing request and to install the signed certificate when received. Unified Communications Certificates can be issued by many certification authorities.
When you complete the request you must have a valid domain name service (DNS SRV record) for autodiscover.<domain>.com. Configure the Subject Alternative Name (SAN) field with the valid domain names that you use. The alternative name should include the domain autodiscover.<company>.com. Include all the domain names required for your environment in the Subject Alternative Name field.
| Make sure that the web server mode is https, both, redirect, or mixed as the autodiscover and other communications from devices is HTTPS. |
Set Up Mobile Synchronization for User Accounts
Mobile sync is enabled either in the COS profiles for the account or on individual accounts. In most cases, no additional plug-ins are required.
Users might need to configure the following on their in the mobile device to sync to their Zimbra account if they don’t have auto discover.
-
Server name (address): Enter the fully qualified host name of the user’s Zimbra Collaboration mailbox server.
-
User name: Enter the user’s primary Zimbra Collaboration account name.
-
Domain: Enter the user’s Zimbra Collaboration domain name (DNS).
-
SSL certificate from the server might have to be added to the device as trusted if SSL is used when the certification is self-signed.
Users can sync their Zimbra account to their mobile device. They can send email, create appointments, and add contacts to their address book.
For details about specific device setup, see the Mobile Device Setup pages on the Zimbra Wiki.
Change Mobile Device Password Policy
If a mobile device is locked by the Zimbra Collaboration mobile password policy, the PIN requirement must be removed to resync the device.
Home → Manage → Accounts → account → Mobile-
In the administration console, open the user account to be modified.
-
On the Mobile page, uncheck Force pin on device. After the password policy has been disabled, the user must resync the device.
User’s Mobile Device Self-Care Features
Users can directly manage the following device functions.
-
Perform a remote wipe of a device. If a mobile device is lost, stolen, or no longer being used, users can initiate a remote wipe from their ZWC account to erase all data from the mobile device. The device is returned to its original factory settings.
-
Suspend a sync that has been initiated from the mobile device and resume the sync to the device.
-
Delete the device from their list. If a device is deleted from the list and the device attempts to sync after that, the server forces the device to fetch the the policy again on the next sync.
Add account to Outlook and Mobile Apps
This section provides step-by-step instructions to configure Zimbra accounts using:
-
Zimbra Connector for Outlook (ZCO)
-
Exchange Web Services (EWS)
-
ActiveSync on mobile devices (iOS & Android)
| The Outlook mobile app (iOS/Android) does not support Free/Busy or Scheduling Assistant when using ActiveSync. For more details, please refer to Free/Busy for Outlook App section. |
| Shared calendar access is currently disabled in Outlook mobile app, as we’ve observed issues with modify/delete actions. We’re working on delivering full and reliable support in an upcoming release. |
Zimbra Connector for Outlook (ZCO)
-
Download ZCO Installer:
-
Go to: https://www.zimbra.com/product/addons/zimbra-connector-for-outlook-download/
-
Download the appropriate installer based on your Windows OS bitness (x64 or x32).
-
-
Install ZCO:
-
Run the
.msiinstaller and follow on-screen prompts.
-
-
Access Mail Profiles:
-
Go to
Control Panel > Mail > Show Profiles.
-
-
Create a New Profile:
-
Click Add Profile → Choose Manual Configuration → Select Zimbra Collaboration Server.
-
-
Enter Account Details:
-
Email: <email_address>
-
Password: <zimbra_password>
-
Server: <server_name>
-
-
Finalize Profile Setup:
-
Choose "Prompt for a profile to be used".
-
Click OK to save settings.
-
-
Open Outlook:
-
Launch Outlook and select the newly created profile to access your Zimbra account.
-
EWS (Exchange Web Services) - macOS
Prerequisites
Ensure your Zimbra account is Active and that EWS (Exchange Web Services) is enabled on the server.
Steps
-
Open Outlook on your Mac.
-
From the Outlook menu, select Legacy Outlook mode (if you’re using the new Outlook interface).
-
Go to Settings → Accounts → "+" icon → Add an Account.
-
Enter your full Zimbra email address and click Continue.
If you’re using a Microsoft 365 subscription or account, Outlook may try to auto-configure the account using Microsoft 365. In that case, follow the additional step: On the "Connecting to Microsoft 365…" screen, click on the "Not Microsoft 365?" link at the top-right corner. -
A list of email providers will appear. Select Exchange.
-
Enter the following details:
-
Method: Select Username and Password
-
Email Address: <email_address>
-
DOMAIN\username or Email Address: <email_address>
-
Password: <zimbra_password>
-
Server:
<zimbra_server_name>(This field is optional if Auto Discover is setup)
-
-
Click Add Account.
-
Once setup is complete, click Done to finish.
Notes
-
If you’re unsure of the Zimbra EWS server name, please contact your administrator.
-
If prompted for account type, always select Exchange (not IMAP or Microsoft 365).
-
Modern Outlook versions may default to Microsoft services; always use the “Not Microsoft 365?” link to override that behavior for Zimbra accounts.
ActiveSync – Mobile Devices
iOS – Outlook App (Microsoft Outlook)
-
If Microsoft Outlook app is not installed, download and install it from the App Store.
-
Launch the Microsoft Outlook app.
-
Add Account:
-
If it’s your first time: Tap Get Started → Add Account
-
If already using Outlook: Tap Home (your initials) → Settings → General → Accounts → Add Account → Email Account → Enter email address → Add Account
-
-
Enter your full email address and tap Add Account.
-
Depending on what Outlook detects, follow one of the below sub-steps:
-
If Outlook shows an IMAP screen:
-
Tap Not IMAP? in the top-right corner.
-
Tap Change Account Provider.
-
Select Exchange.
-
-
If Outlook shows a Microsoft 365 login screen:
-
Tap Not Microsoft 365? in the top-right corner.
-
Tap Change Account Provider.
-
Select Exchange.
-
-
-
Enter Account Details:
-
Email: <email_address>
-
Password: <zimbra_password>
-
Server: <server_name>
-
Domain: (Leave blank unless specified by your IT team)
-
Username: enter user-part of the email (e.g., for john.doe@example.com, enter john.doe)
-
Tap Sign In to complete setup.
-
-
Outlook will verify the account and begin syncing mail, calendar, and contacts.
iOS – Apple Mail App
-
Go to
Settings → Apps → Mail → Mail Accounts → Add Account. -
Choose Microsoft Exchange.
-
Enter:
-
Email: <email_address>
-
Description: optional label like "Work Account" → Tap Next
-
-
If Autodiscover is setup:
-
Tap Sign In → Enter password → Tap Next
-
Select the services to sync (Mail, Contacts, Calendar).
-
Tap Save.
-
-
-
If Autodiscover is not setup
-
Tap Configure Manually → Enter password → Tap Next
-
Enter Server: <server_name>
-
Enter Username: <email_address> → Tap Next
-
Select the services to sync (Mail, Contacts, Calendar).
-
Tap Save.
-
Android – Outlook App
-
If Microsoft Outlook app is not installed, download and install it from the Play Store.
-
Launch the Microsoft Outlook app.
-
Depending on your current Outlook setup:
-
If no accounts are configured, Outlook will show a “Add Account” screen directly.
-
If you already have an account configured, follow these steps to add another:
-
Tap the Exchange logo at the top-left of the app (this opens the side menu).
-
Tap the Settings icon at the bottom-left corner.
-
Go to General > Accounts.
-
Tap Add Account.
-
Tap Add an email account.
-
-
-
Enter your email address and tap Continue.
-
When prompted to choose the account type, select IMAP.
This is a temporary selection required to proceed to advanced options — we will switch to Exchange in the next steps. -
On the IMAP settings screen, tap the ? (Help icon) in the top-right corner.
-
From the help menu, tap Change Account Provider.
-
In the list of account types, select Exchange.
-
Enable ADVANCED SETTINGS
-
Enter:
-
Email: It should be pre-filled. If not, enter your <email_address>.
-
Password: <zimbra_password>
-
Server: <server_name>
-
Domain: (Leave blank unless specified by your IT team)
-
Username: enter user-part of your email (e.g., john.doe)
-
-
Once all details are entered, tap the ✔️ (tick mark icon) at the top-right corner of the screen to initiate the connection.
-
Outlook will validate the configuration. After successfull validation Outlook app will begin syncing emails, calendar, and contacts.
Android – Gmail App
-
Open Gmail App → Tap Profile icon (top-right) → Add another account.
-
Select Exchange and Office 365.
-
Enter:
-
Email: Enter <email_address> → Tap Next
-
Password: Enter <zimbra_password> → Tap Next
-
Server: <server_name> (if prompted)
-
-
Tap Done to finish.
-
To access the account, tap Profile icon (top-right) → Tap on the configured account.
Free/Busy Availability Not Supported in Outlook Mobile App
When using the Outlook mobile app (iOS/Android) with a Zimbra account configured via Exchange ActiveSync, Free/Busy availability information is not displayed. This includes the absence of the Scheduling Assistant feature during meeting creation.
This is a known limitation of the Outlook mobile app, which currently only supports calendar availability features for Office 365 or Microsoft Exchange accounts. The Outlook app does not make Free/Busy lookup requests to Zimbra servers over the ActiveSync protocol.
Recommended Alternatives
To view Free/Busy availability and access full calendar scheduling features, we recommend one of the following:
-
Use the native Calendar app on iOS or Android, which fully supports Free/Busy via ActiveSync.
-
Access your account through Zimbra Web Client (webmail).
-
Use the official Zimbra Mobile App (if available in your environment).
We are continuously monitoring updates from Microsoft and will update this guidance if future versions of the Outlook app expand support.
Backup and Restore
Introduction
Zimbra Collaboration includes a configurable backup manager that resides on every Zimbra Collaboration server and performs both backup and restore functions. You do not have to stop the Zimbra Collaboration server in order to run the backup process.
This section describes how data is backed up and restored and how to use the the Admin User Interface (Admin Console) and CLI tools to backup or restore your Zimbra Collaboration mailbox server. In addition, this chapter also provides information and general guidelines for disaster recovery.
| For Backup & Restore feature, Zimbra Collaboration Daffodil (v10) currently does not support storing backup files on S3 external storage or restoring backup from S3 external storage. |
Starting with Zimbra Collaboration Daffodil version 10.1.16 onwards, the Backup and Restore feature is enhanced with a new implementation referred to as Backup Engine v2. These enhancements are designed to improve backup storage efficiency, reduce backup size, and optimize backup performance while preserving full backward compatibility with existing legacy backups and workflows.
| The enhancements apply only to new backup sessions created after upgrade. Existing backup data remains unchanged and fully restorable. |
Backup Engine v2 – Summary of Enhancements
Backup Engine v2 introduces the following improvements:
-
Session-level deduplication
-
Deduplication support for internal and external storage volumes
-
Modern Zstandard (zstd) compression
-
Optional cross-session deduplication for long-term storage efficiency
-
Enhanced admin controls with safe defaults
What Remains Unchanged
-
Backup scheduling and execution workflows
-
Existing backup labels and directory layout
-
Restore commands and procedures
-
Ability to restore all legacy backups
Deduplication
Introduction
This release enhances the legacy Backup & Restore system by extending deduplication support to blobs stored on external storage, in addition to internal volumes.
Deduplication eliminates redundant data during backup, improving storage efficiency and reducing backup size, without impacting restore behavior or existing workflows.
What’s New in This Release
-
Deduplication is now supported for blobs stored on external storage.
-
Identical data is stored only once during a backup session, even if it appears across multiple mailboxes.
-
Backup size and storage usage are reduced while maintaining full restore compatibility.
These improvements are applied automatically to new backup sessions after upgrade.
Why These Enhancements Were Added
Reduced Storage Usage
Deduplication eliminates redundant copies of identical data, with high impact for:
-
Attachments
-
Broadcast emails
-
Shared documents
Improved Performance
-
Reduced disk I/O
-
Faster backup and restore operations
-
Reduced network transfer, where applicable
Lower Infrastructure Cost
-
Reduced disk requirements
-
Smaller backup archives
-
Lower cloud or object storage consumption
Efficient Scaling
Deduplication is especially effective in:
-
Large organizations
-
Multi-user environments
-
Multi-store deployments
Backup Engine Behavior After Upgrade
After the upgrade, the backup engine continues to ensure backward compatibility with existing backups while introducing internal improvements for performance, reliability, and storage efficiency.
Key behaviors:
-
Existing backups remain usable and can be restored without any manual intervention.
-
New backups follow the upgraded engine logic, including improved handling of metadata, streaming, and storage optimizations.
-
Deduplication and compression are applied only to new backup sessions.
-
Previously created backup data remains unchanged.
-
The engine automatically detects the backup format/version and applies the appropriate processing logic.
-
No re-indexing or full re-backup is required unless explicitly configured by the administrator.
-
Backup and restore operations remain transparent, with no workflow changes required post-upgrade.
Deduplication Overview
What Deduplication Does
Deduplication is a storage optimization technique that ensures identical content is stored only once, while multiple logical references point to the same physical data.
Instead of storing duplicate copies:
-
A single unique instance is stored
-
Subsequent duplicates are replaced with logical references
This reduces:
-
Storage consumption
-
I/O operations
Scope of Deduplication
In Zimbra, deduplication applies to identical blobs (identical MIME content).
This includes:
-
Mail content
-
Attachments
-
Briefcase items
-
Calendar items with identical blobs
Deduplication operates at the blob level. Two blobs must be byte-for-byte identical to be deduplicated.
Example:
If a user sends an email with the same attachment to multiple recipients, each recipient mailbox contains a duplicate copy of the blob. Deduplication ensures the blob is stored only once during the backup session.
Session-Level Deduplication Model
Deduplication is applied within the scope of a single backup session.
Deduplication Boundary per Session
-
Only blobs processed during the same backup run are compared.
-
No lookup is performed against:
-
Previous backup sessions
-
Historical backups
-
External backup stores
-
Characteristics
-
Deduplication map exists only in memory for the duration of the session.
-
The map is cleared when the backup completes.
This design ensures predictable performance and avoids cross-session dependencies.
How Deduplication Works (High-Level Flow)
Full Backup Flow
During a full backup, the engine processes all eligible data (mail items, attachments, blobs) and applies deduplication as part of the data write pipeline.
High-level steps:
-
Backup session starts
-
Items are scanned and read sequentially
-
For each data blob:
-
Blob digest is computed
-
Deduplication check is performed
-
-
Based on the dedupe result:
-
New blob → stored physically
-
Duplicate blob → reference created in metadata
-
-
Metadata is written linking items to blobs
-
Backup session completes
Blob Referencing Explained
-
Each unique blob is stored once.
-
A mapping of blob digest → blob ID is maintained.
-
When duplicates are detected:
-
No new blob is written.
-
Metadata references the existing blob ID.
-
This ensures efficient storage while preserving restore accuracy.
LDAP Configuration Attributes
To support Deduplication, the following LDAP attribute have been introduced.
zimbraBackupDeduplication
Enables or disables deduplication.
Allowed values:
-
dedupe– Enables deduplication (default) -
nodedupe– Disables deduplication
CLI Commands and Examples
Check Current Deduplication State
Server-level:
zmprov gs `zmhostname` zimbraBackupDeduplication
Global-level:
zmprov gcf zimbraBackupDeduplication
Enable or Disable Deduplication
Server-level:
zmprov ms `zmhostname` zimbraBackupDeduplication dedupe zmprov ms `zmhostname` zimbraBackupDeduplication nodedupe
Global-level:
zmprov mcf zimbraBackupDeduplication dedupe zmprov mcf zimbraBackupDeduplication nodedupe
Run Manual Backup with Deduplication
Enable dedupe via LDAP or use CLI flags:
zmbackup -a all -f --dedupe
Override compression:
zmbackup -a all -f --dedupe --zstd zmbackup -a all -f --dedupe --nocompression
Force session-level dedupe when CSD is enabled:
zmbackup -a all -f --nocsd
For updates to the Admin Console, please refer to the Admin Console section.
Multinode Behavior
Deduplication Scope in Multinode Deployments
In a multinode environment, deduplication is scoped per mailstore and per backup session.
Key principle:
Deduplication does NOT span across mailstores or nodes.
Each mailstore:
-
Runs its own backup process
-
Maintains its own persistent deduplication index backed by RocksDB
-
Writes backup data independently
This design ensures:
-
No cross-node coordination overhead
-
No distributed locking
-
Predictable performance and failure isolation
Example: Same Attachment Across Two Mailstores
-
Mailstore A and Mailstore B contain the same attachment
-
Backups run independently on each store
Result:
-
One blob stored in Mailstore A backup
-
One blob stored in Mailstore B backup
-
No cross-store deduplication
Logging and Monitoring
Mailbox logs record:
-
Backup type generated Example:
Session-level dedupe backup initiated using Zstd compression. -
Duplicate blob count at the account level Example:
Duplicate blobs count: 5
These logs help validate deduplication effectiveness and backup behavior.
Compression
Overview
Backup Engine v2 introduces support for Zstandard (ZSTD) compression, a modern, general-purpose compression algorithm designed to provide a significantly better balance between compression ratio and performance compared to legacy ZIP (deflate).
In the context of Zimbra backups:
-
ZSTD is used for dedupe-enabled backups (Backup Engine v2) when
zimbraBackupDedupeCompressionTypeis set tozstd. -
Blobs are written as TAR + ZSTD chunks for deduplicated backups.
-
Each unique blob is compressed once and then referenced via RocksDB and JSON metadata.
-
Compression level is tunable using the localconfig key
backup_zstd_compression_level(range: 1–22, default: 3). -
ZSTD is optimized for fast decompression and good CPU efficiency, which is critical for backup and restore SLAs.
This makes ZSTD well-suited for large Zimbra datasets dominated by email text and attachments, especially in environments with high duplication across accounts and over time.
Benefits Compared to ZIP
Legacy backups used ZIP/deflate compression (--zip, --zipStore, --noZip). Multiple internal benchmarks and performance test runs show that ZSTD consistently outperforms ZIP for backup workloads.
Performance Characteristics
ZSTD with deduplication often achieves higher throughput and shorter wall-clock times than ZIP because:
-
Compression is faster at practical levels (1–5).
-
Less I/O is performed due to deduplication; unique blobs are written once.
-
ZSTD decompression is faster and often comparable or better than ZIP, improving restore times.
For realistic backup workloads (moderate ZSTD levels, high duplication, text-heavy data), ZSTD provides:
-
Smaller backup size than ZIP.
-
Shorter or comparable backup windows.
-
Lower CPU per byte stored compared to aggressive ZIP or very high ZSTD levels.
Internal and External Volume Behavior
Zimbra Backup Engine v2 applies uniform deduplication and compression across both internal and external mailstore volumes.
Mailstore Volumes vs Backup Store
Mailstore volumes may be:
-
Internal – local filesystem volumes
-
External – S3-backed volumes configured via
zmvolume/zms3config
Backup data is written to a local backup store. Blobs from both internal and external volumes are normalized into deduplicated, ZSTD-compressed blobs.
The dedupe index (RocksDB) is global across volumes and does not differentiate between internal or external origins.
This provides uniform behavior:
-
Identical blobs on internal and external volumes are stored once.
-
Cross-session dedupe avoids re-storing blobs regardless of origin volume.
Impact on External-Heavy Deployments
Large environments often store 80–90% of blobs on S3. Previously, dedupe benefits were limited for external data.
With Backup Engine v2:
-
All blobs (internal and external) are deduped using the same RocksDB index.
-
ZSTD compresses deduped blob effectively.
-
Benchmarks with 40–60% duplicate external data show final backup sizes around 25–30% of original size, or smaller when indexes are excluded.
How V2 Backup Works
Compression Flow During Full Backup
This applies to session-level dedupe (V2) and cross-session dedupe backups when:
-
zimbraBackupDeduplication = dedupe -
zimbraBackupDedupeCompressionType = zstd(ornocompression)
High-level flow:
-
Backup session starts (
zmbackup -f) -
BackupModule reads server-level attributes
-
Backup type is selected (legacy, or V2)
-
Mail items are enumerated
-
Blobs are located (internal or external)
-
Deduplication check is performed using RocksDB
-
New blobs are compressed and written
-
Metadata is created
-
Session completes
Blob Storage and ZSTD Compression
For new blobs:
-
Blob is wrapped into a TAR entry
-
Compressed using ZSTD at
backup_zstd_compression_level -
Written to
blob-chunks/in:-
Session directory (V2), or
-
COMMON session backup directory (V2 with CSD)
-
Metadata updates:
-
RocksDB entry: digest, location, compression type, size, refcount
-
Account items metadata JSON under
/accounts
Session Structure
Session-level dedupe (V2):
-
blob-chunks/ -
rocksdb/ -
accounts/ -
ldap/ -
sys/ -
session.xml
CSD COMMON (V2 + CSD Enabled):
-
blob-chunks/ -
rocksdb/ -
accounts/ -
ldap/ -
sys/ -
session.xml
CSD DELTA (V2 + CSD Enabled):
-
No
blob-chunks/orrocksdb/ -
Contains:
-
accounts/ -
ldap/ -
sys/ -
session.xml(points to COMMON)
-
Restore Decompression Behavior
ZSTD compression is fully transparent during restore.
Restore flow:
-
Admin runs
zmrestoreorzmrestoreoffline -
RestoreModule locates backup session(s)
-
Metadata is resolved from account JSON and RocksDB
-
Compressed blob data is read
-
Blob is decompressed (if ZSTD) or streamed directly
-
Blob is written to target mailstore volume
CSD restores combine metadata from COMMON and DELTAs transparently.
Configuration Attributes
Server-Level LDAP Attributes
zimbraBackupDeduplication
Controls whether deduplication is used.
Allowed values:
-
dedupe– (Default) Enables deduplication (V2) -
nodedupe– Legacy behavior
zimbraBackupDedupeCompressionType
Defines compression for deduped backups.
Allowed values:
-
zstd(Default) -
nocompression
Applies only when dedupe is enabled.
Local Configuration (Advanced Tuning)
Localconfig keys control performance only and do not change on-disk format.
Examples include:
-
backup_zstd_compression_level(default: 3) -
zstd_copier_parallel_compression_threads -
RocksDB cache, compaction, and write settings
These should be tuned only if specific performance or memory constraints exist.
CLI Examples
Enable dedupe with ZSTD:
zmprov mcf zimbraBackupDeduplication dedupe zmprov mcf zimbraBackupDedupeCompressionType zstd
Switch back to legacy ZIP behavior:
zmprov mcf zimbraBackupDeduplication nodedupe zmprov mcf zimbraBackupBlobsCompressType zip zmprov mcf zimbraBackupCrossSessionDedupeEnabled FALSE
Validation
Validation can be performed by:
-
Verifying LDAP and localconfig values
-
Inspecting backup directory structure
-
Performing a scoped test restore
Example restore:
zmrestore -a testuser@example.com -ca -pre zstd_ -lb full-YYYYMMDD.HHMMSS.xxx -t /opt/zimbra/backup
For updates to the Admin Console, please refer to the Admin Console section.
Cross-Session Deduplication (CSD)
Overview
Backup Engine v2 extends deduplication beyond a single backup session by introducing Cross-Session Deduplication (CSD). With CSD enabled, data blocks that have already been backed up in previous sessions are detected and reused, instead of being written again in subsequent backups.
As a result, customers experience:
-
Reduced backup data footprint over time
-
Faster backup operations due to fewer write operations
-
Lower storage consumption for long-term retention and compliance scenarios
Cross-session deduplication is particularly beneficial for environments with frequent backups and minimal data changes between sessions, enabling efficient incremental-style backups without compromising data integrity or restore capabilities.
| Cross-session deduplication is supported only for standard backup mothod. CSD is not supported with Autogroup backups. |
How Cross-Session Deduplication Works
Backup Creation Flow
When a full backup request is received with CSD enabled:
-
The request is evaluated by the COMMON or DELTA backup creation logic.
-
Based on this evaluation, either a COMMON backup or a DELTA backup is created.
-
All deduplication checks are performed using a shared RocksDB index associated with the COMMON backup.
Common Backup
The first CSD-enabled full backup creates a COMMON backup directory.
Example:
full-csd-common-20251230.101835.279
The COMMON backup contains:
-
Shared blob storage
-
RocksDB metadata for deduplication
-
Common metadata required for restore operations
The COMMON backup acts as the deduplication baseline for all subsequent DELTA backups.
COMMON Backup Structure
blob-chunks/ rocksdb/ accounts/ ldap/ sys/ session.xml
Conditions That Force Creation of a New COMMON Backup
A new COMMON backup is created when any of the following conditions are met:
-
No existing COMMON backup exists
-
Retention logic requires a new COMMON backup
-
Server attribute
zimbraBackupCSDResetis set toTRUE -
Backup is explicitly forced via CLI:
zmbackup -a all -f --csd
When a new COMMON backup is created, zimbraBackupCSDReset is automatically reset to FALSE.
|
Delta Backup
After a COMMON backup exists, subsequent full backups create DELTA backups.
Example:
full-csd-delta-20251229.102625.190
DELTA backups:
-
Reference the latest valid COMMON backup
-
Store only new or changed metadata
-
Store blob data only if the blob does not already exist in the COMMON backup
DELTA Backup Creation Logic
If:
-
None of the conditions for creating a new COMMON backup are met, and
-
A valid COMMON backup is available
Then the system creates a DELTA backup.
DELTA backups always depend on a specific COMMON backup for blob storage and deduplication checks via RocksDB.
DELTA Backup Structure
DELTA backups do not contain blob-chunks/ or rocksdb/.
They include:
accounts/ ldap/ sys/ session.xml
The session.xml file references the associated COMMON backup.
Delta Blob Deduplication Flow
During a DELTA backup, when a blob needs to be backed up:
-
The system checks the COMMON backup’s RocksDB for the blob hash.
-
If the blob already exists:
-
The blob is not duplicated.
-
The existing blob reference is reused.
-
-
If the blob does not exist:
-
The blob is written to
blob-chunks/in the COMMON backup. -
Metadata is recorded in RocksDB.
-
This ensures:
-
Cross-session deduplication
-
Reduced storage usage
-
Centralized blob management
Retention-Driven COMMON Backup Creation
Retention Policy Source
| Point-in-time restore is supported with session-level, cross-session weekly backups. It is NOT supported for cross-session daily delta backups. |
Retention is derived from the Zimbra backup scheduler using:
zmschedulebackup
Retention rules are defined under the delete (d) schedule, for example:
-
d 7d– retain backups for 7 days -
d 1m– retain backups for 1 month -
d 1y– retain backups for 1 year
Determining When a New COMMON Backup Is Required
From the retention rule, a cutoff date is calculated as:
cutoff = today − retention + 1 day
If the COMMON backup date is less than or equal to the cutoff date, it is considered expired and a new COMMON backup is eligible for creation.
| Even if eligible, a COMMON or DELTA backup is created only when a full backup is triggered. |
Retention Examples
Example 1 – Backup Expired (New COMMON Required)
-
Today: 2025-10-08
-
Retention:
d 8d -
COMMON backup:
20251001
Result: expired → new COMMON backup eligible
Example 2 – Monthly Retention
-
Today: 2025-10-30
-
Retention:
d 1m -
COMMON backup:
20251001
Result: expired → new COMMON backup eligible
Example 3 – Backup Still Valid (DELTA Created)
-
Today: 2025-10-07
-
Retention:
d 7d -
COMMON backup:
20251005
Result: valid → DELTA backup created
COMMON Backup Deletion Restrictions
Deletion Restriction Rule
A COMMON backup cannot be deleted as long as one or more dependent DELTA backups exist.
A COMMON backup becomes eligible for deletion only after all dependent DELTA backups have been deleted.
DELTA and INCREMENTAL backups can be deleted independently.
Deletion Behavior
When a deletion request includes multiple backups:
-
DELTA and INCREMENTAL backups are deleted as requested.
-
COMMON backups are skipped if dependent DELTA backups still exist.
-
If both COMMON and all dependent DELTAs are requested, all are deleted.
No CLI error is displayed when a COMMON backup is skipped.
Logging Behavior
If a COMMON backup deletion is skipped, the following warning is logged:
Backup deletion skipped: CSD common backup <backup_label> is not eligible for deletion, as one or more dependent delta backups are still present.
The CLI command completes successfully.
Compression Handling in CSD
In a CSD backup lineage, the compression type must remain consistent across the COMMON and all DELTA backups.
|
If the compression type changes:
|
This prevents restore failures due to mixed compression formats.
Backup with Autogroup
Cross-Session Deduplication does not support AutoGroup backup method.
Admin UI Behavior
When Autogrouping is enabled:
-
The option to enable CSD is hidden in the Admin UI.
LDAP Override Handling
If CSD is manually enabled via LDAP while Autogrouping is active:
-
CSD is not applied.
-
The system falls back to session-level deduplication.
-
Backup execution continues safely.
Runtime Logging
A warning is logged:
Cross-session deduplication is not supported when the Autogroup feature is enabled.
LDAP Configuration Attributes
zimbraBackupCrossSessionDedupeEnabled
Allowed values:
-
TRUE -
FALSE
zimbraBackupCSDReset
Internal attribute indicating whether a new COMMON backup is required.
Automatically updated when any CSD-related attribute changes.
Enabling Cross-Session Deduplication
Global configuration:
zmprov mcf zimbraBackupCrossSessionDedupeEnabled TRUE
Server-level configuration:
zmprov ms <server_name> zimbraBackupCrossSessionDedupeEnabled TRUE
If zimbraBackupDeduplication is set to nodedupe, enabling CSD automatically switches it to dedupe.
|
CLI Examples
Create a CSD COMMON backup:
zmbackup -a all -f --csd
Override compression:
zmbackup -a all -f --csd --zstd
Disable compression:
zmbackup -a all -f --csd --nocompression
Force creation of a new COMMON backup:
zmbackup -a all -f --csdc
Run a non-CSD backup when CSD is enabled:
zmbackup -a all -f --nocsd
For updates to the Admin Console, please refer to the Admin Console section.
Increasing Parallelism (Advanced)
Localconfig keys controlling parallelism:
-
backup_copy_blob_parallelism_level(default: 5) -
backup_zip_copier_private_blob_zips(default: 4) -
zstd_copier_parallel_compression_threads(default: 8)
Higher values increase throughput at the cost of CPU usage.
For more details on the attributes and recommendation, please refer to Performance Parameter Tuning section
Transitioning Scheduler Configuration for Backup Engine v2
This section describes the steps required to refresh existing backup scheduler configurations when transitioning to Backup Engine v2 (deduplication-enabled backups).
When deduplication is enabled, legacy ZIP-based compression flags (--zip, --zipStore, --noZip) must not be present in the scheduled backup commands. Existing scheduler entries created before the upgrade may still include these flags and must be refreshed.
| Only after the values are refreshed, the new backups will be created using the V2 Backup Engine. |
Purpose of Scheduler Refresh
Refreshing the scheduler configuration ensures that:
-
Backup schedules stored in LDAP are updated to reflect deduplication-enabled behavior.
-
Legacy ZIP-based compression flags are removed from scheduled backup commands.
-
Scheduled backups run using the correct Backup Engine v2 settings.
This step does not change backup timing or retention behavior; it only updates how the scheduler configuration is stored.
Refreshing Scheduler Configuration from CLI
You can reset the scheduler configuration using the CLI. Customize the schedule parameters to match your existing backup configuration.
zmschedulebackup -R \
f '0 1 * * 7' \
i '0 1 * * 1-6' \
d 1m '0 0 * * *'This command forces the scheduler configuration to be rewritten in LDAP without legacy ZIP-based flags when deduplication is enabled.
Refreshing Scheduler Configuration from the Admin Console
You can also refresh the scheduler configuration through the Admin Console.
-
Navigate to:
Configure → Global Settings → Backup/Restore
-
Modify any scheduling parameter (for example, backup hours, days, or retention period).
The scheduler configuration is updated only when a change is made and saved. -
Click Save.
-
Revert the modified parameter back to its original value.
-
Click Save again.
This process forces the scheduler configuration to be re-saved in LDAP using the current backup engine settings.
Cross-Check and Verification
After refreshing the scheduler configuration, verify that the legacy compression flags are no longer present.
Run the following command:
zmschedulebackupConfirm that the scheduled backup expressions do not include:
-
--zip -
--zipStore -
--noZip
when deduplication is enabled.
If these flags are not present, the scheduler is correctly configured to use Backup Engine v2.
When This Step Is Required
Perform this transition step if:
-
You are upgrading from a version that used legacy ZIP-based backups.
-
Deduplication has been enabled after the upgrade and you want to use the new deduplication and compression mechanism.
-
Scheduled backups were configured prior to enabling deduplication.
This step is not required for newly created backup schedules.
Backward Compatibility and Legacy Backup Support
Overview
The enhanced backup system (Backup Engine v2) is fully backward compatible and does not affect existing backups.
All legacy backups created using earlier Zimbra versions remain supported and can be restored seamlessly using the latest system version. No manual migration or conversion of existing backups is required.
The legacy backup mechanism (V1) continues to be available and can be explicitly enabled or disabled using either the Admin Console or CLI.
During restore operations, the system automatically detects the backup version from the backup session directory and invokes the appropriate restore logic for that version.
What Changes for Legacy Backups
The system continues to support the legacy (V1) backups. After upgrading to the latest release:
-
The system automatically switches to Backup Engine v2 for new backups.
-
Deduplication is enabled for both internal and external volumes.
-
Zstandard (ZSTD) compression is applied to deduplicated blobs.
-
All subsequent full backups use the v2 format.
With Backup Engine v2:
-
Only unique blobs across accounts are written during backup.
-
Blob data is compressed using ZSTD.
-
Other backup components (database, LDAP, indexes, metadata) continue to be backed up using existing mechanisms.
Previously created V1 backup data remains unchanged and fully usable.
Restore Compatibility
The restore process is fully backward compatible.
During restore:
-
The system inspects the backup session directory.
-
The backup format/version (V1, V2) is detected automatically.
-
The corresponding restore pipeline is used.
-
No user intervention or special flags are required.
This allows administrators to restore:
-
Legacy ZIP-based backups
-
Session-level deduplicated backups (V2)
-
Cross-session deduplicated backups
All within the same backup repository.
Switching Back to Legacy (V1) Backups
Administrators may choose to continue using legacy V1 backups if required.
Switching via CLI
Backup Engine v2 can be disabled using the following commands.
Global configuration:
su - zimbra
zmprov mcf zimbraBackupDeduplication nodedupeServer-level configuration:
su - zimbra
zmprov ms <server_name> zimbraBackupDeduplication nodedupe-
Restart zmmailbox service on the mailstore nodes:
zmmailboxdctl restart
After applying these settings, subsequent backups will follow legacy (V1) behavior.
Switching via Admin Console
To disable Backup Engine v2 and revert to legacy backups using the Admin Console:
-
Navigate to:
Configure → Global Settings → Backup/Restore
-
Uncheck Enable deduplication
-
Select the desired legacy compression option:
-
zip
-
zipStore
-
noZip
-
-
Click Save
-
Restart zmmailbox service on the mailstore nodes:
su - zimbra zmmailboxdctl restart -
Trigger the backup as usual
After these steps, backups will be created using the legacy V1 format.
Recommended Upgrade Steps
To ensure a smooth transition when upgrading:
-
Allow any in-progress backup jobs to complete before upgrading.
-
After upgrade, run a fresh full backup to take advantage of deduplication and compression.
-
Validate restore operations from:
-
Pre-upgrade (V1) backups
-
Post-upgrade (V2) backups
-
-
Review and update storage planning to reflect reduced backup sizes.
Administrative Considerations
Administrators should be aware of the following:
-
Monitoring metrics may differ due to reduced backup size and deduplication.
-
Storage calculations should be revisited to account for improved efficiency.
-
Backup and restore workflows remain unchanged.
-
Existing automation and operational procedures continue to function as before.
Backup Engine v2 modernizes storage efficiency while preserving operational stability and backward compatibility.
Backing Up the Mailbox Server
Zimbra Collaboration includes a configurable backup manager that resides
on every Zimbra Collaboration server and performs both backup and
restore functions. You do not have to stop the Zimbra Collaboration
server in order to run the backup process. The backup manager can be
used to restore a single user, rather than having to restore the entire
system in the event that one user’s mailbox becomes corrupted. Full and
incremental backups are saved in /opt/zimbra/backup.
Redo Log
Each Zimbra mailbox server generates redo logs that contain current and archived transactions processed by the message store server since the last incremental backup.
When the server is restored, after the backed up files are fully restored, any redo logs in the archive and the current redo log in use are replayed to bring the system to the point before the failure.
When the current redo log file size reaches 100MB, the current redo log rolls over to an archive directory. At that point, the server starts a new redo log. All uncommitted transactions from the previous redo log are preserved. In the case of a crash, when the server restarts, the current redo logs are read to re-apply any uncommitted transactions.
When an incremental backup is run, the redo logs are moved from the archive to the backup directory.
Backup Methods
Two backup methods are available:
-
The standard backup method is the default method and appropriate for customers who want to backup all accounts on the same day
-
The auto-grouped backup method is the method which will backup a subset of accounts each day.
Backup Method Overview
Auto-Grouped and Standard Backup will perform a full backup process backing up all the information needed to restore mailboxes, including the LDAP directory server, database, index directory, and message directory for each mailbox.
The LDAP directory is backed up as part of either the full or incremental backup process. All accounts, domains, servers, COS, and other data are backed up.
Each mailbox server generates redo logs that contain every transaction processed by that server. If an unexpected shutdown occurs to the server, the redo logs are used for the following:
-
To ensure that no uncommitted transactions remain, the server reads the current redo log upon startup and re-executes and completes any uncommitted transactions.
-
To recover data written since the last full backup in the event of a server failure.
When the server is restored, after the backed up files are fully restored, any redo logs in the archive and the current redo log in use are replayed to bring the system to the point before the failure.
When backing up shared messages, if a file representing a message already exists in the daily backup, it flags this object as such and does not copy its content again.
If the Auto-Grouped or incremental backup process finds no previous full backup for a mailbox, a full backup is performed on that mailbox.
Auto-grouped backups combine full and incremental backup functions, there is no need for incremental backups.
Auto-grouped and incremental backups move the redo logs to the backup directory. The redo logs are a journal of every activity that has taken place. They contain a full copy of all messages delivered, as well as metadata such as tags, contacts, and conversations.
These backup files can be used to restore the complete mailbox server or individual mailboxes so that account and message data is completely restored.
The Zimbra MTA is not backed up, as the data is only on the server for a very short time.
Custom configurations — such as mailboxd’s `jetty/etc/*.xml — are not backed up.
Auto-Grouped Backup Method
Auto-grouped backup method runs a full backup for a different group of mailboxes then gathers the redo logs for the remaining accounts on each mailbox server. It is not recommended to run auto-grouped backups manually since they are scheduled from the CLI and run automatically at the scheduled time.
Standard Backup
Standard backup method runs a weekly full backup for each mailbox server, then an incremental backup will occur the remaining days defined within the scheduler.
Starting with Zimbra Collaboration Daffodil version 10.1.16 onwards, bydefault, the Standard backup method will use the enhanced Deduplication and Compression mechanism.
A new mechanism Cross-Session Deduplication can also be enabled. Please refer to Cross-Session Deduplication section for more details.
Backup Notification
A backup report is sent to the admin mailbox when full and incremental backups are performed. This report shows the success or failure of the backup and includes information about when the backup started and ended, the number of accounts backed up and redo log sequence range.
If the backup failed, additional error information is included.
To execute the full backup of the failed account, execute the command as a zimbra user:
zmbackup -f -a user1@domain.com -s server1
Directory Structure for Backup Files
The backup destination is known as a backup target. To the backup
system, it is a path in the file system of the mail server. The Zimbra
default backup directory is /opt/zimbra/backup.
The backup directory structure created by the standard backup process is shown in Standard Backup directory structure. You can run regularly scheduled backups to the same target area without overwriting previous backup sessions.
The accounts.xml file lists all accounts that are in all the backups combined. For each account, this file shows the account ID, the email address, and the label of the latest full backup for that account. If you save your backup sessions to another location, you must also save the latest accounts.xml file to that location. The accounts.xml file is used to look up the latest full Backup for an account during restore. If the accounts.xml file is missing you must specify the backup label to restore from.
The redo log directory is located at /opt/zimbra/redolog/redo.log. When
the current redo log file size reaches 100MB, the current redo log rolls
over to an archive directory, /opt/zimbra/redolog/archive. At this
point the server starts a new redo log. All uncommitted transactions
from the previous redo log are preserved. In the case of a crash, when
the server restarts, the current redo logs are read to re-apply any
uncommitted transactions.
Redo operations are time critical, therefore a directory move is
performed instead of a copy-then-delete function. This directory move
can only be performed if the source and destination paths are on the
same file system volume. In other words, the redo log and redo-archive
log must be on the same file system volume because the archive files are
a subdirectory of the redo log file system.
All incremental and auto-grouped backup sessions must be saved to the same directory as all the redo logs must be found in the same backup target. Standard full backup sessions can use a different target directory.
| Main Directory | Sub-Directory / File | Description |
|---|---|---|
|
— |
Default root directory for all Backup & Restore data |
|
|
Active account mapping file. Maintains email address to Zimbra ID mappings and records the most recent full backup label for each account. Used during restore operations. |
|
|
Previous version of the accounts mapping file retained for reference. |
|
|
Temporary working directory used during backup and restore execution. |
|
|
Root directory containing all backup session data. |
|
Standard full backup session directory. |
|
|
Common backup directory created when cross-session deduplication is enabled. |
|
|
Delta backup directory storing changes since the common backup. |
|
|
Incremental backup directory containing changes since the previous backup. |
|
|
|
Stores deduplicated blob data created during this backup session (session-level deduplication). |
|
Stores system-level backup metadata required for restore processing. |
|
|
Contains per-account backup data directories for all accounts included in this session. |
|
|
Stores LDAP data captured as part of the backup session. |
|
|
Backup session descriptor containing session metadata. |
|
|
|
Stores system-level metadata for the common backup. |
|
Stores account-level metadata required for restore operations. |
|
|
Stores deduplicated and compressed chunk data shared across multiple backup sessions. |
|
|
Stores LDAP data captured for the common backup. |
|
|
RocksDB database used to track chunk references and deduplication metadata. |
|
|
Metadata file describing the common backup session. |
|
|
|
Stores system-level metadata for the delta backup. |
|
Stores account-level metadata for changes since the common backup. |
|
|
Stores LDAP changes captured in this delta backup. |
|
|
Metadata file describing the delta backup session. |
|
|
|
Stores system-level metadata for the incremental backup. |
|
Stores per-account changes since the previous backup. |
|
|
Stores redo logs used to capture incremental mailbox changes. |
|
|
Stores LDAP changes captured during the incremental backup. |
|
|
Metadata file describing the incremental backup session. |
| The full-csd-common-<timestamp> and full-csd-delta-<timestamp> directories are generated only after enabling the Cross-session deduplication feature. |
| For auto-grouped backups, the directory structure saves the redo log files to the full backup session. There are no incremental backup sessions. |
Admin Console – Backup & Restore Configuration
Many backup and restore tasks can be performed directly from the Administration Console. Backup configuration can be applied at the global or server level. Server-level configuration overrides global settings.
The Backup & Restore administration sections are located at:
Global Backup Configuration
Configure → Global Settings → Backup/Restore
Server Backup Configuration
Configure → Server → (Server) → Backup/Restore
Backup Management and Restore
Tools and Migration → Backups → (Server)
Configure Backup/Restore from the Admin Console
Backups can be configured globally or per server. Global settings apply to all servers by default until explicitly overridden at the server level.
Backup/Restore (General Settings)
-
Enable Backups When set to TRUE, enables backup globally and initializes current global and server configurations to create and manage backups.
-
LDAP attribute:
zimbraGlobalBackupEnabled -
Default value:
TRUE
-
-
Type of Backup Select the backup mode:
-
Auto-grouped
-
Standard
-
LDAP attribute:
zimbraBackupMode -
Default value:
Auto-Grouped
-
-
Days to Retain Full Backup Specifies how long full backups are retained. Backups older than this value are deleted by the scheduler.
-
LDAP attribute:
zimbraBackupRetentionDays -
Default value:
8
-
-
Throttling Automatic Backups Auto-grouped backups may throttle the number of mailboxes backed up per run. This is useful after migrations or upgrades to ensure backups complete during off hours. Enable throttling using:
zmprov mcf zimbraBackupAutoGroupedThrottled TRUE
-
Scheduling Hours Defines the daily backup start time.
-
LDAP attribute:
zimbraBackupStartTime -
Default value:
01:00
-
-
Default Backup Target Specifies the path where backups are stored.
-
LDAP attribute:
zimbraBackupTarget -
Default value:
/opt/zimbra/backup
-
-
Prefix for Notification Email Subject Subject prefix used for backup notification emails.
-
LDAP attribute:
zimbraBackupReportEmailSubjectPrefix
-
-
Backup Minimum Free Space Prevents backup from starting if insufficient free space exists on the backup target. Supports percentage or absolute values (e.g.
25%,50GB).-
LDAP attribute:
zimbraBackupMinFreeSpace -
Default value:
0(disabled)
-
Notifications
Configure email notifications for backup results.
-
LDAP attributes:
-
zimbraMailReportEnabled -
zimbraBackupReportEmailSender -
zimbraBackupReportEmailRecipients
-
Backup Options
These options control what data is included in backups.
-
Exclude Blobs Skips all blobs during backup.
-
LDAP attribute:
zimbraBackupSkipBlobs -
Default value:
FALSE
-
-
Exclude Blobs on SM Volumes Skips blobs only on secondary (HSM) volumes.
-
LDAP attribute:
zimbraBackupSkipHsmBlobs -
Default value:
FALSE
-
-
Exclude Search Index Excludes search indexes from backup. Indexes must be rebuilt after restore.
-
LDAP attribute:
zimbraBackupSkipSearchIndex -
Default value:
FALSE
-
Backup Engine v2 – Deduplication, Compression, and CSD
Backup Engine v2 introduces new storage and efficiency controls that apply to new backup sessions only. Existing backups remain unchanged and fully restorable.
These settings are available under:
-
Configure → Global Settings → Backup/Restore
-
Configure → Server → (Server) → Backup/Restore
Deduplication Configuration
-
Enable Deduplication Controls whether deduplication is applied.
-
LDAP attribute:
zimbraBackupDeduplication -
Values:
-
dedupe– Enabled (default) -
nodedupe– Disabled (legacy behavior)
-
-
When enabled:
-
Backup Engine v2 is active
-
Compression type in dedupe backup option is enabled
-
Deduplication applies to both internal and external storage
-
Compression and CSD options become available
When disabled:
-
Backup Engine fallback to legacy (v1) system.
-
Compress blobs in zip format is enabled and has following options in the dropdown:
-
zip
-
zipStore
-
nozip
-
-
Deduplication applies to only internal storage
-
Compression and CSD options become unavailable
Compression for Deduplicated Backups
-
Compression Type in Dedupe Backup Visible only when deduplication is enabled.
-
LDAP attribute:
zimbraBackupDedupeCompressionType -
Values:
-
zstd– Zstandard compression (default, recommended) -
nocompression– No compression
-
-
Behavior:
-
Applies only to deduplicated backups (V2)
-
Compression is uniform across internal and external volumes
-
ZIP-based compression is not used when deduplication is enabled
Cross-Session Deduplication (CSD)
-
Enable Cross Session Deduplication Allows reuse of blobs across multiple backup sessions.
-
LDAP attribute:
zimbraBackupCrossSessionDedupeEnabled -
Values:
-
TRUE– Enabled -
FALSE– Disabled (default)
-
-
Behavior:
-
When enabled:
-
Full backups create a COMMON baseline
-
Subsequent backups create DELTA backups
-
-
When disabled:
-
Each full backup is self-contained (session-level dedupe)
-
Interaction with Autogroup Backups
Cross-Session Deduplication is not supported with Autogroup backups.
Admin Console behavior:
-
The CSD option is hidden when Auto-Grouped method is selected.
Runtime behavior:
-
If CSD is enabled via LDAP while Autogrouping is active:
-
The system falls back to session-level deduplication
-
Backup continues safely
-
Warning logged:
-
Cross-session deduplication is not supported when the Autogroup feature is enabled.
Configuration Safeguards
The internal attribute zimbraBackupCSDReset is automatically managed and not exposed in the UI.
It is set to TRUE whenever any of the following change:
-
Deduplication state
-
Compression type
-
CSD enablement
This ensures restore safety by forcing a new COMMON backup when required.
Selecting Users for Backup
Admins can select users, COS, or domains for backup.
Key points:
-
Configuration applies to all mailstores unless overridden via CLI.
-
An account selected multiple ways is backed up only once.
-
Selecting Domain/COS sets
zimbraBackupObjectLevelEnabled=TRUE. -
Selecting All Users sets
zimbraBackupObjectLevelEnabled=FALSE. -
Zimbra inheritance rules apply.
Recommendations for Working with Storage Volumes
-
Internal storage: with-blob backup/restore recommended
-
External storage (S3): blob-less backup/restore recommended
-
Mixed internal primary + external secondary:
-
With-blob for primary
-
Blob-less for secondary
-
-
Same blob-skip settings must be used for restore
-
Primary external + secondary internal storage is not supported
Message Recovery Settings
Message recovery is implemented using the Dumpster feature and is part of Backup & Restore configuration.
Key notes:
-
Message Recovery and Dumpster share configuration
-
Recommended method for restoring deleted items
-
Can be enabled globally or per COS/Domain
-
Uses standard Zimbra inheritance
Related LDAP attributes:
-
zimbraMailDumpsterLifetimeType– Retention period (default:30d) -
zimbraDumpsterUserVisibleAge– End-user visibility window (default:30d) -
zimbraDumpsterPurgeEnabled– Purge control (default:FALSE)
Backup and Restore Using the Command Line Interface
The Zimbra backup and restore procedures can be run as CLI commands.
The following utilities are provided to create backup schedules, perform full and incremental backups, restore the mail server, or restore the LDAP server.
-
zmschedulebackup— This command is used to schedule full backups, incremental backups, and deletion of old backups. -
zmbackup— This command executes full or incremental backup of the Zimbra Collaboration mailbox server. This is run on a live server, while themailboxdprocess and the mailbox server are running. This command also has an option to manually delete old backups when they are no longer needed. -
zmbackupabort— This command stops a full backup that is in process. -
zmbackupabort -r— This command stops an ongoing restore. -
zmbackupquery— This command lists the information about ongoing and completed backups, including labels and dates. -
zmrestore— This command restores a backup to a running Zimbra Collaboration mailbox server. -
zmrestoreoffline— This command restores the Zimbra Collaboration mail server when themailboxdprocess is stopped. -
zmrestoreldap— This command restores the complete LDAP directory server, including accounts, domains, servers, COS and other data.
Refer to Appendix A: Command Line Utilities for usage and definitions for each of these commands.
Backing up using the Standard Method
When you initiate a backup, you can issue the command from the same server being backed up, run the command remotely and specify the target server on the command line, or use the Administration Console to start a backup session.
Scheduling a Standard Backup
When configuring Standard Backup as your backup method, a full and incremental backup entry will be added to the crontab. Under the default schedule, the full backup is scheduled for 1:00 a.m., every Saturday. The incremental backups are scheduled for 1:00 a.m., Sunday through Friday.
By default, backups older than a month are deleted every night at 12 a.m.
You can change the backup schedule using the zmschedulebackup command or from the Admin UI.
Specify the fields as follows, separate each field with a blank space:
-
minute — 0 through 59
-
hour — 0 through 23
-
day of the month — 1 through 31
-
month — 1 through 12
-
day of the week — 0 through 7 (0 or 7 is Sunday, or use names)
Type an asterisk (*) in the fields you are not using.
zmschedulebackup options-
Replace the existing full backup, incremental backup and delete backup schedule. When you use
-R, the complete backup schedule is replaced. If you use this command, remember to set the deletion schedule, if you want backup sessions to be scheduled for automatic deletion. This example replaces the existing schedule to have full backups run on Sunday at 1 a.m., incremental backups to run Monday through Saturday at 1 a.m., and old backups deleted at 12:00 a.m. every day.zmschedulebackup -R f "0 1 * * 7" i "0 1 * * 1-6" d 1m "0 0 * * *" -
Add an additional full backup time to your current schedule. This example adds a full backup on Thursday at 1 a.m.
zmschedulebackup -A f "0 1 * * 4" -
Review your backup schedule. The schedule is displayed.
zmschedulebackup -q -
Save the schedule command to a text file. This would allow you to easily recreate the same schedule after a reinstall or upgrade
zmschedulebackup -s
To return backups to the default schedule use the command zmschedulebackup -D.
|
Default Standard Backup Schedule
The default backup schedule is displayed similarly to the following example:
0 1 * * 6 /opt/zimbra/bin/zmbackup -f - all
0 1* * 0-5 /opt/zimbra/bin/zmbackup -i
0 0 * * * /opt/zimbra/bin/zmbackup -del 1mRead as follows:
0 1 * * * 6 /opt/zimbra/bin/zmbackup -f - all0 1* * 0-5 /opt/zimbra/bin/zmbackup -i0 0 * * * /opt/zimbra/bin/zmbackup -del 1m- Admin Console:
-
Home → Configure → Global Settings → Backup/Restore
You can add additional recipient addresses or change the notification email address in the Administration Console.
Full Backup Process
The full backup process goes through the following steps to back up the mailbox, the database, the indexes, and the LDAP directory:
-
Backs up the global system data including system tables and
localconfig.xml. -
Iterates through each account to be backed up and backs up the LDAP entries for those accounts.
-
Places the account’s mailbox in maintenance mode to temporarily block mail delivery and user access to that mailbox.
-
Backs up the mailbox.
-
Creates MariaDB dump for all data related to that mailbox.
-
Backs up the message directory for that mailbox.
-
Creates a backup of the index directory for that mailbox.
-
-
Returns that account’s mailbox to active mode and moves on to the next one.
-
Backs up the LDAP directory.
A full backup is usually run asynchronously. When you begin the full
backup, the label of the ongoing backup process is immediately
displayed. The backup continues in the background. You can use the
zmbackupquery command to check the status of the running backup at any
time.
Backup files are saved as zip files without compression. To change the
default zip option, see Appendix A: Command Line Utilities,
zmbackup section.
Incremental Backup Process
Incremental backups are run using the CLI command, zmbackup. The process for incremental backup is as follows:
-
Backs up the global system data including system tables and
localconfig.xml. -
Iterates through each account to be backed up and backs up the LDAP entries for those accounts.
-
Moves the archive redo logs, created since the last backup, to the
<backup_target>/redologsfolder.Archived logs that are less than an hour old at the time of incremental backup are copied to the backup and are not deleted. These redologs are deleted one hour after the backup. The interval is set by the
localconfigkeybackup_archived_redolog_keep_time. The default is 3600 seconds.If no full backup for this account is found, the backup process performs a full backup on this account, even if only an incremental backup was specified.
-
Backs up the LDAP directory.
Performing Manual Backups
Use the zmbackup command to perform the following backup operations:
-
Perform a manual backup of all mailboxes on server<1>:
zmbackup -f -s server1.domain.com -a all
-
Perform a manual, incremental backup of all mailboxes on server1 since last full backup
zmbackup -i -s server1.domain.com -a all
-
Perform a manual, full backup of only user1’s mailbox on server1
zmbackup -f -s server1.domain.com -a user1@domain.com
Deleting Backup Sessions
You can delete backup sessions either by label or by date.
-
Deleting by label deletes that session and all backup sessions before that session.
-
Deleting by date deletes all backup session prior to the specified date.
For example, zmbackup -del 7d deletes backups older than 7 days
from now. You can specify day (d), month (m), or year (y).
Finding a Specific Backups
Each full or incremental backup is a backup session.
Each backup session is labeled with date and time. For example, the
label full-20210712.155951.123 says this is a backup from July 12,
2021 at 3:59:51.123.
| The times set in the session label are GMT, not the local time. GMT is used rather than local time to preserve visual ordering across daylight savings transitions. |
Use the zmbackupquery command to find full backup sessions.
-
To find a specific full backup session:
zmbackupquery -lb full-20210712.155951.123
-
To find a full backup sessions since a specific date:
zmbackupquery --type full --from "2021/01/01 12:45:45"
-
To find all full backup sessions in the backup directory:
zmbackupquery --type full
-
To find the best point in time to restore for an account specify a time window
zmbackupquery -a user1@example.com --type full --from "2021/07/05 12:01:15" --to "2021/07/12 17:01:45"
If a backup session is interrupted because the server crashes during backup
(not aborted), the interrupted backup session is saved as a temporary
session. The temporary backup session is put in
<backup_target>/sessions_tmp folder. You can use the rm command to delete the
directory.
|
Aborting a Full Backup in Progress
-
Before you can abort a backup, you must know the backup session label. This label is displayed when
zmbackupfirst starts. If you do not know the full backup label, usezmbackupqueryto find the label. -
Use the
zmbackupabortcommand to stop a backup that is in progress. The backup is immediately stopped and becomes a partially successful backup.-
Stop the backup, if you know the label name
-
zmbackupabort -lb full-20210712.155951.123 -s server1
-
Stop the backup, if you do not know the label
zmbackupquery zmbackupabort -s server1 -lb full-20210712.155951.123
Backup using the Auto-Grouped Method
The auto-grouped backup method is configured either from the Administration Console or from the CLI.
- Admin Console:
-
Home → Configure → Global Settings → Backup/Restore
Home → Configure → Servers → server → Backup/Restore
Configuring Auto-Grouped Backup from the CLI
Set the backup method in the global configuration, and you can override the configuration on a per server basis if you do not want a particular server to use the auto-grouped backup method.
To set up auto-grouped backup, you modify LDAP attributes with the zmprov command:
zmprov mcf {ldap_attribute} {arg}You can also set the attributes at the server level using zmprov ms {server_name} {attribute}.
The following LDAP attributes are modified:
-
zimbraBackupMode— Set to Auto-Grouped. The default is Auto-Grouped. -
zimbraBackupAutoGroupedInterval— Set this to the interval in either days or weeks that backup sessions should run for a group. The default is8d. Backup intervals can be 1 or more days, entered asxd(e.g.1d); or 1 or more weeks, entered asxw(e.g.1w). -
zimbraBackupAutoGroupedNumGroups— This is the number of groups to spread mailboxes over. The default is 7 groups.
Schedule Auto-Group Backups
The auto-group backup schedule is set as the default mode and can be configured within the admin UI or command line.
Run zmschedulebackup -D to set the default schedule for
auto-grouped backups based on your zimbraBackupAutoGroupedInterval
setting.
One group is backed up each interval. The auto-grouped backup automatically adjusts for changes in the number of mailboxes on the server. Each backup session backs up the following:
-
All mailboxes that have never been backed up before. These are newly provisioned mailboxes.
-
All mailboxes that have not been backed within the number of scheduled backup days. For example, if backups are scheduled to run over six days, mailboxes that have not been backed up in the past 5 days are backed up.
-
More mailboxes, the oldest backup first. This is done so that the daily auto-grouped backup load is balanced.
For example, if you configured the auto-grouped backup interval to be daily (1d) and the number of groups to be 7, the first time auto-grouped backup runs, all accounts are backed up. After the initial backup, auto-grouped backup runs again the next day. This time accounts that have been newly provisioned and a percentage of accounts close to one-seventh of the total are backed up again. Accounts with the oldest backup date are backed up first. The backup continues with newly provisioned accounts and approximately one-seventh of accounts being backed up daily over seven days.
When backing up shared messages, if a file representing a message already exists in the backup, it flags this object as such and does not copy its content again.
Backup files are saved as zip files without compression. To change the
default zip option, see Appendix A: Command Line Utilities,
zmbackup section.
These backup files can be used to restore the complete Zimbra Collaboration system or individual mailboxes so that account and message data is completely restored. Archived redo logs are moved to the backup session as part of the full backup. When the server is restored from an auto-grouped backup, redo logs are replayed to bring the system to the point before the failure.
Backup Options
The backup process can be configured to selectively backup content.
Backup Up content Options
You can configure these backup options so that search indexes, blobs, and SM blobs are not backed up during a full backup session.
-
zimbraBackupSkipSearchIndex— Default is FALSE. If set to TRUE, the search index is not backed up. The mailbox will have to be reindexed after restoring from a backup without the search index. -
zimbraBackupSkipBlobs— Default is FALSE. If this is set to TRUE, blobs are not backed up. This might be useful for getting a quicker backup of just database data when the blobs reside on fault-tolerant storage. This configuration applies to all blobs, those on the primary volumes as well as secondary (SM) volumes. -
zimbraBackupSkipHsmBlobs— Default is FALSE. If this is set to TRUE, blobs on SM volumes are not backed up. Set this ifzimbraBackupSkipBlobsis FALSE but you want to skip blobs on SM volumes.
Managing Disk Space for Backups
Backup sessions fail if the target disk does not have enough space. All data backed up in the backup session is discarded and deleted.
You can choose to receive notification when your disk might not have enough space to complete the backup
Configuring the zimbraBackupMinFreeSpace attribute helps you
manage running backup session by notifying you.
Set the value for attribute zimbraBackupMinFreeSpace to the amount of
free space required on the backup target disk before a backup session is
run. If the disk has less space than the value set in the attribute, the
back up session will not run and an email notification is sent to the
administrator.
If you are also backing up the MariaDB database, make sure you set the value
large enough to include the myslqdump file size.
|
The value for this attribute can be specified as a percentage of the
total disk space, for example 25%, or as a number of bytes, for example
300MB, 50GB, etc. The default value is 0, meaning the check is disabled
and backup is always allowed to start.
The attribute can be set globally or by server.
-
As global:
zmprov mcf zimbraBackupMinFreeSpace <value>
-
By server:
zmprov ms <zmhostname> zimbraBackupMinFreeSpace <value>
Backup sessions run if the free disk space is at least the value you set. If your backup file is larger than the value, the backup session fails. You should monitor the size of the backup files and adjust the attribute value if the backup requires more space than the configured value.
Restoring Data
Three types of restore procedures can be run:
-
The
zmrestorecommand is used to restore the mailboxes while the Zimbra Collaboration mailbox server is running. -
The
zmrestoreofflinecommand is used to restore the mailbox server when just themailboxdprocess been stopped. This command is run for disaster recovery. -
The
zmrestoreldapcommand is used to restore the content of the LDAP directory server.
The restore process allows all accounts or individual accounts to be specified.
| Point-in-time restore is supported only with session-level, cross-session weekly backups. It is NOT supported for cross-session daily delta backups. |
Restore Process
The zmrestore process goes through the following steps to restore the mailbox, the database, the indexes, and the LDAP directory.
-
Retrieves specified accounts to be restored, or specify all for all accounts that have been backed up.
-
Iterates through each mailbox:
-
Deletes the mailbox on the server to clear any existing data
-
Restores the last full backup of the MariaDB data, the index directory, and the message directory for that mailbox
-
Replays redo logs in all incremental backups since last full backup
-
Replays all archived redo logs for that mailbox, from the redo log archive area on the mailbox server
-
Replays the current redo log
-
| Accounts are restored, even if the account exceeds its quota. The next time the user performs an action that affects quota, they receive a warning that they have exceeded their quota. |
| Users using the Zimbra Connector for Microsoft Outlook must perform an initial sync on the Outlook client when they log on after the Zimbra server is restored. |
Examples
Including last full backup and any incremental backups since last full backup
zmrestore -a allzmrestore -a account@company.comThe following restore options affect redo log replay. If you do not specify one of these options, all redo logs since the full backup you’re restoring from are replayed
| After you perform any of the following point-in-time restores, you should immediately run a complete backup for those accounts to avoid future restore problems with those accounts. |
A restore that is run using any of the following options is a point-in-time restore:
-
-restoreToTime<arg> - Replay the redo logs until the time specified. -
-restoreToIncrLabel<arg> - Replay redo logs up to and including this incremental backup. -
-restoreToRedoSeq<arg> - Replay up to and including this redo log sequence. -
-br- Replays the redo logs in backup only, therefore excluding archived and current redo logs of the system. -
-rf- Restores to the full backup only. This does not include any incremental backups at all.
Restore stops at the earliest possible point in time if more than one point in time restore options are specified.
zmrestore -a account@company.com-restoreToTime <arg>Two common ways to write the <timearg> are
-
"YYYY/MM/DD hh:mm:ss" -
YYYYMMDD.hhmmss
zmrestore -rf --a allzmrestore -ra -a account@company.com
When using S3 as the primary message volume, restoring an account with the -pre_restored_ option (e.g., zmrestore -a user@domain.com -restoreToTime <timeArgument> -lb full-xxxxxx -ca -pre restored_) creates a new account such as restored_user@domain.com.
Deleting any data (emails, calendar events, contacts, briefcase documents, etc.) from this restored account can result in data loss from the original account (user@domain.com) as well. Deleting emails may result in "blob not found" errors.
We recommend not deleting the -pre_restored_ account or any data from it if the original account is still in use. This will help prevent accidental data loss.
|
A prefix is prepended to the original account names
zmrestore -ca -a account@company.com -pre restoreThe result from the above example would be an account called restoreaccount@company.com.
localconfig.xmlzmrestore -sys--contineOnError (-c) to the command so that the restore process continues if an error is encountered.zmrestore -a all -cWhen -c is designated, accounts that could not be restored are displayed
when the restore process is complete.
Can also be used to restore deleted accounts
zmrestore -a account@company.comzmrestore -a account@company.com -skipDeletedAccountsWhen the mailbox is restored it will contain messages that were deleted. This is useful if users use POP and remove messages from the server
zmrestore -a account@company.com --skipDeletes
When the latest point in time is requested, do not add a backup label
(-lb). Without specifying the label, the most recent full backup before the
requested point is automatically used as the starting point.
|
Stop a Restore Process
The zmbackupabort -r command interrupts a restore that is in process.
The restore process stops after the current account finishes being
restored. The command displays a message showing which accounts were not
restored.
To stop the restore type:
zmbackupabort -rRestore Mailboxes When Mail Server Is Down
The offline restore process can only be run when the$1`mailboxd` server is not running. In general, offline restore is run under the following circumstances:
-
Certain components of the Zimbra server are corrupted, and the server cannot be started. For example, the data in LDAP or the database are corrupted.
-
A disaster requires the Zimbra software to be reinstalled on the server.
The offline restore must be run before the Zimbra Collaboration mailbox store server is started to keep the redo logs in sequence.
In a disaster recovery when the Zimbra software is reinstalled, if mailboxd
is started before the backup files are restored, the mail server would
begin to accept email messages and perform other activities, producing redo
logs in the process. Since the pre-disaster data have not been restored to
the server, the redo logs would be out of sequence. Once mailboxd is
running, it would be too late to restore the pre-disaster data.
The offline restore process goes through the following steps.
-
Specified accounts to be restored are retrieved. If the command-line does not specify any mailbox address, the list of all mailboxes on the specified mail host is retrieved from Zimbra LDAP directory server.
-
Iterates through each mailbox:
-
Deletes the mailbox on the server to clear any existing data
-
Restores the last full backup of the MariaDB data, the index directory, and the message directory for that mailbox
-
Replays redo logs in all incremental backups since last full backup
-
Replays all archived redo logs for that mailbox, from the redo log archive area on the mailbox server
-
Replays the current redo log
-
Restore All Accounts
-
Restore all accounts on server1 when
mailboxdis stoppedzmrestoreoffline -a all -
Start
mailboxdafter the offline restore is completezmcontrol startup
Restore Individual Accounts on a Live System
Use the zmrestore command to restore one or more selected accounts. In the event that a user’s mailbox has become corrupted, you might want to restore that user from the last full and incremental backup sets.
-
For each account to be restored, put the account into maintenance mode
zmprov ma <account> zimbraAccountStatus maintenanceMaintenance mode prevents the delivery of new emails during the restore. Otherwise, the emails would be overwritten during the restore process.
-
Run the
zmrestorecommand to restore the accountszmrestore -a account@abc.com -
For each account that was restored, put the account back into active mode
zmprov ma <account> zimbraAccountStatus active
| If a user account is restored and the COS that the account was assigned no longer exists, the default COS is assigned to the account. |
Exclude Items from a Restore
When you restore from a full backup, you can exclude the search index and blobs.
-
Search index — If you do not restore the search index data, the mailbox will have to be reindexed after the restore.
zmrestore -a <all|account> --exclude-search-index -
Blobs — This is a useful option when all blobs for the mailbox being restored already exist.
zmrestore <all or account>|--exclude-blobs -
HSM-blobs — This is useful when all SM blobs for the mailbox being restored already exist.
zmrestore <all or account> --exclude-hsm-blobs
Restore the LDAP Server
In a disaster recovery where you need to restore the entire system, restore the LDAP directory server first.
The zmrestoreldap command restores the global LDAP data including COS,
distribution lists, etc. You can restore the complete LDAP server, which
recreates the entire schema or you can restore specific accounts. You
specify the session to restore. The restore command has to be run on the
LDAP server being restored.
Examples
zmrestoreldap -lbszmrestoreldap -lb full20211130135236zmrestoreldap -lb full20211130135236 -a tac@abc.com jane@abc.comGeneral Steps for Disaster Recovery
Use the following steps to restore a mailbox store server in a general disaster scenario involving multiple machines.
Preparation
-
Restore the LDAP directory server to a known good state before doing anything with the mailbox store server.
-
Put all mailboxes into maintenance mode to prevent mail delivery and user login while restoring the mailboxes.
-
Stop the mailbox store server if it is running.
Recovery
-
Reinstall the Zimbra Collaboration software on the mailbox server, if necessary.
-
Restore mailboxes.
-
Start the Zimbra Collaboration server.
-
Put all Zimbra Collaboration mailboxes back in active mode.
-
Run a full backup of the server.
Crash Recovery Server Startup
When your system unexpectedly stops and then restarts on startup, the server searches the redo log for uncommitted transactions and replays any that it finds. Replaying the redo logs brings the system to a consistent state.
Restore Zimbra Collaboration
If a complete machine failure occurs, use the following steps to restore to a new server.
| The Zimbra Collaboration version you install on the new server must be the same version as installed on the old server. The server can have a different operating system. |
The new server hardware must meet the requirements described in the Installation Prerequisites section of the Zimbra Collaboration Single Server Installation guide. Install the new operating system, making any necessary OS configuration modifications as described in the installation guide.
You do the following to restore to a new server:
-
Prepare the new server.
-
Block client access to the old server’s IP address with firewall rules.
-
Mount any volumes that were in use on the older server.
-
Delete the MariaDB data that is set up in the initial installation of Zimbra Collaboration.
-
Copy the backup files to the new server.
-
Run
zmrestoreldapto restore the global LDAP data. -
Run
zmrestoreofflineto restore account data from the backup sessions. -
Prepare and run a new backup.
Old Server Status
Two scenarios for disaster recovery are the server has died and the Zimbra Collaboration files cannot be accessed, or Zimbra Collaboration is still running, but the server hardware needs to be replaced.
If the server is not running:
-
Block client access to the server IP address with firewall rules.
-
Find the latest full Zimbra Collaboration backup session to use.
If the server is still running, to prepare the move to the new server:
-
Block client access to the server’s IP address with firewall rules.
-
Run a full backup of the old service, or if the backup is recent, run an incremental backup to get the most current incremental backup session.
-
Run
zmcontrol stop, to stop Zimbra Collaboration. In order to restore to the most current state, no new mail should be received after the last incremental backup has run. -
Change the hostname and IP address on the old server to something else. Do not turn off the server.
Install Zimbra on a New Server
Before you begin, make sure that the new server is correctly configured with the IP address and hostname and that Zimbra Collaboration is installed and configured with the same domain, hostname, passwords, etc. as the previous server. See the Zimbra Collaboration installation guide for more information about preparing the server. Before you begin to install Zimbra Collaboration, note the information you need from the old server including admin account name and password, LDAP, Amavis, and Postfix passwords, spam training, and non-spam training user account names, exact domain name, and the global document account name.
| Make sure the computer time is set to the same time as the old server. Verify that the old hostname and MX DNS records resolve to the new server. |
-
Copy the Zimbra Collaboration License.xml file to a directory on the new server. You cannot complete the Zimbra Collaboration installation if the license is not on the new server.
-
Run
./install.shand follow the directions in the installation guide to install Zimbra Collaboration. Make sure that you configure the same domain, hostname, passwords as on the old server. During Zimbra Collaboration install, the following settings must be changed to match the original server settings:-
Zimbra LDAP Server — For Domain to create, identify the same default domain as on the old server.
-
Zimbra Mailbox Server — An administrator’s account is automatically created.
-
Make sure that the account name for Admin user to create is the same name as on the original server.
-
Set the admin password to be the same as on the old server.
-
Set the LDAP password to be the same as on the old server.
-
Set the Postfix user and Amavis user passwords to be the same as on the old server
-
Change the Spam training user and the Non-spam (HAM) training user account names to be the same as the spam account names on the old server.
-
Global Document Account — This account name is automatically generated and is usually named wiki. If you changed this, change the Global Document Account name to be the same account name as on the original server.
-
-
Change any other settings on the new server to match the configuration on the original server.
-
In the main menu, set the default backup schedule and the automatic starting of servers after the configuration is complete to NO.
-
Restoring a Backup to a New Server
-
Stop the new server
zmcontrol stop -
If the old server had additional storage volumes configured, mount the additional volumes now.
-
Delete the MariaDB data and reinitialize an empty data directory. If you do not do this,
zmrestoreofflinewill have errors. Aszimbra, type:rm -rf /opt/zimbra/db/data/* ; /opt/zimbra/libexec/zmmyinitThe MariaDB service is now running.
-
Copy all the files in the
/backupfolder from the old server or from an archive location to/opt/zimbra/backup. -
Restore the LDAP.
zmrestoreldap -lb <latest_label>If you are restoring a large number of accounts, you might run a command such as the UNIX command,
nohup, so that the session does not terminate before the restore is complete.To find the LDAP session label to restore, type zmrestoreldap –lbs. -
Ensure that the following services are running before attempting to execute
zmrestoreoffline.-
mysqld(MariaDB) -
slapd(OpenLDAP)zmcontrol start
-
-
Ensure that the following services are stopped before attempting to execute
zmrestoreoffline.-
mailboxdzmmailboxdctl stop
-
Because some Zimbra Collaboration services are running at this
point, type zmconvertctl start. This is required before running
zmrestoreoffline.
-
Sync your LDAP password from backup directory to the new production servers LDAP config.
zmlocalconfig -f -e zimbra_ldap_password=<password> -
Start the offline restore after stopping
mailboxd.zmmailboxdctl stop zmrestoreoffline -sys -a all -c -brYou might run a command such as
nohuphere also. To watch the progress, tail/opt/zimbra/log/mailbox.log.Use –con the command line so that accounts are restored, even if some accounts encounter errors during the offline restore process. -
Because some Zimbra Collaboration services are running at this point, type
zmcontrol stopto stop all services. -
Remove any old backup sessions because these sessions are no longer valid.
rm -rf /opt/zimbra/redolog/* /opt/zimbra/backup/* -
Start Zimbra Collaboration.
zmcontrol start -
Run a full backup.
zmbackup -f -a all -
Remove the firewall rules and allow client access to the new server.
Restoring from Different Failure Scenarios
The restoration steps are similar for most server failures you may encounter. If a failure occurs, review the disaster recovery section to understand the process and then follow the steps below for the specific type of failure.
Restore When LDAP is Corrupted
-
Reinstall the LDAP server. See the Zimbra Collaboration Installation guide.
-
Find the label for the LDAP session to restore. Run the
zmrestoreldap - lb <label>command, with no arguments to restore all accounts, domains, servers, COS, etc. for the LDAP server. -
Make sure that all accounts are in active mode. From the command line, type
zmprov ma zimbraAccountStatus active
Restore After Replacing Corrupted Partitions
-
If a partition becomes corrupted, replace the failed disk.
-
To restore the latest full and incremental backup files, run
zmrestore -a allThe zmrestore process automatically retrieves the list of all mailboxes on the specified mail host from the backup date and iterates through each mailbox to restore the mailboxes to the last known good state.
Restore After Corrupted or Unreadable Redo Log
If the redo log becomes unreadable, the mailboxd service stops and
cannot restart. If this happens, inspect the hardware and software to
find the source of the problem before proceeding.
Without the latest redo log, the Zimbra mailbox server cannot be returned to the most current state. The Zimbra mailbox data can be restored to the latest archived redo log state. A new redo log for current transactions is created after the Zimbra mailbox server is restored.
The mailboxd service must not be running, and all accounts must be in
maintenance mode before beginning.
|
-
Put all accounts into maintenance mode.
zmprov md <domain> zimbraDomainStatus maintenance -
With the
mailboxdservice not running, typezmrestoreofflineThe offline restore process begins by retrieving the list of all mailboxes on the specified mail host from the backup.
The offline restore than iterates through each mailbox to:
-
Delete the mailboxes on the server
-
Restore the last full backup from the backup area
-
Restore all incremental backups for that mailbox in order, since the last full backup. This involves replaying the redo logs from the backup target area
-
Replay all archived redo logs
Because the redo log for current transactions is not available, the mailbox server is returned to the state of the last archived redo log.
-
-
After the offline restore is complete, start Zimbra Collaboration server.
zmcontrol startup -
When the Zimbra mailbox server is up, run a full backup of the Zimbra server. The full backup must be run immediately to have the latest data backed up because the latest redo log is not available.
Change Local Configuration Files After Restoring Zimbra
The localconfig.xml file, located in the /opt/zimbra/conf folder,
includes the core Zimbra server configuration, such as paths and passwords,
This file is backed up in full and incremental backups. When you run an
incremental or full restore, the backed-up version of the localconfig.xml
is renamed localconfig.xml.restore and is copied to the /opt/zimbra/conf
directory.
If you have made changes since the last backup, you might need to replace
the localconfig.xml file with the restored copy. Compare these files, and
if the .restore file has the latest local configuration data, delete the
localconfig.xml file and rename the file with the .restore extension to
localconfig.xml.
Notes on Ephemeral Data
As of Zimbra Collaboration 8.8, ephemeral data is not backed up as part of the backup process. Since auth tokens are ephemeral attributes, the implication is that clients accessing accounts restored after deletion will need to re-authenticate; auth tokens generated prior to the backup will no longer work.
Ephemeral Storage SSDB Backend
Backing up Ephemeral Data in SSDB
If SSDB is used as the ephemeral backend, a backup will not include any ephemeral attributes.
Note: This section does not detail how to deploy and administer an SSDB server. For that information please see section SSDB Configuration Options.
Backing up the data stored in SSDB (if so configured) is done as follows:
ssdb-dump -h localhost -p 8888 -o /tmp/ephemeral-backup-<date>Note: If running in master / slave configuration the ssdb-dump should be run on the master.
Example backup
ssdb-dump - SSDB backup command
Copyright (c) 2012-2015 ssdb.io
recv begin...
received 1 entry(s)
received 10 entry(s)
received 100 entry(s)
received 1000 entry(s)
received 10000 entry(s)
received 100000 entry(s)
received 200000 entry(s)
received 300000 entry(s)
received 400000 entry(s)
received 400021 entry(s)
recv end
total dumped 400021 entry(s)
Compactions
Level Files Size(MB) Time(sec) Read(MB) Write(MB)
--------------------------------------------------
2 1 7 0 0 7
compacting data...
Compactions
Level Files Size(MB) Time(sec) Read(MB) Write(MB)
--------------------------------------------------
2 2 10 0 0 10
backup has been made to folder: /tmp/ephemeral-backup-<date>Restoring Ephemeral Data to SSDB
Restoring ephemeral data to SSDB from a backup can only be done with a backup from an SSDB server.
Restoration can be done in one of two ways:
-
import into a running server
-
override of existing data
Importing into a running server
Using the leveldb-import command provided with the SSDB software a backup created
with the ssdb-dump command can be imported into a running SSDB server.
leveldb-import localhost 8888 /tmp/ephemeral-backup-<date>/dataData override
-
Stop the SSDB server.
-
Copy the directory created using the
ssdb-dumpcommand previously to a known location. -
Update
ssdb.confconfiguration file to update thework_diroption to the proper path. -
Start the SSDB server back up and verify previously working logins still work.
Backups with LDAP backend
If the ephemeral backend is LDAP, a backup will not include auth tokens or CSRF tokens, but it will include the last login timestamp. Upon account restore, the appropriate "Last Login" value in the admin console will be restored.
Restore NG Backup to Zimbra 10
The NG backup restore utility will be helpful to customers who have upgraded to Zimbra 10, which now has a native backup and restore feature. This utility can read existing NG backups and restore them, providing a useful option for customers who have previously used NG backup.
To restore backups using the NG backup restore utility, it should be triggered on the server where the backup needs to be restored. However, before restoring the backup, admins should manually upload the backup folder from the NG server to the server where the restore is being performed. Once the backup folder has been uploaded, the NG backup restore utility can be executed to restore the backup data.
| 'zmrestorengbackup' is a separate package and can only be accessed via command line. It can be installed using the instruction 'apt-get install zimbra-restore-ngbackup' |
Purpose of the migration
Please note that this is not a general purpose restore utility for restoring old NG backups. This utility is only meant to help organizations for auditing and BCP testing purposes.
| Restoring from old NG backups for disaster recovery is not recommended. |
We recommend taking a full-backup using Zimbra backup feature immediately after installation for Zimbra Daffodil (v10) is complete. And then using this full-backup (in conjunction with incremental or auto-grouped backups) in case of disaster recovery.
The utility can be used for the following use cases where customers cannot avoid dealing with old NG Backups:
-
Large organisations, financial institutions and government customers have compliance requirements related to backing up old email data. These requirements come from auditor to conduct forensic accounting.
-
Several medium and large organisations need to create a Business Continuity Planning (BCP). During BCP testing, depending on the regulations applicable for that company, old backups may need to be restored to check if email data is accessible or not.
Please note that, restore happens in a separate environment (not on Production environment).
Syntax
zmrestorengbackup --ngbkdir=FILENAME
[--itemstorecover={all|{DOCUMENT MESSAGE}}]
[--account={all|ACCOUNTS}]
[--prefix=PREFIX]| Option | Short name | Description |
|---|---|---|
ngbkdir |
dir |
Specifies the path to the NG Backup extracted directory. This option is required. |
itemstorecover |
itr |
Specifies the items to recover from the backup. Valid options are "DOCUMENT", "MESSAGE", or "ALL". This option is required. If “ALL” is specified then both “DOCUMENT” and “MESSAGE” will be restored. |
account |
a |
Specifies the email address of the account to be restored. Multiple email addresses can be provided separated by whitespace. Use "all" to restore all accounts. This option is required. |
prefix |
pre |
Restore to a new target account. A prefix is prepended to the original account names. Example: abc@test.com will restored as <prefix>_abc@test.com This is optional. If not specified then will restored the original account. |
Usage Examples
-
To restore emails and documents for the for the account a@test.com to prefixed account name restore_abc@test.com
`zmrestorengbackup -a abc@test.com -pre restore -itr MESSAGE DOCUMENT -dir /opt/zimbra/mybackup/`
-
To restore documents for the account a@test.com
`zmrestorengbackup -a abc@test.com -itr DOCUMENT -dir /opt/zimbra/mybackup/`
-
To restore emails and documents (all - emails, documents for now) for the for the account a@test.com to prefixed account name sample_abc@test.com
`zmrestorengbackup -a abc@test.com -pre sample -itr all -dir /opt/zimbra/mybackup/`
Pre-requisites
Following are the module wise prerequisites which should be satisfied before migration is executed. Please note that these prerequisites may not be comprehensive and additional steps may be required depending on the specific server configurations
-
A backup must be taken on the NG server for the module/data that needs to be migrated.
-
The backup folder must be manually migrated/copied to the server where the backup will be restored.
-
The backup folder must have the correct permissions set to enable the restore process to access and read the backup files.- The restore process must be executed on the Z10 server where the module is installed and needs to be migrated.
Sequence of Migration
The following sequence needs to be adhered to for migration:
-
The utility required to restore the backup needs to be installed on the Z10 server.
-
The backup taken on the NG server needs to be manually transferred to the Z10 server.
-
The backup folder should be located in a directory that is accessible to the Zimbra user on the Z10 server. The ideal location for the backup folder would be "/opt/zimbra/zxbackup".
-
The domain for the account being restored should be present on the Z10 server.
Backup & Restore – Recommended Backup Strategies
This section provides guidance on selecting the appropriate backup strategy based on deployment size, data growth, and operational requirements. The recommendations below are applicable to the Enhanced Backup Engine (v2) and are fully compatible with legacy backup behavior.
Objectives
The objectives of this section are to:
Help administrators choose the most suitable backup strategy
Balance storage efficiency, performance, and recoverability
Provide predictable backup behavior across small, medium, and large environments
Enable informed planning for long-term retention and capacity growth
Standard Backup
Session Deduplication
Session deduplication in Enhanced Zimbra Backup v2 refers to the process of eliminating duplicate blobs within a single backup session. This means that during the creation of a full backup, any identical blobs that appear multiple times within that session are only stored once. The system creates references to the single unique blob and maintains metadata and reference mappings between physical blob and storage locations with reference counts. This reduces the overall size of the backup and improves storage efficiency for that specific backup run.
Session deduplication backup is enabled at the server or global configuration level when the following attributes are set:
-
zimbraBackupDeduplication = dedupe -
zimbraBackupDedupeCompressionType = zstdornocompression -
zimbraBackupCrossSessionDedupeEnabled = FALSE
This backup strategy is the default backup strategy and is similar to the older Standard Zimbra backup, providing the same level of reliability and redundancy, except that the full backup size is significantly reduced.
Backup Schedule
Session Deduplication (SD) backup with a retention period of 1 month (default).
-
Weekly full backup on Saturday
-
Incremental backups on the remaining days of the week
-
Deletion of backups after 30 days
Backup schedule should look like:
f 0 1 * * 6 -a all --mail-report
i 0 1 * * 0-5 --mail-report
d 1m 0 0 * * * --mail-reportLimitations
-
Deduplication is limited to a single backup session; there is no deduplication across different backup runs.
-
Every weekly full backup stores the entire data again, even if most of the data is unchanged.
-
Storage consumption grows significantly over time due to repeated full backups.
-
Backup windows can be longer during weekly full backups.
-
Higher storage I/O usage compared to cross-session deduplication approaches.
Pros
-
Simple and well-understood backup model.
-
Supports incremental backups using redo logs.
-
Easier recovery process since each full backup is self-contained.
-
No dependency on a single common backup set.
-
High compression ratio achieved using Zstandard as the compression engine.
-
Deduplication works for both internal and external data, providing highly efficient deduplication.
Cons
-
High storage redundancy due to repeated full backups.
-
Inefficient storage utilization.
-
Longer full backup durations every week.
-
Increased storage cost over time.
High-Level Data Size Projection
Hardware Resources: 4 vCPU, 16 GB RAM
Based on the following dataset composition:
-
Internal Local Data: 32%
-
External AWS Data: 68%
-
Unique Data: 40%
-
Duplicate Data: 60%
Weekly Data Size
| Day # | Backup Type | Percent Increase | Data Size (GB) | Total Data Size (GB) | Accounts | Backup Size (GB) |
|---|---|---|---|---|---|---|
Day 1 |
Full Backup |
167.00 |
167.00 |
100 |
74 |
|
Day 2 |
Incremental Backup |
5% |
8.35 |
175.35 |
108 |
14.4 |
Day 3 |
Incremental Backup |
5% |
8.77 |
184.12 |
116 |
10.00 |
Day 4 |
Incremental Backup |
5% |
9.21 |
193.32 |
124 |
10.50 |
Day 5 |
Incremental Backup |
5% |
9.67 |
202.99 |
132 |
11.00 |
Day 6 |
Incremental Backup |
5% |
10.15 |
213.14 |
140 |
11.70 |
Day 7 |
Incremental Backup |
5% |
10.66 |
223.80 |
148 |
12.50 |
Day 8 |
Full Backup |
223.80 |
148 |
102.00 |
||
Total |
246.1 |
Monthly Data Size
| Day # | Backup Type | Percent Increase | Data Size (GB) | Total Data Size (GB) | Accounts | Backup Size (GB) |
|---|---|---|---|---|---|---|
Day 1 |
Full Backup |
167.00 |
167.00 |
100 |
74 |
|
Day 2 |
Incremental Backup |
5% |
8.35 |
175.35 |
108 |
14.4 |
Day 3 |
Incremental Backup |
5% |
8.77 |
184.12 |
116 |
10.00 |
Day 4 |
Incremental Backup |
5% |
9.21 |
193.32 |
124 |
10.50 |
Day 5 |
Incremental Backup |
5% |
9.67 |
202.99 |
132 |
11.00 |
Day 6 |
Incremental Backup |
5% |
10.15 |
213.14 |
140 |
11.70 |
Day 7 |
Incremental Backup |
5% |
10.66 |
223.80 |
148 |
12.50 |
Day 8 |
Full Backup |
223.80 |
148 |
102.00 |
||
Day 9 |
Incremental Backup |
5% |
11.19 |
234.99 |
156 |
19.3 |
Day 10 |
Incremental Backup |
5% |
11.75 |
246.74 |
164 |
11.1 |
Day 11 |
Incremental Backup |
5% |
12.34 |
259.07 |
172 |
11.7 |
Day 12 |
Incremental Backup |
5% |
12.95 |
272.03 |
180 |
12.3 |
Day 13 |
Incremental Backup |
5% |
13.60 |
285.63 |
188 |
12.9 |
Day 14 |
Incremental Backup |
5% |
14.28 |
299.91 |
196 |
13.5 |
Day 15 |
Full Backup |
299.91 |
196 |
136.7 |
||
Day 16 |
Incremental Backup |
5% |
15.00 |
314.90 |
204 |
25.9 |
Day 17 |
Incremental Backup |
5% |
15.75 |
330.65 |
212 |
14.5 |
Day 18 |
Incremental Backup |
5% |
16.53 |
347.18 |
220 |
15.6 |
Day 19 |
Incremental Backup |
5% |
17.36 |
364.54 |
228 |
16.4 |
Day 20 |
Incremental Backup |
5% |
18.23 |
382.77 |
236 |
17.2 |
Day 21 |
Incremental Backup |
5% |
19.14 |
401.91 |
244 |
18.1 |
Day 22 |
Full Backup |
401.91 |
204 |
183.2 |
||
Day 23 |
Incremental Backup |
5% |
20.10 |
422.00 |
212 |
34.7 |
Day 24 |
Incremental Backup |
5% |
21.10 |
443.10 |
220 |
20.0 |
Day 25 |
Incremental Backup |
5% |
22.16 |
465.26 |
228 |
21.0 |
Day 26 |
Incremental Backup |
5% |
23.26 |
488.52 |
236 |
22.0 |
Day 27 |
Incremental Backup |
5% |
24.43 |
512.94 |
244 |
23.1 |
Day 28 |
Incremental Backup |
5% |
25.65 |
538.59 |
252 |
24.2 |
Day 29 |
Full Backup |
512.94 |
244 |
227.3 |
||
Day 30 |
Incremental Backup |
5% |
25.65 |
538.59 |
252 |
44.2 |
Cross Session Deduplication Weekly Backup
Cross-session deduplication in Enhanced Zimbra Backup v2 means that instead of deduplicating data only within a single backup run (session), Zimbra also deduplicates data across multiple backup sessions over time.
When the first Cross-Session Deduplication (CSD) full backup is taken (referred to as a common CSD backup), all unique blobs are stored once in a common full backup session.
On subsequent full backups:
-
If a blob already exists in the common full backup session, it is not written again.
-
Only references and metadata are added pointing to the existing blob.
-
New unique blobs found during subsequent full backups are appended to the common full backup session.
Cross-session deduplication backup is enabled at the server or global configuration level when the following attributes are set:
-
zimbraBackupDeduplication = dedupe -
zimbraBackupDedupeCompressionType = zstdornocompression -
zimbraBackupCrossSessionDedupeEnabled = TRUE
This backup strategy provides faster subsequent full backups and further improvement in storage space requirements compared to the Session Deduplication backup strategy.
Retention Behavior (CSD)
| Cross-session deduplication (CSD) backup retention policy is different from legacy or session deduplication backup retention. |
-
Full common backups are deleted only when all referencing full-delta backups are deleted.
-
Deletion of a full common backup is skipped even if the common backup is older than the retention period.
-
A new full common backup becomes eligible to be created one day before the end of the retention period.
-
The new common backup is created only when a full backup is triggered by the scheduler.
Backup Schedule
Cross-Session Deduplication (CSD) backup with a retention period of 1 month (default).
-
Full common backup on Day 1 and also on the first day of a new backup cycle (based on retention logic)
-
Full delta backup on remaining Saturday(s) in the cycle
-
Incremental backups on remaining days of the week
Backup schedule should look like:
f 0 1 * * 6 -a all --mail-report
i 0 1 * * 0-5 --mail-report
d 1m 0 0 * * * --mail-report| For CSD, the retention period can be configured to 6 months or 1 year. There is no requirement to create a new common backup every month. |
Limitations
-
Depends on a single common backup set for blob storage.
-
Corruption or loss of the common backup impacts all dependent backups.
-
No backup redundancy for blob data, as all blobs reside in a shared common backup.
Pros
-
Cross-session deduplication ensures blob data is stored only once.
-
Weekly full backups create delta backups, storing only newly added email data.
-
Significantly reduced storage usage compared to standard dedupe backups.
-
Supports incremental backups using redo logs.
-
Reduced backup window for weekly full backups.
-
Very high backup speed for delta backups since only changed data is backed up.
-
High compression ratio achieved using Zstandard as the compression engine.
-
Deduplication works for both internal and external data, providing highly efficient deduplication.
Cons
-
Delta backups depend on a single shared common backup.
-
Backup redundancy cannot be achieved.
High-Level Data Size Projection
Hardware Resources: 4 vCPU, 16 GB RAM
Based on the following dataset composition:
-
Internal Local Data: 32%
-
External AWS Data: 68%
-
Unique Data: 40%
-
Duplicate Data: 60%
Weekly Data Size
| Day # | Backup Type | Percent Increase | Data Size (GB) | Total Data Size (GB) | Accounts | Backup Size (GB) |
|---|---|---|---|---|---|---|
Day 1 |
CSD Common Full Backup |
167.00 |
167.00 |
100 |
89.00 |
|
Day 2 |
Incremental Backup |
5% |
8.35 |
175.35 |
108 |
13.70 |
Day 3 |
Incremental Backup |
5% |
8.77 |
184.12 |
116 |
7.40 |
Day 4 |
Incremental Backup |
5% |
9.21 |
193.32 |
124 |
7.80 |
Day 5 |
Incremental Backup |
5% |
9.67 |
202.99 |
132 |
8.10 |
Day 6 |
Incremental Backup |
5% |
10.15 |
213.14 |
140 |
8.50 |
Day 7 |
Incremental Backup |
5% |
10.66 |
223.80 |
148 |
9.00 |
Day 8 |
CSD Full Delta Backup |
223.80 |
148 |
51.00 |
||
Total |
194.5 |
Monthly Data Size
| Day # | Backup Type | Percent Increase | Data Size (GB) | Total Data Size (GB) | Accounts | Backup Size (GB) | Grown Size (GB) |
|---|---|---|---|---|---|---|---|
Day 1 |
CSD Common Full Backup |
167.00 |
167.00 |
100 |
72.00 |
164.83 |
|
Day 2 |
Incremental Backup |
5% |
8.35 |
175.35 |
108 |
13.70 |
|
Day 3 |
Incremental Backup |
5% |
8.77 |
184.12 |
116 |
7.40 |
|
Day 4 |
Incremental Backup |
5% |
9.21 |
193.32 |
124 |
7.80 |
|
Day 5 |
Incremental Backup |
5% |
9.67 |
202.99 |
132 |
8.10 |
|
Day 6 |
Incremental Backup |
5% |
10.15 |
213.14 |
140 |
8.50 |
|
Day 7 |
Incremental Backup |
5% |
10.66 |
223.80 |
148 |
9.00 |
|
Day 8 |
CSD Full Delta Backup |
223.80 |
148 |
51.00 |
|||
Day 9 |
Incremental Backup |
5% |
11.19 |
234.99 |
156 |
10.32 |
|
Day 10 |
Incremental Backup |
5% |
11.75 |
246.18 |
164 |
11.28 |
|
Day 11 |
Incremental Backup |
5% |
12.31 |
257.92 |
172 |
11.81 |
|
Day 12 |
Incremental Backup |
5% |
12.90 |
270.23 |
180 |
12.38 |
|
Day 13 |
Incremental Backup |
5% |
13.51 |
283.13 |
188 |
12.97 |
|
Day 14 |
Incremental Backup |
5% |
14.16 |
296.64 |
196 |
13.59 |
|
Day 15 |
CSD Full Delta Backup |
296.64 |
196 |
67.60 |
|||
Day 16 |
Incremental Backup |
5% |
14.83 |
311.47 |
204 |
13.67 |
|
Day 17 |
Incremental Backup |
5% |
15.57 |
327.05 |
212 |
14.95 |
|
Day 18 |
Incremental Backup |
5% |
16.35 |
343.40 |
220 |
15.69 |
|
Day 19 |
Incremental Backup |
5% |
17.17 |
360.57 |
228 |
16.48 |
|
Day 20 |
Incremental Backup |
5% |
18.03 |
378.60 |
236 |
17.31 |
|
Day 21 |
Incremental Backup |
5% |
18.93 |
397.53 |
244 |
18.17 |
|
Day 22 |
CSD Full Delta Backup |
397.53 |
244 |
90.59 |
|||
Day 23 |
Incremental Backup |
5% |
19.88 |
417.41 |
252 |
18.32 |
|
Day 24 |
Incremental Backup |
5% |
20.87 |
438.28 |
260 |
20.03 |
|
Day 25 |
Incremental Backup |
5% |
21.91 |
460.19 |
268 |
21.03 |
|
Day 26 |
Incremental Backup |
5% |
23.01 |
483.20 |
276 |
22.09 |
|
Day 27 |
Incremental Backup |
5% |
24.16 |
507.36 |
284 |
23.20 |
|
Day 28 |
Incremental Backup |
5% |
25.37 |
532.73 |
292 |
24.35 |
|
Day 29 |
CSD Full Delta Backup |
532.73 |
300 |
121.40 |
|||
Day 30 |
Incremental Backup |
5% |
26.64 |
559.36 |
308 |
24.56 |
Cross-Session Deduplication Daily Delta Backup
Cross-session deduplication daily delta backup follows the same behavior as the Cross-Session Deduplication Weekly Backup except for the differences listed below.
Everything else—including deduplication logic, common backup handling, and retention behavior—remains unchanged.
Key Differences from Weekly CSD Backup
-
Incremental backups (redo log backups) are not executed.
-
The system runs a daily full backup with no incremental backups.
-
Search indexes are not included in the backup.
Backup Schedule
Cross-session deduplication (CSD) backup with a retention period of 1 month (default).
-
Full COMMON backup on Day 1 and on the first day of a new backup cycle (based on retention logic).
-
Full DELTA backup runs daily on the remaining days in the cycle.
Backup schedule should look like:
f 0 1 * * * -a all --mail-report
d 1m 0 0 * * * --mail-reportNOTE: For CSD, the retention period can be configured to 6 months or 1 year. There is no requirement to create a new common backup every month.
Limitations
-
Redo logs are not generated; therefore, point-in-time restore is not supported.
-
Strong dependency on the integrity of the common backup repository.
-
Depends on a single common backup set for blob storage.
-
Corruption or loss of the common backup impacts all dependent backups.
-
No backup redundancy for blob data, as all blobs reside in a shared common backup.
Pros
-
Maximum storage efficiency due to cross-session deduplication.
-
No redo logs, significantly reducing storage usage.
-
Daily full backups are fast because only delta data is written.
-
Simplified backup schedule with no incremental backups.
-
Reduced backup and restore time compared to redo-log-based incremental approaches.
-
Minimum storage utilization and maximum speed can be achieved.
-
High compression ratio achieved using Zstandard as the compression engine.
-
Deduplication works for both internal and external data, providing highly efficient deduplication.
Cons
-
Loss of point-in-time restore functionality.
-
Loss of all CLI capabilities related to redo-log-based restore.
-
Delta backups depend on a single shared common backup.
-
Backup redundancy cannot be achieved.
High-Level Data Size Projection
Hardware Resources: 4 vCPU, 16 GB RAM
Based on the following dataset composition:
-
Internal Local Storage: 32%
-
External AWS Storage: 68%
-
Dataset Composition:
-
Unique Data: 40%
-
Duplicate Data: 60%
-
Weekly Data Size
| Day # | Backup Type | Percent Increase | Data Size (GB) | Total Data Size (GB) | Accounts | Backup Size (GB) |
|---|---|---|---|---|---|---|
Day 1 |
CSD Common Full Backup |
267.47 |
196 |
56 |
||
Day 2 |
Delta Backup |
3% |
8.02 |
275.49 |
204 |
2.00 |
Day 3 |
Delta Backup |
3% |
8.26 |
283.76 |
212 |
2.10 |
Day 4 |
Delta Backup |
3% |
8.51 |
292.27 |
220 |
2.20 |
Day 5 |
Delta Backup |
3% |
8.77 |
301.04 |
228 |
2.30 |
Day 6 |
Delta Backup |
3% |
9.03 |
310.07 |
236 |
2.40 |
Day 7 |
Delta Backup |
3% |
9.30 |
319.37 |
244 |
2.50 |
Total |
83.00 |
Monthly Data Size
| Day | Backup Type | Percent Increase | Total Data Size (GB) | Data Size (GB) | Total Accounts | Backup Size (GB) |
|---|---|---|---|---|---|---|
1 |
CSD Common Full Backup |
267.47 |
196 |
56 |
||
2 |
Delta Backup |
3% |
275.49 |
8.02 |
204 |
2.01 |
3 |
Delta Backup |
3% |
283.76 |
8.27 |
212 |
2.07 |
4 |
Delta Backup |
3% |
292.27 |
8.51 |
220 |
2.13 |
5 |
Delta Backup |
3% |
301.04 |
8.77 |
228 |
2.19 |
6 |
Delta Backup |
3% |
310.07 |
9.03 |
236 |
2.26 |
7 |
Delta Backup |
3% |
319.37 |
9.30 |
244 |
2.33 |
8 |
Delta Backup |
3% |
328.95 |
9.58 |
252 |
2.40 |
9 |
Delta Backup |
3% |
338.82 |
9.87 |
260 |
2.47 |
10 |
Delta Backup |
3% |
348.99 |
10.17 |
268 |
2.54 |
11 |
Delta Backup |
3% |
359.46 |
10.47 |
276 |
2.62 |
12 |
Delta Backup |
3% |
370.24 |
10.78 |
284 |
2.70 |
13 |
Delta Backup |
3% |
381.35 |
11.11 |
292 |
2.78 |
14 |
Delta Backup |
3% |
392.79 |
11.44 |
300 |
2.86 |
15 |
Delta Backup |
3% |
404.57 |
11.78 |
308 |
2.94 |
16 |
Delta Backup |
3% |
416.71 |
12.14 |
316 |
3.04 |
17 |
Delta Backup |
3% |
429.21 |
12.53 |
324 |
3.13 |
18 |
Delta Backup |
3% |
442.09 |
12.88 |
332 |
3.22 |
19 |
Delta Backup |
3% |
455.35 |
13.26 |
340 |
3.32 |
20 |
Delta Backup |
3% |
469.01 |
13.66 |
348 |
3.41 |
21 |
Delta Backup |
3% |
483.08 |
14.07 |
356 |
3.52 |
22 |
Delta Backup |
3% |
497.57 |
14.49 |
364 |
3.62 |
23 |
Delta Backup |
3% |
512.50 |
14.93 |
372 |
3.73 |
24 |
Delta Backup |
3% |
527.88 |
15.38 |
380 |
3.85 |
25 |
Delta Backup |
3% |
543.71 |
15.83 |
388 |
3.96 |
26 |
Delta Backup |
3% |
560.02 |
16.31 |
396 |
4.08 |
27 |
Delta Backup |
3% |
576.82 |
16.80 |
404 |
4.20 |
28 |
Delta Backup |
3% |
594.13 |
17.31 |
412 |
4.33 |
29 |
Delta Backup |
3% |
611.95 |
17.82 |
420 |
4.46 |
30 |
Delta Backup |
3% |
630.31 |
18.36 |
428 |
4.59 |
Auto-Grouped Backup
The Auto-Grouped Backup method in Zimbra is an alternative to the Standard backup method, designed specifically for very large deployments where performing a full backup of all mailboxes at once might take too long or consume excessive resources.
Key Characteristics
-
Group-based full backups Instead of backing up all mailboxes in a single run, auto-grouped backup divides mailboxes into groups and backs up one group per scheduled interval (for example, daily).
-
No separate incremental backups Because the system treats each group’s full backup as the equivalent of a combined full + incremental cycle, there is no separate incremental backup process.
-
Ideal for large environments This backup method is particularly useful when backing up all accounts within a single backup window is impractical.
-
Adaptive behavior Each run backs up:
-
Newly provisioned mailboxes that have never been backed up.
-
Mailboxes that have not been backed up within the defined schedule window.
-
Additional oldest backup mailboxes to balance workload across days.
-
-
Backup contents Each auto-grouped backup session contains full backups for that group along with the required redo logs.
-
Retention period The retention period for auto-grouped backup should be configured such that all accounts are backed up at least once before the end of the retention period.
LDAP Attributes Used for Auto-Grouped Backup
| LDAP Attribute | Description |
|---|---|
zimbraBackupMode |
Sets the backup method. Valid values include Standard and Auto-Grouped. To enable auto-grouped backup, set this attribute to Auto-Grouped. |
zimbraBackupAutoGroupedInterval |
Defines the interval used by internal logic to determine which accounts are eligible for backup in the next scheduled auto-grouped run. Typically kept the same as the scheduled full backup interval. |
Note: This attribute does not control backup execution. Execution is governed by the backup schedule configured in the server crontab. |
|
zimbraBackupAutoGroupedNumGroups |
Specifies the number of groups used to distribute mailboxes across the auto-grouped backup schedule. |
zimbraBackupAutoGroupedThrottled |
Optional. When set to TRUE, throttles mailboxes per run by limiting backup workload per interval (mailboxes are constrained to total mailboxes divided by scheduled days). Default is FALSE. |
zimbraBackupRetentionDays |
Defines the number of days backups are retained. Backup Scheduler deletes backups older than this value. Used by both Standard and Auto-Grouped backup methods. |
Key Points to Consider for Auto-Grouped Backup
-
Grouped full backups are triggered by the backup schedule configured in the server crontab. They are not governed by
zimbraBackupAutoGroupedInterval. -
zimbraBackupAutoGroupedIntervalis used only to identify which accounts are eligible for backup during the current auto-grouped run. It is typically set to match the full backup interval in the backup schedule for optimal behavior. -
zimbraBackupRetentionDaysmust be configured to ensure that at least one backup copy exists for every account.
Example Configuration
If:
* zimbraBackupAutoGroupedNumGroups = 7
* Full backup runs daily
* zimbraBackupAutoGroupedInterval = 1d
Then the minimum retention period required is:
zimbraBackupRetentionDays = 8d
Backup schedule example:
f 0 1 * * 0-6 --mail-report
d 8d 0 0 * * * --mail-reportRecommended Redundancy Configuration
To maintain four copies of full backups for all accounts, configure retention as follows:
f 0 1 * * 0-6 --mail-report
d 28d 0 0 * * * --mail-reportLimitations
-
Cross-session deduplication is supported only when compression is disabled (NoZip), which significantly increases storage usage due to Linux-based soft and hard links.
-
When compression is enabled, cross-session deduplication is not supported, resulting in redundant blob copies across backup cycles.
-
Backup duration is longer when NoZip is used, especially in very large environments, due to the volume of uncompressed data.
-
Storage requirements can grow substantially because uncompressed backups do not benefit from compression ratios such as Zstandard (which can reduce blob size to approximately 65% of the original).
Pros
-
Designed for very large environments with large account counts.
-
Divides accounts into groups, reducing load and runtime compared to backing up all accounts at once.
-
Supports cross-session deduplication when NoZip is used, reducing redundant storage of unchanged blobs.
-
Supports redo log-based incremental backups.
Cons
-
High storage consumption when using NoZip, especially in large deployments.
-
Longer backup times compared to compressed backups.
-
Enabling compression disables cross-session deduplication, resulting in redundant storage across multiple backup copies.
Strategy Comparison
The following table provides guidance on selecting an appropriate backup strategy based on overall mailstore data size.
| Mailstore Data Size | Recommended Backup Method | Backup Strategy Details |
|---|---|---|
Small – <500 GB |
Standard Backup – Session Deduplication (Scheduled) |
Use default or customized crontab schedules. Weekly full backups with daily incremental backups. Retain backups for at least 2 weeks (minimum of 2 full backups). |
Medium – 500 GB to 1 TB |
Standard Backup – Session Deduplication (Scheduled) |
Use default or customized crontab schedules. Weekly full backups with daily incremental backups. Retain backups for at least 2 weeks (minimum of 2 full backups). |
Large – 1 TB to 5 TB |
Standard Backup – Cross-Session Deduplication Weekly Backup (Scheduled) |
Weekly full backups with daily incremental backups scheduled via crontab. Regularly monitor backup job success and redo log size. |
Very Large – >5 TB |
Auto-Grouped + Snapshots or Standard Backup – Cross-Session Deduplication Daily Delta Backup (Scheduled) |
Combine auto-grouped backups with storage or SAN snapshots for crash-consistency and rapid recovery. Alternatively, run daily full backups scheduled via crontab and monitor job success. |
Performance and Resource Usage Expectations
This section provides guidance on expected backup performance and resource usage based on a representative dataset and commonly used tuning profiles.
Test Environment
-
Instance size: 4 vCPU, 16 GB RAM
-
Data size: 167 GB
-
Data distribution:
-
Local storage: 20%
-
External (AWS): 80%
-
-
Data composition:
-
Unique data: 40%
-
Duplicate data: 60%
-
Performance Profiles and Observed Behavior
| Profile | backup_zstd_compression_level | backup_copy_blob_parallelism_level | Backup Size (GB) | Backup Speed (GB/hr) | Peak CPU | Peak Memory | When to Recommend |
|---|---|---|---|---|---|---|---|
V2 – Default |
3 |
5 |
74 |
86.3 |
~25–30% |
~55–60% |
Safe default for most customers. ~22% size reduction and ~58% time reduction compared to Legacy backups, with moderate CPU usage. |
V2 – Performance (Low–Mid) |
3 |
8 |
74 |
~130–150 |
~30–40% |
~55–60% |
Suitable for customers with some CPU headroom who want shorter backup windows without maxing out the node. |
V2 – Performance (Balanced High) |
3 |
12 |
74 |
~160–190 |
~40–45% |
~60–62% |
Good middle ground providing strong performance gains while keeping CPU usage reasonable. Avoid overlap with heavy cron or reporting jobs. |
V2 – Aggressive |
3 |
16 |
74 |
~200–230 |
~45–55% |
~60–62% |
Intended for short backup windows on nodes with low mail activity during backup. Monitor CPU usage and user experience closely. |
V2 – Max Performance |
12 |
20 |
73 |
~270 |
~90–92% |
~67–68% |
Maximum throughput profile. Not recommended as a default. Use only when backups run in isolated windows and CPU saturation is acceptable. Avoid overlap with heavy cron or reporting jobs. |
Recommendation by Customer Scenario
| Scenario / Customer Need | Recommended Profile | Key Settings | Comments |
|---|---|---|---|
Typical production environment, balanced performance vs resource usage |
V2 – Default |
Compression = 3 Parallelism = 5 |
Moderate CPU usage and safest generic recommendation for most customers. |
Tight backup window with some CPU headroom |
V2 – Performance (Balanced High) |
Compression = 3 Parallelism ≈ 8 |
Strong reduction in backup time compared to default, while keeping CPU usage manageable on a 4 vCPU / 16 GB system. |
Backup-dedicated window with low mail activity and no heavy cron or reporting jobs |
V2 – Aggressive |
Compression = 3 Parallelism = 16 |
Suitable for environments prioritizing short backup windows. Requires close monitoring of CPU usage and user experience. |
Performance Parameter Tuning
This section describes the key Local Configuration (LC) parameters that influence backup performance, especially when backups involve external storage.
Performance Tuning Parameters
The following LC parameters directly affect performance when using external storage as part of the backup process.
backup_zstd_compression_level
Controls the Zstandard (ZSTD) compression level used for blob data.
-
Range: 1–22
-
Default: 3
Behavior
-
Higher value → better compression
-
Higher value → higher CPU utilization
Recommendation
-
Start with the default value of 3 for most environments.
-
Increase only if:
-
Storage is expensive or limited.
-
Adequate CPU headroom is available.
-
-
Treat values greater than 4 as storage-optimized but CPU-expensive and validate carefully before using in production.
backup_zip_copier_private_blob_zips
Determines the number of ZSTD-compressed TAR archives generated for blob storage during backup.
-
Range: 1–10
-
Default: 4
Behavior
-
Higher values create more parallel streams.
-
Common data across streams is stored once.
-
Increasing this value increases storage usage without providing significant performance improvement.
Recommendation
-
Keep the default value of 4.
-
Increasing this parameter is generally not recommended, as it does not meaningfully improve performance and increases storage consumption.
backup_copy_blob_parallelism_level
Controls how many blobs are compressed in parallel during backup.
-
Range: 5-20
-
Default: 5
Behavior
-
Higher value → higher backup throughput and shorter backup window.
-
Higher value → increased CPU usage.
Observed Impact
-
Increasing from 5 → 20:
-
Backup speed: ~86 GB/hr → ~270 GB/hr
-
Backup time: ~2 hours → < 40 minutes
-
CPU usage: increases from ~25% to ~90%
-
Recommendation
-
Start at the default value of 5.
-
Increase gradually:
-
Step to 6, then 8, then 10.
-
Observe CPU usage and impact on other services.
-
-
On 4 vCPU systems, avoid high values (15 or 20) if:
-
Heavy workloads such as cron jobs, indexing, or usage reporting run during backup.
-
-
Always pair changes with resource-level monitoring:
-
CPU
-
Memory
-
Disk I/O
-
Compression Level vs CPU Usage, Compression Efficiency, and Recommended Use
The following guidance helps administrators choose an appropriate Zstandard compression level based on CPU usage, compression efficiency, and backup duration trade-offs.
CPU ranges are indicative for a 4 vCPU / 16 GB RAM system during backup, assuming a moderate value of backup_copy_blob_parallelism_level = 5.
Memory utilization typically remains within a similar range (~50–65%). The primary impact of changing the compression level is on CPU usage and backup duration.
| backup_zstd_compression_level | Expected CPU Usage (Relative) | Expected Compression Efficiency | Expected Impact on Backup Duration | Recommended Use Case / Environment |
|---|---|---|---|---|
3 (Default) |
Moderate CPU (good balance) Peak ~25–30% |
Good compression (Observed in current V2 tests) |
Good – balanced speed vs size |
Recommended default for almost all customers. Balanced CPU usage, backup time, and compression efficiency. Works well with tuning parallelism. |
4–5 |
Moderately high CPU Peak ~35–40% |
Slightly better compression than level 3 |
Slightly slower than level 3 |
Suitable for customers who are slightly more storage-sensitive and have some additional CPU headroom, while still requiring acceptable backup windows. |
6–8 |
High CPU Can approach saturation with high parallelism Peak ~55–60% |
Moderate compression Smaller backup size |
Noticeably slower; CPU-bound |
Recommended for storage-constrained, CPU-rich environments. Use when storage cost is a priority and the customer can tolerate slower backups and higher CPU usage. |
9–12 |
Very high CPU Peak ~75–92% |
Better compression with diminishing returns |
Much slower; frequently CPU bottlenecked |
Not ideal and rarely recommended. Suitable only for niche scenarios such as extremely tight storage constraints or offline/maintenance backup windows. |
Visual Representation of Backup Types and Frequency Over a 30-Day Period
This section illustrates how different backup strategies execute over a 30-day timeline, highlighting the frequency and type of backups generated.
Session Deduplication (Standard Backup)
In the Session Deduplication model, weekly full backups are taken, with incremental backups on the remaining days.
| Timeline | Backup Type |
|---|---|
Day 1 |
Full |
Day 2 |
Incremental |
Day 3 |
Incremental |
Day 4 |
Incremental |
Day 5 |
Incremental |
Day 6 |
Incremental |
Day 7 |
Incremental |
Day 8 |
Full |
Day 9 |
Incremental |
Day 10 |
Incremental |
Day 11 |
Incremental |
Day 12 |
Incremental |
Day 13 |
Incremental |
Day 14 |
Incremental |
Day 15 |
Full |
Day 16 |
Incremental |
Day 17 |
Incremental |
Day 18 |
Incremental |
Day 19 |
Incremental |
Day 20 |
Incremental |
Day 21 |
Incremental |
Day 22 |
Full |
Day 23 |
Incremental |
Day 24 |
Incremental |
Day 25 |
Incremental |
Day 26 |
Incremental |
Day 27 |
Incremental |
Day 28 |
Incremental |
Day 29 |
Full |
Cross-Session Deduplication – Weekly Backup
In the Cross-Session Deduplication (Weekly) model, a COMMON backup is created initially. Subsequent weekly backups are DELTA backups, with incremental backups on other days.
| Timeline | Backup Type |
|---|---|
Day 1 |
Full-CSD-Common |
Day 2 |
Incremental |
Day 3 |
Incremental |
Day 4 |
Incremental |
Day 5 |
Incremental |
Day 6 |
Incremental |
Day 7 |
Incremental |
Day 8 |
Full-DELTA |
Day 9 |
Incremental |
Day 10 |
Incremental |
Day 11 |
Incremental |
Day 12 |
Incremental |
Day 13 |
Incremental |
Day 14 |
Incremental |
Day 15 |
Full-DELTA |
Day 16 |
Incremental |
Day 17 |
Incremental |
Day 18 |
Incremental |
Day 19 |
Incremental |
Day 20 |
Incremental |
Day 21 |
Incremental |
Day 22 |
Full-DELTA |
Day 23 |
Incremental |
Day 24 |
Incremental |
Day 25 |
Incremental |
Day 26 |
Incremental |
Day 27 |
Incremental |
Day 28 |
Incremental |
Day 29 |
Full-DELTA |
Cross-Session Deduplication – Daily Delta Backup
In the Daily Delta model, an initial CSD full backup is created, followed by daily FULL-DELTA backups. No incremental (redo-log) backups are generated.
| Timeline | Backup Type |
|---|---|
Day 1 |
Full-CSD |
Day 2 |
Full-DELTA |
Day 3 |
Full-DELTA |
Day 4 |
Full-DELTA |
Day 5 |
Full-DELTA |
Day 6 |
Full-DELTA |
Day 7 |
Full-DELTA |
Day 8 |
Full-DELTA |
Day 9 |
Full-DELTA |
Day 10 |
Full-DELTA |
Day 11 |
Full-DELTA |
Day 12 |
Full-DELTA |
Day 13 |
Full-DELTA |
Day 14 |
Full-DELTA |
Day 15 |
Full-DELTA |
Day 16 |
Full-DELTA |
Day 17 |
Full-DELTA |
Day 18 |
Full-DELTA |
Day 19 |
Full-DELTA |
Day 20 |
Full-DELTA |
Day 21 |
Full-DELTA |
Day 22 |
Full-DELTA |
Day 23 |
Full-DELTA |
Day 24 |
Full-DELTA |
Day 25 |
Full-DELTA |
Day 26 |
Full-DELTA |
Day 27 |
Full-DELTA |
Day 28 |
Full-DELTA |
Day 29 |
Full-DELTA |
Backup & Restore V2 – FAQ
Section 1 – Customer & Sales FAQ (High-Level)
1. What changes in backup after upgrading to the new version?
After upgrade:
-
The new backup engine (V2) is enabled by default.
-
Zstandard (Zstd) compression is enabled by default.
-
Deduplication is enabled by default within each backup run (session-level).
-
Cross-session deduplication (CSD) is off by default.
-
Existing backups remain usable.
-
New full backups use the V2 format unless explicitly switched back to V1.
If you are using any of the flags --zip, --zipStore, --noZip in your V1 Backup configuration, refer to the Transitioning to Backup Engine V2 section to transition to V2 Backup.
|
2. Will our existing backups still work?
Yes.
-
Existing V1 backups are not changed or deleted.
-
Restore automatically detects backup version.
-
Older backups can be restored using the latest version.
3. What is deduplication?
Deduplication means:
-
Identical content is stored only once.
-
Other copies reference the same stored data.
Benefits:
-
Reduced backup size
-
Reduced disk I/O
-
Better performance
Useful for:
-
Shared attachments
-
Large organizations
-
External storage deployments
4. What is Cross-Session Deduplication (CSD)?
CSD extends deduplication across multiple backup runs.
-
First run creates a COMMON backup.
-
Later runs create DELTA backups.
-
Only new or changed data is added.
Benefits:
-
Smaller long-term storage
-
Faster backups
-
Reduced storage cost
CSD works only with scheduled full backups and not with Autogroup backups.
5. Benefits of dedupe + compression
-
Smaller backup size
-
Faster backups
-
Lower storage cost
-
Efficient scaling
6. Will restores take longer?
No.
Restores are:
-
Same speed as V1 or
-
Slightly faster due to reduced data size and fast Zstd decompression.
7. Can we continue using V1 backups?
Yes.
CLI – Global
zmprov mcf zimbraBackupDeduplication nodedupe
zmprov mcf zimbraBackupDedupeCompressionType zip
zmprov mcf zimbraBackupCrossSessionDedupeEnabled FALSECLI – Server
zmprov ms <server_name> zimbraBackupDeduplication nodedupe
zmprov ms <server_name> zimbraBackupDedupeCompressionType zip
zmprov ms <server_name> zimbraBackupCrossSessionDedupeEnabled FALSEAdmin Console
Path: Configure → Global Settings → Backup/Restore
Uncheck Enable deduplication and select ZIP / NOZIP / ZIPSTORE.
8. What if a backup session is corrupt?
-
Behavior is same as V1.
-
Other sessions remain usable.
-
No additional risk due to V2.
Best practice:
-
Keep multiple backups
-
Test restores regularly
Section 2 – Support & Admin FAQ
1. Default settings after upgrade
-
Backup type: V2 dedupe
-
Compression: zstd
-
Deduplication: dedupe
-
CSD: FALSE
2. Why is backup size not reducing?
Common reasons:
Deduplication disabled
zmprov gs `zmhostname` zimbraBackupDeduplication
zmprov gcf zimbraBackupDeduplicationExpected: dedupe
Compression level
Localconfig:
-
backup_zstd_compression_level Range: 1–22 (default ~3)
Dataset not compressible
Media, ZIPs, videos reduce less.
3. How to verify deduplication
Mailbox log shows:
Duplicate blobs count : 5Check config:
zmprov gacf | egrep 'zimbraBackupDeduplication|zimbraBackupDedupeCompressionType|zimbraBackupCrossSessionDedupeEnabled'
zmprov gs `zmhostname` | egrep 'zimbraBackupDeduplication|zimbraBackupDedupeCompressionType|zimbraBackupCrossSessionDedupeEnabled'4. Dedupe vs Compression savings
Total savings come from:
-
Deduplication
-
Compression
Formula:
Backup savings ≈ Original size − Backup size
5. Enable / Disable dedupe & compression
Admin Console
Path: Configure → Global Settings → Backup/Restore
CLI – Global
zmprov mcf zimbraBackupDeduplication dedupe
zmprov mcf zimbraBackupDedupeCompressionType zstd
zmprov mcf zimbraBackupCrossSessionDedupeEnabled FALSECLI – Server
zmprov ms `zmhostname` zimbraBackupDeduplication dedupe
zmprov ms `zmhostname` zimbraBackupDedupeCompressionType zstd
zmprov ms `zmhostname` zimbraBackupCrossSessionDedupeEnabled FALSEImportant: Do not mix old and new backup methods.
6. Enable / Disable CSD
CLI
zmprov mcf zimbraBackupCrossSessionDedupeEnabled TRUE
zmprov ms <server_name> zimbraBackupCrossSessionDedupeEnabled TRUEAutogroup disables CSD automatically.
7. CSD COMMON creation & zimbraBackupCSDReset
A new COMMON is created when:
-
No existing COMMON
-
Retention expired
-
Attributes changed
-
CLI forced
zimbraBackupCSDReset is internal and should not be manually changed.
8. Why COMMON backup cannot be deleted?
COMMON cannot be deleted if DELTA backups depend on it.
Log warning:
Backup deletion skipped: CSD common backup <backup_label> is not eligible for deletionDelete DELTAs first.
9. One-off backups from CLI
Session-level dedupe
zmbackup -a all -f --dedupe
zmbackup -a all -f --dedupe --zstd
zmbackup -a all -f --dedupe --nocompressionCSD backups
zmbackup -a all -f --csd
zmbackup -a all -f --csd --zstd
zmbackup -a all -f --csd --nocompressionForce new COMMON:
zmbackup -a all -f --csdcDisable CSD for run:
zmbackup -a all -f --nocsdDelegated Administration
The global administrator can create different delegated administrator roles.
Delegated administrator roles can be as simple as having the rights to manage one or more distribution lists or reset forgotten passwords for one or more users, to having domain administration rights on one or more domains.
Two frequently used delegated administrator roles, domain administrator and distribution list administrator, are already defined. You can add administrators to these predefined roles with no other configuration necessary.
Target Types for Granting Administrative Rights
Delegated administration provides a way to define access control limits on targets and grant rights to administrators to perform tasks on the target.
A target is a Zimbra Collaboration object on which rights can be granted. Each target is associated with a target type that identifies the type of access control entries you can grant on the target.
When selecting a target type for a target consider the following:
-
Target: Which specific target are you granting rights? For example, if the target type you select is "domain", which domain do you mean? You specify a specific domain’s name (Target Name = example.com). Access Control Entries (ACE) are granted on that target. An ACE is stored in an LDAP attribute on the target entry.
-
Is the right you want to grant applicable to the selected target type? A right can only be applied on the relevant target type. For example, creating an account can only apply to a domain target type, and the setting passwords can only apply to accounts and calendar resources target types. If a right is granted on a target that is not applicable to the target, the grant is ignored.
-
When defining rights, you need to consider the scope of targets in which granted rights are effective. For example, the right to set the password is applicable only to accounts and calendar resources, but if this right is included in the domain targets list of rights, it is effective for all accounts or calendar resource in the domain.
| Target Type | Description of Target Scope |
|---|---|
Account |
An account entry (a specific user) |
Calendar Resource |
A calendar resource entry |
COS |
COS entry |
Distribution List |
Includes the distribution list and all distribution lists under this distribution list. If the right is applicable to accounts and calendar resources, all accounts and calendar resources that are direct or indirect members of this distribution list. |
Domain |
Applicable to a specific domain, not to any sub-domains. Sub-domains must be explicitly marked as targets. When domain is the target, the rights are granted for all accounts, calendar resources and distribution lists in the domain. |
Config |
Grants specific to global config |
Global ACL |
Administrator rights for all entries in a target type. For example, you could add an ACE to the Global Access Control List (ACL) that grants the right to create accounts on domains. Delegated administrator accounts that are granted this right can create accounts in all domains in the system. |
Server |
Server entry |
Zimlet |
Zimlet entry |
Rights
Rights are the functions that a delegated administrator can or cannot perform on a named target. A right is either system-defined or granted at the attribute level.
System-defined rights
Types of system defined rights include:
-
Preset rights (preset). For example,
createAccountcreates an account;renameDomain, renames the domain.Preset rights are associated with a fixed target type. For example,
createAccountis a right only on a domain;renameAccountis a right on an account;getServeris a right on a serverNo other rights are required to administer that action on the target.
Preset rights could involve accessing multiple targets. The grantee needs to have adequate rights on all pertinent targets. For example, to create an alias for an account, the grantee must have rights to add an alias to an account and to create an alias on a domain.
Attribute Right
Granting rights at the attribute level allow a delegated administrator/ administrator group to modify or view (or not modify or view) a specific attribute on a target.
Types of attributes rights include:
-
Attribute (
setAttrs) rights allow the domain administrator to modify and view an attribute value. For example, themodifyAccountright allows the domain administrator to modify all attributes of the account. -
Get attribute rights (
getAttrs) let the domain administrator view an attribute value. For example, thegetAccountright shows all the attributes for a user’s account.
The specific attribute being granted is configured on the target and the type of permission, read (get) or write (set), is specified.
Attribute rights can be granted in any combination of attributes to grant positive or negative rights. This lets you negate some attributes from a grant.
Combo Rights
Combo rights can be assigned to any target type and can include preset rights and attribute rights. You can use combo right to grant multiple attribute rights quickly on targets.
Negative Rights
Rights can be either positive or negative. Negative rights are rights specifically denied to a grantee.
-
When a negative right is granted to an admin group, all administrators in the group are denied that right for the target and sub-targets on which the right is granted.
-
When a negative right is granted to an administrator who may or may not be in an admin group, the specific administrator is denied that right for the target and sub-targets on which the right is granted.
An admin group is granted domain administrator rights, including the right
to create accounts on Domain1. AdminA is in this admin group, but you want
AdminA to have all domain administrator rights, except the right to create
accounts. You would grant a negative createAccount right to AdminA on the
target Domain1.
For grants on the same level, negative rights always take precedence. For example, AdminGroup1 is granted a positive right to view accounts in a domain; AdminGroup2 is granted a negative right to view accounts in the same domain. AdminA is a member in both admin groups. AdminA cannot view any account in this domain because the negative right takes precedence.
For grants on different levels, the most specific grant takes precedence. For example, AdminA is granted the negative right to view accounts in GroupDistributionList1, which User1 is a member. AdminA is also granted the positive right to view account directly on User1’s account. In this case, AdminA can view User1’s account as the grant on the account target is more specific than the grant on the distribution list.
Using the Rights List
System rights are listed and described in the Rights folder in the Administration Console Overview pane. You can use the Rights folder to help you define which system-defined rights to grant to delegated administrators. This folder displays the name of the right, the target types associated with that right, the right type and a brief description.
When you select a right on the page and click on it, another page displays more information:
-
For combo rights, a list of the rights associated with the combo right are listed.
-
For the other system rights, a list of attributes associated with the right are listed
You can use zmprov commands to view combo rights.
-
Direct sub-rights of a combo right
zmprov gr adminConsoleDLRights -
Second level sub-rights of the combo
zmprov gr adminConsoleDLRights -e
Viewing System Defined Rights Lists
You can use zmprov commands to view system defined rights for a specific
topic:
| To View This | Use This zmprov Command |
|---|---|
Account |
|
Calendar Resources |
|
COS |
|
|
|
Domain |
|
Global Config [2]
2. All rights for accounts and calendar resources can also be granted on domain targets. All rights for distribution list can also be granted on domain targets. When rights are granted on a domain, the ACEs apply the right to all direct or indirect account calendar resources, and members of the distribution list in the domain.
|
|
Global Grant [3]
3. All rights for all other targets can also be granted on the global targets. When any rights are granted on a global grant entry, the ACEs apply the right to all entries on the system. For example, if you grant a createAccount (which is a domain right) to AdminA on the global grant entry, AdminA can create accounts in all domains on the system.
|
|
Server |
|
Zimlets |
|
Implementing Delegated Administration
Before you create delegated administrators and grant rights, define the role and which rights to assign to the targets the administrator will manage.
For more efficient management of delegated administrators, create administrator groups and add individual administrator accounts to the group. An administrator group allows you to create role-based access control. Administrators with the same or almost the same responsibilities can be grouped into an admin group.
Delegated administration rights can be set up in one of the following methods:
-
Create an administrator or an administrator group and grant rights to the account using the Administrator Wizard.
-
Configure grants on existing administrator accounts. Add new rights or modify rights to an existing delegated administrator or administrator group account.
-
Add, modify and delete rights directly in a target’s Access Control List page.
Administrator Groups and Administrators
Administrator and group administrator accounts are created in the Administration Console.
Use the administration wizard to
-
Create the create either an Admin Group or an Admin Account.
-
Admin Groups are distribution lists (DL) that have Admin Group enabled, which flags it as a delegated administrator DL. After the admin group administrator is created and configured with rights and admin views, you add administrator user accounts to the admin group.
-
Admin Account is a user account that has Administrator enabled on the account.
-
-
Configure the admin views for the account. You select the views from the Directly Assigned Admin views list. An admin view represent the items the delegated administrator sees when logged on to the Administration Console.
A directly assigned admin view is the view set on the admin account. An inherited admin view is the view set on the admin group the account belongs to.
-
Configure the Grants. The Grants dialog displays a list the grants requiredto display the items you selected in the Directly Assigned Views column. You can accept these rights and add additional rights, skip this page to not configure these rights, or click Finish to accept these rights and quit the wizard.
Configure Grants on Administrator Accounts or Admin Groups
You can manage the rights granted to an administrator or an administrator group through the Configure Grants link on the accounts toolbar. When you click Configure Grant on the Manage Accounts Addresses toolbar, the Content pane shows a list of direct and inherited grants. You can grant rights, modify rights or delete rights on existing administrator accounts.
Grant ACLs to a Target
When you want to add a specific grantee or specific rights on a target you can edit the target directly. Each target has an ACL page which lists the granted ACLs. You can add, edit or delete the target’s grants. The administration account (grantee) is updated to reflect the change.
Revoking Rights
Global administrators can revoke any rights granted to an administrator.
Home → Manage → AccountsOpen the desired administrator account and click Configure Grants.
-
Select the right to revoke and click Delete.
-
When the dialog asks if are sure, click Yes.
Delegated administrators can revoke rights if the right was created with the Can Grant the right to other admins enabled.
Temporarily Revoke Delegated Admin Rights
To temporarily revoke rights to a delegated administrator account, you can edit the administrator account and remove the check next to the Administrator field. The ACLs are not removed from the account.
View Rights Granted to Administrators
The View Rights link from an admin account or admin group account toolbar displays the granted rights, readable attributes and modifiable attributes associated with a specific target. Click on the tabs to view rights for different targets.
Granting Predefined Rights
Delegated Administrators can be assigned predefined rights for common tasks. A common example is to create a Helpdesk administrator who can only reset password.
Home → Manage → Accounts → Delegated AdministratorFollowing commonly used rights have been predefined, and more are planned to be added in the future.
Domain administrator
When an admin is assigned a Domain administrator predefined right, the administrator can access all commonly used functionality that is required by an administrator who is managing a domain. Assigning this right to the user is equivalent of assigning the following rights and views:
-
Assigned rights
-
domainAdminRights
-
getDomainQuotaUsage
-
-
Assigned views
-
accountListView
-
downloadsView
-
DLListView
-
aliasListView
-
resourceListView
-
domainListView
-
certificatesView
-
saveSearch
-
Reset passwords
When an admin is assigned a Reset passwords predefined right, the administrator can access all commonly used functionality that is required by an administrator who is resetting password for an organization. Assigning this right to the user is equivalent of assigning the following rights and views:
-
Assigned rights
-
listDomain
-
listAccount
-
countAccount
-
countAlias
-
countCalendarResource
-
countDistributionList
-
listDistributionList
-
listAlias
-
changeAccountPassword
-
-
Assigned views
-
accountListView
-
downloadsView
-
DLListView
-
aliasListView
-
resourceListView
-
saveSearch
-
Edit contact info
When an admin is assigned an Edit contact info predefined right, the administrator can access all commonly used functionality that is required by an administrator who needs to edit contact information for users. Assigning this right to the user is equivalent of assigning the following rights and views:
-
Assigned rights
-
listDomain
-
listAccount
-
countAccount
-
countAlias
-
countCalendarResource
-
countDistributionList
-
listDistributionList
-
listAlias
-
getAccountInfo
-
domainAdminConsoleAccountsContactTabRights
-
-
Assigned views
-
accountListView
-
downloadsView
-
DLListView
-
aliasListView
-
resourceListView
-
saveSearch
-
Predefined Delegated Administrator Role
The following pre-configured administrator groups are created automatically. You can assign administrator accounts to these groups.
Domain Administration Group
The zimbradomainadmins delegated admin group grants all the rights
necessary to support Zimbra Collaboration domain administration for
accounts, aliases, distribution lists and resources.
Administrators who are part of the zimbradomainadmins group can create
and manage accounts including setting the account quota, aliases,
distribution lists, and resources accounts in their domain.
When domain administrators log onto the Administration Console, only the functions they are authorized to manage are displayed on the console’s Navigation pane.
Create Link from Zimbra Classic Web App Account to Admin Console
For domain administrators, all tasks are performed from the Administration Console. To facilitate easy log in, when a delegated administrator account is created, their Classic Web App account can have a link to the Administration Console.
The link is created from the zmprov CLI
zmprov md {server.example.com} zimbraWebClientAdminReference {https://server.example.com:7071/}| This feature is supported only in the Classic Web App. |
Distribution List Administration Group
The zimbradladmin delegated admin group grants all the rights necessary
to log on to the Administration Console and manage distribution lists.
Administrators who are part of this group can
-
View the account list
-
Create new distribution lists and delete distribution lists
-
Add, edit and remove members in a distribution list
Creating Delegated Administrator Roles
Manage multiple domains
To have one domain administrator manage more than one domain, you assign the rights to manage individual domains to the administrator account or administrator group.
For example, to set up domanadministrator1@example.com to manage domainexample1.com and domainexample2.com. Create a new administrator account on one of the domains to be managed.
-
Create the administrator account on one of the domains to be managed (domainexample1.com)
-
Select the views that domain administrators need to manage a domain. When the views are selected, the rights associated with these views automatically display on the Configure the Grants dialog.
-
Configure the grants for this domain if they are different from the grants associated with the views you select.
-
To add another domain to be managed (domainexample2.com).
-
On the Configure Grants page, click Add
-
Select the target type as domain
-
Enter the target’s domain name (domainexample2.com)
-
For Right Type, select System Defined Right
-
For Right Name type, adminConsoleAccountRights. Is Positive Right should be selected.
-
Click Add and More
-
The Add ACE page displays again and the Right Name field is empty. Type, adminConsoleDLRights and click Add and More.
-
Continue to add the following right names:
-
adminConsoleAliasRights
-
adminConsoleResourceRights
-
adminConsoleSavedSearchRights
-
adminConsoleDomainRights
-
-
After the last right, click Add and Finish. The Configure the Grants dialog displays these rights associated with the target domain. If you are adding another domain to manage, click Add and More. Repeat Step 4. If not, click Finish.
-
Manage Distribution Lists
To assign a user to manage a distribution list, you create a distribution list and enable Admin Group, select the view, grant the distribution list rights, add the user to the list and make that user an administrator.
-
Create a new distribution list:
-
Check Admin Group
-
Add the user who will be the administrator as a member of the DL.
-
Go to the Admin Views page and check Distribution List View so the admin can view the distribution list.
-
Click Save.
-
-
In the Configure Grants page, add the following rights.
Table 59. Rights Right Name Target Type Target Right Type The following right let the administrator manage distribution lists.listDistributionListdl
DL email address
SD Right
addDistributionListAliasdl
DL email address
SD Right
addDistributionListMemberdl
DL email address
SD Right
modifyDistributionListdl
DL email address
SD Right
getDistributionListMembershipdl
DL email address
SD Right
removeDistributionListMemberdl
DL email address
SD Right
This domain right displays user account list that the administrator can select from to add to a distribution list.listAccountdomain
DL email address
SD Right
Change Passwords
To create delegated administrators who only change passwords, you create the admin or admin group, select the views and grant the set Account Password combo right.
-
Select the following views
-
Account List view to be able to select accounts to change passwords
-
Alias List view to be able to find users who use an alias instead of account name.
-
-
The Configure the Grants page displays recommended grants for the views you have chosen. For Change Password rights, do not configure these grants. Select Skip. Click Add to add the following right:
Right Name Target Type Target Right Type setAccountPassworddomain
domain name
SD Right
View Mail Access Right
View Mail access right can be granted on accounts, domains, and distribution lists.
| Right Name | Target Type | Target | Right Type |
|---|---|---|---|
|
account, domain, dl |
account, domain, or distribution list address |
To prevent administrators from viewing an account with a domain or distribution list, assign the Is Negative Right to the account.
Manage Class of Service Assigned to Users
You can expand the domain administrator role to be able to view and change the class of service (COS) assigned to a user. To add the rights to manage the COS for a domain, add the following rights to the domain administrator account or domain administrator admin group.
Add the System Defined Rights to each COS in the domain.
| Right Name | Target Type | Target | Right Type |
|---|---|---|---|
|
cos |
COS name |
SD Right |
|
cos |
COS name |
SD Right |
|
cos |
COS name |
SD Right |
|
|||
|
domain |
domain name |
Attribute Right |
Manage Cross Mailbox Search
This role creates a delegated administrator role that can run the Search Mail tool to search mail archives or live mail for accounts. This also allows the administrator to create, abort, delete, purge or get status of a cross mailbox search request.
| The Archiving and Discovery feature must be installed for this feature to work. |
| Right Name | Target Type | Target | Right Type |
|---|---|---|---|
|
(combo) |
server name where cross mailbox searches can be run |
SD Right |
For full functionality, this role includes the ability to create new accounts so that the admin can create the target mailbox to receive the search results. If you do not want this role to have the ability to create accounts, grant the following negative right as well.
| Right Name | Target Type | Target | Right Type |
|---|---|---|---|
|
domain |
domain name |
If you want this admin to also view the target mailbox with the results of the cross mailbox search, grant the right to view that mailbox only.
| Right Name | Target Type | Target | Right Type |
|---|---|---|---|
|
account |
cross mailbox search target account name |
Manage Zimlets
This role creates a delegated administrator role that can create, deploy and view Zimlets.
| Right Name | Target Type | Target | Right Type |
|---|---|---|---|
|
server, domain |
server name or domain name |
SD Right |
|
server, domain |
server name or domain name |
SD Right |
Manage Resources
This role creates a delegated administrator that can create and manage resources.
| Right Name | Target Type | Target | Right Type |
|---|---|---|---|
|
combo |
server name or domain name |
SD Right |
Access to the Saved Searches
This role creates a delegated administrator that can access all the searches saved in the Administration Console Navigation pane, Search section.
| Right Name | Target Type | Target | Right Type |
|---|---|---|---|
|
combo |
server name or domain name |
SD Right |
Access to the Server Status Pages
This role creates a delegated administrator that can access the Server Status page. In addition to granting this right, you must also select the Admin View, Global Server Status View.
| Right Name | Target Type | Target | Right Type |
|---|---|---|---|
|
global |
SD Right |
| Accounts that are configured as global administrator accounts cannot be granted ACLs. Global administrator accounts automatically have full rights on Zimbra Collaboration. If an ACL is added to a global administrator account, it is ignored. If a delegated administrator account is changed to a global administrator account, any ACLs associated with the account are ignored. |
Zimlets
Zimlets are a mechanism to integrate Zimbra with different third-party applications to enhance the user experience from the Zimbra Classic Web App. With Zimlets, users can look at information and interact with the third-party application from within their email messages. Zimlets can be made available from the Zimbra Classic Web App Overview Pane to users by modifying the Class of Service (COS).
Classic Web App lists only the classic zimlets.
Zimbra includes several predefined Zimlets. You can also create Zimlets or download them from the Zimlet Gallery located on the Zimbra Web site.
In Admin Console → Home → Configure → Zimlets, zimlets developed for Modern Web App have (Modern) in Description.
Default zimlets in Classic Web App
Classic Web App lists only th
Predefined Zimlets, when enabled, let users preview the following in Classic Web App:
-
Mouse over a date or time and see what is in calendar.
-
Mouse over a name or email address and see details from the address book for this name.
-
Right-click on a phone number to make a call with your soft-phone.
-
Right-click on a date to schedule a meeting.
-
Right-click on a name, address, or phone number to update address book information.
Managing Zimlets from the Administration Console
The following Zimlet management tasks are available from the Zimbra Administration Console.
-
Deploy a Zimlet, which creates the Zimlet entry in the LDAP server, installs the Zimlet files on the server, enables the Zimlet and makes it available to the members of the default COS.
-
Make a Zimlet available or not available per COS or account.
-
Make a Zimlet mandatory.
-
Disable a Zimlet, which leaves it on the server, but the Zimlet is not used.
-
Undeploy a Zimlet, which removes it from the COS listings and the Zimlets list but does not uninstall the Zimlet from the server.
| You cannot uninstall a Zimlet from the Administration Console. |
Deploying Custom Zimlets
You can download and deploy custom Zimlets from the Zimlet Gallery located on the Zimbra Web site. When a Zimlet is deployed, it is available immediately to everyone in the default COS. If a Zimlet is not deployed to another COS directly, the COS displays the Zimlets but they are not enabled.
- Admin Console:
-
Home → Configure → Zimlets, from the Gear icon select Deploy
-
Browse to the Zimlet you want to deploy, then click Deploy.
The Zimlet deploys to the server. A dialog displays indicating the server name where the Zimlet is deployed and the status of the deployment.
-
Click Finish.
Verify the Zimlet is enabled by viewing the Zimlets page.
Enable, Disable, or Make Zimlets Mandatory
You can enable, disable, or make Zimlets mandatory. You can also use the toggle feature to choose if an installed Zimlet will be made available for users to choose from.
- Admin Console:
-
Home → Configure → Class of Service → COS → Zimlets
| Setting | Description |
|---|---|
Mandatory |
Zimlet will always be enabled in user accounts. Users do not see these Zimlets on their Zimlet page. |
Disabled |
Zimlet will not be immediately available to users in the associated COS. |
Enabled |
All deployed Zimlets will be enabled. |
| Users can enable or disable optional Zimlets from their account’s Preferences → Zimlets page. If you select a Zimlet as mandatory, it cannot be disabled by the user. |
Undeploying a Zimlet
When a Zimlet is undeployed, it is removed from all COSs and then removed from the LDAP.
- Admin Console:
-
Home → Configure → Zimlets
-
Select a Zimlet to undeploy.
-
From the Gear icon menu select Undeploy.
-
Click Yes to confirm.
-
Adding Proxy-Allowed Domains to a Zimlet
Proxy Allowed Domains lets you configure which external domains can be accessed through a Zimlet. For the Zimlets that are included in Zimbra, proxy allowed domains are already configured. If you download and deploy other Zimlets, you can add additional proxy domain names.
- Admin Console:
-
Home → Configure → Class of Service
-
Select the COS to edit.
-
In the Advanced page, scroll down to the Proxy Allowed Domains section.
-
Click Add Domain to add domains.
-
Click Save.
-
Upgrading a Zimlet
Use the same steps as deploying a new Zimlet to upgrade a customized Zimlet. The new Zimlet zip file should have the same name as the existing Zimlet zip file.
- Admin Console:
-
Home → Configure → Zimlets, from the Gear icon select Deploy
-
Check Flush Zimlet cache, so that the upgraded zimlet will be used.
-
Browse to the Zimlet you want to upgrade, then click Deploy.
-
Click Finish.
-
Managing Zimlets from the Command Line Interface
The following Zimlet management tasks are available from the command line interface.
Deploying Zimlets
When a Zimlet is deployed, it is available immediately to everyone in the default COS. If a Zimlet is not deployed to another COS directly, the COS displays the Zimlets but they are not enabled.
Deploy a Zimlet using the CLI, including modifying the COS before deploying.
-
Select a Zimlet and copy the Zimlet
zipfile to/tmpfolder on your Zimbra server. -
Login as the zimbra user
su - zimbra -
Deploy the Zimlet
zmzimletctl deploy /tmp/<zimlet>.zip
Adding Proxy Allowed Domains to a Zimlet
When deploying a Zimlet, the COS attributes, zimbraProxyAllowedDomains,
must be set for the domain address that the Zimlet might call to get information.
To set the zimbraProxyAllowedDomains attribute, type:
zmprov mc <COSname> +zimbraProxyAllowedDomains '*.example.com'The * must be added before the example.com.
This must be applied to all COSs that have your Zimlet enabled.
Deploying a Zimlet and Granting Access to a COS
Use steps in this section to deploy a Zimlet to one or more COSs other than the default:
-
Login as zimbra user: su – zimbra
-
Copy the Zimlet file from Gallery to /tmp folder.
-
Install the Zimlet to the default COS:
zmzimletctl deploy /tmp/<zimlet>.zip -
To deploy the zimlet to additional COSs, run:
zmzimletctl acl <zimletname> <cosname1> grantThis will grant permission to
cosname1. You can also grant access to more than one COS on the same command line:zmzimletctl acl <zimletname> <cosname1> grant <cosname2> grant -
To allow this zimlet to use the allowed proxy domains, run the following on each COS and add the allowed domains.
zmprov mc <COSname1> +zimbraProxyAllowedDomains '*.example.com' zmprov mc <COSname2> +zimbraProxyAllowedDomains '*.example.com'
Viewing Installed Zimlets
Use the zmzimletctl command to view currently installed Zimlets:
zmzimletctl listZimlets allThe output from this command displays the Zimlets installed on the server, installed in LDAP, and those available by COS.
Changing Zimlet Configurations
Some Zimlets may require additional configuration after they are deployed.
The Zimlet configuration template allows you to make changes on the configuration template and then install the new configuration file on the Zimbra server.
Use steps in this section to change a Zimlet configuration:
-
Extract the configuration template:
zmzimletctl getConfigTemplate <zimlet.zip> -
Make the required changes in the template, taking care to change only the required areas, then save the file.
If you have more than one custom Zimlet, rename the config template.xml file before updating the configuration in LDAP so that files are not overwritten. -
Use the
zmzimletctlcommand to update the configuration in the LDAP. If you changed the name of the configuration template, replaceconfig_template.xmlwith the new name.zmzimletctl configure config_template.xml
Upgrading a Zimlet
Upgrading a customized Zimlet is performed by using the same steps as those used to deploy a new Zimlet.
The new Zimlet zip file should be named identically to the existing Zimlet
zip file.
|
Use steps in this section upgrade a Zimlet:
-
Copy the Zimlet
zipfile to the/opt/zimbra/zimlets-extrafolder, replacing the older version. -
Deploy the Zimlet
zmzimletctl deploy <zimlet.zip file name>The Zimlet is copied to the
/opt/zimbra/zimlets-deployedfolder. If your Zimlet includes a.jspfile, the.jspfile is also copied to the/opt/zimbra/jetty/webapps/zimlet/<zimletnamefolder>. -
To ensure availability of the newer version, flush the cache:
zmprov flushCache zimlet
Using the Zimbra Gallery
You can download and deploy Zimlets from the Zimlet Gallery located on the Zimbra web site. Go to https://www.zimbra.org/extend/ and scroll through the Extensions from the Zimbra Gallery section.
Developing Customized Zimlets
To develop your own custom Zimlets, see the Zimlet Developers Guide on the Zimbra Wiki at https://wiki.zimbra.com.
Configuring Zimlets for Modern Web App
Zimlets are plugins which enhance the Modern Web App’s functionalities. The zimlets need to be configured and authorized before you can use them with the Modern Web App.
Modern Web App lists only the modern zimlets.
Default zimlets in Modern Web App
Default Zimlets, for Modern Web App, let users perform the following tasks:
-
Restore contacts from previous backups
-
Add additional signatures for replies, forwards, or new emails
-
Detect dates from given content and provide event list of that day on mouse hover
-
Use Zimbra as a progressive web app
-
Subscribe to external calendar feeds
-
Add an option in settings to change default client in Zimbra
| Zimlets developed for Modern Web App have (Modern) in description. |
Configuring LDAP
This section is a basic guide to configuring the necessary LDAP properties for zm-oauth-social.
Assumes basic Zimbra Collaboration CLI knowledge.
The following examples may be used as a starting point for configuring the required LDAP properties to enable use of the zm-oauth services.
As the Zimbra Collaboration user, these properties can be applied globally as in the following examples, or applied to specific domains.
Basic Info
Basic Template For User OAuth Token Configuration
zimbraOAuthConsumerRedirectUri is the app’s relay during the oauth flow (i.e. where the social media site will send the user with a one-time use code to continue the oauth flow).
The left part of the LDAP value must match the app’s whitelist.
zmprov mcf +zimbraOAuthConsumerRedirectUri 'https://<zimbra-hostname>:<port>/service/extension/oauth2/authenticate/<client>:<client>'
zimbraOAuthConsumerCredentials is the app’s credentials — provided by the social media app setup.
verification_token may be left out for all clients except Zoom.
These credentials tie the oauth flow to a specific app.
The clientId is used by an end-user to request an oauth code, then the clientId + clientSecret are both used by the Zimbra Collaboration server to exchange that code for an access_token.
zmprov mcf +zimbraOAuthConsumerCredentials '<clientId>:<clientSecret>[:<verification_token>]:<client>'
zimbraOAuthConsumerAPIScope is the app’s required scopes for the specified auth type (caldav,contact,noop). These scopes determine what permissions are requested from an authorizing user during the social media site leg of the oauth flow.
zmprov mcf +zimbraOAuthConsumerAPIScope '<scope><delimiter><scope><delimiter>. . .:<client>_<type>'
Client Examples
Dropbox Example
| The following is required configuration for dropbox. |
zmprov mcf +zimbraOAuthConsumerRedirectUri 'https://your.mail.server.host.here/service/extension/oauth2/authenticate/dropbox:dropbox' zmprov mcf +zimbraOAuthConsumerCredentials 'yourDropboxClientIdHere:yourDropboxClientSecretHere:dropbox'
See Setting Up Dropbox for instructions on obtaining a Client Id, and Client Secret.
Google Example
| The following is required basic google configuration. |
zmprov mcf +zimbraOAuthConsumerRedirectUri 'https://your.mail.server.host.here/service/extension/oauth2/authenticate/google:google' zmprov mcf +zimbraOAuthConsumerCredentials 'yourGoogleClientIdHere:yourGoogleClientSecretHere:google' zmprov mcf +zimbraOAuthConsumerAPIScope 'https://www.googleapis.com/auth/drive:google_noop'
See Setting Up Google Drive for instructions on obtaining a Client Id and Client Secret.
Microsoft Example
| The following is required basic microsoft configuration. |
zmprov mcf +zimbraOAuthConsumerRedirectUri 'https://your.mail.server.host.here/service/extension/oauth2/authenticate/outlook:outlook' zmprov mcf +zimbraOAuthConsumerCredentials 'yourMSClientIdHere:yourMSClientSecretHere:outlook' zmprov mcf +zimbraOAuthConsumerAPIScope 'profile+User.Read+Files.ReadWrite.All:outlook_noop'
See Setting Up OneDrive for instructions on obtaining a Client Id, and Client Secret.
Slack Example
| The following is required configuration for slack. The scopes are only applied when authorization is performed for the noop scope. |
zmprov mcf +zimbraOAuthConsumerRedirectUri 'https://your.mail.server.host.here/service/extension/oauth2/authenticate/slack:slack' zmprov mcf +zimbraOAuthConsumerCredentials 'yourSlackClientIdHere:yourSlackClientSecretHere:slack' zmprov mcf +zimbraOAuthConsumerAPIScope 'groups:write,team:read,users:read,users:read.email,chat:write,mpim:write:slack_noop'
See Setting Up Slack for instructions on obtaining a Client Id and Client Secret.
Zoom Example
| The following is required configuration for zoom. The scopes are only applied when authorization is performed for the noop scope. |
zmprov mcf +zimbraOAuthConsumerRedirectUri 'https://your.mail.server.host.here/service/extension/oauth2/authenticate/zoom:zoom' zmprov mcf +zimbraOAuthConsumerCredentials 'yourZoomClientIdHere:yourZoomClientSecretHere:yourZoomVerificationTokenHere:zoom' zmprov mcf +zimbraOAuthConsumerAPIScope 'meeting:write:zoom_noop' zmprov mc default +zimbraProxyAllowedDomains 'api.zoom.us'
The last line of the above code block allows Zimbra Collaboration to perform proxy requests for the Zoom zimlet to the Zoom API on behalf of default class of service Zimbra Collaboration accounts. This is necessary for the Zoom Zimlet’s basic operations. If users on other class of services should have access, this may be applied on those as well.
See Setting Up Zoom for instructions on obtaining a Client Id, Client Secret, and Verification Token.
Domain Configuration
Details
Configuring the credentials of a single domain will override the credentials inherited from global configuration for that domain. Because of this, it is possible to configure just the credentials, and allow the domain to inherit the redirect uri and scopes if neither of these configurations should differ between the global and domain app.
Dropbox Example
The following is an example for applying dropbox app credentials, which has no additional scope requirements, on the Zimbra Collaboration domain example.zimbra.com:
|
zmprov md example.zimbra.com +zimbraOAuthConsumerRedirectUri 'https://your.mail.server.host.here/service/extension/oauth2/authenticate/dropbox:dropbox' zmprov md example.zimbra.com +zimbraOAuthConsumerCredentials 'yourDropboxClientIdHere:yourDropboxClientSecretHere:dropbox'
Setting Up Dropbox
- Create a Dropbox Application
-
-
Visit Dropbox App Console
-
Choose Create app.
-
Choose Dropbox API with Full Dropbox access, name your app, then click create app.
-
Adjust and configure the following Redirect URLs in the OAuth 2 section:
-
https://<hostname>/service/extension/oauth2/authenticate/dropbox -
https://<hostname>/@zimbra/service/extension/oauth2/authenticate/dropbox
-
-
Adjust and configure the relevant hostnames in the Chooser/saver domains section.
-
Fill out the application Branding information and descriptions.
-
Click Enable additional users so that others may authorize with the app.
-
- Configure the new Application Credentials in Zimbra Collaboration
-
-
Acquire the App key and App Secret from the Settings tab.
-
See Configuring LDAP.
-
Setting Up Google Drive
- Create a Google APIs Application
-
-
Visit Google API Console.
-
Select Select a project from the project dropdown menu in the top navigation bar.
-
Select New Project.
-
Configure the project name (and optionally organization location).
-
Select + Enable APIs and Services
-
Search for Google Drive then select Google Drive API.
-
Select Enable.
-
Select Google APIs to return to the APIs & Services menu.
-
Navigate to the APIs & Services section: OAuth consent screen via the left navigation menu.
-
Choose either internal or external application type, then configure the basic application information.
-
Select Add scope then enable all of the scopes related to Google Drive.
-
Add your mail server’s host as an authorized domain.
-
Select Save.
-
Navigate to the APIs & Services section: Credentials via the left navigation menu.
-
Select + Create Credentials, then select OAuth client ID.
-
Choose Web application as the Application type.
-
Configure the application name.
-
Under Authorized JavaScript origins select + Add URI then adjust and add your mail server’s hostname (Replace "hostname" with the public hostname of your Zimbra Collaboration server):
-
https://hostname
-
-
Under Authorized redirect URIs select + Add URI then adjust and add the following redirect URIs (Replace "<hostname>" with the public hostname of your Zimbra Collaboration server):
-
https://<hostname>/service/extension/oauth2/authenticate/google -
https://<hostname>/@zimbra/service/extension/oauth2/authenticate/google
-
-
Select Create, then copy the Client ID and Client Secret.
-
- Configure the new Application Credentials in Zimbra Collaboration
-
-
Acquire the App key and App Secret from the Settings tab.
-
See Configuring LDAP.
-
Setting Up OneDrive
- Create a Microsoft Azure Application
-
-
Visit Azure Portal.
-
Search for and select App Registrations.
-
Select New registration.
-
Configure the application name.
-
Under Supported account types, select Accounts in any organizational directory and personal Microsoft account.
-
Adjust and add the following Redirect URL (Replace "<hostname>" with the public hostname of your Zimbra Collaboration server):
-
https://<hostname>/service/extension/oauth2/authenticate/outlook
-
-
Select Register.
-
Navigate to the Manage section: Authentication via the left navigation menu.
-
Select Add URI then adjust and add the following Redirect URL (Replace "<hostname>" with the public hostname of your Zimbra Collaboration server), then click Save:
-
https://<hostname>/%40zimbra/service/extension/oauth2/authenticate/outlook
-
-
Navigate to the Manage section: API Permissions via the left navigation menu.
-
Add the required Microsoft Graph Delegated Permissions, then click Save:
-
email
-
offline_access
-
openid
-
profile
-
Files.ReadWrite.All
-
User.Read
-
-
Navigate to the Manage section: Certificates & secrets via the left navigation menu.
-
Select New client secret, add a description, and no expiration.
-
Repeat this task, removing previously created entries, until a
Valuewithout a:is created (secret must not contain colons for compatibility reasons), then click Save.Configure the new Application Credentials in Zimbra
-
Acquire the
Application (client) IDfrom theOverviewvia the left navigation menu, andClient Secretfrom the Manage section:Certificates & secretsvia the left navigation menu.
-
- Configure the new Application Credentials in Zimbra Collaboration
-
-
Acquire the App key and App Secret from the Settings tab.
-
See Configuring LDAP.
-
Setting Up Slack
- Create a Slack Application
-
-
Visit Slack App Management
-
Configure the Basic Information section after creating the Application.
-
Navigate to the Features section: OAuth & Permissions via the left navigation menu.
-
Add the required Bot Token Scopes:
-
chat:write
-
-
Add the required User Token Scopes:
-
chat:write
-
groups:write
-
mpim:write
-
team:read
-
users:read
-
users:read.email
-
-
Adjust and add the following Redirect URLs (Replace "<hostname>" with the public hostname of your Zimbra Collaboration server):
-
https://<hostname>/service/extension/oauth2/authenticate/slack -
https://<hostname>/@zimbra/service/extension/oauth2/authenticate/slack
-
-
Configure the Bot Name in Features section: App Home.
-
- Configure the new Application Credentials in Zimbra Collaboration
-
-
Acquire the App key and App Secret from the Settings tab.
-
See Configuring LDAP.
-
Setting Up Zoom
| Zoom app marketplace has has recently disabled Zimbra’s Zoom integration. We are evaluating this further and will update the documentation based on the conclusion of the evaluation. |
| For Zoom to work with Zimbra Collaboration, the server must have ephemeral storage configured. |
- Create a Zoom Application
-
-
Sign-in to Zoom as your organization‘s owner or an organization account with the developer role.
-
Visit Zoom App Management
-
Choose Develop → Build App → OAuth → Create
-
Configure the App name, turn on User-managed app, leave on the intent to publish, then click Create.
-
Navigate to the App Credentials section via the left navigation menu.
-
Add the following Redirect URL to the Production section (Replace "<hostname>" with the public hostname of your Zimbra Collaboration server):
-
https://<hostname>/service/extension/oauth2/authenticate/zoom
-
-
Add the following Whitelist URLs (Replace "<hostname>" with the public hostname of your Zimbra Collaboration server):
-
https://<hostname>/service/extension/oauth2/authenticate/zoom -
https://<hostname>/@zimbra/service/extension/oauth2/authenticate/zoom
-
-
Navigate to the Information section via the left navigation menu.
-
Configure the Deauthorization Notification Endpoint URL (Replace "<hostname>" with the public hostname of your Zimbra Collaboration server):
-
https://<hostname>/service/extension/oauth2/deauthorization/zoom
-
-
Navigate to the Scopes section via the left navigation menu.
-
Add the required Scopes:
-
meeting:write
-
user:read
-
-
Navigate to the Submit section via the left navigation menu.
-
Generate a Publishable URL then leave the Submit page (do not submit the app if using for a single Zoom Organization account).
-
- Configure the new Application Credentials in Zimbra Collaboration
-
-
Acquire the App key and App Secret from the Settings tab.
-
See Configuring LDAP.
-
Setting up NextCloud
For easy understanding of the steps, we will refer to following examples throughout the section:
NextCloud Server - nextcloud.server.com
Zimbra Server - myzimbra.server.com
Domain - example.com
| You can skip step #1 if you already have NextCloud server setup available. |
-
Setup a NextCloud server by following this video - https://www.youtube.com/watch?v=QXfsi0pwgYw
-
Install NextCloud zimlet and its dependencies on Zimbra Server:
-
To install on Red Hat and CentOS, run:
yum install zimbra-zimlet-nextcloud
-
To install on Ubuntu, run:
apt-get install zimbra-zimlet-nextcloud
-
Restart zmmailbox server:
su - zimbra zmmailboxdctl restart
-
-
On NextCloud server, update the below configuration in
/etc/httpd/conf.d/nextcloud-ssl.confRewriteEngine On RewriteCond %{HTTP:Authorization} ^(.*) RewriteRule .* - [e=HTTP_AUTHORIZATION:%1] -
Login to NextCloud server URL https://nextcloud.server.com and navigate to Settings → Administration → Security.
-
In Brute-force IP whitelist section, specify the Zimbra server’s IP Range.
-
In OAuth 2.0 clients section, specify the Name and Redirection URL of the Zimbra server. For e.g.:
Specify Name -
My Zimbra ServerSpecify Redirection URL -
https://myzimbra.server.com/service/extension/oauth2/authenticate/nextcloud -
Copy the Client Identifier and Client Secret fields for the above entered Client. This will be used to update LDAP related configuration in the next step.
-
-
To enable NextCloud for domain example.com, add LDAP entries for it by executing the following commands:
zmprov md example.com zimbraOAuthConsumerCredentials <Client Identifier>:<Client Secret>:nextcloud zmprov md example.com zimbraOAuthConsumerRedirectUri https://myzimbra.server.com/service/extension/oauth2/authenticate/nextcloud:nextcloud zmprov md example.com zimbraOAuthConsumerAPIScope 'https://nextcloud.server.com/nextcloud/index.php:nextcloud_noop'
| zimbraOAuthConsumerAPIScope holds the URL to your Nextcloud instance, in our example we have set-up Nextcloud in a folder /nextcloud on nextcloud.server.com. If your Nextcloud is installed directly in the root / of your domain, make sure to use https://nextcloud.server.com/index.php:nextcloud_noop as zimbraOAuthConsumerAPIScope. |
In case your Zimbra and Nextcloud are on different domains, for e.g. zimbra.example.com and nextcloud.example.org, in that case you have to disable the same site cookie restriction. Execute the following commands:
zmlocalconfig -e zimbra_same_site_cookie="" zmmailboxdctl restart
| Please review your organization’s security policies before disabling the same site cookie. |
| Your browser will cache the previous cookie settings. So remove your cookies and site data and try accessing NextCloud again. |
Setting up Jitsi Videoconferencing Solution
Jitsi is a fully encrypted, 100% open-source, video conferencing solution. Jitsi integration is available in the Modern Web App allowing end-users to set up video conferencing directly in their calendar; i.e. just click a button to add a Jitsi link to a meeting invite and then launch into that video meeting.
Administrators must install/enable the zimlet and define what video server instance they plan to use. Administrators can deploy their own Jitsi video server instance. Even if administrators have not set up a Jitsi server instance, the Jitsi integration zimlet can use Jitsi’s publicly available free video conferencing solution to schedule meetings for the end users.
| No configuration changes are required if Jitsi’s publicly available free video conferencing solution is used for setting up events. |
-
Install Jitsi zimlet and its dependencies on Zimbra Server:
-
To install on Red Hat or CentOS, run:
yum install zimbra-zimlet-jitsi
-
To install on Ubuntu, run:
apt-get install zimbra-zimlet-jitsi
-
Restart zmmailbox server:
su - zimbra zmmailboxdctl restart
-
Setting up separate Jitsi server for the organization
If an organization do not intend to use Jitsi’s publicly available free video conferencing solution and wants to set up their own Jitsi server, they can refer to this setup guide
Once the Jitsi server is set up, configuration changes would be required on the Zimbra server to update the organization’s Jitsi server URL.
In this example, we will assume your organization’s Jitsi server URL as https://my-org-jitsi-server.com.
-
The following CLI commands need to be run as zimbra user.
su - zimbra
-
Go to /opt/zimbra/zimlets-deployed/zimbra-zimlet-jitsi.
-
Edit
config_template.xmland change the value of jitUrl parameter to https://my-org-jitsi-server.com. -
Example of the global block in the file after the update.
<zimletConfig name="zimbra-zimlet-jitsi" version="0.0.1"> <global> <property name="jitsiUrl"> https://my-org-jitsi-server.com</property> </global> </zimletConfig> -
Execute these commands to apply the changes:
zmzimletctl configure config_template.xml zmprov fc all
| For already logged in users, they will have to reload the Modern UI to apply configuration changes. |
-
End-user guide on how to use Jitsi integration zimlet - https://zimbra.github.io/userguide/zcloud/userguide-zcloud.html#_jitsi
Setting up Signature Template
The Signature Template Zimlet offers a globally configured email signature template that users can use to configure their email signature. This way all users in an organization can have a uniform signature.
The Administrator must install the zimlet and enable it for the users.
| In case of images in HTML, those should be on a public URL that does not change, as that will be fetched by the recipients. |
-
The following CLI commands need to be run as zimbra user.
su - zimbra
-
Copy and paste the below config file in
/tmp/zimbra-zimlet-signature-template.xml:<zimletConfig name="zimbra-zimlet-signature-template" version="0.0.1"> <global> <property name="htmlTemplate">PGRpdj48c3BhbiBzdHlsZT0iY29sb3I6ICNlMDNlMmQ7Ij48c3Ryb25nPk5BTUU8L3N0cm9uZz48L3NwYW4+PC9kaXY+PGRpdj48ZW0+PHNwYW4gc3R5bGU9ImNvbG9yOiAjN2U4YzhkOyI+RlVOQ1RJT048L3NwYW4+PC9lbT48YnIvPjxici8+PGltZyBzcmM9Imh0dHBzOi8vczIyLnE0Y2RuLmNvbS80NzYzMjUxMzcvZmlsZXMvZGVzaWduL3N5bmFjb3ItbG9nby0yMDE2LXJnYi5wbmciPjwvaW1nPjwvZGl2Pgo=</property> </global> </zimletConfig> -
Use base64 decoder to decode the htmlTemplate value.
-
Make the required changes in htmlTemplate block. Re-encode it and paste it in
/tmp/zimbra-zimlet-signature-template.xml -
Deploy the changes:
zmzimletctl configure /tmp/zimbra-zimlet-signature-template.xml
Preventive Out-of-Office Alert
The Preventive Out-of-Office Alert feature in Zimbra allows administrators to configure the visibility of out-of-office notifications within the organization. By default, the feature is enabled for users within the same domain, but cross-domain visibility can be configured based on organizational needs.
How to Configure the Preventive Out-of-Office Alert
Enable Cross-Domain Visibility (Optional)
By default, the out-of-office alert feature is restricted to users within the same domain. To enable cross-domain visibility of out-of-office statuses, the following local configuration setting must be adjusted:
-
Localconfig Key:
get_out_of_office_cross_domains -
When set to
true, the system will allow users to check the out-of-office status of recipients in other domains, as long as permissions allow it.
Managing External OOO Notifications
The following existing attributes allow you to control how out-of-office notifications are handled for external domains:
-
zimbraPrefOutOfOfficeSuppressExternalReply: Set toTRUEto prevent out-of-office messages from being sent to external domains. Set toFALSEto send OOO messages to external domains unless restricted by other attributes. -
zimbraInternalSendersDomain: Add domains that should be treated as "internal" to the recipient. Out-of-office notifications will be shown for users from these domains. -
zimbraPrefOutOfOfficeSpecificDomains: Specify which domains can receive out-of-office replies. -
zimbraPrefExternalSendersType: Controls which external senders receive out-of-office replies. -
ALL: All external domains. -
ALLNOTINAB: External users not in the recipient’s address book. -
INAB: Only users in the recipient’s address book. -
INSD: Specific domains.
Custom Fonts
The Custom Fonts feature allows users and administrators to personalize their email compositions by adding specific font names to their custom font lists. This feature supports consistent branding across an organization while allowing individual users to use their preferred fonts, provided these fonts are installed locally on their systems.
Custom Fonts List (Administrator)
-
Administrators can add names of specific fonts to the "Custom Fonts" list within the Zimbra web app.
-
These fonts must be installed on each user’s local system to render correctly in the email composer.
-
If a custom font is not installed on a user’s system, it will render in the default composer font.
Personal Fonts List (User)
-
Users can add names of their preferred fonts to the "My Personal Fonts" list through the settings in the Modern UI.
-
The fonts listed must be installed on the user’s local system to be used in the email composer.
-
Users can type in the font name using the provided input field and add it to their personal fonts list.
Font Selection in Composer
-
Fonts listed under "Custom Fonts" and "My Personal Fonts" will appear in the font selection menu in the email composer.
-
If a font is not installed on the user’s machine, the font name will appear in the list but will render using the default font.
-
Users can create email signatures using the custom fonts added to their lists.
Default Composer Font
-
Users can set a custom font as the default font for the email composer by navigating to Settings > Writing Email > Composer.
Known Limitations
-
Fonts with names that match TinyMCE’s default fonts may cause conflicts. For instance, if a custom font name is "Mycustom == Roboto", selecting "Mycustom" in the toolbar might incorrectly select "Roboto" from the font menu. This behavior is related to TinyMCE and is beyond Zimbra’s control.
Custom Fonts Configuration
This section provides instructions for configuring and using custom fonts in Zimbra Modern UI.
How to Configure Admin-Defined Custom Fonts on the Server
-
Connect to the Zimbra server using SSH.
-
Switch to the Zimbra user.
-
Navigate to
/opt/zimbra/zimlets-deployed/zimbra-zimlet-custom-fontsand openconfig_template.xmlin an editor. -
Follow the instructions provided in
config_template.xmlto set custom fonts in thecustomFontsListproperty. Modify theallowPersonalFontsproperty as needed. If this property is set to false, users will not see the "My Personal Fonts" section in the Custom Fonts Settings. -
After making changes to
config_template.xml, run the following commands:-
zmzimletctl configure config_template.xml -
zmmailboxdctl restart
-
Appendix A: Command Line Utilities
Command Line Interface (CLI) can be used to create, modify and delete certain features and functions of the Zimbra Collaboration. The Administration Console is the main tool for maintaining the Zimbra Collaboration, but some functions can only be changed from CLI utilities.
The CLI utilities can be used for the following purposes:
-
Provisioning accounts
-
Backup and Restore
-
Starting and stopping a service
-
Move mailboxes
-
Cross-mailbox searches
-
Installing self-signed certificates
-
Local configuration
| In general, provisioning and managing accounts should be performed from the Administration Console. |
General Tool Information
The Zimbra Collaboration command-line utilities follow standard UNIX command-line conventions. Use the following general guidelines with the CLI:
-
CLI commands are run as the zimbra user:
su - zimbra -
The CLI commands are case-sensitive. You must type them in lower case.
-
Press ENTER after you type a command.
-
To display usage information about a command, type the CLI command with
-h.Example:
zmprov -hlists all the options available for thezmprovutility. -
Each operation is invoked through command-line options. Many have a long name and a short name. For example, these two commands are equivalent:
zmprov createAccount joe@domain.com test123 zmprov ca joe@domain.com test123
Syntax Conventions
When demonstrating the syntax of each tool, the following conventions indicate required, optional, and alternate values:
-
{
attribute} in curly brackets is required information. -
[
attribute] in square brackets are optional arguments or information. -
{
a|b|c} or [a|b|c] options separated by the pipe character|means "a" OR "b" OR "c" -
For attribute names that may contain spaces, surround the name with double quotes.
Location of Command-Line Utilities
The command-line tools available for administrators are all located in
the /opt/zimbra/bin folder on the Zimbra Collaboration server.
Zimbra CLI Commands
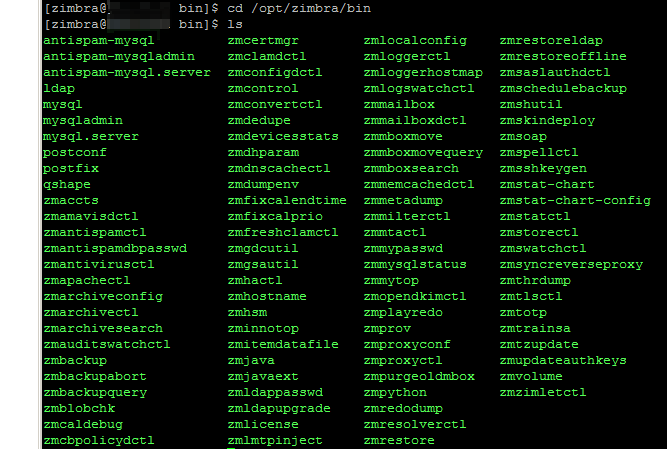
The table below lists the CLI commands in /opt/zimbra/bin.
| CLI | Description |
|---|---|
|
anti-spam SQL server admin utility |
|
anti-spam SQL client |
|
Start, stop the anti-spam SQL instance |
|
Start, stop, or find the status of Zimbra LDAP |
|
Perform a search on an LDAP server |
|
Send mysqladmin commands to the logger SQL instance |
|
Enters interactive command-line for the mailbox SQL instance |
|
Start, stop the mailbox SQL instance |
|
Send admin commands to the mailbox SQL instance |
|
Postfix command to view or modify the postfix configuration |
|
Start, stop, reload, flush, check, upgrade-configuration of postfix |
|
Examine postfix queue in relation to time and sender/recipient domain |
|
Lists the accounts and gives the status of accounts on domain |
|
Start, stop, restart, or find the status of the Amavis-D New |
|
Start, stop, reload, status for anti-spam service |
|
Start, stop, reload, status for the anti-virus service |
|
Changes anti-spam SQL database password |
|
Start, stop, reload, or check status of Apache service (for spell check) |
|
Command to view, modify, or configure archiving |
|
Start, stop, reload, status for archiving |
|
Search archives on the account |
|
Start, stop, restart, reload, status of the auditswatch |
|
Performs full backups and incremental backups for a designated mail host. |
|
Stops a backup that is in process. |
|
Find a specific full backup set |
|
Check consistency of the Zimbra blob store |
|
Check consistency of appointments and attendees in the Zimbra calendar |
|
Start, stop, and restart the cluebringer policyd service, if enabled |
|
Start, stop, kill, restart status of the MTA configuration daemon. |
|
Manage self-signed and commercial certificates |
|
Start, stop, or find the status of Clam AV |
|
Clean iPlanet ICS calendar files |
|
Start, stop, restart, status of the Zimbra servers. Also can use to find the Zimbra version installed |
|
Start, stop, the conversion server or find the status of the converted attachments conversion/indexing |
|
Number of unique ActiveSync device IDs per server |
|
(get devices count) gives the total devices system wide without the need of specifying individual servers. |
|
General information about the server environment is displayed |
|
Global Address Book (GAL) synchronization utility. Create, delete the GAL sync account and initiate manual syncs. |
|
Find the hostname of the Zimbra server |
|
Start, stop and status of a SM session. |
|
Extracts and packs |
|
Execute Java with Zimbra-specific environment settings |
|
Execute Java and Zimbra-specific environment settings including extension based jars. |
|
Changes the LDAP password |
|
View and install your Zimbra license |
|
Testing tool |
|
Used to set or get the local configuration of a Zimbra server |
|
Start, stop, reload, or find the status of the Zimbra logger service |
|
Used to manually map a DNS hostname to a zmhostname. |
|
Start, stop, status of the swatch that is monitoring logging. |
|
Performs mailbox management tasks |
|
Start, stop, reload, or find the status of the mailbox components (zmmailboxd, MariaDB, convert) |
|
(Cross Mailbox Search) Search across mailboxes to find messages and attachments |
|
7.1.3 and later. Used to move selected mailboxes from one Zimbra server to another. |
|
7.1.3 and later. Used to query ongoing mailbox moves on a server |
|
7.1.3 and later. Purges a mailbox from the old server after a mailbox move |
|
Start, stop, and restart |
|
Support tool that dumps an item’s metadata in a human-readable form |
|
Start, stop, and restart the Zimbra milter server if enabled |
|
Beginning in Zimbra Collaboration 7.0, this command is not used. Use |
|
Start, stop, or find the status of the MTA |
|
Change SQL passwords |
|
Status of mailbox SQL instance |
|
Output the reverse proxy configuration |
|
Start, stop, and restart the Zimbra reverse proxy |
|
Performs data restore using backed up snapshots taken periodically. Users who use snapshots to backup and restore their information from a standby site use this command. |
|
Performs all provisioning tasks in Zimbra LDAP, including creating accounts, domains, distribution lists and aliases |
|
Generates configuration for the nginx proxy |
|
Start, stop, restart, and find the status of the IMAP proxy service |
|
Purges POP/IMAP routing information from one or more memcached servers |
|
Ability to write Python scripts that access Zimbra Java libraries. It sets the Zimbra class path and starts the Jython interpreter. |
|
Support tool for dumping contents of a redolog file for debugging purposes |
|
Performs full restores and incremental restores for a designated mail host |
|
Restore accounts from the LDAP backup |
|
(Offline Restore) Performs full restore when the Zimbra server (i.e.,
the |
|
Start, stop, or find the status of saslauthd (authentication) |
|
Schedule backups and add the command to your cron table |
|
Used for other zm scripts, do not use |
|
Deploy skins |
|
Print mail, account, and admin information in the SOAP format |
|
Start, stop, or find the status of the spell check server |
|
Generate Zimbra’s SSH encryption keys |
|
Generate charts from zmstat data collected in a directory |
|
Outputs an XML configuration that describes the current state of the data gathered from zmstat-chart to generate charts on the Administration Console. |
|
Start, stop, check status, or rotate logs of zmstat data collectors |
|
Start, stop, or find the status of Zimbra store services |
|
Start, stop, or find the status of the Swatch process, which is used in monitoring |
|
Decodes the sync request/responses and logs them when verbose mode is turned on. |
|
Initiate a thread dump and save the data to a file with a timestamp |
|
Set the Web server mode to the communication protocol options: HTTP, HTTPS or mixed |
|
Used to train the anti-spam filter to recognize what is spam or ham |
|
Provides mechanism to process time zone changes |
|
Used to fetch the ssh encryption keys created by |
|
Manage storage volumes on your Zimbra Mailbox server |
|
Deploy and configure Zimlets |
|
Manage various operations for LDS. |
|
Utility to move blobs between storage volumes. |
Using non-ASCII Characters in CLIs
If you use non-ASCII characters in the CLI, in order for the characters to display correctly, you must change this setting to the desired UTF-8 before running the CLI command. To change this, type
export LC_All=<UTF_locale>
| The default locale on the zimbra user system account is LANG=C. This setting is necessary for starting Zimbra services. Changing the default LANG=C setting may cause performance issues with amavisd-new. |
zmprov (Provisioning)
The zmprov tool performs all provisioning tasks in Zimbra LDAP, including
creating accounts, aliases, domains, COS, distribution lists, and calendar
resources. Each operation is invoked through command-line options, each of
which has a long name and a short name.
The syntax is zmprov [cmd] [argument].
The syntax for modify can include the prefix “+” or “-” so that you can make changes to the attributes affected and do not need to reenter attributes that are not changing.
-
Use
+to add a new instance of the specified attribute name without changing any existing attributes. -
Use
-to remove a particular instance of an attribute.
The following example would add the attribute zimbraZimletUserProperties
with the value "blue" to user 1 and would not change the value of any other
instances of that attribute.
zmprov ma user1 +zimbraZimletUserProperties "com_company_testing:favoriteColor:blue"The attributes for the tasks zmprov can be used with are listed when you
type zmprov -h. The task area divided into the following sections:
| Long Name | Short Name | Syntax, Example, and Notes |
|---|---|---|
|
|
display usage |
|
|
use file as input stream |
|
|
{host}[:{port}] server hostname and optional port |
|
|
provision via LDAP instead of SOAP |
|
|
log4j property file, valid only with |
|
|
account name to auth as |
|
|
password for account |
|
|
read password from file |
|
|
use Zimbra admin name/password from localconfig for admin/password |
|
|
use auth token string (has to be in JSON format) from command line |
|
|
use auth token string (has to be in JSON format) from a file |
|
|
verbose mode (dumps full exception stack trace) |
|
|
debug mode (dumps SOAP messages) |
|
|
use LDAP master. This only valid with |
|
|
allow replacement of safe-guarded multi-value attribute configured in
localconfig key |
The commands are categorized and briefly described in the following topics:
Account Provisioning Commands
| Command | Syntax | Example/Notes | ||
|---|---|---|---|---|
|
|
|
||
|
|
|
||
|
|
|
||
|
|
|||
|
|
|||
|
|
|||
|
|
|
||
|
|
|||
|
|
|||
|
|
|||
|
|
|
||
|
|
|||
|
|
Must include |
||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|
||
|
|
|||
|
|
|||
|
|
|||
|
|
|
||
|
|
|
||
|
|
|
||
|
|
|
Calendar Resource Provisioning Commands
| Command | Syntax |
|---|---|
|
{name@domain} [attr1 value1 [attr2 value2]…] |
|
{name@domain | id} |
|
[-v] [domain] |
|
{name@domain | id} |
|
{name@domain | id} [attr1 value1 {attr2 value2]…] |
|
{name@domain} […] |
|
{name@domain | id} {newName@domain} |
Free Busy Commands
| Command | Syntax |
|---|---|
|
[-v] |
|
[{provider-name}] |
|
{domain | account-id} [account-id…] |
|
{domain} |
|
[{provider-name}] |
Domain Provisioning Commands
| Command | Syntax | Example/Notes | ||
|---|---|---|---|---|
|
|
This lists each COS, the COS ID and the number of accounts assigned to each COS |
||
|
|
|||
|
|
|
||
|
|
|
||
|
|
|
||
|
|
|||
|
|
|||
|
|
|
||
|
|
|
COS Provisioning Commands
| Command | Syntax | Example/Notes |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Server Provisioning Commands
| Command | Syntax | Example/Notes |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Used to publish into |
|
|
Used to list memcached servers (for nginix use). |
Config Provisioning Commands
| Command | Syntax | Example/Notes |
|---|---|---|
|
|
All LDAP settings are displayed |
|
|
|
|
|
Modifies the LDAP settings. |
|
|
|
|
|
|
|
|
|
|
|
Distribution List Provisioning Commands
| Command | Syntax | Example/Notes | ||
|---|---|---|---|---|
|
|
|
||
|
|
|
||
|
|
|
||
|
|
|||
|
|
|
||
|
|
|
||
|
|
|
||
|
|
|||
|
|
|||
|
|
|||
|
|
Mailbox Commands
| Command | Syntax | Example/Notes | ||
|---|---|---|---|---|
|
|
|||
|
|
|||
|
|
When unread message count and quota usage are out of sync with the data in the mailbox, use this command to immediately recalculate the mailbox quota usage and unread messages count.
|
||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
|||
|
|
Only specify the hostname parameter when unlocking a mailbox after a failed move attempt. |
Miscellaneous Provisioning Commands
| Command | Syntax | Example/Notes |
|---|---|---|
|
|
|
|
|
|
|
|
Prints all attribute names (account, domain, COS, servers, etc.). |
|
|
Flush cached LDAP entries for a type. See Zimbra LDAP Service. |
|
|
Generates a pre-authentication key to enable a trusted third party to
authenticate to allow for single-sign on. Used in conjunction with
|
|
|
Generates preAuth values for comparison. |
|
|
|
|
|
Logs Commands
| Command | Syntax | Example/Notes |
|---|---|---|
|
|
Creates custom logging for a single account. |
|
|
|
|
|
Shows all individual custom logger account. |
|
|
When name@domain is specified, removes the custom logger created for the account otherwise removes all accounts all account loggers from the system. |
|
|
This command removes all account loggers and
reloads |
See the zmprov Log Categories for a list of
logging categories.
Search Commands
| Command | Syntax | Example/Notes |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
Share Provisioning Commands
| Command | Syntax | Example/Notes |
|---|---|---|
|
|
Unified Communication Service Commands
| Command | Syntax | Example/Notes |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
IMAP/POP Proxy Commands
| Command | Example/Notes |
|---|---|
|
Used to publish into nginx.conf the servers that should be used for reverse proxy lookup. |
|
Returns the list of servers that have
Indicates whether a mailbox server is available for lookup requests from the proxy. |
|
Returns a list of all domains configured with |
Examples — using zmprov
zmprov ca name@domain.com passwordYou must know the COS ID number. To find a COS ID:
zmprov gc <COSname>
zmprov ca name@domain.com password zimbraCOS cosIDnumberstringzmprov ca name@domain.com ''The empty single quote is required and indicates that there is no local password.
See Provisioning User Accounts for the procedure.
See the Zimbra wiki page Bulk_Provisioning.
zmprov aaa accountname@domain.com aliasname@domain.comzmprov cdl listname@domain.comThe ID of the distribution list is returned.
zmprov adlm listname@domain.com member@domain.com| You can add multiple members to a list from the Administration Console. |
Use this command to change any password. Enter the address of the password to be changed.
zmprov sp admin@domain.com passwordzmprov cd marketing.domain.com zimbraAuthMech zimbrazmprov mcf zimbraDefaultDomain domain1.comzmprov gac -vzmprov gaa domain.comzmprov gaa -v domain.comzmprov ms server.com +zimbraServiceEnabled loggerThen type zmloggerctl start, to start the logger.
zmprov gs server.com attribute=valueFor example, zmprov gs example.com zimbraServiceEnabled=ldap to find out if
the ldap service is enabled.
To modify the purge interval, set zimbraMailPurgeSleepInterval to the
duration of time that the server should "sleep" between every two
mailboxes.
zmprov ms server.com zimbraMailPurgeSleepInterval <Xm>X is the duration of time between mailbox purges; m represents minutes. You could also set <xh> for hours.
Modify zimbraNewMailNotification to customize the notification email
template. A default email is sent from Postmaster notifying users that
they have received mail in another mailbox. To change the template, you
modify the receiving mailbox account. The variables are
-
${SENDER_ADDRESS}
-
${RECIPIENT_ADDRESS}
-
${RECIPIENT_DOMAIN}
-
${NOTIFICATION_ADDRESSS}
-
${SUBJECT}
-
${NEWLINE}
You can specify which of the above variables appear in the Subject,
From, or Body of the email. The following example is changing the
appearance of the message in the body of the notification email that is
received at name@domain.com. You can also change the template in a class
ofservice, use zmprov mc. The command is written on one line.
zmprov ma name@domain.com zimbraNewMailNotificationBody 'Important message from ${SENDER_ADDRESS}.${NEWLINE}Subject:${SUBJECT}'zmprov mc <default> zimbingaFeatureCalendarReminderDeviceEmailEnabled TRUE
zmprov ma <user1> zimbraFeatureCalendarReminderDeviceEmailEnabled TRUE
zmprov md <domain> zimbraFeatureCalendarReminderDeviceEmailEnabled TRUEzmprov mc <default> zimbraFeaturePriorityInboxEnabled TRUE
zmprov ma <user1> zimbraFeaturePriorityInboxEnabled TRUEConfigure Auto-Grouped Backup from the CLI
Set the backup method in the global configuration, and you can override the configuration on a per server basis if you do not want a server to use the auto-grouped backup method.
To set up auto-grouped backup, you modify LDAP attributes using the zmprov CLI. Type the command as
zmprov mcf <ldap_attribute> <arg>You can also set the attributes at the server level using zmprov ms.
The following LDAP attributes are modified:
-
zimbraBackupMode— Set it to beAuto-Grouped. The default isStandard. -
zimbraBackupAutoGroupedInterval — Set this to the interval in either days or weeks that backup sessions should run for a group. The default is `1d. Backup intervals can be 1 or more days, entered asxd(1d); or 1 or more weeks, entered asxw(1w). -
zimbraBackupAutoGroupedNumGroups— This the number of groups to spread mailboxes over. The default is 7 groups.
Changing Conversations Thread Default
Messages can be grouped into conversations by a common thread. The default is to thread messages in a conversation by the References header. If there is no References header, the Subject is used to determine the conversation thread. The default options can be changed from the COS or for individual accounts.
zmprov mc [cosname] zimbraMailThreadingAlgorithm [type]The types include:
-
none — no conversation threading is performed.
-
subject — the message will be threaded based solely on its normalized subject.
-
strict — only the threading message headers (References, In-Reply-To, Message-ID, and Resent-Message-ID) are used to correlate messages. No checking of normalized subjects is performed.
-
references — the same logic as "strict" with the constraints slightly altered so that the non-standard Thread-Index header is considered when threading messages and that a reply message lacking References and In-Reply-To headers will fall back to using subject-based threading.
-
subjrefs — the same logic as "references" with the further caveat thatchanges in the normalized subject will break a thread in two.
Detecting Corrupted Indexes
Run zmprov verifyIndex as a sanity check for the specified mailbox index.
Diagnostic information is written to stdout. If problems are detected, a
failure status is returned.
verifyIndex locks the index while it’s running, and checks every byte in
the index. Therefore, it’s not recommended to run this on a regular basis
such as in a cron job. The zmprov verifyIndex command should be used only
when you need to make a diagnosis.
zmprov verifyIndex <user@example.com>If verifyIndex reports that the index is corrupted, you can repair the
mailbox index by running reIndexMailbox (rim).
zmprov rim <user@example.com> start
|
Account operations |
|
ACL operations |
|
Backup and restore |
|
Inmemory cache operations |
|
Calendar operations |
|
DAV operations |
|
Database connection tracing |
|
Server extension loading |
|
Mail filtering |
|
GAL operations |
|
IMAP protocol operations |
|
Index operations |
|
Filesystem operations |
|
LDAP operations |
|
LMTP operations (incoming mail) |
|
General mailbox operations |
|
Miscellaneous |
|
Changes to mailbox state |
|
POP protocol operations |
|
Redo log operations |
|
Security events |
|
User session tracking |
|
SMTP operations (outgoing mail) |
|
SOAP protocol |
|
SQL tracing |
|
Mail store disk operations |
|
Sync client operations |
|
Startup/shutdown and other system messages |
|
Wiki operations |
|
Zimlet operations |
zmaccts
Use zmaccts to run a report that lists all the accounts, their status,
when they were created and the last time anyone logged on. The domain
summary shows the total number of accounts and their status.
Syntax
zmacctszmarchiveconfig
Use zmarchiveconfig for configuring the archiving mailbox. It has the
option of using short commands or full names for commands that lead to the
same function being carried out.
Syntax
zmarchiveconfig [args] [cmd] [cmd-args]...Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
Displays the usage options for this command |
|
|
(host)[:(port)] Displays the server hostname and optional port |
|
|
(name) Returns the value of the account name to be authorized |
|
|
Allows archiving to be provisioned via LDAP |
|
|
(pass) Returns the password for auth account |
|
|
(file) Allows password to be read from file |
|
|
Allows use of Zimbra admin/password from local |
|
|
Activates debug mode (dumps SOAP messages) |
|
||
|
[archive-address <aaddr> [archive-cos <cos>] [archive-create <TRUE/FALSE>] [archive-password <pa [zimbraAccountAttrName <archive-attr-value]+ |
|
|
||
zmarchivectl
Use zmarchivectl to start, stop, reload, or check the status of the Zimbra
account archive.
Syntax
zmarchivectl start|stop|reload|statuszmarchivesearch
Use zmarchivesearch to search across account archives. You can search
for archives that match specific criteria and save copies to a
directory.
Syntax
zmarchivesearch {-m <user@domain.com>} {-q <query_string>} [-o <offset>] [-l <limit>] [-d <output_directory>]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
|
|
|
Displays help messages |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Allows printing of status messages while the search is being executed |
zmarchivesearch -m user1@yourdomain.com -q "in:sent" -o 0 -l 30 -d /var/tmpzmbackup
Use zmbackup to perform full backups and incremental backups for a
designated mail host.
This utility has short option names and full names. The short option is
preceded by a single dash, while the full option is preceded by a double
dash. For example, -f is the same as --fullBackup.
Syntax
One of -f, -i, or -del must be specified.
zmbackup {-f | -i | del} {-a <arg>} [options]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
|
|
|
Display diagnostics for debugging purposes. |
|
|
|
|
Exclude blobs from full backup. If unspecified, use server config |
|
|
Exclude blobs on SM volumes from full backup; if unspecified, use server config |
|
|
Exclude search index from full backup; if unspecified, use server config |
|
|
|
Starts a full backup. In auto-grouped backup mode, this option also copies the redologs since the last backup (which is the main function of an incremental backup). |
|
|
Displays the usage options for this command. |
|
|
Starts an incremental backup. This option is not available in the auto-grouped backup mode. |
|
Include blobs in full backup. If this is unspecified, the server config is used. |
|
|
Include blobs on SM volumes in full backup. If this is unspecified, the server config is used. |
|
|
Include search index in full backup. If this is unspecified, the server config is used. |
|
|
Backs up blobs as individual files rather than in |
|
|
|
|
|
|
Runs full backup synchronously. |
|
|
|
|
|
Backs up blobs in compressed |
|
Backup blobs in |
Examples
In these examples, the server (-s) is server1.domain.com. The (-t)
is not required if the target is the default directory,
(/opt/zimbra/backup).
zmbackup -f -a all -s server1.domain.comzmbackup -i -a all -s server1.domain.comzmbackup -f -a user1@domain.com -s server1| Hostname does not need full domain if account is used. |
zmbackup -i -a user1@domain.com -s server1zmblobchk
Use zmblobchk to check the consistency of the Zimbra blob store
(/opt/zimbra/store). This command checks and records notes of files
without matching database metadata. It also checks to make sure that size
information is correct for the files.
Syntax
zmblobchk [options] startThe start command is required to avoid unintentionally running a blob check. The ID values are separated by commas.
Description
| Long Name | Short Name | Description |
|---|---|---|
|
<path> Target directory for database export files. |
|
|
|
Displays help messages |
|
|
<mailbox-ids> Specify which mailboxes to check. If not specified, check all mailboxes. |
|
Delete any items that have a missing blob. |
|
|
Delete items without exporting |
|
|
Skip blob size check |
|
|
<path> Write the paths of any unexpected blobs to a file |
|
|
|
Display verbose output; display stack trace on error |
|
<volume-ids> Specify which volumes to check. If not specified, check all volumes |
zmcalchk
Use zmcalchk to check the consistency of appointments on the Zimbra
calendar and sends an email notification regarding inconsistencies. For
example, it checks if all attendees and organizers of an event on the
calendar agree on start/stop times and occurrences of a meeting.
See the output of zmmailbox help appointment for details on
time-specs.
Syntax
zmcalchk [-d] [-n <type>] <user> <start-time-spec> <end-time-spec>Description
| Short Name | Description |
|---|---|
|
Debugs verbose details |
|
Allows the user to specify the maximum number of attendees to check. The default value is 50. |
|
Send email notifications to selected users if they are out of sync for an appointment |
zmschedulebackup
Use zmschedulebackup to schedule backups and add the command to your cron
table.
The default schedule is as follows:
-
Full backup, every Saturday at 1:00 a.m. (
0 1 * * 6) -
Incremental backup, Sunday through Friday at 1:00 a.m. (
0 1 * * 0-5)
Each crontab entry is a single line composed of five fields separated by a blank space. Specify the fields as follows:
-
minute — 0 through 59
-
hour — 0 through 23
-
day of the (month) — 1 through 31
-
month — 1 through 12
-
day of the (week) — 0 through 7 (0 or 7 is Sunday, or use names)
Type an asterisk (*) in the fields you are not using.
This command automatically writes the schedule to the crontab.
Syntax
zmschedulebackup {-q|-s|-A|-R|-F|-D}[f|i|d|] ["schedule"]Description
| Name | Command Name | Description | ||
|---|---|---|---|---|
|
|
Displays the usage options for this command. |
||
|
|
Default command. Displays the existing Zimbra backup schedule. |
||
|
|
Save the schedule. Allows you to save the schedule command to a text file so that you can quickly regenerate the backup schedule when the system is restored. |
||
|
|
Removes the current schedule and cancels all scheduled backups. |
||
|
|
Adds an additional specified backup to the current schedule. |
||
|
|
Replaces the current schedule with the specified schedule. |
||
|
|
Replaces the current schedule with the default schedule. |
||
|
||||
|
|
Backs up blobs as individual files rather than in |
||
|
|
Backs up blobs in compressed |
||
|
Backs up blobs in |
|||
|
|
Can be used only to designate a full back target location. The default is
|
||
|
|
Account specific. The default is all accounts. |
||
|
Send an email report to the admin user. |
|||
|
server - Mail server hostname. Default is localhost. |
|||
|
Runs full backup synchronously. |
|||
|
Exclude blobs from full backup. If unspecified, server config is used. |
|||
|
Include blobs in full backup. If unspecified, the server config is used. |
|||
|
Exclude blobs on SM volumes from full backup. If unspecified, the server config is used. |
|||
|
Include blobs on SM volumes in full backup. If unspecified, the server config is used. |
|||
|
Exclude search index form full backup. If unspecified, the server config is used. |
|||
|
Include search index in full backup. If unspecified, the server config is used. |
|||
|
||||
|
|
Incremental backup is not used with the auto-grouped backup mode. |
||
|
|
Full backup |
||
|
|
Delete backups. |
||
Backup Scheduling Examples
zmschedulebackup -Dzmschedulebackup -R f ["schedule"]zmschedulebackup -A f ["schedule"]zmschedulebackup -A i ["schedule"]zmschedulebackup -qDisplay the schedules on one line as a command, so that they can be copied to a text file and saved to be used if the application needs to be restored.
zmschedulebackup -szmbackupabort
Use zmbackupabort to stop a backup process. Before you can abort an
account you must know its backup label. This label is displayed after you
start the backup procedure. If you do not know the label, use
zmbackupquery to find the label name.
To stop the restore process:
The zmbackupabort -r interrupts an ongoing restore. The restore process
is stopped after the current account is restored. The command displays
message showing which accounts were not restored.
Syntax
zmbackupabort [options]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
Display diagnostics for debugging purposes |
|
|
Displays the usage options for this command |
|
|
Use |
|
|
Abort the restore in process |
|
|
|
|
|
The default is |
zmbackupquery
Use zmbackupquery to find full backup sets. The command can be used to
find a specific full backup set or full backup sets since a specific date,
or all backup sets in the backup directory.
To find out the best full backup to use as the basis for point-in-time restore of an account, run a command like this:
zmbackupquery -a <account email> --type full --to <restore-to time>Syntax
zmbackupquery [options]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
|
|
|
Display diagnostics for debugging purposes |
|
|
Displays the usage options for this command |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Returns detailed status information |
Specify date/time in one of these formats:
|
|
|
|
|
|
|
|
|
Specify year, month, date, hour, minute, second, and optionally millisecond.
Month/date/hour/minute/second are 0-padded to 2 digits, millisecond to 3 digits.
Hour must be specified in 24-hour format, and time is in local time zone.
zmrestore
Use zmrestore to perform full restores and incremental restores for a
designated mail host. You can either specify specific accounts, or, if no
accounts are specified, all accounts are in the backup are restored. In
addition, you can restore to a specific point in time.
This utility has short option names and full names. The short option is
preceded by a single dash, the full option is proceeded by a double dash.
For example, -rf is the same as --restorefullBackupOnly.
Syntax
zmrestore [options]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
|
|
|
Replays the redo logs in backup only, which Only excludes archived and current redo logs of the system. |
|
|
Continue to restore other accounts when an error occurs. |
|
|
Restores accounts to target accounts whose names are prepended with prefix. (Can only be used in commands that use the |
|
|
Display diagnostics for debugging purposes. |
|
Do not restore blobs (SM or not). |
|
|
Do not restore SM blobs. |
|
|
Do not restore search index. |
|
|
|
Displays the usage options for this command. |
|
|
|
|
|
|
|
|
Restores the account in directory service. |
|
|
|
|
|
|
|
|
|
|
|
Restores to the full backup only, not any incremental backups since that backup. |
|
|
|
|
If true, do not execute delete operation during redo log replay. |
|
|
Do not restore if named accounts were deleted or did not exist at backup
time. (This option is always enabled with |
|
|
|
Restores global tables and local config. |
|
|
|
Examples
Perform complete restore of all accounts on server1, including last full backup and any incremental backups since last full backup.
zmrestore -a all -s server1.domain.comPerform restore only to last full backup, excluding incremental backups since then, for all accounts on server1.
zmrestore -rf -a all -s server1.domain.comThe name of the new account will be new_user1@domain.com.
zmrestore -a user1@domain.com -ca -pre new_zmrestoreoffline (Offline Restore)
zmrestoreoffline requires that the following is true:
-
mailboxdIS NOT running -
SQL database IS RUNNING
-
LDAP directory IS RUNNING
Pre-requisites
Syntax
zmrestoreoffline [options]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
|
|
|
Replays the redo logs in backup only, which excludes archived and current redo logs of the system. |
|
|
Continue to restore other accounts when an error occurs. |
|
|
Restores accounts to new target accounts whose names are pre-pended with prefix. |
|
|
Display diagnostics for debugging purposes. |
|
|
Displays the usage options for this command. |
|
If true, ignore all errors during redo log replay. |
|
|
|
|
|
|
|
|
|
Restores the account in directory service. |
|
|
|
|
|
|
|
|
|
|
|
Restores to the full backup only, not any incremental backups since that backup. |
|
|
|
|
|
Do not restore if named accounts were deleted or did not exist at backup
time. (This option is always enabled with |
|
|
Restores global tables and local config. |
|
|
|
Examples
Before you begin zmrestoreoffline, the LDAP directory server must be
running.
Perform a complete restore of all accounts on server1, including last full backup and any incremental backups since last full backup.
zmrestoreoffline -s server1.domain.comzmrestoreldap
Use zmrestoreldap to restore accounts from the LDAP backup.
Syntax
zmrestoreldap {-lb <arg>} {-t <arg>} [options]Description
| Short Name | Description |
|---|---|
|
|
|
|
|
Lists all session labels in backup. |
|
Lists accounts in file. |
|
|
zmcontrol (Start/Stop/Restart Service)
Since the license daemon service is a critical and important service, it is not managed through the zmcontrol command. The zmcontrol command shows the status but you cannot start/stop/restart the LDS. Use zmlicensectl to perform the start/stop/restart operations for LDS.
|
Use zmcontrol to start, to stop, or to restart services. You can also
find which version of the Zimbra Collaboration is installed.
Syntax
zmcontrol [ -v -h ] command [args]Description
| Long Name | Short Name | Description |
|---|---|---|
|
Displays Zimbra software version. |
|
|
Displays the usage options for this command. |
|
|
Host name (localhost). |
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
zmmboxsearch (Cross Mailbox Search)
Use zmmboxsearch is used to search across mailboxes. You can search
across mailboxes to find messages and attachments that match specific
criteria and save copies of these messages to a directory.
Syntax
zmmboxsearch {-m <arg>} {-q <arg>} [-o <arg>] [-l <arg>] [-d <arg>] [options]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
|
|
|
Displays help information. |
|
|
Sets the limit for the number of results returned. The default is 25. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Request that the status message print while the search is being executed. |
Example
The following example performs a cross-mailbox search in the inbox folder of two different mailboxes on the specified server and puts a copy of the found messages in to the specified directory.
zmmboxsearch -m user1@yourdomain.com,user2@yourdomain.com -q "in:inbox" -d /var/tmpzmmboxmove
Use zmmboxmove to move mailboxes. The destination server manages the
overall move process. Using the zmmboxmove command significantly reduces
the account lockout time.
The CLI command zmmboxmove is used to move mailboxes from one Zimbra
server to another. Mailboxes can be moved between Zimbra servers that
share the same LDAP server. All the files are copied to the new server and
the LDAP is updated. After the mailbox is moved to a new server a copy
still remains on the older server, but the status of the old mailbox is
closed. Users cannot log on and mail is not delivered. You should check
to see that all the mailbox content was moved successfully before purging
the old mailbox.
Syntax
zmmboxmove -a <email> --from <src> --to <dest> [--sync]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
|
|
|
Displays the usage options for this command. |
|
|
|
|
|
|
|
|
Run synchronously |
zmmboxmovequery
Use zmmboxmovequery to query ongoing mailbox moves on a server, both
move-ins and move-outs.
Syntax
zmmboxmovequery -a <account email> [-s <server to query>]zmpurgeoldmbox
Use zmpurgeoldmbox to purge the mailbox from the older server after a
mailbox move.
Syntax
zmpurgeoldmbox -a <account email> [-s <server to purge>]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
|
|
|
Displays the usage options for this command |
|
|
|
zmgsautil
Use zmgsautil to create or delete the GAL sync account, and to force
syncing of the LDAP data to the GAL sync account.
A GAL sync account is created when the GAL is configured on a domain. This account is created and the polling interval for performing a full sync is managed from the Administration Console.
To see attributes and settings for a GAL sync account, run zmprov gds
against the account.
| Long Name | Description |
|---|---|
|
Creates the GAL sync account. This should be done from the Administration Console. The parameter "server" is required.
|
|
When configuring a datasource for a server, specify a folder name other
than
|
|
Deletes the GAL sync account and the references to the LDAP server. The account can also be deleted from the Administration Console.
|
|
This syncs new and updated contact data only.
The datasource ID the LDAP datasource ID. The datasource name is the name of the address book (folder) in the GAL account created to sync LDAP to. A cron job can be set up to run |
|
This syncs all LDAP contact data. You can also set this from the Administration Console.
|
|
This should be used to reload the entire GAL if there is change in the filter, attribute mapping or LDAP server parameters.
|
zmldappasswd
Use zmldappasswd to change the LDAP password on the local server. In
multi node environments, this command must be run on the LDAP master server
only.
This CLI command used with options changes other passwords.
For better security and audit trails the following passwords are generated in Zimbra:
-
LDAP Admin password. This is the master LDAP password.
-
LDAP Root password. This is used for internal LDAP operations.
-
LDAP Postfix password. This is the password used by the
postfixuser to identify itself to the LDAP server and must be configured on the MTA server to be the same as the password on the LDAP master server. -
LDAP Amavis password. This is the password used by the
amavisuser to identify itself to the LDAP server and must be configured on the MTA server to be the same as the password on the LDAP server. -
LDAP Replication password. This is the password used by the
LDAPreplicationuser to identify itself to the LDAP master and must be the same as the password on the LDAP master server.
Syntax
zmldappasswd [-h] [-r] [-p] [-l] new-passwordDescription
| Name | Syntax, Example, Notes |
|---|---|
|
Displays the help. |
|
Changes |
|
Changes |
|
Changes |
|
Changes |
|
Changes |
|
Changes |
|
Updates the password in the config database on replicas. Must be used with
|
|
|
zmlocalconfig
Use zmlocalconfig to set or get the local configuration for a Zimbra
server. Use zmlocalconfig -i to see a list of supported properties that
can be configured by an administrator.
Syntax
zmlocalconfig [options]To see the local config type zmlocalconfig.
Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
|
|
|
Show default values for keys listed in |
|
|
Edit the configuration file, change keys and values specified. The
|
|
|
Edit the keys whose change is known to be potentially dangerous. |
|
|
Shows the help for the usage options for this tool. |
|
|
Shows the list of supported properties. |
|
|
|
|
|
Shows the values for only those keys listed in the |
|
|
Shows which configuration file will be used. |
|
|
Suppress logging. |
|
|
This option is used with the edit option. Specified key is set to a random password string. |
|
|
Forces the display of the password strings. |
|
|
Remove a configuration key. If this is a key with compiled-in defaults, set its value to the empty string. |
|
|
Expand values. |
|
Allows control of the concurrency of Amavisd (default 10). |
|
|
Allows control of the concurrency of ClamAV (default 10). |
zmmailbox
Use zmmailbox for mailbox management. The command can help
administrators provision new mailboxes along with accounts, debug issues
with a mailbox, and help with migrations.
You can invoke the zmmailbox command from within the zmprov command.
You enter selectMailbox within zmprov to access the zmmailbox command
connected to that specified mailbox. You can then enter zmmailbox
commands until you type exit. Exit returns you to zmprov. This is
useful when you want to create accounts and also pre-create some folders,
tags, or saved searches at the same time.
Syntax
zmmailbox [args] [cmd] [cmd-args]...Description
| Short Name | Long Name | Syntax, Example, and Notes |
|---|---|---|
|
|
Display usage. |
|
|
Use file as input stream. |
|
|
|
|
|
Account name to auth as |
|
|
Use zimbra admin name/password from localconfig for admin/password. |
|
|
Use authtoken string (has to be in JSON format) from command line. |
|
|
Use authtoken string (has to be in JSON format) from a file. |
|
|
Mailbox to open. Can be used as both authenticated and targeted unless other options are specified. |
|
Account name to authorize as. Defaults to
|
|
|
|
Execute requests with admin privilege. |
|
|
Password for admin account and or mailbox. |
|
|
Read password from file. |
|
|
Timeout (in seconds). |
|
|
Verbose mode (dumps full exception stack trace) |
|
|
Debug mode (dumps SOAP messages) |
Specific CLI tools are available for the different components of a mailbox. Usage is described in the CLI help for the following.
|
Help on admin-related commands. |
|
Help on all |
|
Help on appointment-related commands. |
|
Help on contact-related commands (address book). |
|
Help on conversation-related commands. |
|
Help on filter-related commands. |
|
Help on folder-related commands. |
|
Help on item-related commands. |
|
Help on message-related commands. |
|
Help on miscellaneous commands. |
|
Help on right commands. |
|
Help on search-related commands. |
|
Help on tag-related commands. |
Examples
When you create an account, you may want to pre-create some tags and
folders. You can invoke zmmailbox inside of zmprov by using
selectMailbox(sm).
$ zmprov
prov> ca user10@domain.example.com test123
9a993516-aa49-4fa5-bc0d-f740a474f7a8
prov> sm user10@domain.example.com
mailbox: user10@domain.example.com, size: 0 B, messages: 0, unread: 0
mbox user10@domain.example.com> createFolder /Archive
257
mbox user10@domain.example.com> createTag TODO
64
mbox user10@domain.example.com> createSearchFolder /unread "is:unread"
258
mbox user10@domain.example.com> exit
prov>zmmailbox -z-m user@example.com gmsThis is required when using the command emptyDumpster. Use
--admin-priv to skip delegated auth as the target mailbox.
zmmailbox -z --admin-priv -m foo@example.com emptyDumpster--admin-priv with select Mailbox commandzmmailbox -z
mbox> sm --admin-priv foo@domain.comThis lets one user login to another user’s mailbox. The authenticating
user must be a delegated admin account and must have the adminLoginAs right
on the target mailbox. This auth option uses a non-admin auth token. Use
the --auth option to specify the authenticating account. To login as
user bar and open mailbox foo:
$ zmmailbox --auth bar@example.com -p password -m foo@example.comzmmailbox -z -m user@example.com gmszip fileWhen you use zmmailbox to backup individual mailboxes, you can save
the file as either a zip file or a tgz file. The default settings for
the information that is saved in these formats is different.
| File | TGZ | ZIP |
|---|---|---|
Briefcase |
X |
X |
Calendar |
X |
|
Conversations |
X |
|
Contacts |
X |
X |
Deleted Messages |
X |
X |
Emailed Contacts |
X |
|
Inbox |
X |
X |
Sent |
X |
X |
Sent Messages |
X |
X |
Tasks |
X |
To include all the mailbox content in a zip file, you must enable the meta
data. Type as:
zmmailbox -z -m user@example.com gru "?fmt=zip&meta=1" > <filename.zip>zmtlsctl
Use zmtlsctl to set the Web server zimbraMailMode to the communication
protocol options: HTTP, HTTPS, Mixed, Both and Redirect. The default
setting is HTTPS.
The zmtlsctl setting also impacts the ZCO’s Use Secure Connection
setting. ZCO users in a self-signed environment will encounter warnings
about connection security unless the root CA certificate is added to Window
Certificate Store. See the Zimbra Wiki article
ZCO Connection
Security for more information.
|
-
HTTP. HTTP only, the user would browse to
http://zimbra.domain.com. -
HTTPS. HTTPS only (default), the user would browse to
https://zimbra.domain.com.http://is denied. -
Mixed If the user goes to
http://it will switch tohttps://for the login only,then will revert tohttp://for normal session traffic. If the user browses tohttps://, then the user will stayhttps:// -
Both A user can go to
http://orhttps://and will keep that mode for the entire session. -
Redirect Like mixed if the user goes to
http://it will switch tohttps://but they will stayhttps://for their entire session.
All modes use TLS encryption for back-end administrative traffic.
Only zimbraMailMode HTTPS can ensure that no listener will be available
on HTTP/port 80, that no client application will try to auth over HTTP, and
that all data exchanged with the client application will be encrypted.
|
Note, mailboxd has to be stopped and restarted for the change to take effect.
| If you switch to HTTPS, you use the self-signed certificate generated during Zimbra installation in /opt/zimbra/ssl/zimbra/server/server.crt. For ZCO users, secure ZCO profiles will display Certificate Trust dialogs unless the root CA certificate is deployed to the server. For more information about ZCO certificates, see the Zimbra Wiki page ZCO Connection Security. |
Syntax
zmtlsctl [mode]mode = http, https, mixed, both, redirect
Steps to run
-
Type
zmtlsctl [mode]and press ENTER. -
Type
zmmailboxdctl stopand press ENTER. -
When
mailboxdis stopped, typezmmailboxdctl startand press ENTER.
Limitations When Using Redirect
-
Many client applications send an auth request in the initial HTTP request to the Server ("blind auth"). The implications of this are that this auth request is sent in the clear/unencrypted prior to any possible opportunity to redirect the client application to HTTPS.
-
Redirect mode allows for the possibility of a man-in-the-middle attack, international/unintentional redirection to a non-valid server, or the possibility that a user will mis type the server name and not have certificate-based validity of the server.
-
In many client applications, it is impossible for users to tell if they have been redirected (for example, ActiveSync), and therefore the users continue to use HTTP even if the auth request is being sent unencrypted.
zmhsm
Use zmhsm to start, stop (abort), and see the status of a SM session.
The threshold for when messages are moved to a storage volume is
configured from the Administration Console, Servers → Volumes page.
Syntax
zmhsm {abort|start|status} {server} <name>Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
Aborts the current SM session. If all the messages in a mailbox being processed were not moved before you clicked Abort, no messages from that mailbox are moved from the primary volume. Messages for mailboxes that have completed the move to the secondary volume are not moved back to the primary volume. |
|
|
Shows the help for the usage options for this tool. |
|
|
|
|
|
Manually starts the SM process. |
|
|
The status of the last SM session is displayed. |
zmlicense
Use zmlicense to view and install your Zimbra license.
The license can be viewed and installed from the Administration Console, Global Settings → License page.
Syntax
zmlicense [options]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
Check to see if a valid license is installed. |
|
|
Shows the help for the usage options for this tool. |
|
|
|
|
|
Install on LDAP only. |
|
|
Displays the license information. |
zmmetadump
The zmmetadump command is a support tool that dumps the contents of an
item’s metadata in a human readable form.
Syntax
zmmetadump -m <mailbox id/email> -i <item id>or
zmmetadump -f <file containing encoded metadata>zmmypasswd
Use zmmypasswd to change zimbra_mysql_password. If the --root option
is specified, the mysql_root_passwd is changed. In both cases, MariaDB is
updated with the new passwords. Refer to the MariaDB documentation to see
how you can start the MariaDB server temporarily to skip grant tables, to
override the root password.
| This requires a restart for the change to take effect. |
Syntax
zmmypasswd [--root] <new_password>zmplayredo
Users who maintain a backup and restore mechanism using the snapshot
facility of the storage layer use zmplayredo to restore backed up data.
This command brings all backed up data to the current state so that there
is no loss of information during the restore process.
Syntax
zmplayredo <option>Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
|
|
|
|
|
|
Shows the help information for this command. |
|
|
|
|
|
|
|
|
|
|
Stops the replay on occurrence of any error. |
|
|
|
|
|
|
|
|
|
Time is specified in the local time zone. The year, month, date, hour, minute, second, and optionally millisecond should be specified. Month/date/hour/ minute/second are 0-padded to 2 digits, millisecond to 3 digits. The hour must be specified in a 24-hour format.
zmproxyconfgen
Use zmproxyconfgen to generate the Nginx proxy configuration files. It
reads LDAP settings to replace template variables and generates the
final Nginx configuration.
Syntax
ProxyConfGen [options]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
|
|
|
Prints the default variable map. |
|
|
Prints the Definitions variable map after loading LDAP configuration and processing overrides. |
|
|
Displays help information. |
|
|
|
|
|
Specifies not to write configuration and only display the files that would be written. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Displays verbose data. |
|
|
|
zmproxypurge
Use zmproxypurge to purge POP/IMAP proxy routing information from one or
more memcached servers. Available memcached servers are discovered by the
zmprov gamcs function. Others can be specified if necessary using the
server port.
Syntax
ProxyPurgeUtil [-v] [-i] -a account [-L accountlist] [cache1] [cache2]...]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
Shows the help for the usage options for this tool. |
|
|
Displays verbose data. |
|
|
Displays account routing information. |
|
|
Displays account name. |
|
|
Displays file containing list of accounts, one per line. |
|
|
Specifies the format to be used for printing routing information with information. The fields that display by default are
|
|
(optional command) Specifies additional memcache server in the form of server:port. |
zmredodump
Use zmredodump for debugging purposes and to dump the contents of a
redolog file. When users are debugging a problem, Zimbra support might
ask them to run zmredodump with specific options.
Multiple log files/directories can be specified with all redolog files under each directory being sorted in ascending order and processed.
Syntax
zmredodump [options] <redolog file/directory> [...]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
Displays help messages. |
|
Specifies the mailbox ids separated by a comma or a space. The entire list of mailbox ids must be quoted if using space as a separator. To dump contents of all the redolog files, omit this option. |
|
|
Specifies if file offsets and size for each redolog dump should not be shown. |
|
|
|
Activates the quiet mode. Used to only print the log filename and errors, if any. Useful for verifying integrity of redologs with minimal output. |
|
Shows blob content. The specified item’s blob is printed with |
zmskindeploy
Use zmskindeploy to simplify the process of deploying skins for the Classic Web App.
This tool processes the available skins, enables them for all users of the Zimbra deployment, and restarts the web server so that it recognizes the new skins.
Syntax
zmskindeploy <path/to/skin/dir/or/zipfile>zmsoap
Use zmsoap to print mail, account, and admin information in the SOAP format.
Syntax
zmsoap [options] {path1} [path2]...Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
Prints usage information. |
|
|
|
|
|
|
|
|
|
|
|
Displays the Zimbra admin name and password to authenticate as. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Prints the SOAP request and other status information. |
|
|
zmstat-chart
Use zmstat-chart to collect statistical information for the CPU, IO,
mailboxd, MTAqueue, MariaDB, and other components and to run a script on the
csv files to display the usage details in various charts. These csv files
are saved to /opt/zimbra/zmstat/.
You must enable zmstat to collect the performance charts data:
-
Enter
zmprov ms {hostname} zimbraServerEnable stats. -
Restart the server, Enter:
zmcontrol stop zmcontrol start
Syntax
zmstat-chart -s <arg> -d <arg> [options]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Summary data generation is not included. |
|
|
|
|
|
|
|
|
One or more directories where the csv files are located. The csv files are
moved to directories listed by date under |
zmstat-chart-config
Use zmstat-chart-config to generate an xml file
/opt/zimbra/conf/zmstat-chart.xml from a template, taking into account
the server setup including theLDAP node and the processes run, among other
specifications.
zmstatctl
Use zmstatctl to run a control script for checking zmstat data
collectors. This instruction starts or stops monitoring processes, and
checks status or rotates logs.
Syntax
zmstatctl start|stop|status|rotatezmthrdump
Use zmthrdump to invoke a thread dump in the Zimbra server process and
print the output file. This command also gives the option of saving the
thread dump to a file and inserts a timestamp on the logfile.
Syntax
zmthrdump [-h] [-i] [-t <timeout seconds>] [-p <pid file>] [-f <file>] [-o <out-file>]Description
| Short Name | Description |
|---|---|
|
Displays help messages. |
|
Appends the timestamp to the LOGFILE before invoking SIGQUIT. |
|
Returns the PID to send SIGQUIT. The default value can be found in
|
|
Specifies the LOGFILE to save the thread dump output in. The default value
is |
|
Specifies the output file of the thread dump. The default value is stdout. |
|
Specifies the timeout value (in seconds) to exit if the process becomes unresponsive. The default value is 30 seconds. |
zmtrainsa
Use zmtrainsa to train the anti-spam filter. This command is run
automatically every night to train the SpamAssasin filter from messages
users mark as "junk" / "not junk" from their mailbox. See
SpamAssassin’s sa-update tool, which is
included with SpamAssassin. This tool updates SpamAssassin rules from the
SA organization. The tool is installed into /opt/zimbra/common/bin.
The zmtrainsa command can be run manually to forward any folder from any
mailbox to the spam training mailboxes. If you do not enter a folder name
when you manually run zmtrainsa for an account, for spam, the default
folder is Junk. For ham, the default folder is Inbox.
Syntax
zmtrainsa <user> <spam|ham> [folder]zmtzupdate
Use zmtzupdate to update time zone changes in existing appointments for
specific users or all users. An .ics rule file should first be created to
run with this command. A rule file lists a series of rules to match a time
zone and the replacement time zone definitions. More information about
this command can be found at:
https://wiki.zimbra.com/wiki/Changing_ZCS_Time_Zones.
Syntax
zmtzupdate --rulefile <rule file> -a <"all" or list of specific email addresses> [--sync] [--after <date/time stamp>]Description
| Long Name* | Short Name | Description |
|---|---|---|
|
|
|
|
|
|
|
|
Displays help information. |
|
Specifies the |
|
|
|
|
|
If specified, this option causes the |
zmvolume
Use zmvolume to manage storage volumes from the CLI. Note that volumes
can be managed from the Administration Console, Server → Volumes page.
Syntax
zmvolume {-a|-d|-l|-e|-dc|-sc} [options]Description
| Long Name | Short Name | Description |
|---|---|---|
|
|
Adds a volume. |
|
|
|
|
|
Compression threshold; default 4KB. |
|
|
Deletes a volume. |
|
|
Displays the current volume. |
|
|
Edits a volume. |
|
|
Shows the help for the usage options for this tool. |
|
|
|
|
|
Lists volumes. |
|
|
|
|
|
|
|
|
|
|
|
Sets the current volume. |
|
|
|
|
|
Turns off the current secondary message volume. |
zmzimletctl
Use zmzimletctl to manage Zimlets and to list all Zimlets on the server.
Additional information is provided in Zimlets. Most Zimlet
deployment can be completed from the Zimbra Administration Console.
Syntax
zmzimletctl [-l] {command} [<zimlet.zip>|<config.xml>|<zimlet>]Description
| Long Name | Description |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
Sets the access control, grant|deny, to a COS. |
|
|
|
View details about all Zimlets on the server. |
|
|
|
|
|
Shows the current Zimlet priorities (0 is high, 9 is low) |
|
|
zmproxyconfig
Use zmproxyconfig to manage Zimbra proxy and should only be used when
you have to make changes to Zimbra proxy after it has been installed.
See Zimbra Proxy Server.
Previous to Zimbra Collaboration 6.0, this command was called zmproxyinit.
|
Syntax
/opt/zimbra/libexec/zmproxyconfig [-h] [-o] [-m] [-w] [-d [-r] [-s] [-a w1:w2:w3:w4] [-i p1:p2:p3:p4] [-p p1:p2:p3:p4] [-x mailmode]] [-e [-a w1:w2:w3:w4] [-i p1:p2:p3:p4] [-p p1:p2:p3:p4] [-x mailmode]] [-f] -H hostnameDescription
| Short Name | Description |
|---|---|
|
Displays help messages. |
|
Hostname of the server on which enable/disable proxy functionality. |
|
Colon separated list of Web ports to use. Format: HTTP-STORE:HTTP-PROXY:HTTPS-STORE:HTTPS-PROXY (Ex: 8080:80:8443:443) |
|
Disable proxy. |
|
Enable proxy. |
|
Full reset on memcached port and search queries and POP/IMAP throttling. |
|
Colon separated list of IMAP ports to use. Format: IMAP-STORE:IMAP-PROXY:IMAPS-STORE:IMAPS-PROXY (Ex: 7143:143:7993:993) |
|
Toggle mail proxy portions. |
|
Override enabled checks. |
|
Colon separated list of POP ports to use. Format: POP-STORE:POP-PROXY:POPS-STORE:POPS-PROXY (Ex: 7110:110:7995:995) |
|
Run against a remote host. Note that this requires the server to be properly configured in the LDAP master. |
|
Set Cleartext to FALSE (secure mode) on disable. |
|
Disable reverse proxy lookup target for the store server. Only valid with
|
|
Toggle Web proxy portions. |
|
|
hostname is the value of the zimbra_server_hostname LC key for the
server being modified.
Required options are -f by itself, or -f with -d or -e.
Note that
-
-dor-erequire one or both of-mand-w. -
-ior-prequire-m. -
-arequires-w. -
-xrequires-wand-dfor store. -
-xrequires-wfor proxy.
The following are the defaults for -a, -i, -p, and -x if they are
not supplied as options.
|
default on enable: 8080:80:8443:443 |
default on disable: 80:0:443:0 |
|
default on enable: 7143:143:7993:993 |
default on disable: 143:7143:993:7993 |
|
default on enable: 7110:110:7995:995 |
default on disable: 110:7110:995:7995 |
|
default on store disable: http |
default on proxy enable/disable: http |
zmsyncreverseproxy
Use zmsyncreverseproxy to reverse proxy mobile sync HTTP traffic
between the source and forwarding server and port. Decodes the sync
requests/responses and logs them when verbose mode is turned on.
Syntax
zmsyncreverseproxy [-v] [-d] [-L log4j.properties] -p <port number> -fs <fwd server> -fp <fwd port> [-sv syncversions]Description
| Long Name | Short | Description |
|---|---|---|
|
|
Displays help. |
|
|
Verbose mode, dumps full exception stack trace. |
|
|
Debug mode, dumps decoded sync messages. |
|
|
The port this service listens on. |
|
|
The server host to forward requests to. |
|
|
The server port to forward requests to. |
|
|
Active sync versions supported. |
|
|
|
zmmoveblobs
The zmmoveblobs utility is designed for administrators to efficiently move blob data between storage volumes. This tool supports multiple movement scenarios for internal and external volumes and provides fine-grained control over the data transfer process. The utility supports multiple parameters to configure the blob movement process efficiently.
zmmoveblobs allows for the movement of blobs between:
-
Internal to Internal volumes.
-
Internal to External volumes.
-
External to External volumes.
-
External to Internal volumes.
This functionality is essential for optimizing blob storage and managing storage across volumes.
Important Notes
-
Volumes: Verify that sourceVolumeIds and destVolumeId exist and are accessible.
-
MaxBytes Constraint: Make sure the maxBytes value aligns with your system’s capacity and requirements.
-
Query Filtering: Adjust the query (is:anywhere) to match your specific use case.
Syntax
zmmoveblobs {-sid <sourceVolumeId> -did <destinationVolumeId>} [options]Description
| Long Name | Short | Description |
|---|---|---|
|
|
Displays help. |
|
|
Specifies the ID of the source volume from which blobs are to be moved. |
|
|
Specifies the ID of the destination volume to which blobs are to be moved. |
|
|
Specifies a comma-separated list of item types to move, or "all" to move all types. Supported Values: message, contact, appointment, task, wiki, document Default: "all" if not specified. |
|
|
Defines query parameters for filtering blobs during the movement process. Useful in Hierarchical Storage Management (HSM) to move data to a secondary store. Default: "is:anywhere" if not specified. |
|
|
Limits the total number of bytes to be moved. The operation will abort if this threshold is exceeded. Default: No limit. |
Examples
-
Command moves all types of blobs (-t all) from volume ID 1 to volume ID 5, with the query filter is:anywhere, limiting the total size of blobs to 1 MB (1048576 bytes).
$ zmmoveblobs -sid 1 -did 5 -t all -q is:anywhere -mb 1048576
-
Success Response: Upon successful execution, the utility will display the following details:
-
Blobsmoved: The total number of blobs moved.
-
Bytesmoved: The total size of blobs moved (in bytes).
-
TotalMailboxes: The number of mailboxes impacted by the operation.
-
-
Command to move appointments:
$ zmmoveblobs -sid 1 -did 4 -t appointment
-
Command to move all type of data with a query parameter:
$ zmmoveblobs -sid 1 -did 4 -t all -q after:-60minutes-
-t all / --types all: Indicates that all types of blobs (e.g., messages, contacts, appointments, tasks) should be included in the move. -
-q after:-60minutes / --query after:-60minutes: Filters the blobs to be moved based on their modification time.-
Only blobs modified or created within the last 60 minutes (more recent than 60 minutes ago) will be selected for movement.
-
-
-
Following are some more example with a query parameter:
$ zmmoveblobs -sid 1 -did 3 -t all -q in:junk$ zmmoveblobs -sid 1 -did 3 -t all -q in:inbox$ zmmoveblobs -sid 1 -did 3 -t all -q before:9/5/2025$ zmmoveblobs -sid 1 -did 3 -t all -q is:anywhere-
Command to move document blobs with a query and a max size:
$ zmmoveblobs -sid 1 -did 4 -t document -mb 52428800
-
Command to move documents using
-mbparameter to limit the document size:
Scenario:
Two documents are uploaded to the user’s inbox:
-
Document 1: Size 211 KB (approximately 215,362 bytes).
-
Document 2: Size 324 KB.
Following command executed to move the documents:
$ zmmoveblobs -sid 1 -did 4 -t document -mb 250000Sample Output:
Blobs Moved: 1
Bytes Moved: 215362
Total Mailboxes: 9Total Bytes Moved: 215,362 bytes (Document 1).
Behavior:
-
The -mb parameter limits the total size of blobs moved to 250,000 bytes.
-
Only blobs that fit within this size limit are moved.
Outcome:
-
Document 1 was moved as its size (211 KB) was within the limit.
-
Document 2 was skipped because its size (324 KB) exceeded the limit.
Document 2 will never be moved until the size in -mb option is increased.
-
Recommendation for movement of large data size
Depending upon various factors - data size, network speed, I/O speed, etc, you might want to update the timeout value of socket_so_timeout and increase to the suitable limit when doing movement of large data set.
Default value of socket_so_timeout is 30000. The value is in milliseconds which translates to 30 seconds. So if you want to change the default value to 60 seconds, following are the steps:
-
As a
zimbrauser, execute the following command to update thesocket_so_timeout:$ zmlocalconfig -e socket_so_timeout=60000 -
Restart mailbox service:
zmmailboxdctl restart
Appendix B: Configuring SPNEGO Single Sign-On
The SPNEGO protocol mechanism can be configured on Zimbra for single sign-on authentication to the Zimbra Classic Web App, Modern Web App, and to the Zimbra Connector for Outlook (ZCO). For ZCO configuration see Setting Up Single Sign-On Options for ZCO.
When users have authenticated to their Intranet through Active Directory, they can enter their Zimbra mailbox using Classic Web App or Modern Web App without having to re-authenticate.
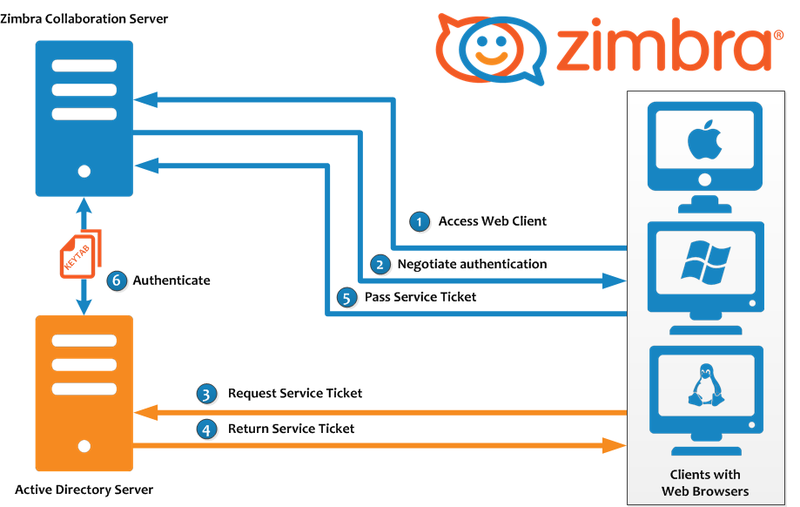
The Zimbra server configuration will redirect users attempting to log on to the Classic Web App or Modern Web App to a URL under SPNEGO protection. The server asks for authentication with Kerberos through SPNEGO, and redirects users to their Zimbra mailbox. When users log out, they get redirected to a logout URL that displays a Launch button. When users click it, they get directed to the Zimbra login page.
| When users log on to their Zimbra accounts from the Internet, the Zimbra login page displays and they must enter their Zimbra password to log on. |
| With SPNEGO SSO enabled on a domain, corresponding browser configuration is essential. See Configure Your Browser. Improperly configured browsers may bypass SPNEGO by opening an authentication dialog, thereby allowing a user to log in to the Zimbra mailbox by entering their correct AD domain username/password. Some other browsers may display a "401 Unauthorized" error in that situation. |
Configuration Process
-
Create the Kerberos keytab file.
-
Create an Active Directory service account. You use this account to generate the Kerberos keytab file.
-
Add the service Principal Names (SPN) directory property for an Active Directory service account.
-
Create the keytab file.
-
-
Enable and configure the SPNEGO protocol on the Zimbra server.
-
Configure browsers
Create the Kerberos Keytab File
Create an Active Directory service Domain account for each mailstore server.
-
Create an Active Directory service account. You use this account to generate the Kerberos keytab file to add to the Zimbra server.
-
Go to the Active Directory Start → Programs → Administrative Tools → Active Directory Users and Computers console.
-
To create the service account, click the AD Domain name and from the expanded content right-click Users and select New → User. Complete the New Object – User dialog.
-
Full name: Enter the user display name for the AD service account. We recommend using the Zimbra mailbox server name as the full name.
Example: Zimbra SPNEGO.
-
User Logon Name: This name is the value set for the
zimbraSpnegoAuthTargetNameserver attribute in LDAP. Write it down.Example: zimbraspnego/zimbralab.local.
-
User Logon Name (pre-Windows2000): This name is used for the
–mapUserparameter in thesetspnandktpasscommands.Example: ZIMBRALAB\zimbraspnego.
-
Click Next.
-
-
Enter and confirm the password for the
–pass {AD-user-password}parameter in thektpasscommand, configured below. -
Check Password never expires and User cannot change password, and click Next.
-
Click Finish to create the user. The service account name displays in the Users directory.
-
-
Use the
setspncommand to map the mailbox server name to the user account as the Service Principal Name (SPN). The SPN features in the process of mutual authentication between the client and the server hosting a particular service.-
From the command prompt, type
setspn –a {userlogonname} {serviceaccountname}Example 87. Map mailbox server name as servie Principal Names to user accountsetspn –a HTTP/mail1.example.com mail1 -
To verify that the SPN is registered, type
C:\>setspn –l {accountname}
A list of registered SPNs is displayed.
-
-
Create the keytab file used when signing into the Kerberos domain. Use the
ktpasstool from the Windows Server toolkit to create the Kerberos keytab.A Kerberos keytab file contains a list of keys that are analogous to user passwords. Restrict and monitor permissions on any keytab files you create. The command to type follows:
ktpass -out {keytab-file-to-produce} -princ {Service-Principal-Name}@\{the-kerberos-realm} -mapUser {AD-user} -mapOp set -pass {AD-user-password} -crypto RC4-HMAC-NT -pType KRB5_NT_PRINCIPALktpass -outThe key is written to this output file.
Enter the directory location and keytab file name. The keytab file name is
jetty.keytab.For example,
C:\Temp\spengo\jetty.keytab.-princThe principal name.
Enter the service Principal Name as used in Step 2 of Create the Kerberos Keytab File.
For example,
HTTP/mail1.example.com@MY_COMPANY.COM.-mapUserMaps the principal name from the
-princparameter to this user account.Enter the name of the AD service account previously set as the User Logon Name (pre-Windows2000) in Step 1.b of Create the Kerberos Keytab File.
-mapOpThis option sets the mapping. The value for this parameter is set.
-passSpecifies the password to use with the
-princaccount.Enter the password entered in the User Logon Name (pre-Windows2000) set in Step 1.c of Create the Kerberos Keytab File.
-cryptoThe cryptosystem to use.
Enter RC4-HMAC-NT.
-pTypeEnter KRB5_NT_PRINCIPAL.
To avoid warning messages from the toolkit, enter this value.
-
Using
ktpassto create ajetty.keytabfilektpass -out C: \Temp\spengo\jetty.keytab -princ HTTP/mail1.example.com@MY_COMPANY.COM -mapUser mail1 -mapOp set - pass password123 -crypto RC4-HMAC-NT -pType KRB5_NT_PRINCIPALThe command confirmation comes with something similar to the example below.
Targeting domain controller: ... Using legacy password setting method Successfully mapped HTTP/mail1.example.com to mail1. Key created. Output keytab to c:\Temp\spengo\jetty.keytab: Keytab version: 0x502 keysize 71 HTTP HTTP/mail1.example.com@MY_COMPANY.COM ptype 1 (KRB5_NT_PRINCIPAL) vno3 etype 0x17 (RC4-HMAC) keylength 16 (0xc383f6a25f1e195d5aef495c980c2bfe)
-
Transfer the keytab file (jetty.keytab) to the Zimbra server. Copy the file created in step 3 to the following Zimbra server location:
/opt/zimbra/data/mailboxd/spnego/jetty.keytab.
Do not rename the jetty.keytab file.
Many configuration files reference this filename.
|
Repeat steps 1 to 4 to create an create the keytab file (jetty.keytab) for each Zimbra mailstore server.
Configure Zimbra
SPNEGO attributes get configured in Global Config and on each Zimbra server, and domain pre-authentication gets configured for the domain.
Use the zmprov command to modify the Zimbra server.
| A Zimbra installation may support only one Kerberos REALM. |
-
Modify the following global config attributes, with the
zmprov mcfcommand.zimbraSpnegoAuthEnabledSet to TRUE.
zimbraSpnegoAuthErrorURLThis value is the URL that users get redirected to when SPNEGO auth fails. Setting it to
/zimbra/?ignoreLoginURL=1redirects the user to the regular Zimbra login page, where the user enters their Zimbra user name and password.zimbraSpnegoAuthRealmThe Kerberos realm in the domain controller; the domain name in the Active Directory. (
MY_COMPANY.COM)To modify the global config attributes, type:
-
zmprov mcf zimbraSpnegoAuthEnabled TRUE -
zmprov mcf zimbraSpnegoAuthErrorURL '/zimbra/?ignoreLoginURL=1' -
zmprov mcf zimbraSpnegoAuthRealm <MY_COMPANY.COM>
-
-
On each Zimbra server, modify the following global config attributes with the
zmprov mscommand.zimbraSpnegoAuthTargetNameThis is the user logon name from Step 1 B, User Logon Name.
zimbraSpnegoAuthPrincipalEnter the user logon name set in
zimbraSpnegoAuthTargetNameand the address set in global configzimbraSpnegoAuthRealm.Type as
zimbraSpnegoAuthTargetName@zimbraSpnegoAuthRealm.For example,
HTTP/mail1.example.com@MY_COMPANY.COM.To modify the server global config attributes, type:
-
zmprov ms mail1.example.com zimbraSpnegoAuthTargetName HTTP/mail1.example.com -
zmprov ms mail1.example.com zimbraSpnegoAuthPrincipal HTTP/mail1.example.com@MY_COMPANY.COM
-
-
Set up the following for the domain.
-
Kerberos Realm
-
Virtual host
-
Web client login URL and UAs
-
Web client logout URL and UAs
-
Set up the Kerberos Realm for the domain as the same realm set in the global config attribute
zimbraSpnegoAuthRealm. Typezmprov md {domain} zimbraAuthKerberos5Realm {kerberosrealm}. -
Set up the virtual hosts for the domain. Virtual-hostname-* are the hostnames you can browse to for the Zimbra Classic Web App UI. Type:
zmprov md {domain} +zimbraVirtualHostname {virtual-hostname-1} +zimbraVirtualHostname {virtual-hostname-2} ... -
Setup the web client login URL, and UAs allowed for the login URL on the domain.
-
Set the login URL. The login URL is the URL to redirect users to when the Zimbra auth token is expired.
zmprov md {domain} zimbraWebClientLoginURL '../service/spnego'. -
Honor only supported platforms and browsers.
zimbraWebClientLoginURLAllowedUA is a multi-valued attribute,values are regex. If this is not set, all UAs are allowed. If multiple values are set, an UA is allowed as long as it matches any one of the values.
zmprov md {domain} +zimbraWebClientLoginURLAllowedUA {UA-regex-1} +zimbraWebClientLoginURLAllowedUA {UA-regex-2} ...For example, to honor
zimbraWebClientLoginURLonly for Firefox, Internet Explorer, Chrome, and Safari on computers running Windows, and Safari on Apple Mac computers, type the following commands.zmprov md {domain} +zimbraWebClientLoginURLAllowedUA '._Windows._Firefox/3.*' zmprov md {domain} +zimbraWebClientLoginURLAllowedUA '._MSIE._Windows.*' zmprov md {domain} +zimbraWebClientLoginURLAllowedUA '._Windows._Chrome.*' zmprov md {domain} +zimbraWebClientLoginURLAllowedUA '._Windows._Safari.*' zmprov md {domain} +zimbraWebClientLoginURLAllowedUA '._Macintosh._Safari.*'
-
-
Setup the web client logout URL and UAs allowed for the logout URL on the domain.
-
Set the logout URL. The logout URL is the URL to redirect users to when users click Logout.
zmprov md {domain} zimbraWebClientLogoutURL '../?sso=1' -
Honor only supported platforms and browsers.
zimbraWebClientLogoutURLAllowedUAis a multi-valued attribute, where the accepted values are regex. If this attribute has no set value, all UAs are allowed. When it has multiple values, a UA is allowed as long as it matches any one of the values.zmprov md {domain} +zimbraWebClientLogoutURLAllowedUA {UA-regex-1} +zimbraWebClientLogoutURLAllowedUA {UA-regex-2} ...For example, to honor zimbraWebClientLogoutURL only for Firefox, Internet Explorer, Chrome, and Safari on computers running Windows, and Safari on Apple Mac computers, type the following commands.
zmprov md {domain} +zimbraWebClientLogoutURLAllowedUA '._Windows._Firefox/3.*' zmprov md {domain} +zimbraWebClientLogoutURLAllowedUA '._MSIE._Windows.*' zmprov md {domain} +zimbraWebClientLogoutURLAllowedUA '._Windows._Chrome.*' zmprov md {domain} +zimbraWebClientLogoutURLAllowedUA '._Windows._Safari.*'
-
-
-
Configure Your Browser
With the SPNEGO SSO feature enabled on your domain, you must configure users' browsers to use its Authentication mechanism. Improperly configured browsers exhibit different behaviors depending on the browser.
The following browsers are supported:
-
For computers running Windows: Edge, Firefox 52 or later, Chrome, Safari
-
Apple Mac computer: Safari
Configuration steps:
-
Firefox browser for computers running Windows
-
In the Firefox browser address field, type
about:config. The warning — This might void your warranty, is now displayed. -
Click I’ll be careful, I promise!
-
Search in Filters, type
network.n. Enter a comma-delimited list of trusted domains or URLs.Double-click
network.negotiate-auth.delegation-uris. Enterhttp://,https://.Double-click
network.negotiate-auth.trusted-uris. Enterhttp://,https://.Or, to set specific URLs,
Double-click
network.negotiate-auth.delegation-uris. Enter the domain addresses. For example,http://mail1.example.com,https://mail2.example.com.Double-click
network.negotiate-auth.trusted-uris. Enter the domain addresses. For example,http://mail1.example.com,https://mail2.example.com.
-
-
Internet Explorer, Chrome, and Safari for computers running Windows
-
In these browsers, go to Tools → Internet Options → Security → Local Intranet >Sites. In the "Sites" dialog, check all items.
-
Select Advanced. Add the domain server (hostname) URL, both
http://andhttps://. -
Click OK to close the file.
-
Go to Tools → Options → Advanced → Security. Locate and check Enable Integrated Windows Authentication.
-
Click OK and close the browser.
-
-
Safari for Apple Mac computers. No configuration is necessary.
Test your setup
-
On a Windows computer or an Apple Mac computer, log in to the computer as a domain user.
Your domain user token gets saved on the computer. The token gets picked up by the SPNEGO-aware browser and sent to the Zimbra server in the Authorization header.
-
Browse to the Zimbra Classic Web App login page. You should get redirected to your inbox without being prompted for your user name and password.
If SPNEGO auth fails, the user gets redirected to an error URL.
Troubleshooting setup
Make sure the following are true.
-
The browser is in the Intranet zone.
-
The user is accessing the server using a Hostname rather than an IP address.
-
Integrated Windows Authentication has been enabled in Internet Explorer, and the host has been "trusted" in Firefox.
-
The server is not local to the browser.
-
The client’s Kerberos system is authenticated to a domain controller.
-
If the browser displays "401 Unauthorized", it’s most likely that the browser either did not send another request with Authorization in response to the 401 or had sent an Authorization without using the GSS-API/SPNEGO scheme.
Check your browser settings and make sure it is one of the supported browsers/platforms.
-
If you get redirected to the error URL specified in
zimbraSpnegoAuthErrorURL, it means that the SPNEGO authentication sequence does not work.Take a network trace, make sure the browser sends Authorization header in response to the
401. Make sure the Negotiate is using GSS-API/ SPNEGO, not NTLM (use a network packet decoder like Wireshark).After verifying that the browser is sending the correct Negotiate, if it still does not work, turn on the following debug and check Zimbra logs:
-
Add (do not replace)
-DDEBUG=true -Dsun.security.spnego.debug=allto local config keyspnego_java_options. -
Add
log4j.logger.org.mortbay.log=DEBUGinlog4j.
Then restart the mailbox server.
Browse to the debug snoop page (
http://{server}:{port}/spnego/snoop.jsp). See if you can accesssnoop.jsp.Check
zmmailboxd.outandmailox.logfor debugging output.-
One of the errors at this stage could be because of clock skew on the jetty server. If this is the case, it should get shown in
zmmailboxd.out. Fix the clock skew and try again.
-
Configure Kerberos Auth with SPNEGO Auth
Kerberos auth and SPNEGO can co-exist on a domain. In this use case, you are using Kerberos as the mechanism for verifying a user’s principal/password against a KDC, instead of the native Zimbra LDAP, when the user cannot get in by SPNEGO.
In a properly configured browser, users are redirected to the Zimbra sign-in page when SPNEGO auth fails.
Users can enter their Zimbra username and password on the sign-in page to sign in manually.
The Domain attribute zimbraAuthMech controls the mechanism for verifying passwords.
If zimbraAuthMech is "kerberos5", the entered user name is used first to identify a valid Zimbra user (users must appear in the Zimbra LDAP).
The Zimbra user gets mapped to a Kerberos principal, and then the Kerberos principal + password is validated against a KDC.
This KDC could be different from, or the same as, the KDC used by the Active Directory domain controller (for SPNEGO auth).
| Every Microsoft Active Directory domain controller acts as Kerberos KDC. For SPNEGO auth, KDC does not get contacted by the mailbox server. The Kerberos token sent from the Authorization HTTP header along with jetty’s keytab file can identify/authenticate the user. |
For Kerberos auth (zimbraAuthMech*="kerberos5"), the mailbox server needs to contact KDC to validate principal+password.
For the java Kerberos client (i.e., Zimbra mailbox server), the default realm and KDC for the realm get specified in a Kerberos config file.
Specify the location of this config file in the optional JVM argument as java.security.krb5.conf.
If it is not specified, the default is /etc/krb5.conf.
When SPNEGO gets enabled in Zimbra, java.security.krb5.conf for the mailbox server is set to /opt/zimbra/jetty/etc/krb5.ini.
Therefore, that is the active file for configuring Kerberos auth.
Note that /opt/zimbra/jetty/etc/krb5.ini gets rewritten from /opt/zimbra/jetty/etc/krb5.ini.in each time the mailbox server restarts.
For persistent configuration then, you need to modify the /opt/zimbra/jetty/etc/krb5.ini.in file, not /opt/zimbra/jetty/etc/krb5.ini.
Under the [realms] section, KDC and admin_server get left unset for SPNEGO auth, but Kerberos auth requires them.
To configure:
-
Edit
/opt/zimbra/jetty/etc/krb5.ini.in. -
Change:
[realms] %%zimbraSpnegoAuthRealm%% = { default_domain = %%zimbraSpnegoAuthRealm%% }to
%%zimbraSpnegoAuthRealm%% = { kdc = YOUR-KDC admin_server = YOUR-ADMIN-SERVER default_domain = %%zimbraSpnegoAuthRealm%% } -
Replace YOUR-KDC and YOUR-ADMIN-SERVER to the hostname on which the
kdc/admin_serverfor Kerberos auth is running. -
Save the file and restart the mailbox server.
An important restriction is that the realm for SPNEGO and Kerberos auth must be the same.
For SPNEGO auth, the Kerberos principal in the Authorization header gets mapped to a unique Zimbra account.
For Kerberos auth, the Zimbra account gets mapped to a unique Kerberos principal.
The mapping (by domain attribute zimbraAuthKerberos5Realm) is the same for both.
Setting Up Single Sign-On Options for ZCO
| To use SSO, SPNEGO must be configured on the Zimbra server to use this option. |
The single sign-on option works with a specific server.
The server name used in the ZCO profile must match that in the SPNEGO configuration.
Make sure that the server name gets incorporated into the .msi file before installation.
To set up the single sign-on option in the .msi customization script:
-
Set the server name to be the server name configured for SPNEGO, enter
-sn <spnegoserver.example.com>. -
Set the password rule, enter
-pw 0.
cscript ZmCustomizeMsi.js <path/msi-filename> -sn <spnegoserver.example.com> -pw 0Appendix C: Zimbra Crontab Jobs
The crontab is used to schedule commands to be executed periodically on the Zimbra servers.
How to read the crontab
Each entry in a crontab file consists of six fields, specified in the following order: minute, hour, day, month, weekday, command
The fields are separated by blank spaces or tabs.
| Field | Description |
|---|---|
minute |
0 through 59 |
hour |
0 through 23 |
day of the (month) |
1 through 31 |
month |
1 through 12 |
day of the (week) |
0 through 7 (0 or 7 is Sunday, 1 is Monday, etc., or use names) |
command |
This is the complete sequence of commands to be executed for the job |
When an asterisk (*) is displayed, it means all possible values for the field. For example, an asterisk in the hour time field would be equivalent to "every hour".
Zimbra Cron Jobs
You can view the Zimbra crontab by logging on as zimbra and typing
crontab -l.
Scheduled jobs
The following cron jobs are scheduled to run for Zimbra:
Log pruning
The log pruning deletes logs from /opt/zimbra/log that are over eight
days old. The job runs at 2:30 a.m.
Status logging
zmstatuslog calls zmcontrol status and outputs it data into syslog.
This is primarily so that logger can read the data and keep the administration console status up-to-date.
Status logging job runs every 2 minutes.
Backups
Full and increment backups are scheduled to run according to the schedule
defined by zmschedulebackup command. By default the full backup is
scheduled for 1:00 a.m., every Saturday. The incremental backups are
scheduled for 1:00 a.m., Sunday through Friday.
By default, backups older then a month are deleted on the first of each month at 12 a.m.
Jobs for crontab.store
Log pruning
The log pruning deletes logs from /opt/zimbra/mailboxd/logs that are over
eight days old. The job runs at 2:30 a.m.
Clean up the quarantine dir
Mail identified with a virus or spam are not dropped immediately, but are put in quarantine. Messages older than seven days are deleted at 1:00 a.m daily.
Table maintenance
The ANALYZE TABLE statement is run on all tables in the database to
update the statistics for all indexes. This is done to make sure that the
SQL query optimizer picks the correct indexes when executing SQL
statements. This script is run 1:30 a.m. on Sunday.
Report on any database inconsistencies
zmdbintegrityreport is run weekly to check the SQL database for
corruption and will notify the administrator if any corruption is found.
When this is run, it may consume a significant amount of I/O. If you find
that it is an issue, you may want to change the frequency with which
zmdbintegrityreport is run by editing the Zimbra crontab entry.
This report runs at 11:00 p.m. Sundays.
Large sites may opt to disable this by setting:
zmlocalconfig -e zmdbintegrityreport_disabled=TRUEIf you choose to disable this, it is recommended that the integrity report be run by hand during the normal maintenance windows and prior to running any Zimbra upgrades.
Monitor for multiple mysqld to prevent corruption
A script is executed to see if mysqld process is running to detect cases where corruption is likely to be caused. An email is generated if it finds more than 1 mysqld process running. The script runs every 5 minutes.
Jobs for crontab.logger
process logs
zmlogprocess runs every 10 minutes to parse logs and produce MTA
metrics (as/av, volume, count, etc).
Daily reports
When the logger package is installed, a daily mail report is automatically
scheduled in the crontab. The report runs every morning at 11:30 and is
sent to the administrator’s email address.
Jobs for crontab.mta
Queue logging
The zmqueue report status via the syslog is reviewed. This is logger
data. The status is updated every 10 minutes.
Spam training
The zmtrainsa script is enabled to feed mail that has been classified as
spam or a non-spam to the SpamAssassin application. SpamAssassin learns
what signs are likely to mean spam or ham. This job should run only on one
Zimbra MTA. The job runs at 11:00 p.m.
Spam training cleanup
zmtrainsa empties the spam and ham mailboxes each day. The job runs at
11:45 p.m.
Spam Bayes auto-expiry
Spam bayes auto-expiry maintains the SpamAssassin Bayes database. This keeps the database to manageable size ensuring spam processing remains as quick as possible. This runs every day at 11:20 p.m.
Clean up amavisd/tmp
This job is used to clean up the amavisd temp files. It runs at 5:15 a.m. and at 8:15 p.m.
Single Server Crontab -l Example
crontab -l# ZIMBRASTART -- DO NOT EDIT ANYTHING BETWEEN THIS LINE AND ZIMBRAEND
#
# Log pruning
#
30 2 * * * find /opt/zimbra/log/ -type f -name *.log* -mtime +8 -exec rm {} \; > /dev/null 2>&1
35 2 * * * find /opt/zimbra/log/ -type f -name *.out.???????????? -mtime +8 -exec rm {} \; > /dev/null 2>&1
#
# Status logging
#
*/2 * * * * /opt/zimbra/libexec/zmstatuslog
#
# Backups
#
# BACKUP BEGIN
# BACKUP END
#
# crontab.ldap
#
#
#
# crontab.store
#
# Log pruning
#
30 2 * * * find /opt/zimbra/mailboxd/logs/ -type f -name \*log\* -mtime +8 -exec rm {} \; > /dev/null 2>&1
30 2 * * * find /opt/zimbra/log/ -type f -name stacktrace.\* -mtime +8 -exec rm {} \; > /dev/null 2>&1
#
# Table maintenance
#
30 1 * * 7 /opt/zimbra/libexec/zmmaintaintables >> /dev/null 2>&1
#
# # Report on any database inconsistencies
#
0 23 * * 7 /opt/zimbra/libexec/zmdbintegrityreport -m
#
# Monitor for multiple mysqld to prevent corruption
*/5 * * * * /opt/zimbra/libexec/zmcheckduplicatemysqld -e > /dev/null 2>&1
#
# crontab.logger
#
# process logs
#
00,10,20,30,40,50 * * * * /opt/zimbra/libexec/zmlogprocess > /tmp/logprocess.out 2>&1
#
# Graph generation
#
10 * * * * /opt/zimbra/libexec/zmgengraphs >> /tmp/gengraphs.out 2>&1
#
# Daily reports
10 1 * * * /opt/zimbra/libexec/zmdailyreport -m
#
#
crontab.mta
#
#
# Queue logging
#
0,10,20,30,40,50 * * * * /opt/zimbra/libexec/zmqueuelog
#
# Spam training
0 23 * * * /opt/zimbra/bin/zmtrainsa >> /opt/zimbra/log/spamtrain.log 2>&1
#
# Spam training cleanup
#
45 23 * * * /opt/zimbra/bin/zmtrainsa --cleanup >> /opt/zimbra/log/spamtrain.log 2>&1
#
# Dspam cleanup
#
0 1 * * * [ -d /opt/zimbra/data/dspam/data/z/i/zimbra/zimbra.sig ] && find /opt/zimbra/dspam/var/dspam/data/z/i/zimbra/zimbra.sig/ -type f -name \*sig -mtime +7 -exec rm {} \; > /dev/null 2>&1
8 4 * * * [ -f /opt/zimbra/data/dspam/system.log ] && /opt/zimbra/dspam/bin/dspam_logrotate -a 60 -l /opt/zimbra/data/dspam/system.log
8 8 * * * [ -f /opt/zimbra/data/dspam/data/z/i/zimbra/zimbra.log ] && /opt/zimbra/dspam/bin/dspam_logrotate -a 60 -l /opt/zimbra/data/dspam/data/z/i/zimbra/zimbra.log
#
# Spam Bayes auto-expiry
#
20 23 * * * /opt/zimbra/libexec/sa-learn -p /opt/zimbra/conf/salocal.cf --dbpath /opt/zimbra/data/amavisd/.spamassassin --siteconfigpath /opt/zimbra/conf/spamassassin --force-expire --sync > /dev/null 2>&1
#
# Clean up amavisd/tmp
#
15 5,20 * * * find /opt/zimbra/data/amavisd/tmp -maxdepth 1 -type d -name 'amavis-*' -mtime +1 -exec rm -rf {} \; > /dev/null 2>&1
#
# Clean up the quarantine dir
#
0 1 * * * find /opt/zimbra/data/amavisd/quarantine -type f -mtime +7 -exec rm -f {} \; > /dev/null 2>&1
ZIMBRAEND -- DO NOT EDIT ANYTHING BETWEEN THIS LINE AND ZIMBRASTART
Zimbra Single Sign-On using SAML with SimpleSAMLphp
Did you know that Zimbra supports SAML single sign-on? SAML is an open standard that allows you to have a single login page for all applications in your organization. SAML is a Zimbra Network Edition feature. Once you have set-up your SAML portal you can easily add [Multi Factor Authentication](multi-factor authentication).
Set up Zimbra SP in SimpleSAMLphp
In SAML terms applications are called Service Providers or SP’s. The service that provides your user database and takes care of your authentication is in SAML terms called Identity Provider or IDP. Usually, you only have one IDP and as many SP’s as you have applications. In this example, we will set-up Zimbra as a SAML SP and use SimpleSAMLphp as IDP. This is the configuration needed on SimpleSAMLphp (in /etc/simplesamlphp/metadata/saml20-sp-remote.php):
$metadata['https://zimbra.example.com/service/extension/samlreceiver'] = [
'simplesaml.attributes' => true,
'metadata-set' => 'saml20-sp-remote',
'debug' => TRUE,
'AssertionConsumerService' = [
[
'Binding' => 'urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST',
'Location' =>; 'https://zimbra.example.com/service/extension/samlreceiver',
'index' => 0,
'isDefault' => true,
],
],
'SingleLogoutService' => [
[
'Binding' => 'urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect',
'Location' => 'https://zimbra.example.com/service/extension/samlslo',
],
],
'NameIDFormat' => 'urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress',
'authproc' => array (
10 => array(
'class' => 'saml:AttributeNameID',
'identifyingAttribute' => 'mail',
'Format' => 'urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress',
),
)
];
You will also need to get the X.509 public certificate that is used for signing the SAML request from the IDP to Zimbra. You will need to download it and save it on your Zimbra server. This guide will assume you store your cert in /tmp/idpcert.pem, don’t forget to chown zimbra:zimbra /tmp/idpcert.pem. If you followed the SimpleSAMLphp setup guide you can find the certificate at /etc/simplesamlphp/cert/server.crt.
Set up Zimbra
Add the file /opt/zimbra/conf/saml/saml-config.properties to configure SAML in Zimbra add the contents:
# Issuer
saml_sp_entity_id=https://zimbra.example.com/service/extension/samlreceiver
# Login receiver for the service provider
saml_acs=https://zimbra.example.com/service/extension/samlreceiver
# Name ID format for the IDP to use in the SAMLResponse
saml_name_id_format=urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
# Date format for issue instant
saml_date_format_instant=yyyy-MM-dd'T'HH:mm:ss'Z'
# Identity provider login endpoint for redirect method
saml_redirect_login_destination=https://saml.example.tk/simplesaml/saml2/idp/SSOService.php?spentityid=https://zimbra.example.com/service/extension/samlreceiver
# Identity provider login endpoint for POST method
saml_post_login_destination=
# Identity provider logout endpoint for redirect method
saml_redirect_logout_destination=https://saml.example.tk/simplesaml/saml2/idp/SingleLogoutService.php
# Identity provider logout endpoint for POST method
saml_post_logout_destination=
# Logout redirect page if we are the landing page logout endpoint
saml_landing_logout_redirect_url=/
# Disable the audience path check
saml_skip_audience_restriction=true
# URL to send the user with error_code, error_msg query params. Default results in HTTP error code pages.
saml_error_redirect_url=
# The SAML logout document encoding, and SAML login receiver parameter encoding.
saml_document_encoding=ASCII
# Set to true to disable the audience path check.
saml_skip_audience_restriction=false
# The redirect location to send the user if their Zimbra account is not active.
saml_inactive_account_redirect_url
From command line as user root, copy the samlextn.jar and set up the IDP certificate:
mkdir /opt/zimbra/lib/ext/saml cp /opt/zimbra/extensions-network-extra/saml/samlextn.jar /opt/zimbra/lib/ext/saml/ su - zimbra cat /tmp/idpcert.pem |xargs -0 zmprov md exampledomain.com zimbraMyoneloginSamlSigningCert zmprov mcf zimbraCsrfRefererCheckEnabled FALSE zmmailboxdctl restart
Create users
Your user accounts must be manually created in Zimbra and be available in your IDP user database. It is important that the E-mail attribute in your IDP is set exactly the same as the Zimbra account name. Or the user will not be able to log-in. If it does not work run a tail -f /opt/zimbra/log/* while doing the authentication request and dig through to log to find out what the issue may be. Keywords to grep for: SAML, Audience and assertion.
Configurable Properties in saml-config.properties
The samlextn.jar uses a property file located at: ${zimbra_home}/conf/saml/saml-config.properties.
The following properties are supported:
| Key | Description | Default | Optional |
|---|---|---|---|
|
|
||
|
|
||
|
|
||
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
SLO Endpoint
In case you need to support SLO initiated from the IDP you need the SLO URL: https://zimbra.example.com/service/extension/samlslo
Also if you want to trigger the IDP to log-out when the user clicks logout in Zimbra you have to configure Zimbra to use this log-out URL: https://zimbra.example.com/service/extension/samllogout.
CsrfRefererCheck
On Zimbra 9 in most cases, you will need to disable CsrfRefererCheck for the SAML and restart Mailbox service to work.
su - zimbra zmprov mcf zimbraCsrfRefererCheckEnabled FALSE zmmailboxdctl restart
Glossary
The Glossary lists terms and acronyms used in this document, and includes both industry terms and application-specific terms. If a general industry concept or practice has been implemented in a specific way within the product, that is noted as well.
- A record
-
A (for "Address") records map the hostname to the numeric IP address. For Zimbra, the A record is the IP address for the Zimbra server.
- ABQ
-
The Allow/Block/Quarantine function gives system administrators control over which devices are allowed to sync via ActiveSync.
- Account Policy
-
Class of Service as exposed in Zimbra administration console.
- AD
-
Microsoft Active Directory Server. Used in Zimbra Collaboration as an optional choice for authentication and GAL, along with OpenLDAP for all other Zimbra Collaboration functions.
- Alias
-
An “also known as” email address, which should be routed to a user at a different email address.
- Attribute
-
Contains object-related data for directory server entries. Attributes store information such as a server host name or email forwarding address.
- Authentication
-
Process by which user-supplied login information is used to validate that user’s authority to enter a system.
- Blacklist
-
Anti-spam term, indicates a known bad IP address. This could be one that has been hijacked by spammers, or also one from a poorly maintained but legitimate site that allows mail relaying from unauthorized parties.
- BLOB
-
Binary Large Object.
- Class of Service (COS)
-
Describes an object in the Zimbra Collaboration LDAP data schema, which contains settings for things like user mail quotas. Each Zimbra Collaboration account includes a COS, and the account inherits all the settings from the selected COS.
- CLI
-
Command-Line Interface. Used to refer to the collective set of Zimbra Collaboration command-line tools, such as
zmprov. - Cluster
-
A type of network configuration for high availability, using clusters of servers (nodes). If one server fails or drops off the network, a spare takes over.
- Contacts
-
Within Zimbra Collaboration, Contacts are a user-interface feature listing that user’s personal collection of address and contact information.
- Conversation
-
Within Zimbra Collaboration, Conversations are a user-interface feature that presents email threads (emails sharing the same subject line) as a single Conversation listing. Users can expand the Conversation to view all emails within it.
- DHTML
-
Dynamic HTML. A technology employed in the Zimbra Classic Web App.
- DNS
-
Domain Name System is an Internet directory service. DNS is how domain names are translated into IP addresses and DNS also controls email delivery. Correctly configured DNS is required for Postfix to route messages to remote destinations
- Edge MTA
-
Generic term used to refer to any mail transfer agent that is the first line of defense in handling incoming email traffic. Functions that may occur on the Edge MTA include spam filtering.
- Entry
-
An item in the directory server, such as an account or mail host.
- Ephemeral Data
-
Data which is short lived or fast changing in nature. Login timestamps, authentication tokens, etc.
- Failover
-
Takeover process where a spare server machine detects that a main server is unavailable, and the spare takes over processing for that server.
- FQDN
-
Fully qualified domain name. The hostname and the path to the host. For example,
www.zimbra.comis a fully qualified domain name wherewwwis the host,zimbrais the second-level domain, and.comis the top level domain. - GAL
-
Global Address List, the Outlook version of a company directory. Lists contact information, including email addresses, for all employees within an organization.
- Global Configuration
-
A Zimbra Collaboration object containing default settings for servers and Class of Service.
- High Availability
-
Abbreviated as HA, high availability refers to the availability of resources in a computer system in the wake of component failures in the system.
- HTTP
-
HyperText Transfer Protocol, used along with SOAP for UI integration.
- IMAP
-
Internet Message Access Protocol is a method of accessing mail from a remote message store as if the users were local.
- Store
-
Within Zimbra Collaboration, a directory area that stores all the indexing information for mail messages on a particular mailbox server.
- Indexing
-
The process of parsing incoming email messages for search words.
- Java
-
Java is an industry standard object-oriented programming language. Used for the core Zimbra Collaboration application server.
- JavaScript
-
Scripting largely developed by Netscape that can interact with HTML source code. Technology used in the Zimbra Classic Web App.
- LDAP
-
Lightweight Directory Access Protocol, an industry standard protocol used for authentication.
- LMTP
-
Local Mail Transfer Protocol, used for transferring messages from Postfix MTA to the Zimbra Collaboration server for final delivery.
- Mailbox Server
-
Alternative term for Zimbra Collaboration server.
- MAPI
-
Messaging Application Programming Interface. A system built into Microsoft Windows to enable different email applications to work together.
- Message Store
-
Within Zimbra Collaboration, a directory area that stores the mail messages on a particular mailbox server.
- MDA
-
Mail Delivery Agent, sometimes known as a mail host. The Zimbra Collaboration server functions as an MDA.
- Metadata
-
Data that describes other data, rather than actual content. Within Zimbra Collaboration, metadata consists of user folders, threads, message titles and tags, and pointers.
- MIME
-
Multipurpose Internet Mail Extensions, a specification for formatting non-ASCII Internet message content such as image files. Format used to store messages in Message Store.
- MTA
-
Message Transfer Agent. MTA is a program that delivers mail and transports it between machines. A Zimbra Collaboration deployment assumes both the Postfix MTA and an edge MTA.
- MX Record
-
Mail eXchange. An MX record is an entry in a domain name database that identifies the mail server that is responsible for handling emails for that domain name. The email system relies on DNS MX records to transmit emails between domains. When mail is processed, the MX record is checked before the A record for the destination address.
- OOTO
-
Common shorthand for “out of the office”, used when sending vacation messages.
- Open Source
-
Refers to software created by groups of users for non-commercial distribution, where source code is published rather than proprietary.
- OS
-
Operating system, such as Linux, UNIX, or Microsoft Windows.
- POP
-
Post Office Protocol is used to retrieve email from a remote server over TCP/IP and save it to the local computer.
- Provisioning
-
The process of creating accounts or other data, usually in batch or automated fashion.
- RBH
-
Real-time black hole. Usually refers to web sites that, as a public service, provide lists of known bad IP addresses from which mail should be blocked, because the servers are either known to be spammers, or are unsecured and exploited by spammers.
- Responsive (web app)
-
This approach to design ensures that the application displays and functions well on a variety of devices and window or screen sizes. The Modern Web App is a Responsive Web App, facilitating a consistent user experience on any screen.
- Redo Logs
-
Detailed transaction log for the Zimbra Collaboration server, used for replay and replication.
- SAN
-
Storage Array Network. A high-availability data storage area.
- Schema
-
Describes the data structures in use for by directory services at a particular organizational site.
- SMTP
-
Simple Mail Transfer Protocol. Used in Zimbra Collaboration deployments between the Edge MTA and the Postfix MTA.
- SNMP
-
Simple Network Monitoring Protocol. Used by monitoring software to pick up critical errors from system logs.
- SOAP
-
Simple Object Access Protocol, an XML-based messaging protocol used for sending requests for Web services. The Zimbra Collaboration servers use SOAP for receiving and processing requests, which can come from Zimbra Collaboration command-line tools or Zimbra Collaboration user interfaces.
- Spam
-
Unsolicited commercial email. Spammers refer to their output as “bulk business email”.
- SQL
-
Structured Query Language, used to look up messages in the Message Store.
- SSL
-
Secure Sockets Layer.
- Tags
-
A Zimbra Classic Web App feature. Users can define tags and apply them to mail messages for searching.
- TCO
-
Total Cost of Ownership. Zimbra Collaboration reduces total cost of ownership (TCO) by reducing requirements for server hardware, OS licensing fees, supporting application license fees, disk storage requirements, and personnel (IT, help desk, consulting).
- TLS
-
Transport Layer Security.
- UCE
-
Unsolicited commercial email, also known as spam.
- Virtual Alias
-
A type of mail alias recognized in the Postfix MTA.
- Whitelist
-
Anti-spam term for a known good mail or IP address. Mail coming from such an address may be “automatically trusted”.
- XML
-
eXtended Markup Language.
- Zimbra administration console
-
The Zimbra Collaboration administrator interface.
- Zimbra Web Client
-
Refers to any of the end-user interfaces provided over the Web as part of a Zimbra server.